Method for short message password protection matrix authentication
A short message password and matrix technology, which is applied in information format, wireless communication, user identity/authority verification, etc., can solve the problems of inability to cover remote areas, difficulties in promotion and sales, and prominent delay phenomena, so as to increase the amount of effective information, High security and effect of reducing the number of transmissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] specific implementation plan
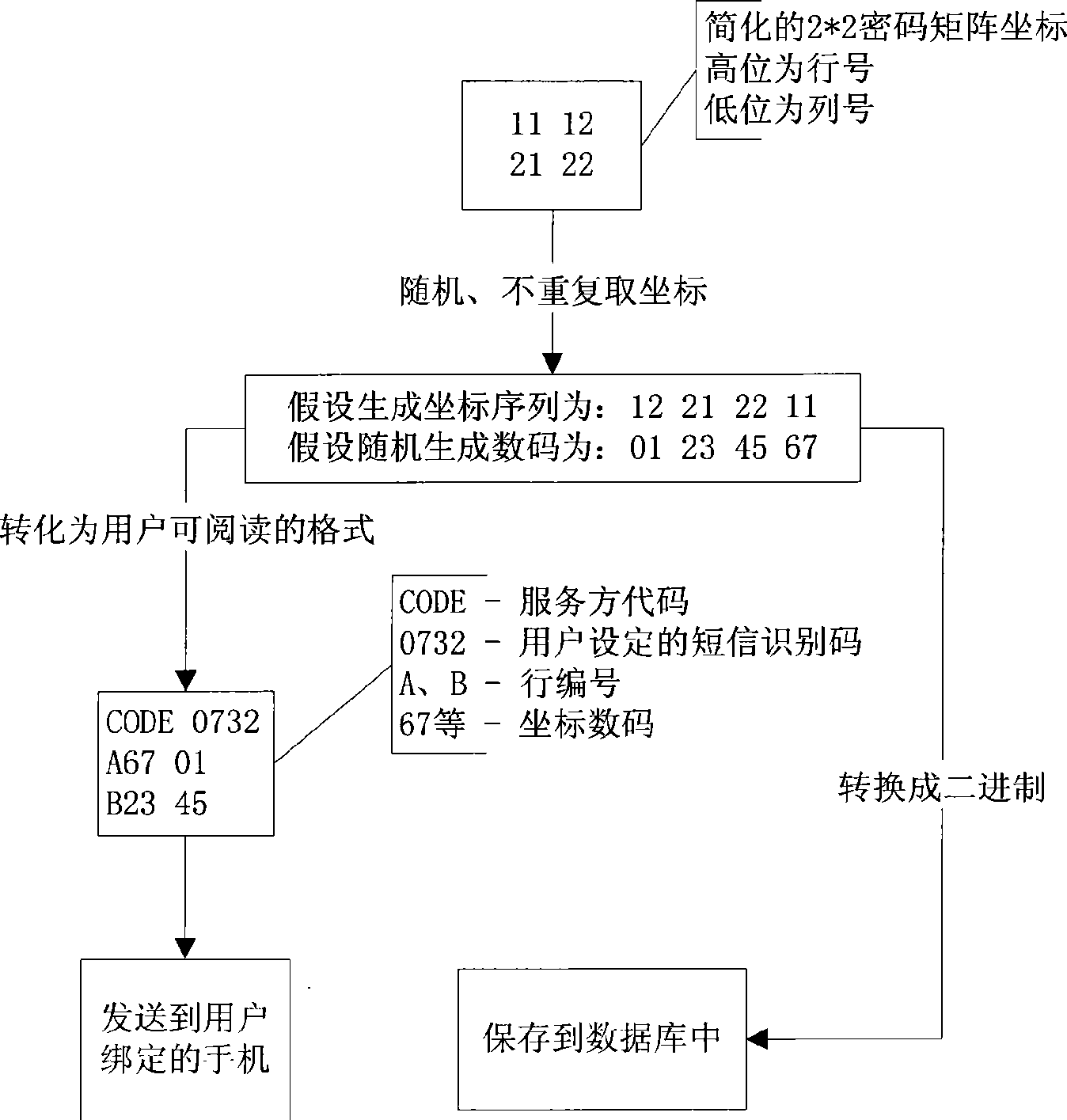
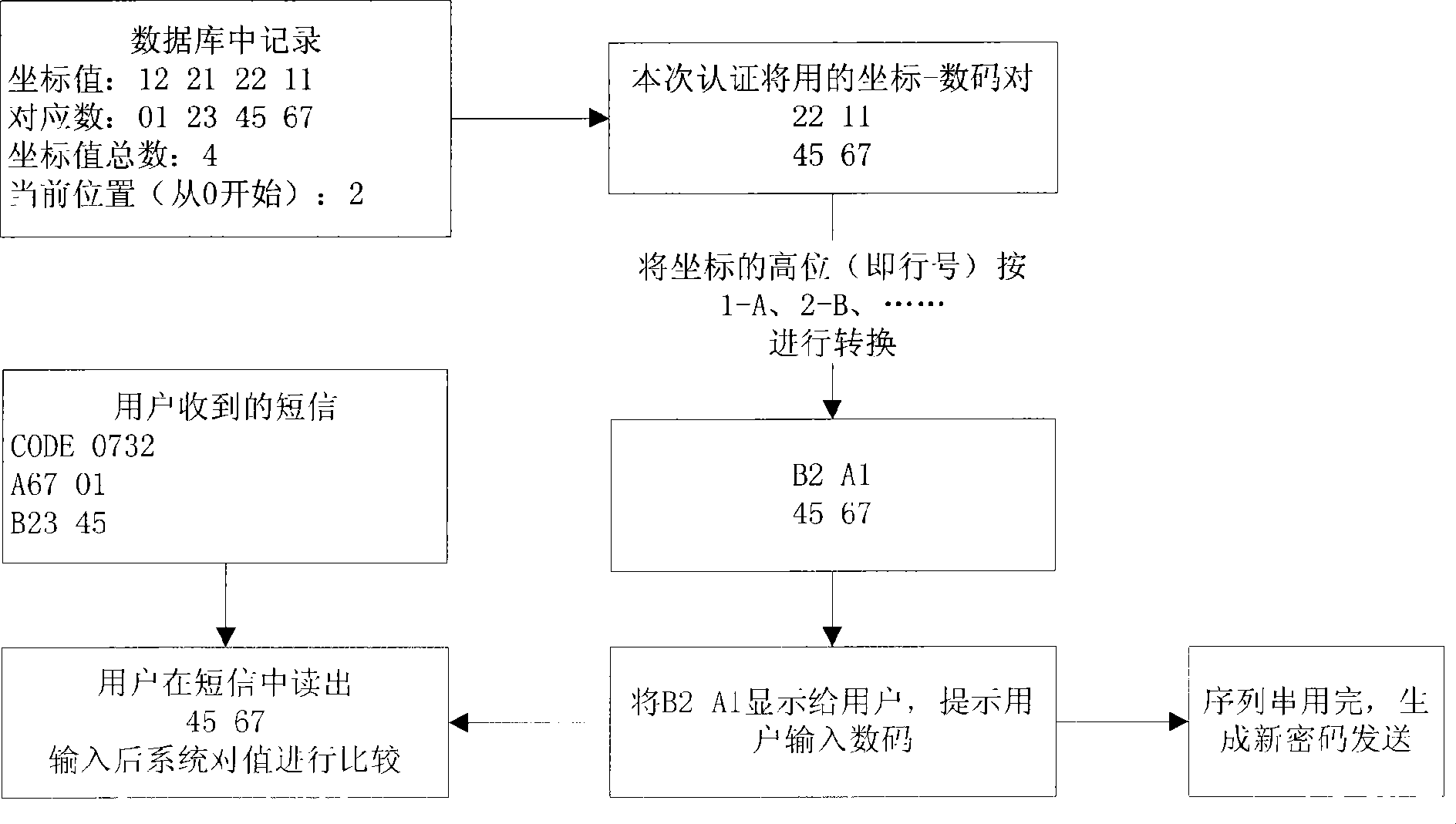
[0026] 1. The service party connects the mobile phone or GSM module to the server with a data cable, and uses serial port programming and other technologies to communicate with the mobile device and send and receive short messages;
[0027] 2. Design and build database tables:
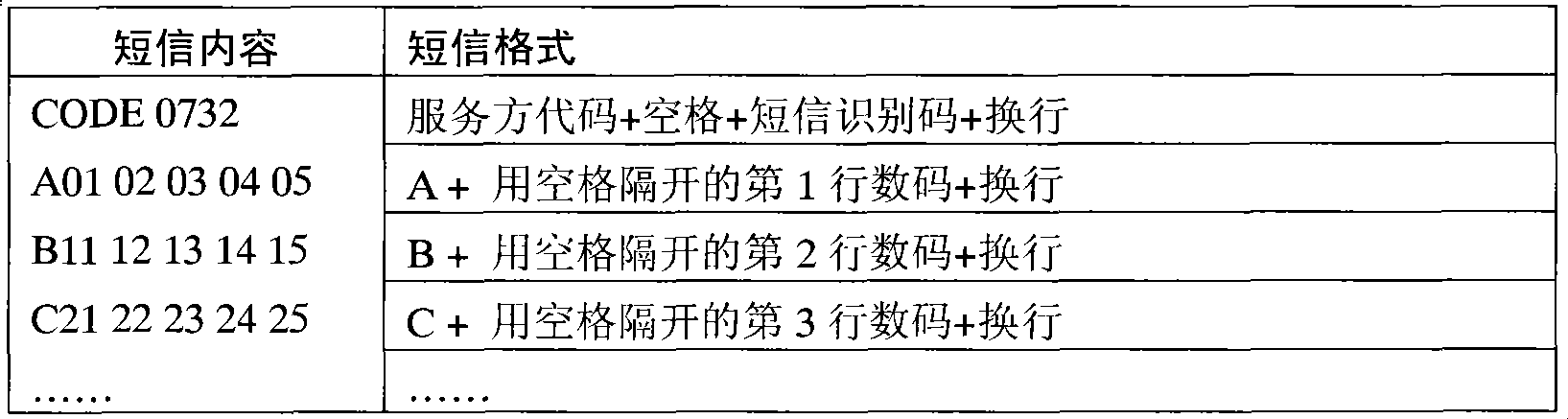
[0028] field data type illustrate password matrix coordinate string VARBINARY The upper 4 bits of each character are the line number, and the lower 4 bits are the column number password matrix number string VARBINARY 0≤ASCII value of each character≤99 Length position value (LP) SMALLINT LP=Len*256+Pos(Len-length, Pos-position)
[0029] Table 1 Data table field description
[0030] 3. After the user registers, bind the account with the mobile phone number, assuming that the relevant value is:
[0031] key value illustrate username username password 123456 server code COMP The uniq...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com