Text message security technology
A technology of text information and security technology, which is applied in the field of text information security, can solve the problems of encryption, interception and cracking of text information in the entire file, and time-consuming problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
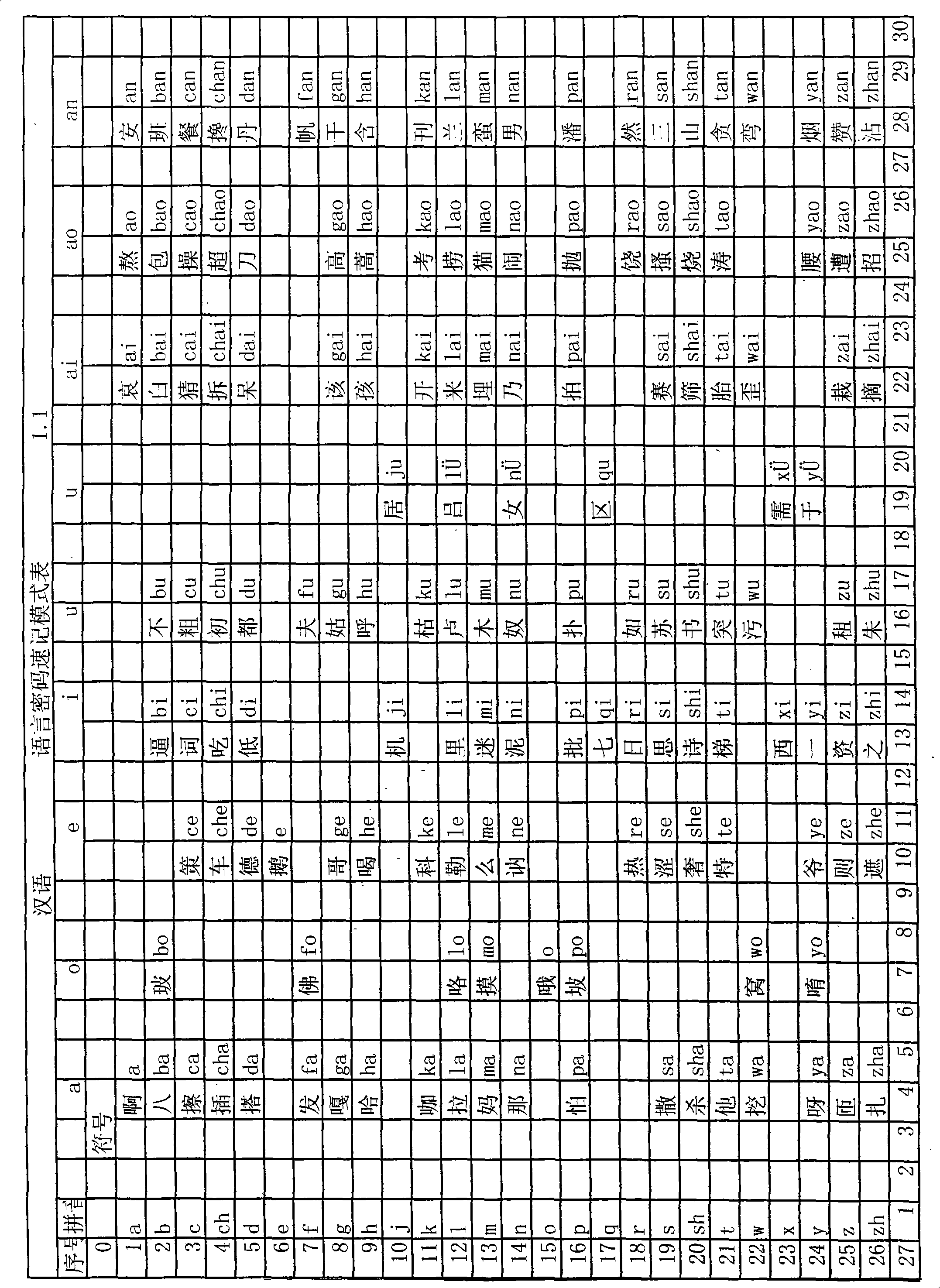
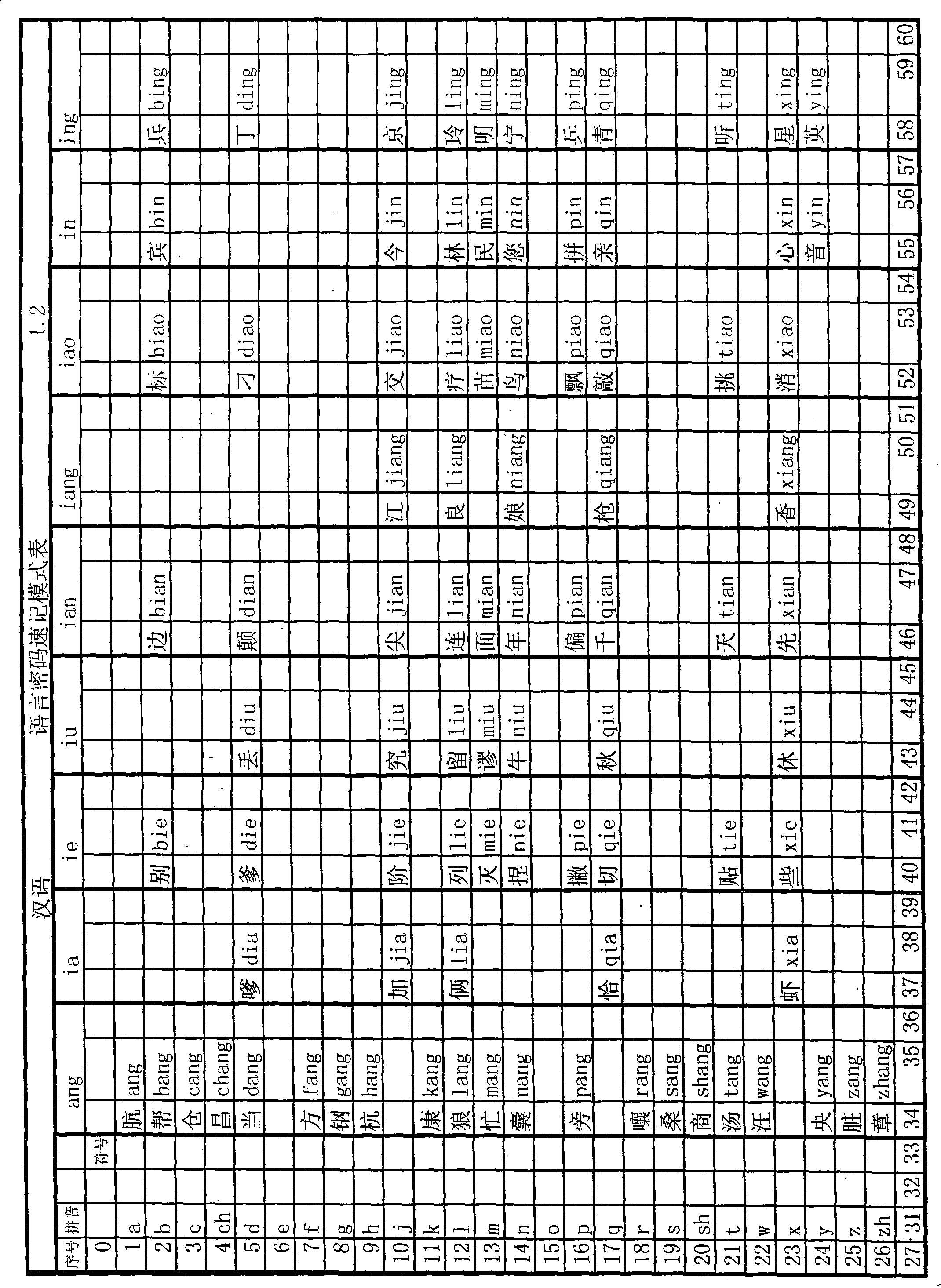
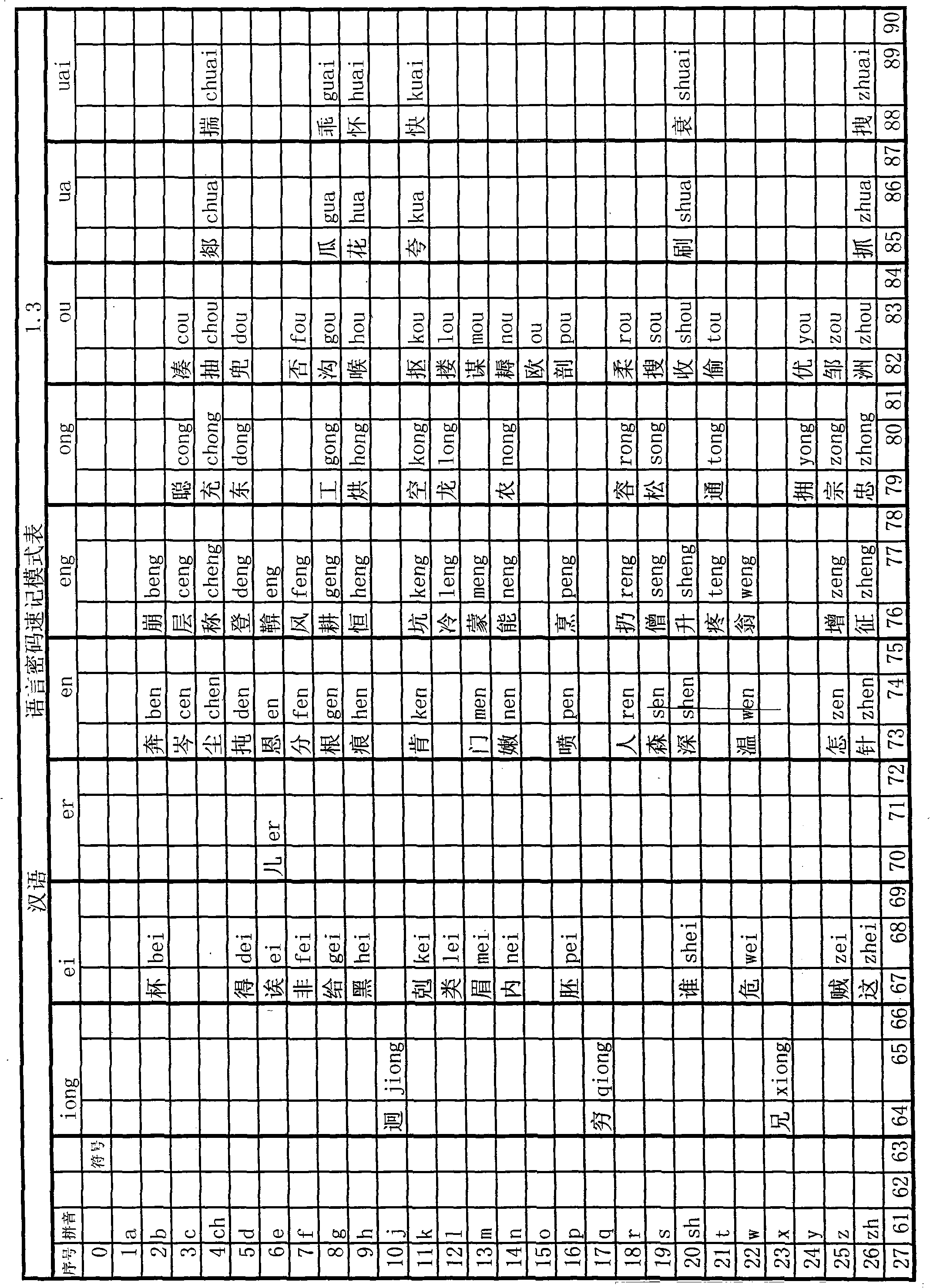
[0005] This kind of text information security technology requires human translation, and can also be made into translation software for translation on electronic devices. This kind of password uses the initials and vowels in Chinese Pinyin, replaces the initials with 26 simple characters, and replaces the vowels with 34 simple characters, and arranges the substitute symbols in rows and columns corresponding to the initials and vowels. In summary, select the password mode or change the password mode and mark it in the form. The selection of the password mode or the change password mode can also be directly input to the computer or recorded on paper. For English, you can use 26 simple characters to replace the 26 letters of English, and then arrange the table in rows and columns according to the corresponding symbols and English letters. Select the password mode or change the password mode and mark it in the table. Select the password mode or change the password mode can also be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com