Growing hierarchical self-organizing maps (GHSOM)-based intrusion detection method for neural network
A self-organizing map and neural network technology, applied in the field of computer network information security, can solve the problems of increasing system overhead, not accurately reflecting the characteristics of attack behavior, and a large number of neurons
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
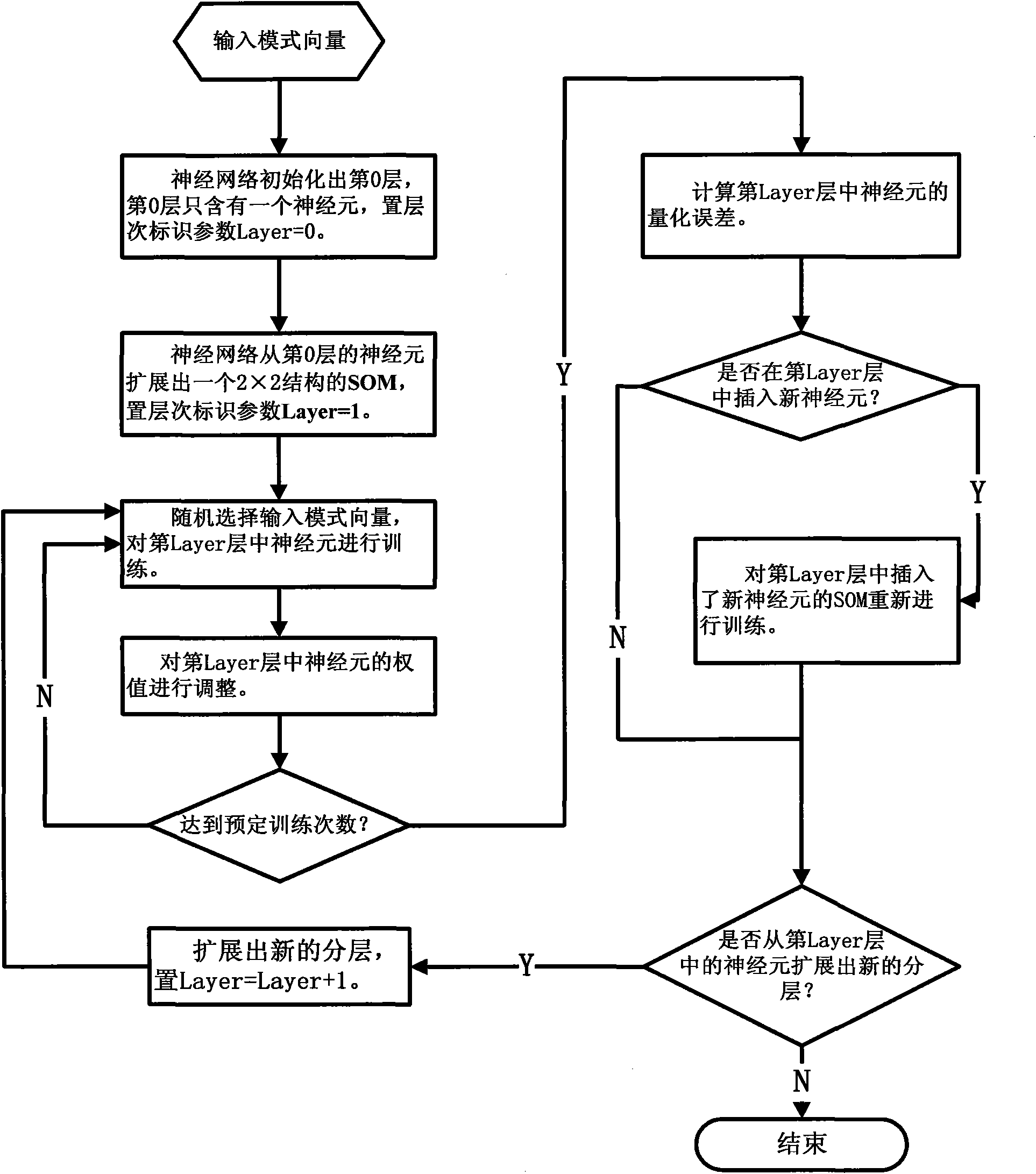
[0044] The present invention is described in further detail below in conjunction with accompanying drawing:
[0045] The intrusion detection system of the present invention consists of two parts: offline training of the neural network model and online detection based on the neural network model. The system collects sample data from the network as a training sample data set for offline training, and obtains an intrusion detection model for online detection. The offline training process applies the neural network training algorithm to train the neural network model based on the training data set. The trained neural network model can be applied to online network intrusion detection. Obviously, the neural network training algorithm is the core technology of the intrusion detection system based on the neural network.
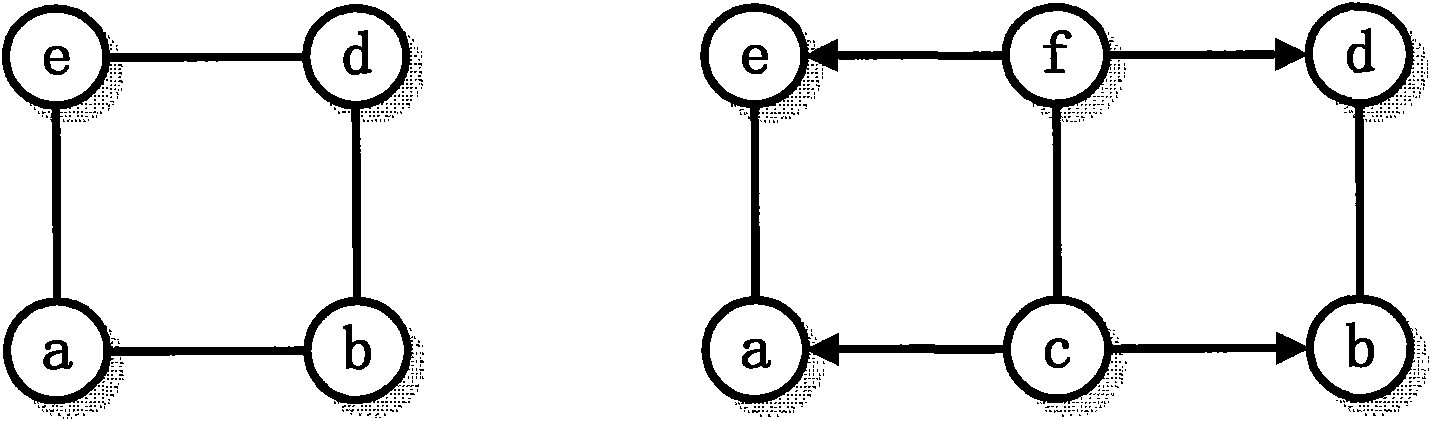
[0046] Below we will focus on how to improve the GHSOM training method in combination with the training process. Then briefly introduce the process and method of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com