Method for protecting privacy based on access control
A privacy information and access control technology, applied in the direction of digital transmission systems, electrical components, transmission systems, etc., can solve privacy protection and other issues, and achieve the effects of leakage prevention, strong versatility and practicability, and easy implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
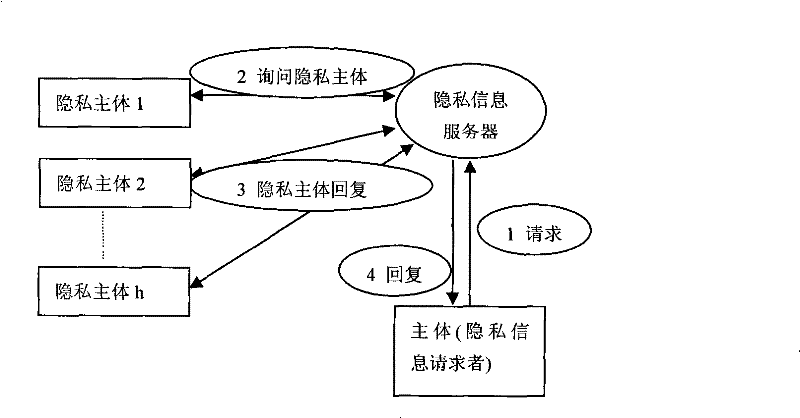
[0029] In this embodiment, the hospital protects the medical record information of patient A as an example. Patient A's medical record information is private information that needs to be protected, namely object o; medical record information is stored in the hospital's server, and all access to private information is controlled by the server. Patient A's medical record information involves the privacy of the hospital and patient A. Therefore, there are two privacy subjects: hospital s' 1 , patient A s’ 2 ; Here consider the situation that doctors and nurses access medical record information, that is, the subjects are: doctor s 1 , nurses 2 .
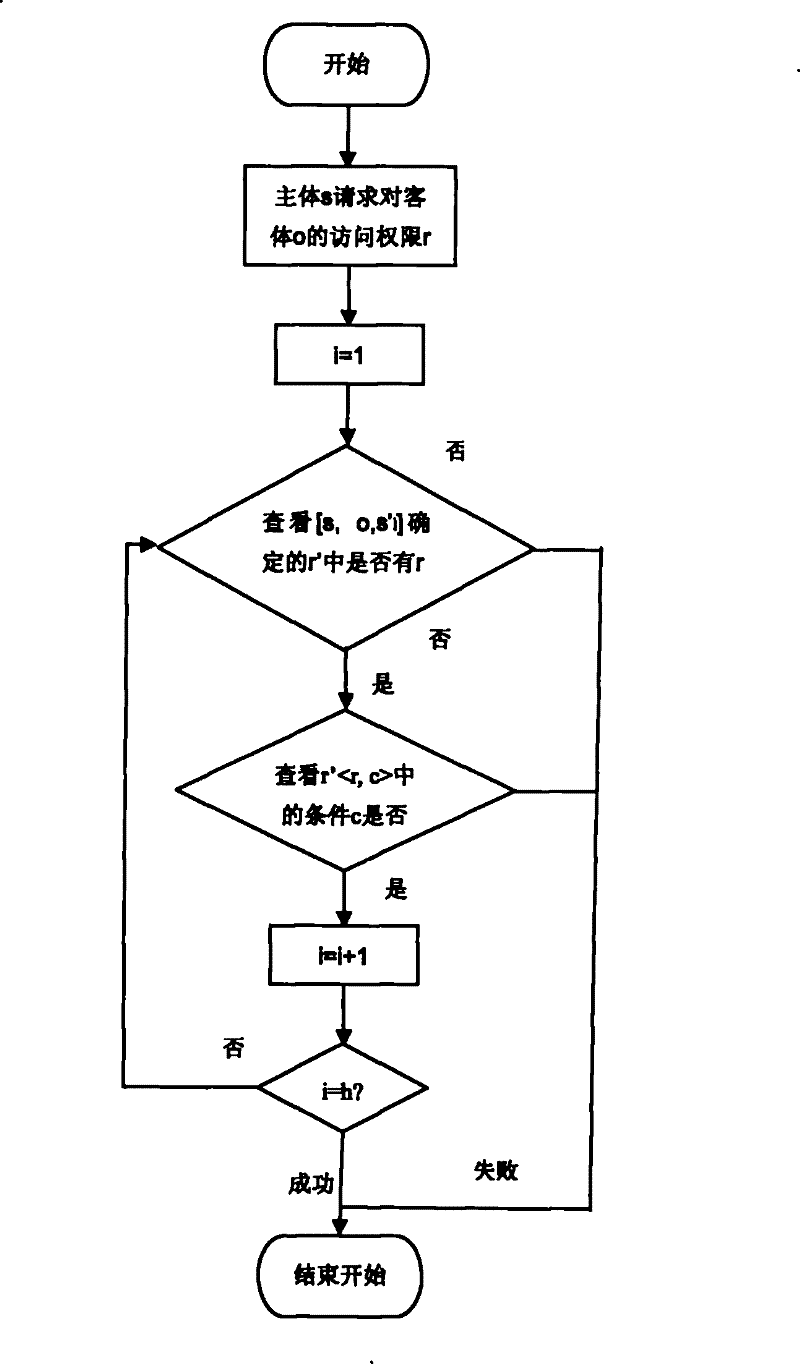
[0030]First, the privacy subject hospital and patient A respectively set access control policies when different subjects access medical record information. Usually, the privacy access policy set by the hospital is often for all patient medical record information, so it is relatively loose, so as to facilitate doctors and nurses to pe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com