Method and device for actively finding malicious code control end
A malicious code, active discovery technology, applied in the field of information security, can solve the problems of huge time cost, high time cost, efficiency consideration and optimization of scanning, etc., to achieve the effect of important information security guarantee and avoid time cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
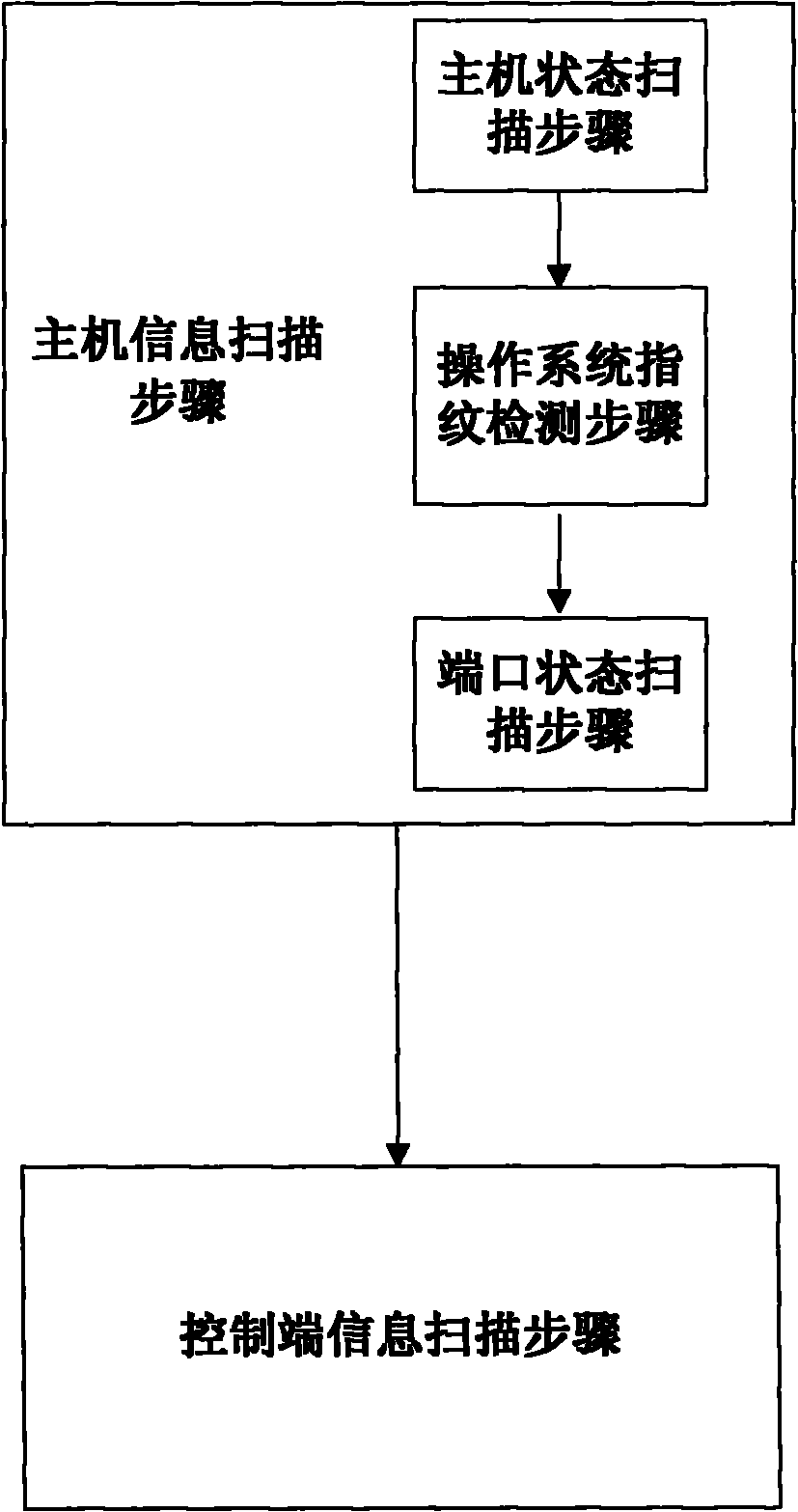
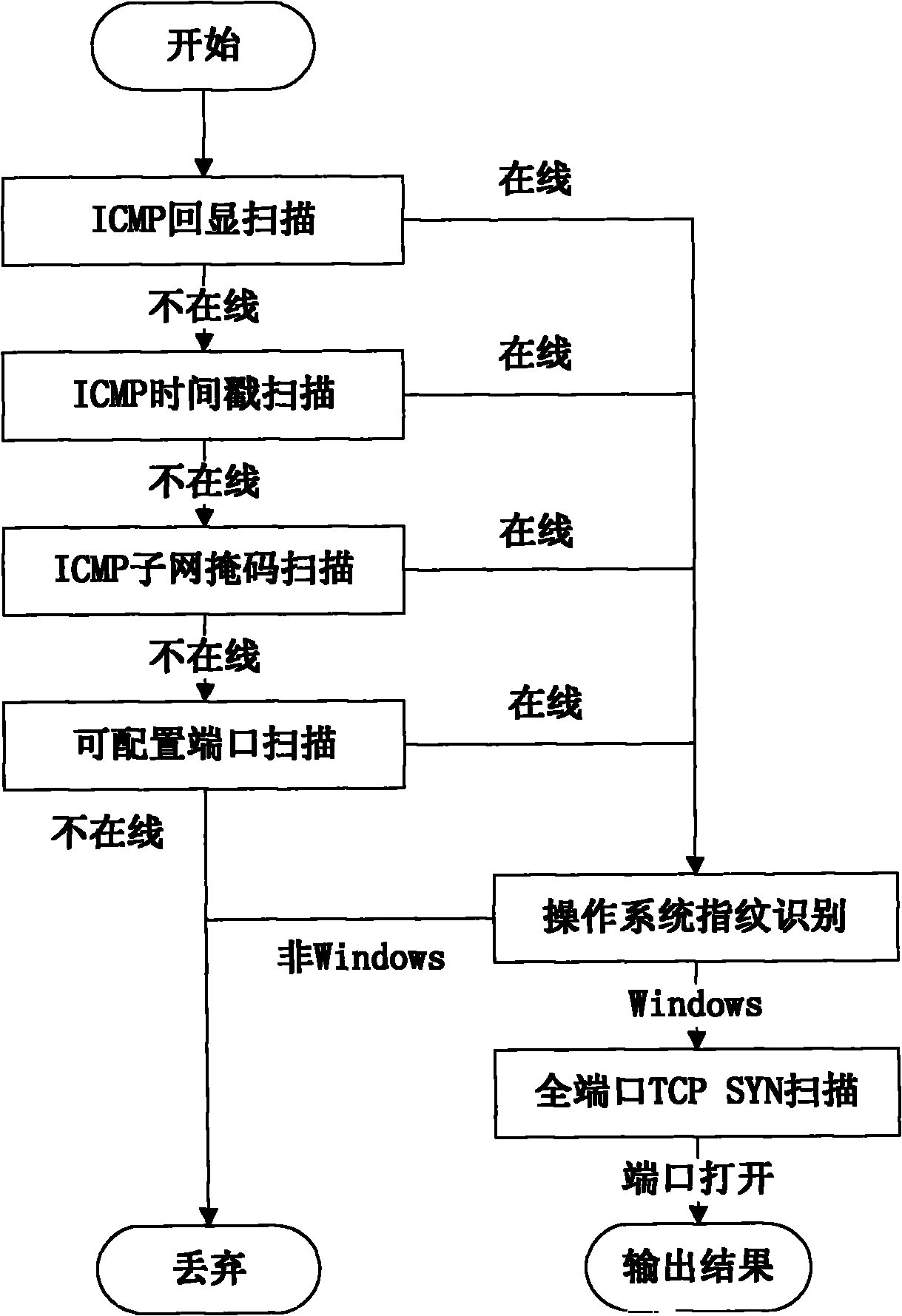
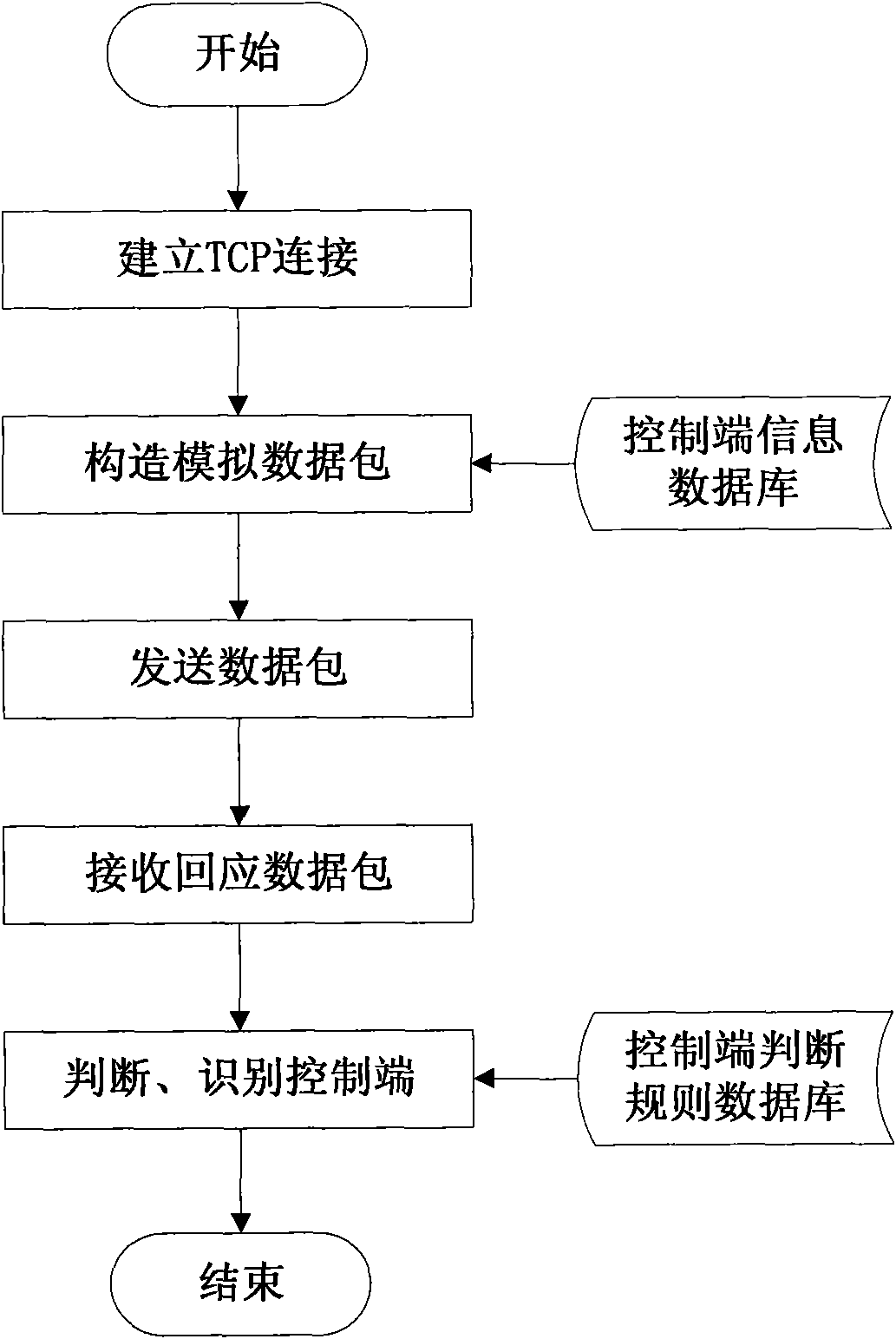
[0063] The present invention proposes a solution for the active discovery of malicious code control terminals, namely: actively scan hosts in the Internet to obtain their online status, open ports and operating system types; The port establishes a network connection to simulate the network behavior of the controlled terminal; compares the communication data returned by the host with the network behavior characteristics of the control terminal, and judges whether there is a control terminal in the host and what kind of control terminal it is based on the comparison results, so as to finally realize active discovery and identify the console.
[0064] figure 1 It is a schematic flowchart of the method for actively discovering malicious code control terminals of the present invention. As shown, the method for discovering malicious code c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com