Intrusion detection method and device thereof in self-organized network
A self-organizing network, intrusion detection technology, applied in the direction of network topology, electrical components, wireless communication, etc., to achieve the effect of improving the detection speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
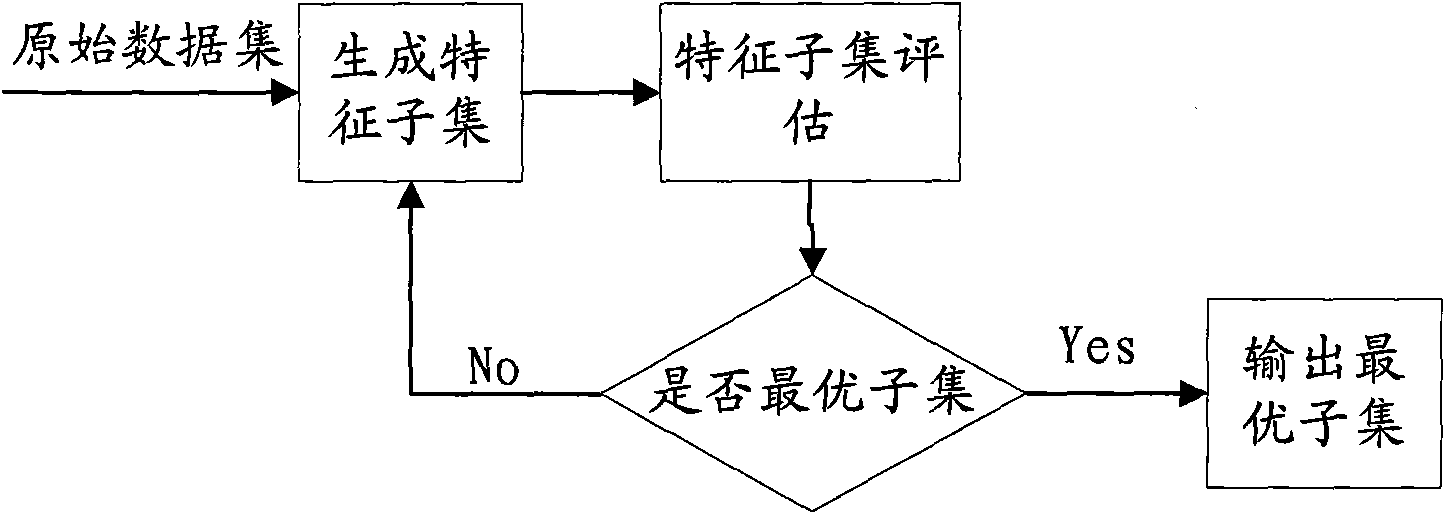
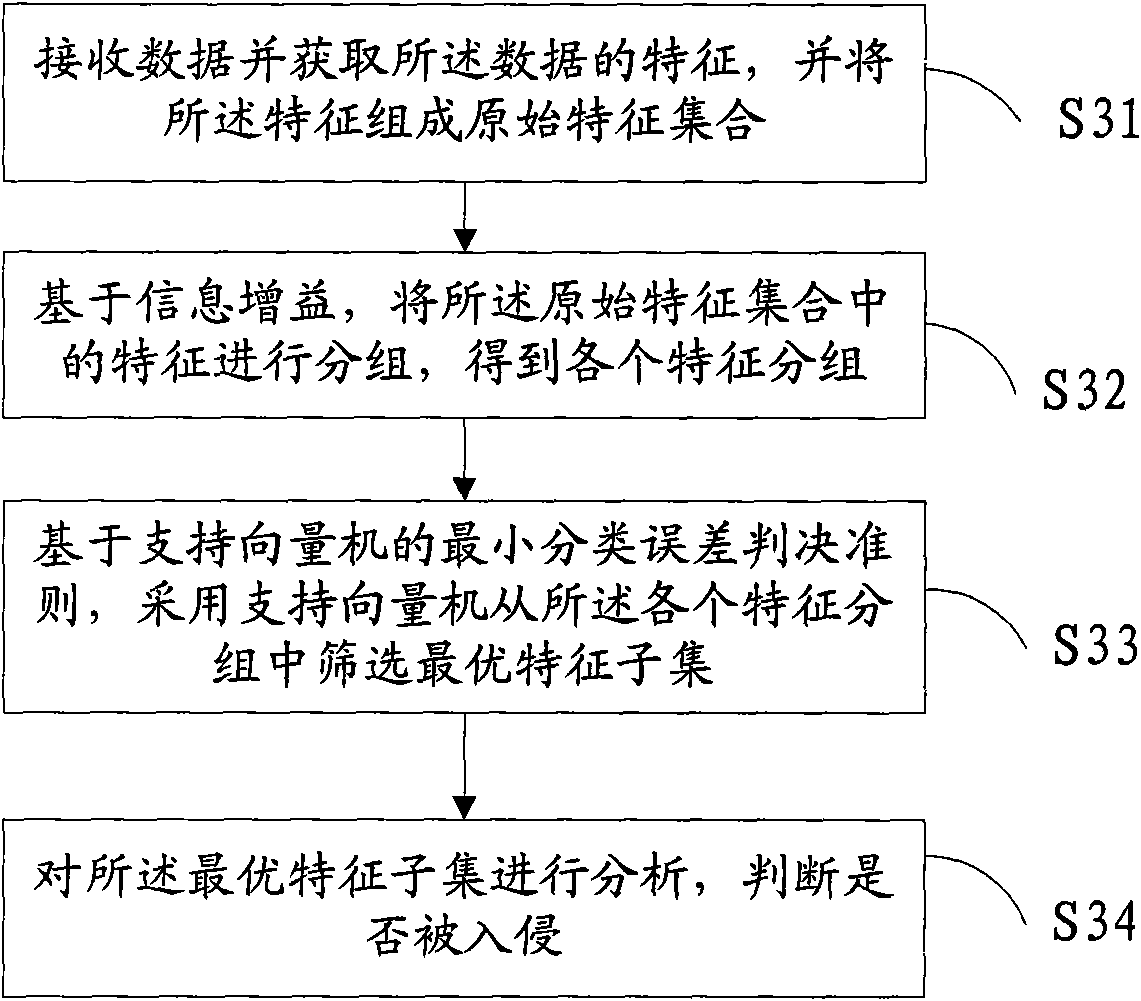
[0036] Such as image 3 As shown, the intrusion detection method in the Ad Hoc network of the embodiment of the present invention comprises:
[0037] S31. Receive data and acquire features of the data, and form the features into an original feature set;
[0038] S32. Based on the information gain, group the features in the original feature set to obtain each feature group;
[0039] S33. Based on the minimum classification error decision criterion of the support vector machine, use the support vector machine to select the optimal feature subset from each feature group;
[0040] S34. Analyze the optimal feature subset to determine whether it has been invaded.
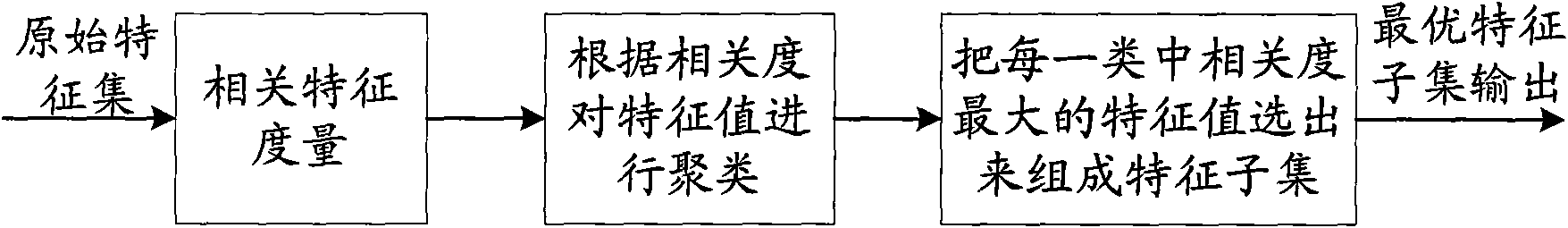
[0041] For example, the situation of the ad hoc network being invaded includes: whether the node is intercepted, whether the key held by the enemy node pretends to be a legitimate node and joins the network, etc. Optionally, step S34 may refer to the process of selecting and obtaining a feature subset through a genetic...
Embodiment 2
[0086] Such as Figure 6 As shown, the embodiment of the present invention provides an intrusion detection device 600 in an Ad Hoc network, including:
[0087] The feature grouping unit 601 is configured to receive data and acquire features of the data, form the features into an original feature set, group the features in the original feature set based on information gain, and send the obtained feature groups to To the optimal feature subset screening unit 602;
[0088] The optimal feature subset screening unit 602 is configured to receive the feature groups sent by the feature grouping unit 601, and use a support vector machine to filter from the feature groups based on the minimum classification error decision criterion of the support vector machine. An optimal feature subset, and sending the optimal feature subset to the detection unit 603;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com