System and method for implementing high-efficiency security memory
A safe storage and high-efficiency technology, applied in the direction of response error generation, redundancy in operation for data error detection, etc. The effect of improving storage efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0150] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
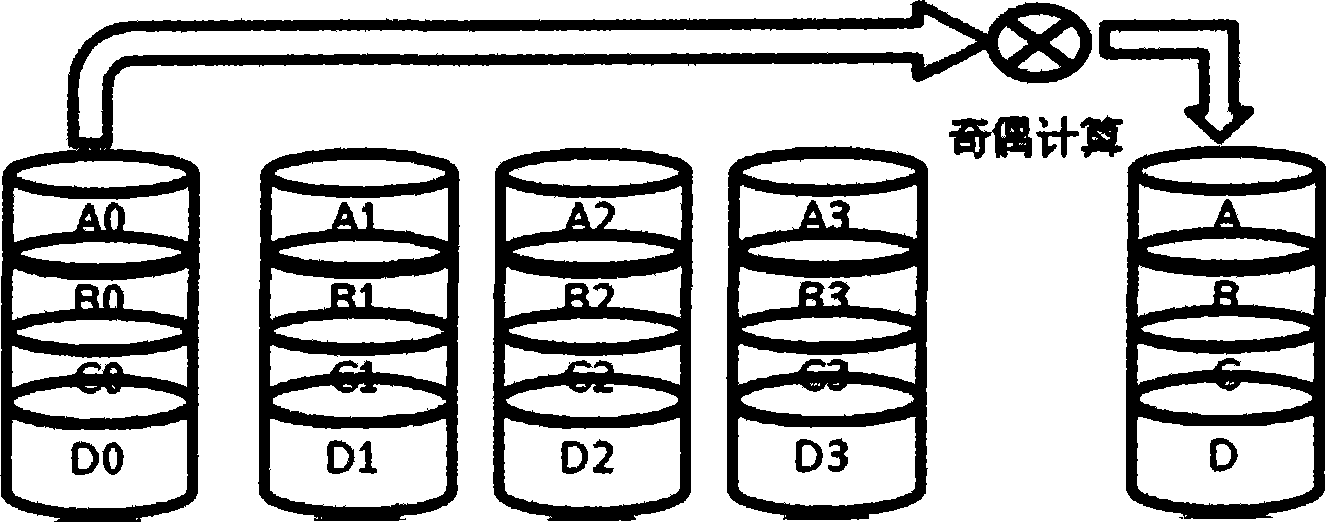
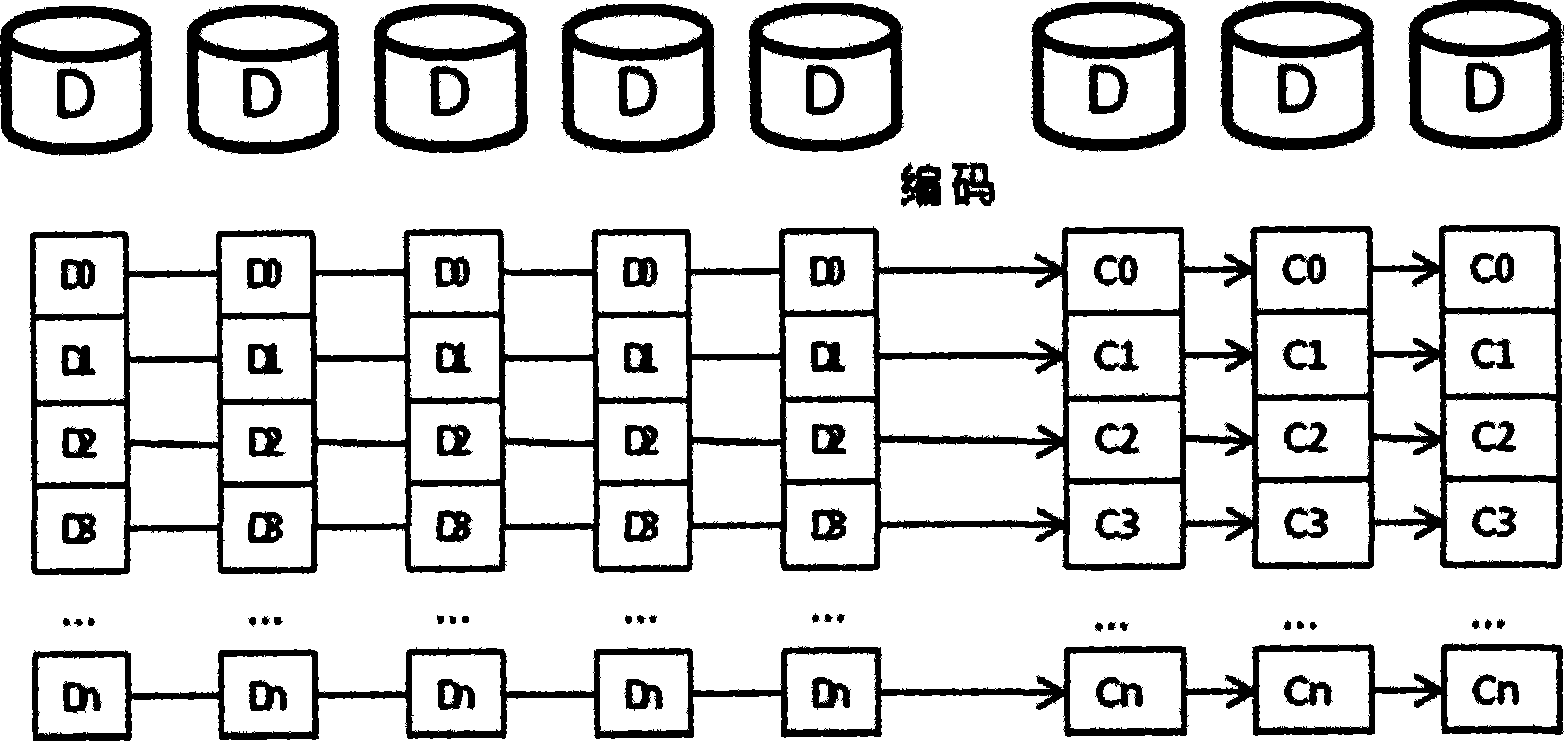
[0151] In order to solve the problems existing in the prior art, the system for realizing efficient and safe storage proposed by the present invention mainly includes the following parts:
[0152] storage server for storing original data and redundant data;
[0153] Metadata server, used to save the basic information of all file data;
[0154] The protocol server, when receiving the write operation request, writes the original data to be written to the storage server, and at the same time instructs the encoding server to encode the original data to be written, and after the writing is completed, writes the The basic information is stored in the metadata server; when a read operation request is received, the metadata server is accessed, the storage location of the original data to be read is obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com