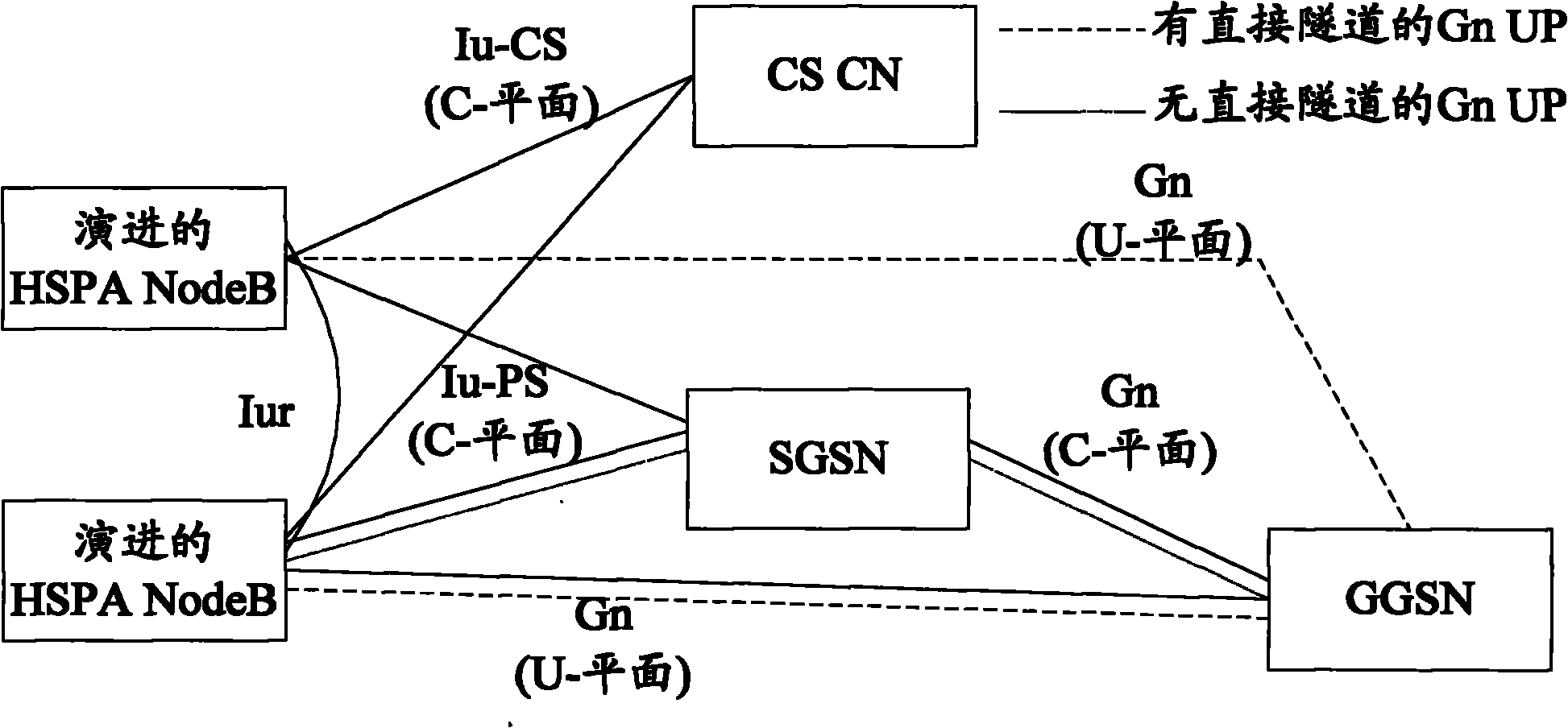
Method and system for creating secret key as interconnecting GERAN with enhanced UTRAN
An interconnection, intermediate key technology, applied in wireless communication, wireless network protocols, electrical components, etc., can solve the problem of insecurity, security is not particularly high
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
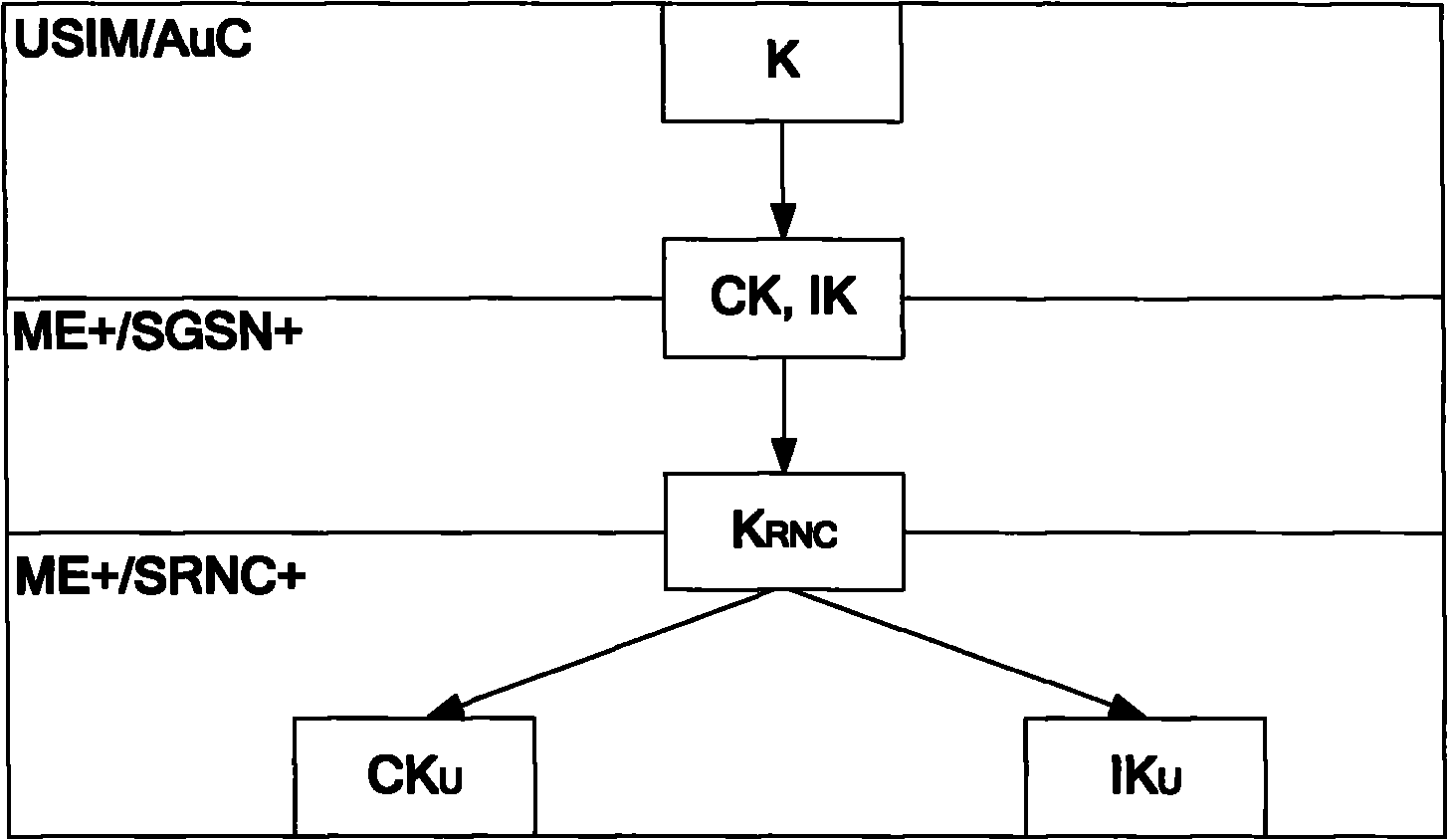
[0091] This embodiment illustrates an example of the air interface key management process when the terminal moves from GERAN to enhanced UTRAN. In this embodiment, the target SGSN+ is responsible for deriving K RNC , the target RNC+ is responsible for deriving the enhanced key CK U and IK U ,Such as Figure 3a with Figure 4 shown, including the following steps:
[0092] Step 101, the source BSC decides to switch from the GERAN network to the target enhanced UTRAN network;
[0093] Step 102, the source BSC sends a handover requirement message to the source SGSN;
[0094] Step 103, the source SGSN sends a handover message to the target SGSN+, if the source SGSN is R99+SGSN, the message carries security-related parameters CK / IK; if the source SGSN is R98-SGSN, the message carries security-related parameters Kc;
[0095] Step 104, if the target SGSN supports the enhanced security function of HSPA+, that is: if the target SGSN is SGSN+, then the target SGSN+ derives the inter...
Embodiment 2
[0123] This embodiment describes an example of an enhanced air interface key establishment process when a terminal moves from GERAN to enhanced UTRAN. The difference between this embodiment and Example 1 is that: the source SGSN and the target SGSN+ are the same SGSN, and both are enhanced SGSNs, that is, SGSN+. Such as Figure 5 shown, including the following steps:
[0124] All steps are basically the same as in Embodiment 1, except that the processing in the source SGSN and the target SGSN+ in Embodiment 1 is in the SGSN+ of this embodiment, and there is no signaling interaction between the source SGSN and the target SGSN+ in Embodiment 1 .
Embodiment 3
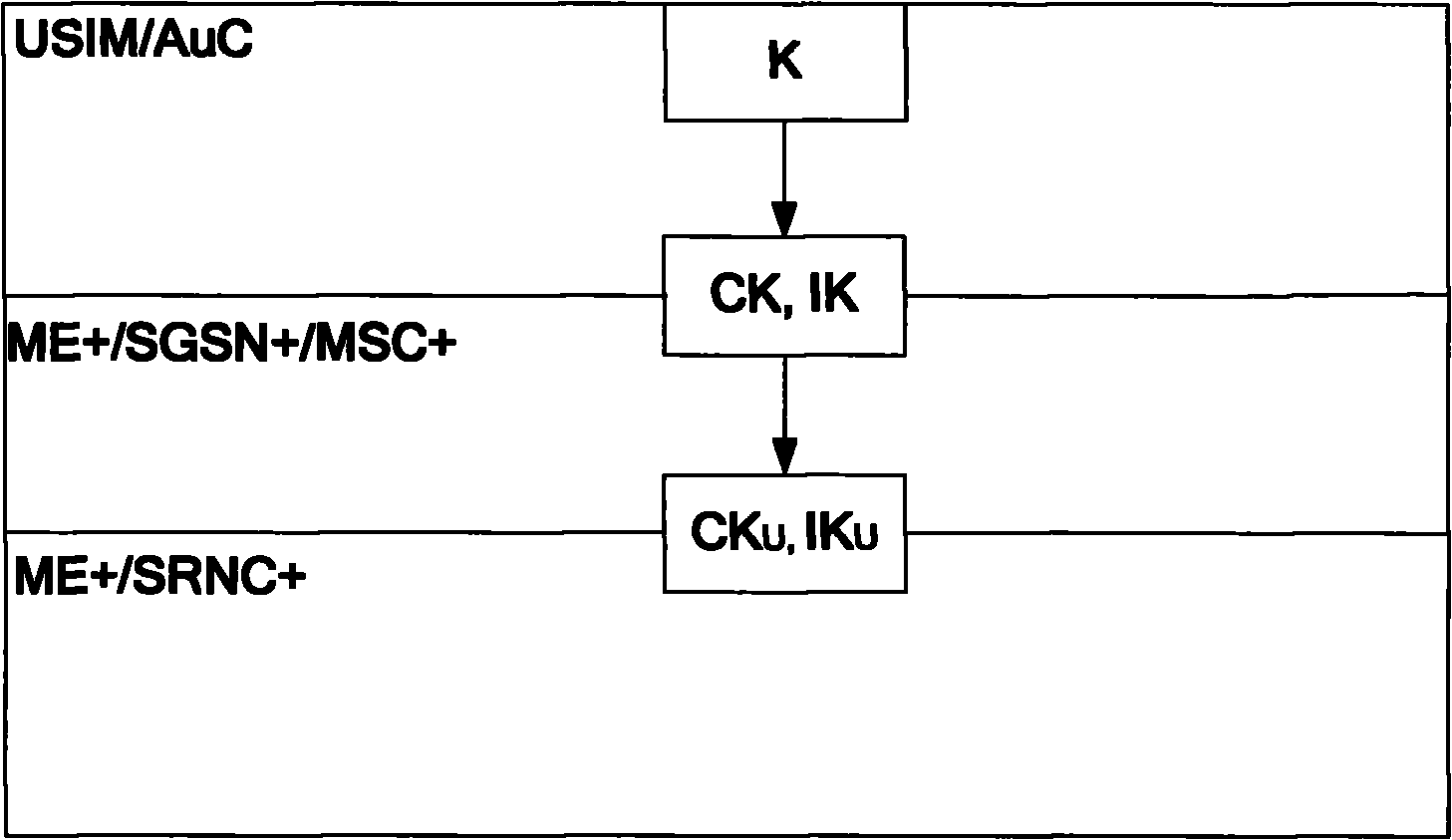
[0126] This embodiment describes an example of an enhanced air interface key establishment process when a terminal moves from GERAN to enhanced UTRAN. The difference between this embodiment and Example 1 is: the enhanced air interface integrity key IK U and air interface encryption key CK U Generated at the target SGSN+, and sent to the target RNC+ in the relocation request message through the target SGSN+. Such as Image 6 shown, including the following steps:
[0127] Steps 301-303 are the same as Steps 101-103 of Embodiment 1;
[0128] Step 304, if the target SGSN supports enhanced security functions, that is: if the target SGSN is SGSN+, then:
[0129] The target SGSN+ derives K from the received keys IK and CK RNC ; If the target SGSN+ receives Kc, then the target SGSN+ first derives IK / CK based on Kc, and then derives K based on the IK / CK RNC ;
[0130] Then according to the intermediate key K RNC Derivation of enhanced air interface integrity key IK U and / or ai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com