Method for realizing information bypass by using IP Option
A technology for information encapsulation and user identity, applied in transmission systems, digital transmission systems, error prevention/detection using return channels, etc., can solve problems such as message loss, delay, and failure to find NAT entries, etc., and achieve real-time performance Guarantee, the effect of reliability guarantee
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
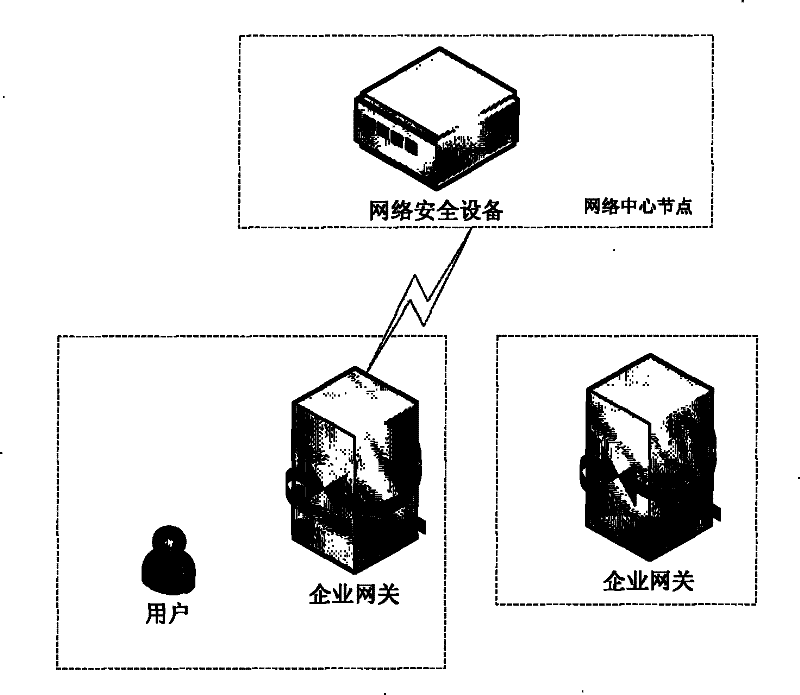
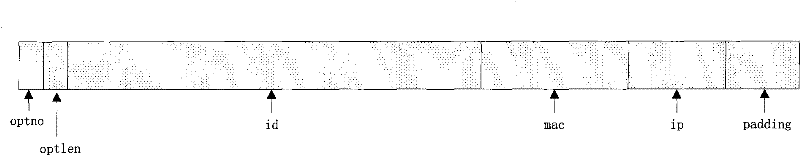
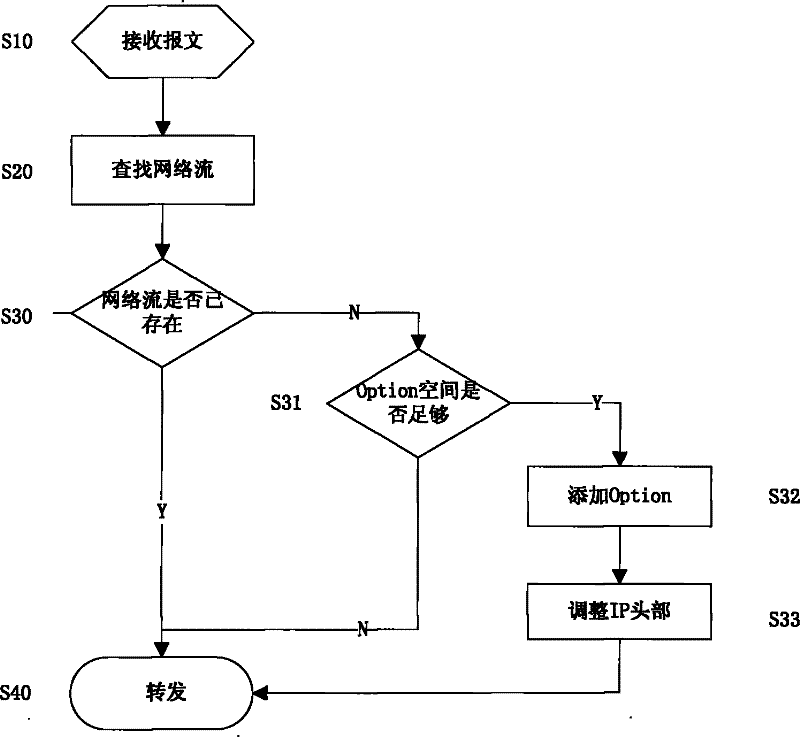
[0027] The method of using IP Option to realize information transparent transmission, the specific process is: 1) Intercept the first message of each network flow on the gateway; 2) Before the message is forwarded, the private information is encapsulated into IP Option, and the IP header of the message is inserted Tail; 3) Adjust the IP header ihl, tot_len, and recalculate the IP header checksum; 4) Forward the message; 5) At the central node of the network, intercept the message, analyze the first message of each network flow, and get private information, and remove the private information from the message, and then forward the message.
[0028] Wherein, the network flow is uniquely defined by the quintuple, and the quintuple refers to: source IP, destination IP, source port, destination port, and transport layer protocol. Transparently transmit private information by modifying the IP header of forwarded packets. Any private information can be carried, such as source IP, sou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com