Implementation method of three-state content addressable memory and device
A technology for addressing memory and an implementation method, which is applied in the field of three-state content addressable memory implementation, and can solve the problems that a single chip is difficult to achieve high capacity, increased complexity, and increased cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
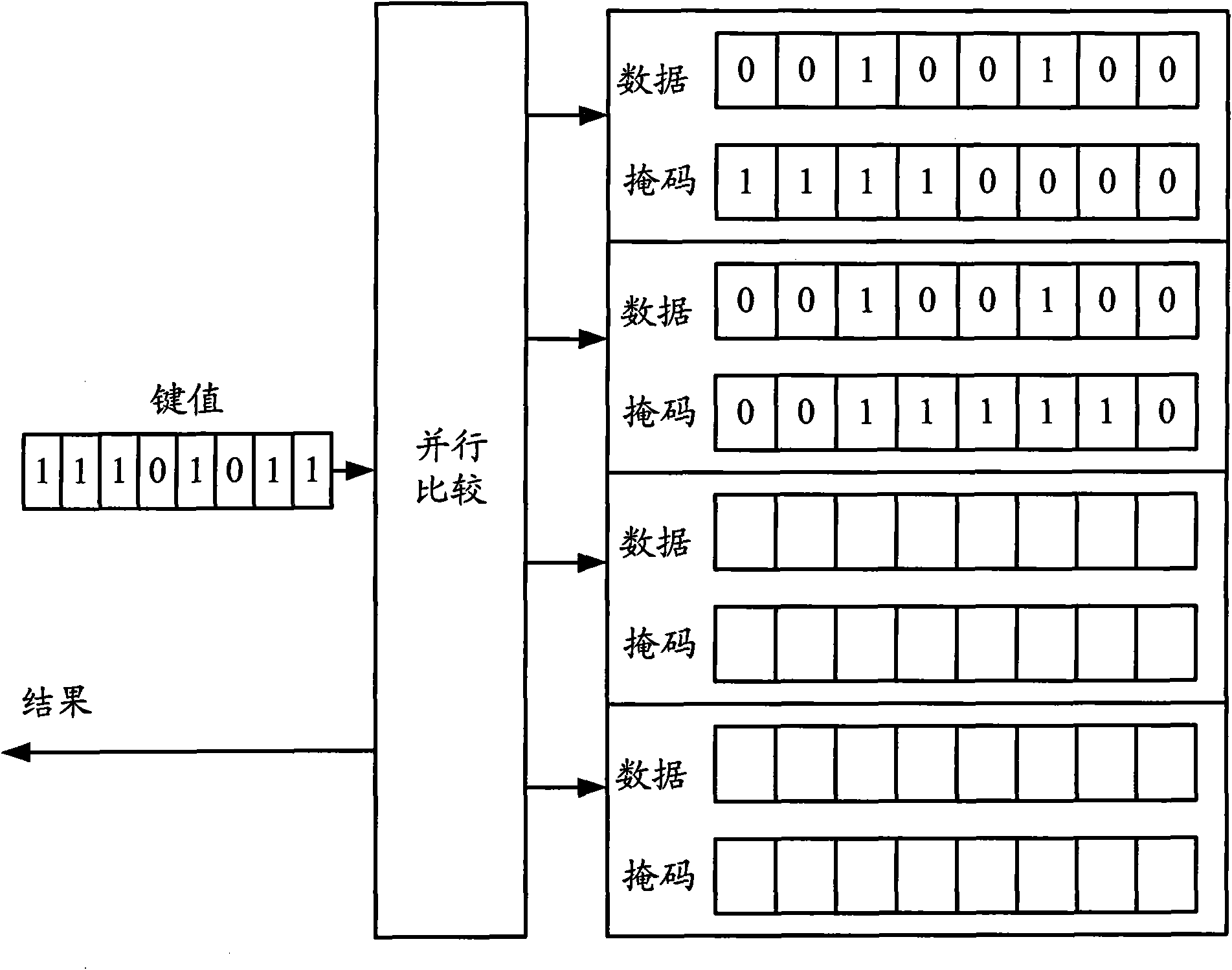
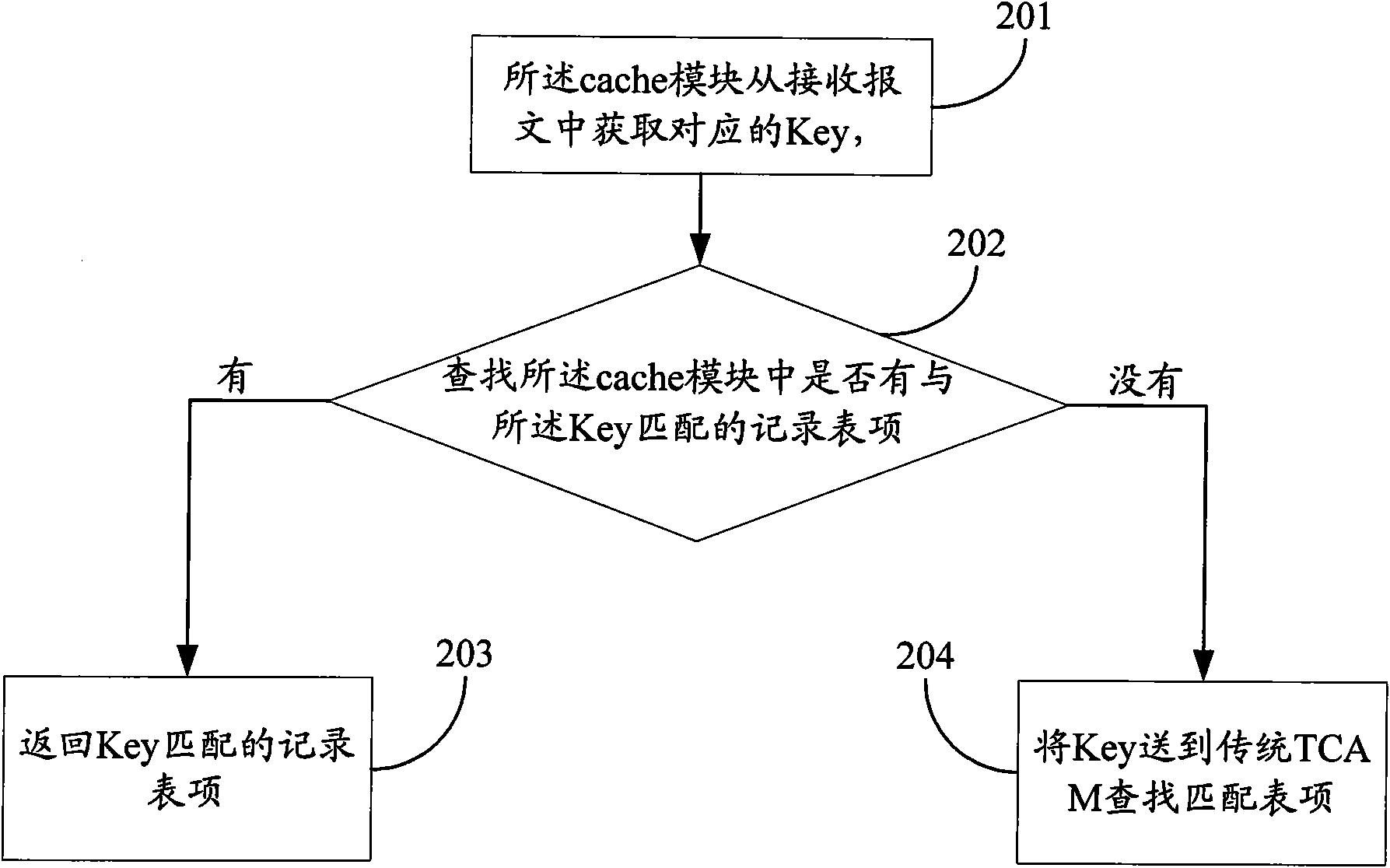
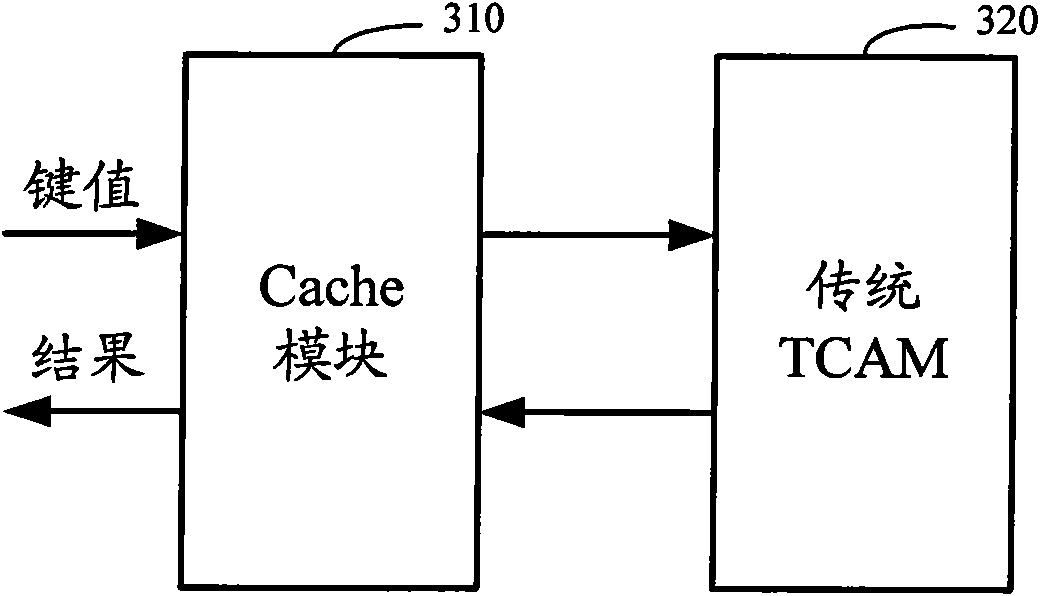
[0041] The invention reduces the design difficulty of the traditional TCAM by adding a cache module. High-end routers generally forward on a packet-by-packet basis, that is to say, each packet checks routing or ACL; in fact, packets belonging to the same connection have the same attributes, such as 5-tuples (source IP address, destination IP address, source The port number, destination port, protocol number) are the same, TOS (Type-Of-Service, service type) is the same, and the key value is obtained through the above attributes. For the same attribute message, the key value is the same, and the same key value is checked The result of routing or information flow is the same.
[0042] If you consider that the same connection messages get the same results from the traditional TCAM check, assuming that there are 10 messages for each connection, the first message cannot find matching content in the cache module, so the cache module sends the Key Traditional TCAM, after TCAM finds a m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com