Sequence diagram defect inspection method based on safety knowledge base
A technology of security knowledge and defect detection, applied in the direction of program control device, software testing/debugging, etc., can solve problems such as being attacked, achieve the effects of eliminating ambiguity, facilitating operation and processing, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
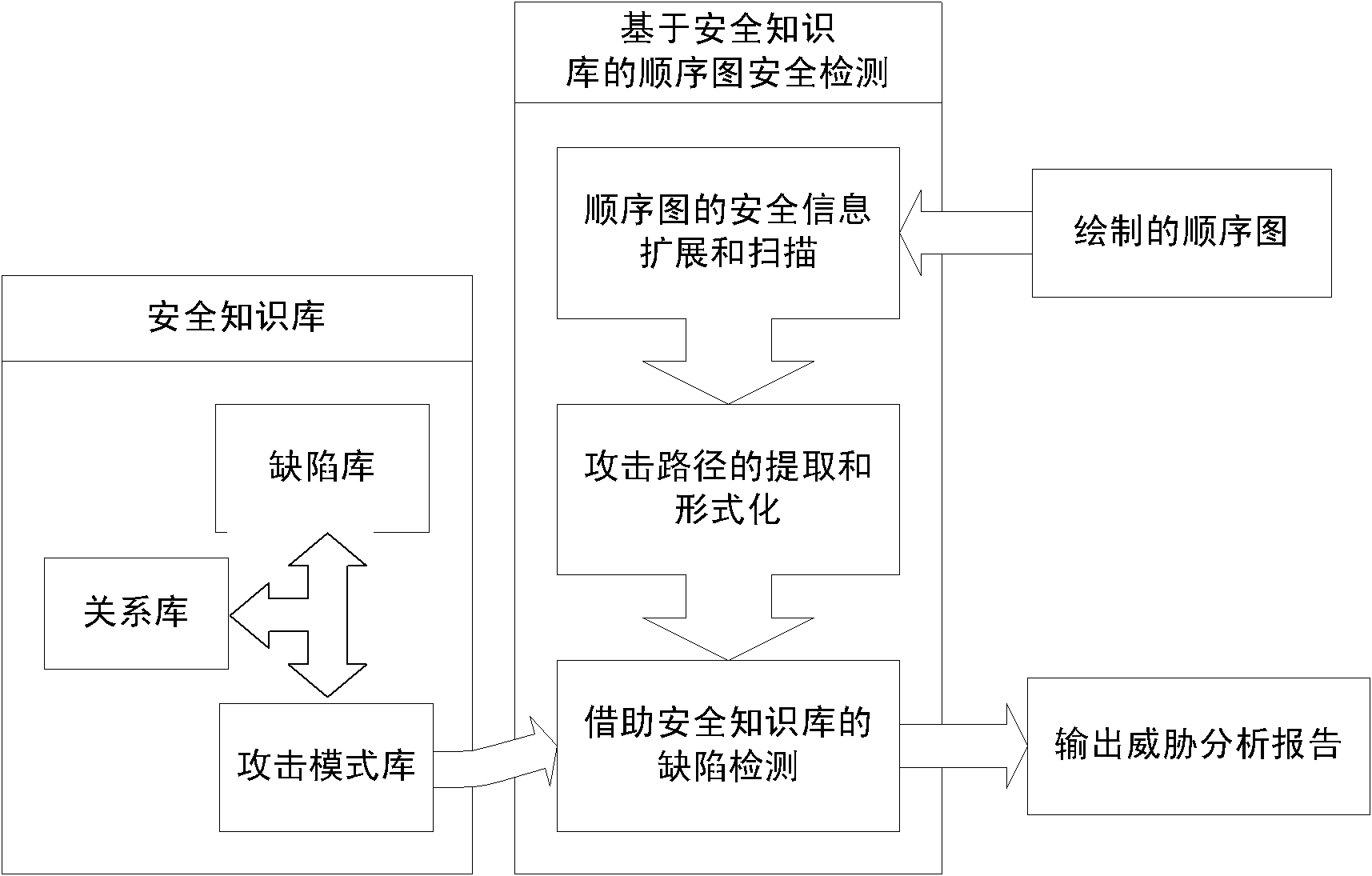
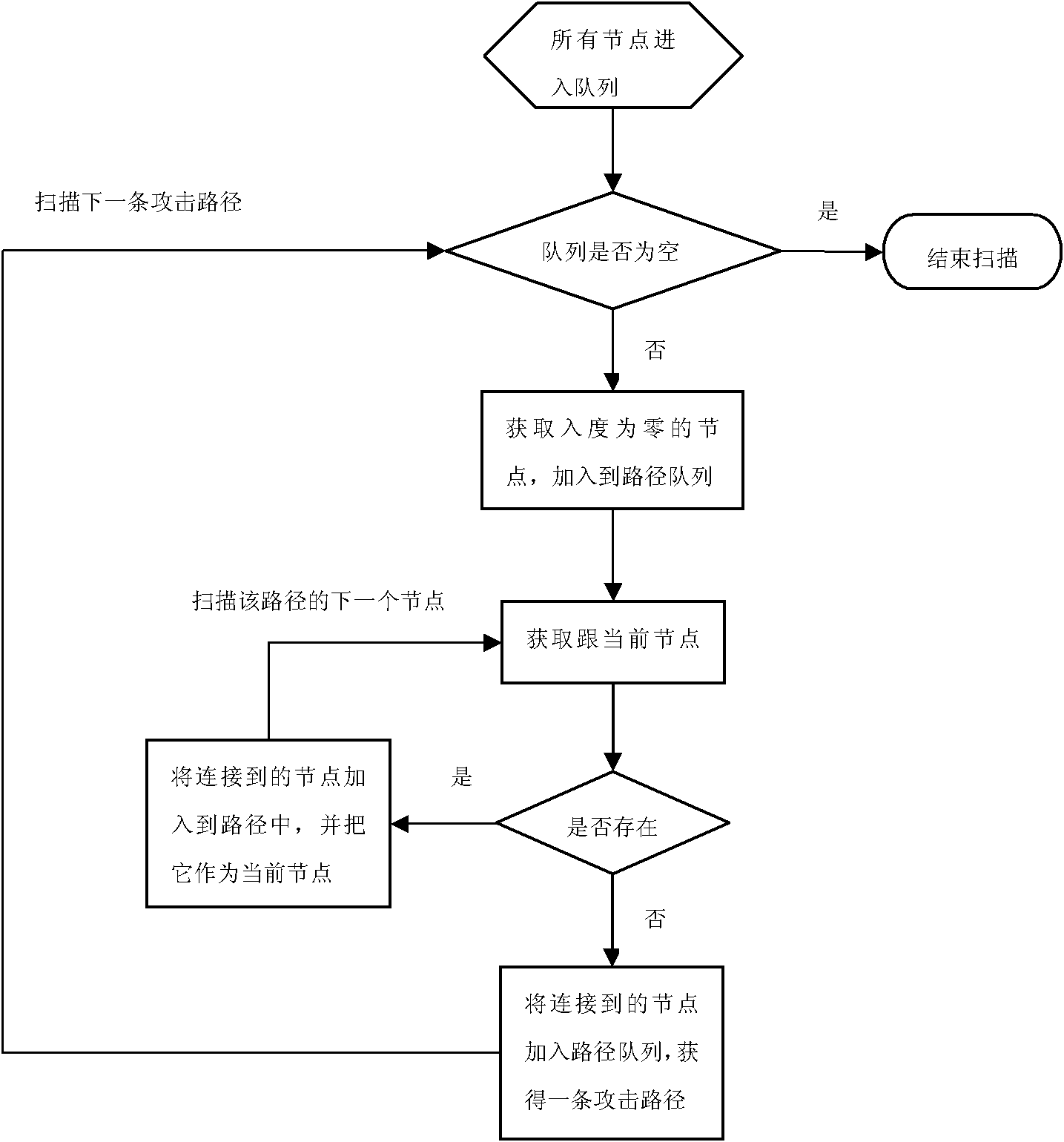
[0025] Aiming at the above objectives, the method proposed by the present invention is roughly divided into four parts, namely the security extension of the sequence diagram, the scanning and modeling of the sequence diagram, the extraction of the attack path and the defect detection with the aid of the security knowledge base. The overall structure diagram is attached figure 1 shown.
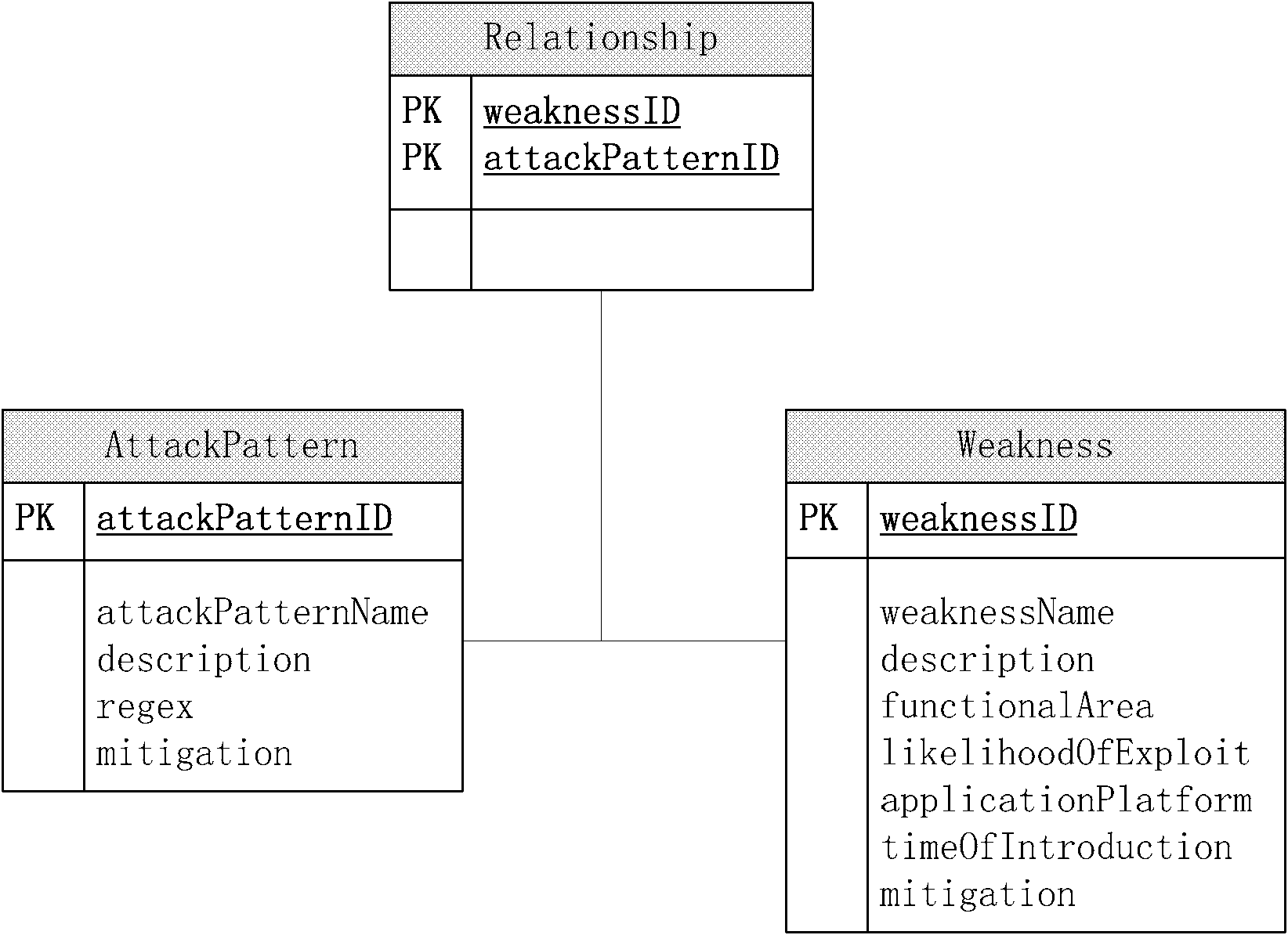
[0026] 1. Security extension of the sequence diagram: Through the UML extension mechanism, some security attributes are added to the objects and messages in the sequence diagram. These properties can be taken from the system component diagram of M. Gegick's doctoral thesis "Analyzing Security Attacks to Generate Signatures from Vulnerable Architectural Patterns". Security attributes are the abstraction and classification of software system components, which can abstract and formalize the components in the sequence diagram. For example, Apache can be abstracted as a Web server, and MySQL can b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com