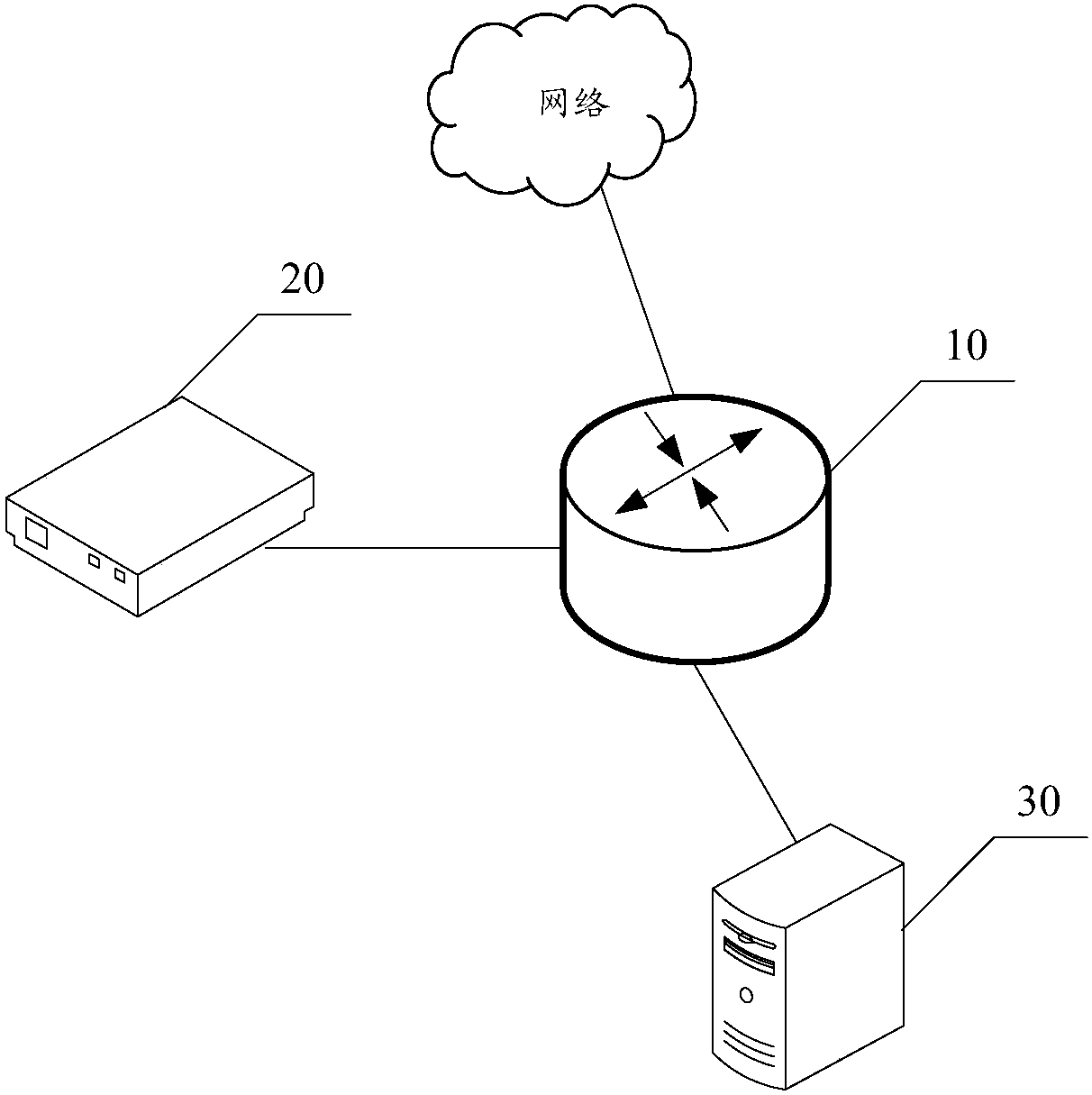
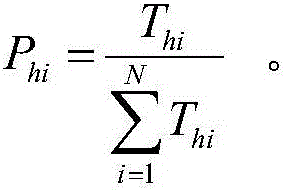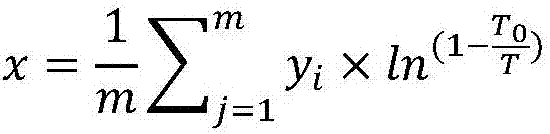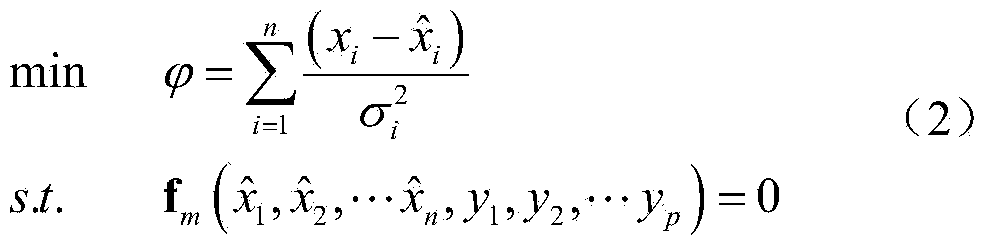Patents
Literature
101results about How to "Effective identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
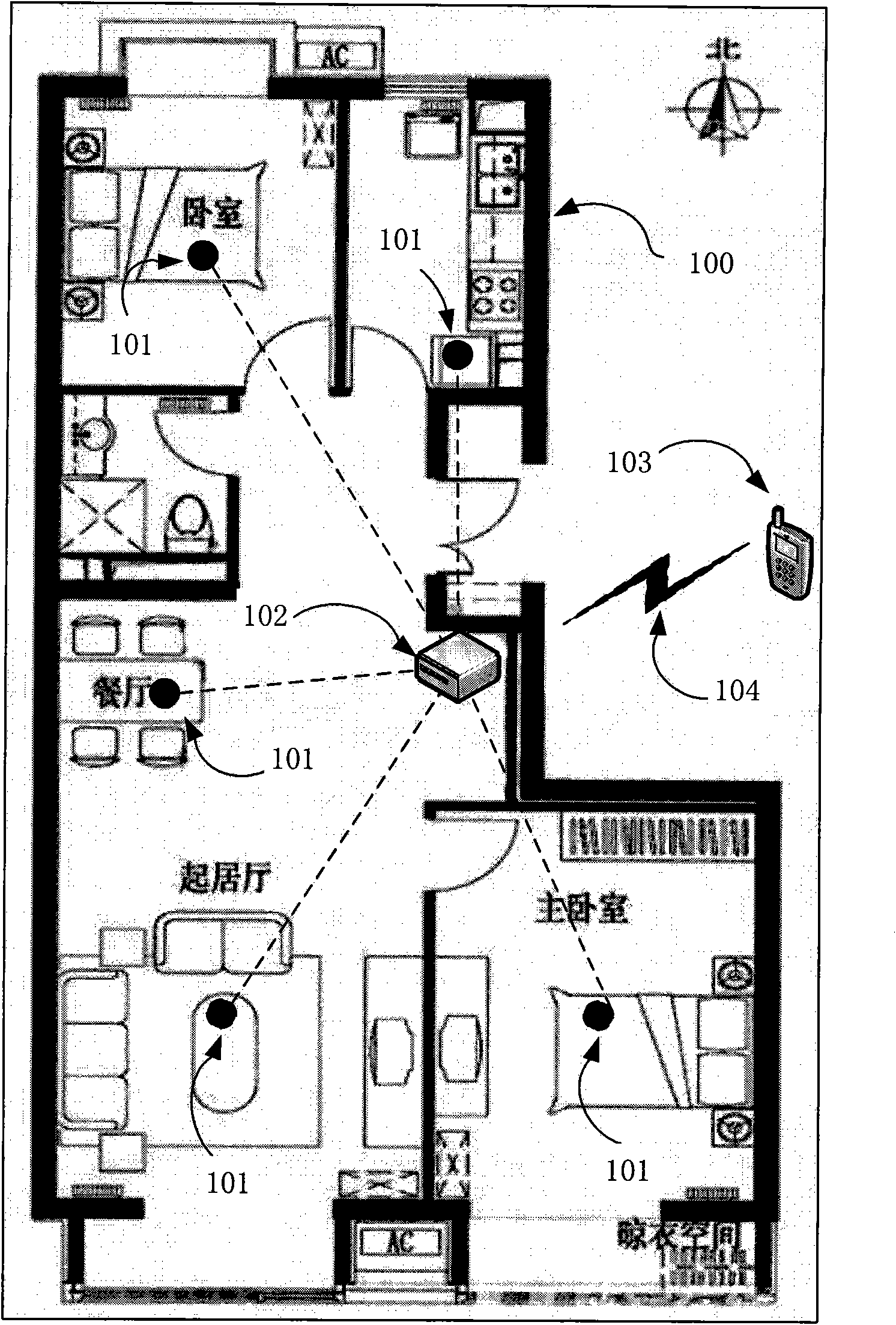
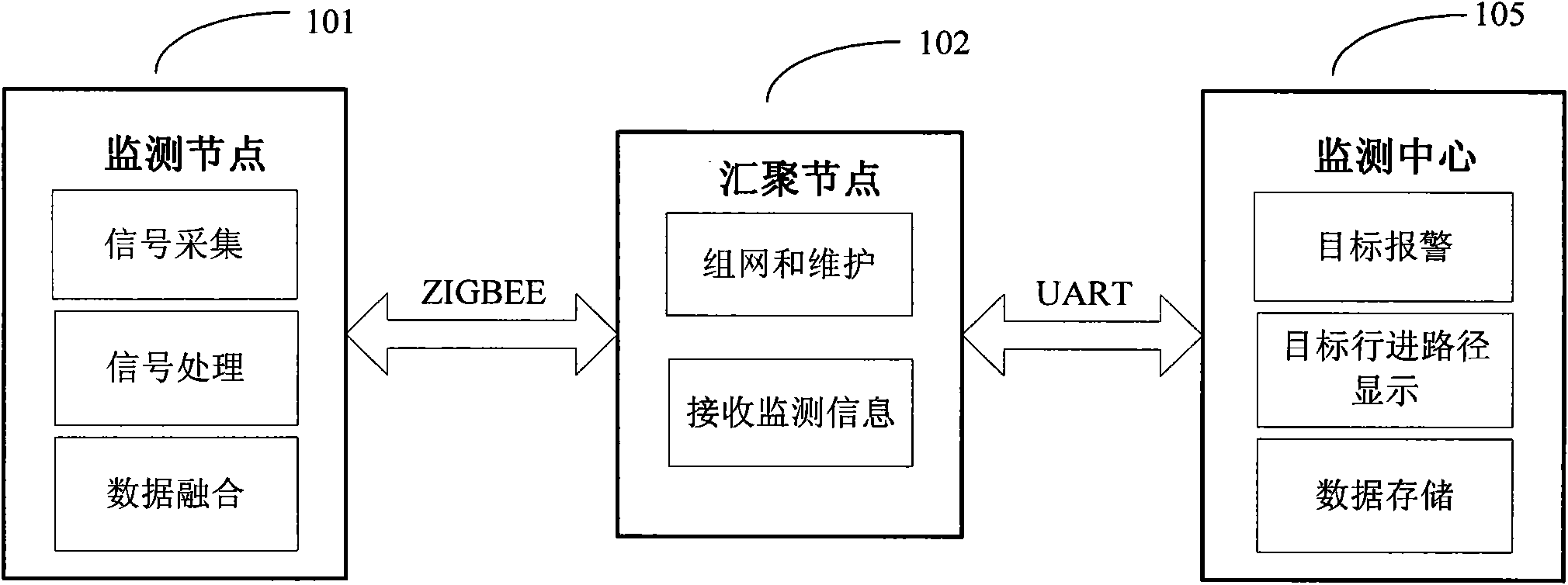
System for monitoring intrusion on basis of wireless sensor network
InactiveCN101872536AEffective monitoringEffective identificationEnergy efficient ICTNetwork topologiesVideo monitoringCivil security
The invention, which is applicable to civil security and surveillance and military intrusion detection, relates to a wireless network system for monitoring, identifying and judging the pathway of an intruding target by setting up a plurality of nodes. The intruding target can be located, identified and tracked by carrying out the extraction, analysis and data integration on the signal characteristic quantity of the sensors at each monitoring node, moreover, the function for a user to set sensitive areas is served, so that various alarm signals can be sent according to the closeness of the intruding target to the sensitive areas. Additionally, a monitoring sensor at the monitoring node is used for generating sleeping and waking-up signals on a real-time basis, thus achieving the deep sleeping and waking of the processor and the communication module and achieving the purpose of saving the energy of the monitoring nodes and guaranteeing that the target intruding the monitoring area can be reliably monitored at the same time. The invention has the characteristics of low cost, low power consumption, flexible arrangement and high applicability and overcomes the defects that the conventional video monitoring method for monitoring the intrusion has complex installation, poor concealment, vulnerable circuit and limited monitoring range and requires artificial event discrimination.
Owner:BEIHANG UNIV
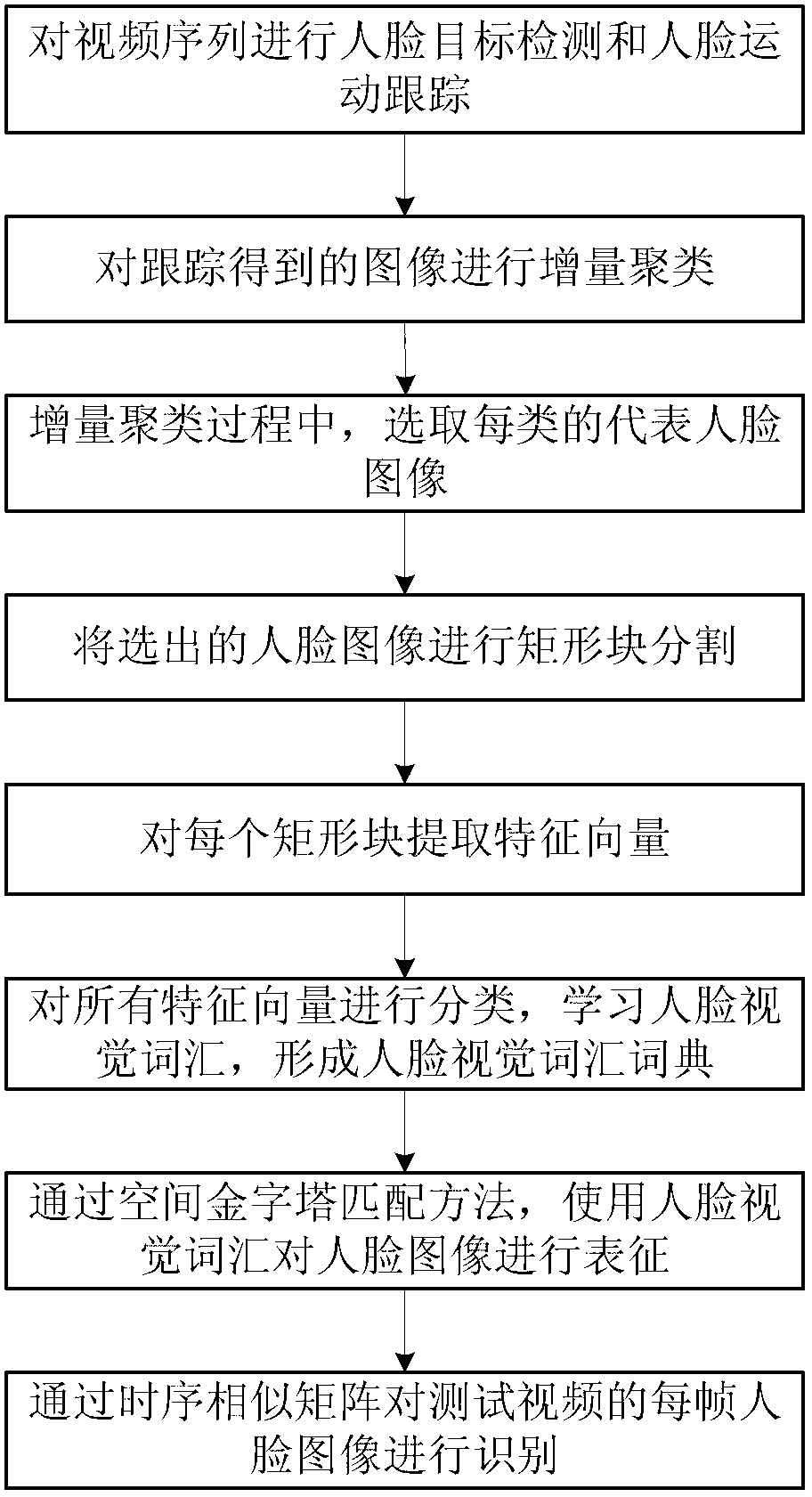
Method for identifying faces in videos based on incremental learning of face partitioning visual representations
InactiveCN103279768AEfficient automatic detectionFacilitates automatic detectionCharacter and pattern recognitionIncremental learningAdaboost algorithm
The invention provides a method for identifying faces in videos based on incremental learning of face partitioning visual representations and belongs to the field of pattern recognition. According to the method, an Adaboost algorithm is used for detecting frontal face images in a first frame of the face videos, a Camshift algorithm is used for tracking, all face images are obtained, in the process of reading the face images in the videos, incremental cluttering is carried out on the face images, and a representative image is selected from each kind of face images; the representative images are processed, and a visual dictionary based on the piece visual representations is learnt; the visual dictionary is used for carrying out the representations on the face images; finally, according to similar matrices, the videos composed of the face images are identified. According to the method, an identification rate and robustness of the video faces can be improved under the state that illumination, postures and tracking results are not ideal. The faces in the videos can be detected, tracked and identified effectively, conveniently and automatically.
Owner:BEIHANG UNIV
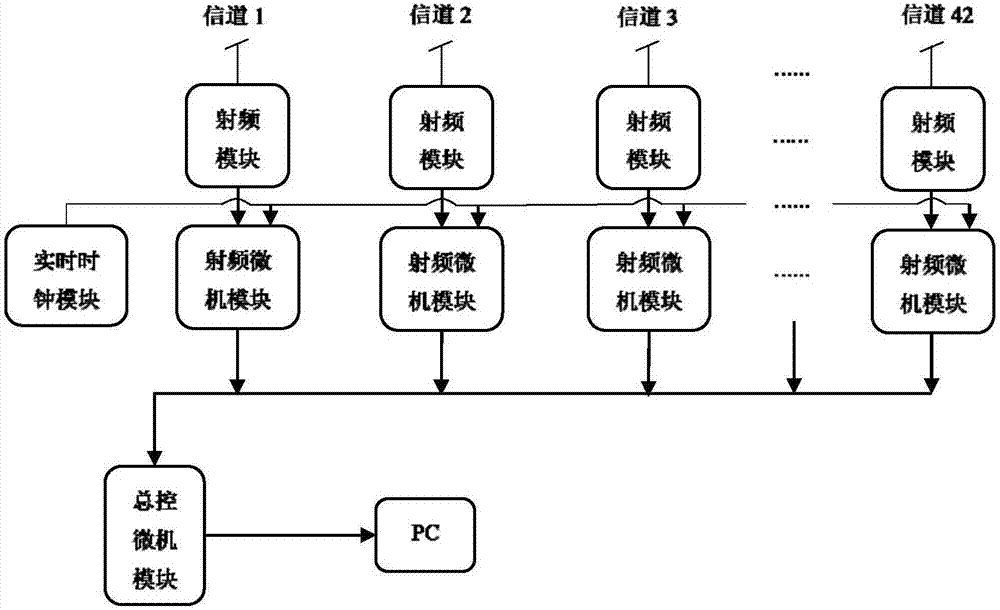
Radio frequency channel parallel detecting device and method for unmanned aerial vehicle
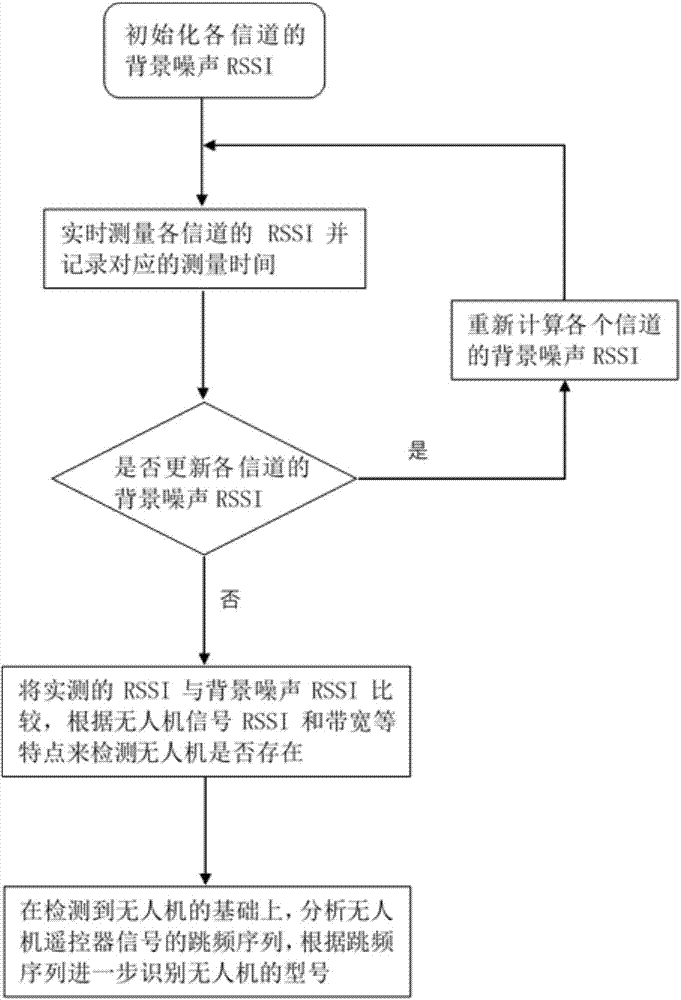
ActiveCN106877947AEffective detectionEffective identificationPropogation channels monitoringMicrocomputerReal-time clock
The invention discloses a radio frequency channel parallel detecting device and method for an unmanned aerial vehicle. The device comprises a number of radio frequency modules, a number of radio frequency microcomputer modules, a general control microcomputer module and a real time clock module. The device divides the common 2.4GHz communication band of the unmanned aerial vehicle into 42 channels, and then measures the RSSI and time of each channel in parallel. According to the measurement result, the difference between an unmanned aerial vehicle signal and the RSSI of the background noise and the bandwidth characteristic of the unmanned aerial vehicle signal are used to detect the unmanned aerial vehicle, wherein the unmanned aerial vehicle signal mainly comprises an image transmission signal and a remote control signal. In addition, the device can detect the frequency hopping sequence of the remote control signal of the unmanned aerial vehicle, and further identifies the unmanned aerial vehicle model according to the frequency hopping sequence. The radio frequency channel parallel detecting device and method for the unmanned aerial vehicle have the advantages of low cost, high detection precision, simple and convenient deployment of the device structure and the like, can effectively detect and identify the unmanned aerial vehicle, and can be widely used and deployed in various areas where unmanned aerial vehicle detection is needed.
Owner:ZHEJIANG UNIV
Shale gas reservoir staged comprehensive evaluating method
InactiveCN108222925AQuick identificationEfficient identificationBorehole/well accessoriesShale gasResponse characteristics
The invention discloses a shale gas reservoir staged comprehensive evaluating method. Shale gas well core analysis and test data and logging information are collected, the corresponding relation of the development characteristics and logging parameters of a shale gas reservoir in a target area is determined, and the shale gas reservoir is identified qualitatively; and a key parameter system for evaluating of the shale gas reservoir is selected and determined, shale gas reservoir staged comprehensive evaluating standards are built according to the characteristics and correlation of key parameters, and the quality of the shale gas reservoir in the target area is divided and evaluated quantitatively. The multiple key parameters of the shale gas reservoir are composited, the logging response characteristics of the single-well shale gas reservoir section are combined, thus staged comprehensive evaluating of the shale gas reservoir is formed, and the shale gas reservoir can be evaluated quantitatively in the two aspects of geology and geophysical logging.
Owner:CHINA NAT PETROLEUM CORP CHUANQING DRILLING ENG CO LTD +1
Hotspot data identification method and device
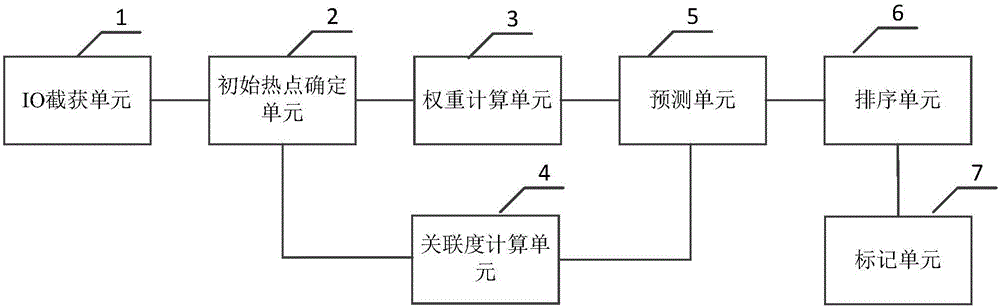
ActiveCN106709068AEfficient identificationEffective identificationSpecial data processing applicationsVisit timeData mining
The invention discloses a hotspot data identification method and a hotspot data identification device. The method comprises the steps of determining an initial hotspot queue according to the visit times of each storage data block within a first preset time slot; computing the weight of each hotspot data block in the all hotspot data blocks and the association degree between each data block in a data block set associated with the hotspot data blocks and the hotspot data blocks at preset intervals; multiplying the weight of each hotspot data block by the association degree between the hotspot data block and each associated data block, thus acquiring a heat prediction value of each data block; sorting the all data blocks with the heat prediction values according to the heat prediction value, wherein the data block with the plurality of heat prediction value is subject to the own highest heat prediction value; and adding the former preset quantity of data blocks in a sorting result into the initial hotspot queue to acquire the current hotspot queue. According to the method and the device provided by the invention, the hotspot data can be effectively identified, and the situation that the data is upgraded, degraded and migrated repeatedly in short time due to sudden visits can be avoided as much as possible.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Method and device for actively finding malicious code control end
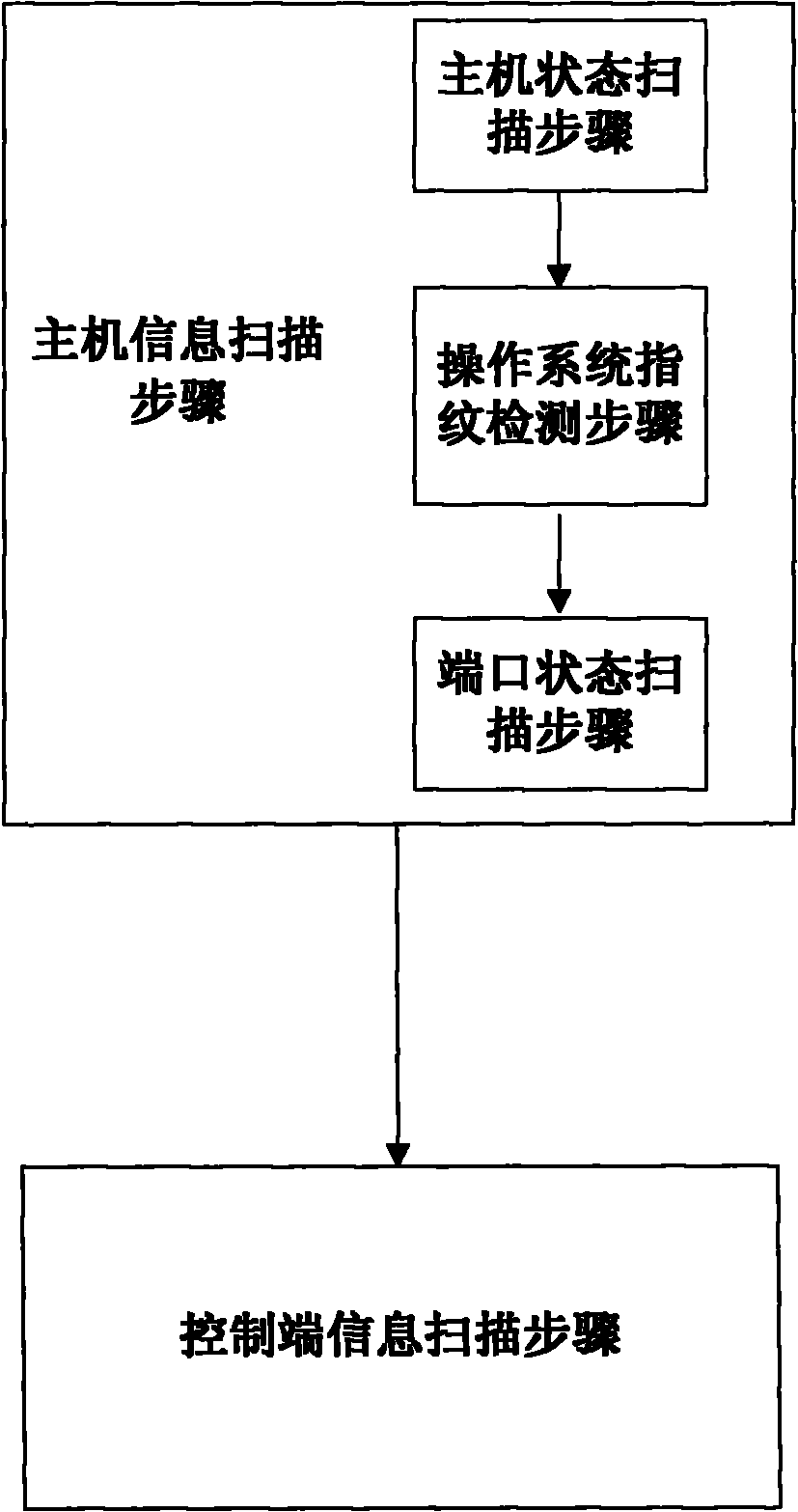
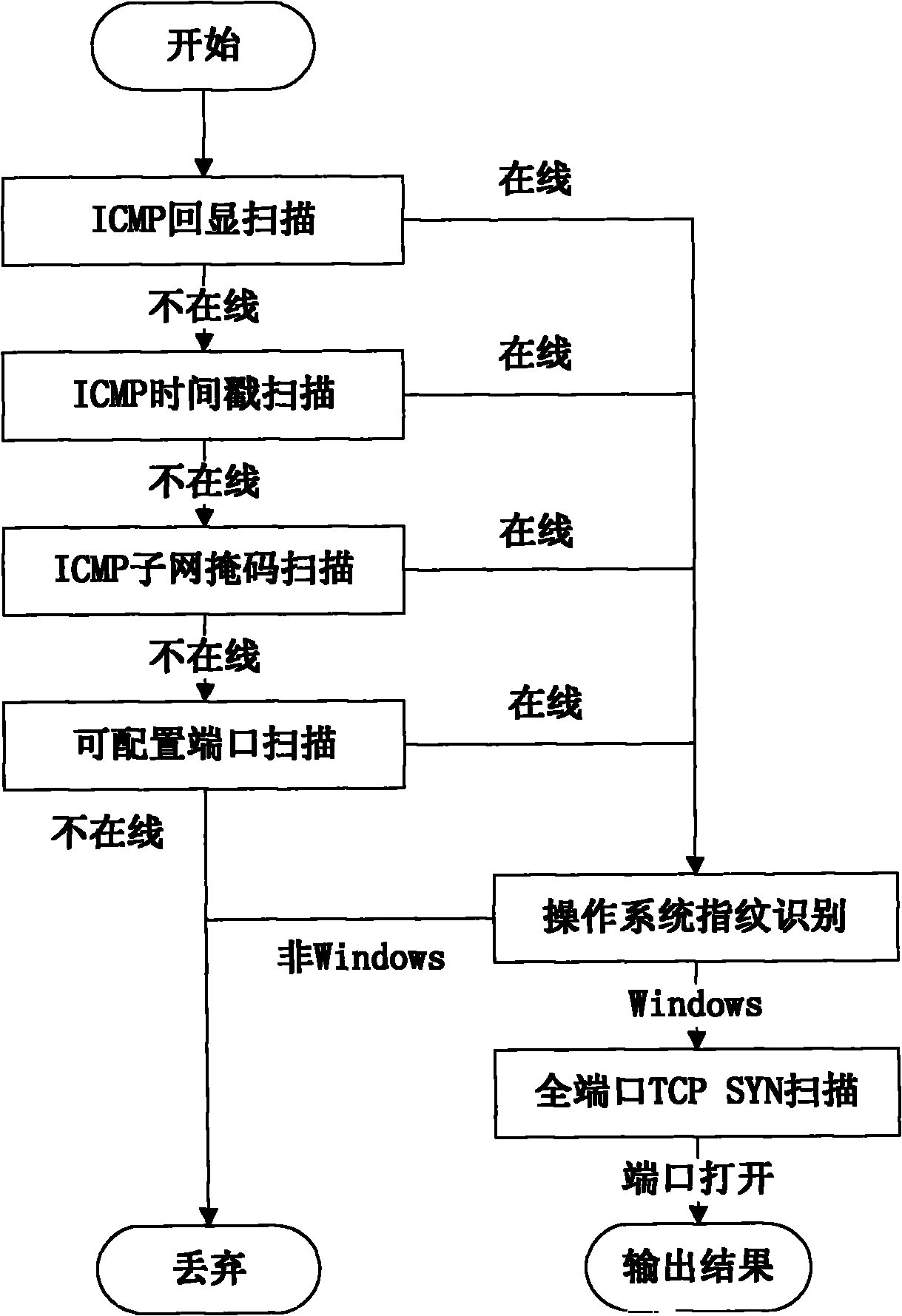
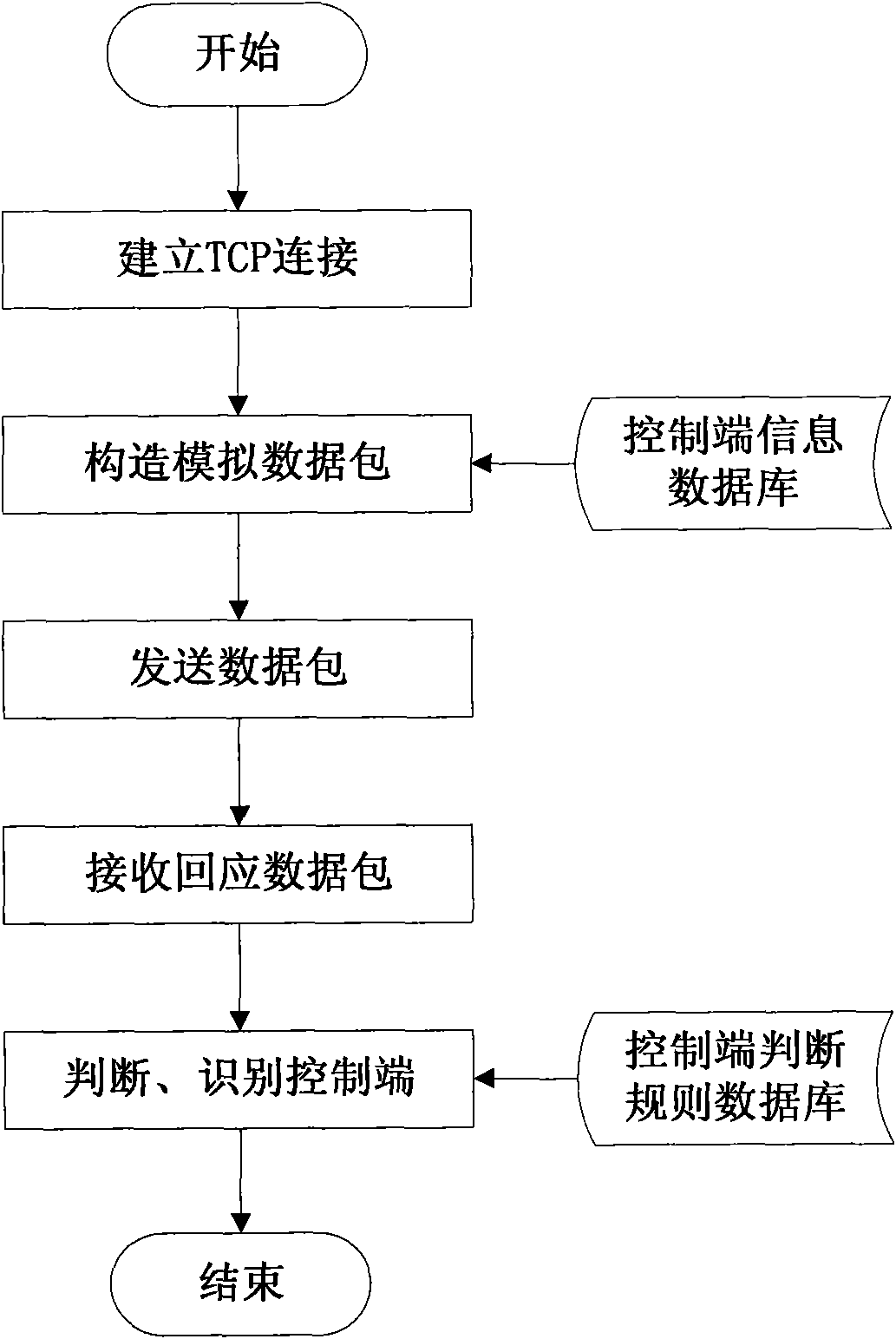
ActiveCN101924754AEffective active discoveryEffective identificationTransmissionOperational systemIp address
The invention discloses a method for actively finding a malicious code control end, which comprises the following steps of: scanning host information, namely finding a host computer in an on-line state of which the operating system is Windows and which is provided with open ports in an IP address range needing to be scanned and determining at least one open ports of the host computer; and scanning control end information, namely establishing network connection with the open ports of the host computer, simulating a network behavior of a controlled end host computer corresponding to the known type of the malicious code control end, sending data to the host computer, analyzing the received return data, and if the data meets the characteristic of the known type of the malicious code control end, indicating that the type of the malicious code control end exists in the host computer. The method can effectively identify the malicious code control end, is suitable for large-scale scanning of the host computer in the Internet and has great practical significance for guaranteeing information security. Correspondingly, the invention also provides a device for actively finding the malicious code control end.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Vehicle driving data management system and realization method
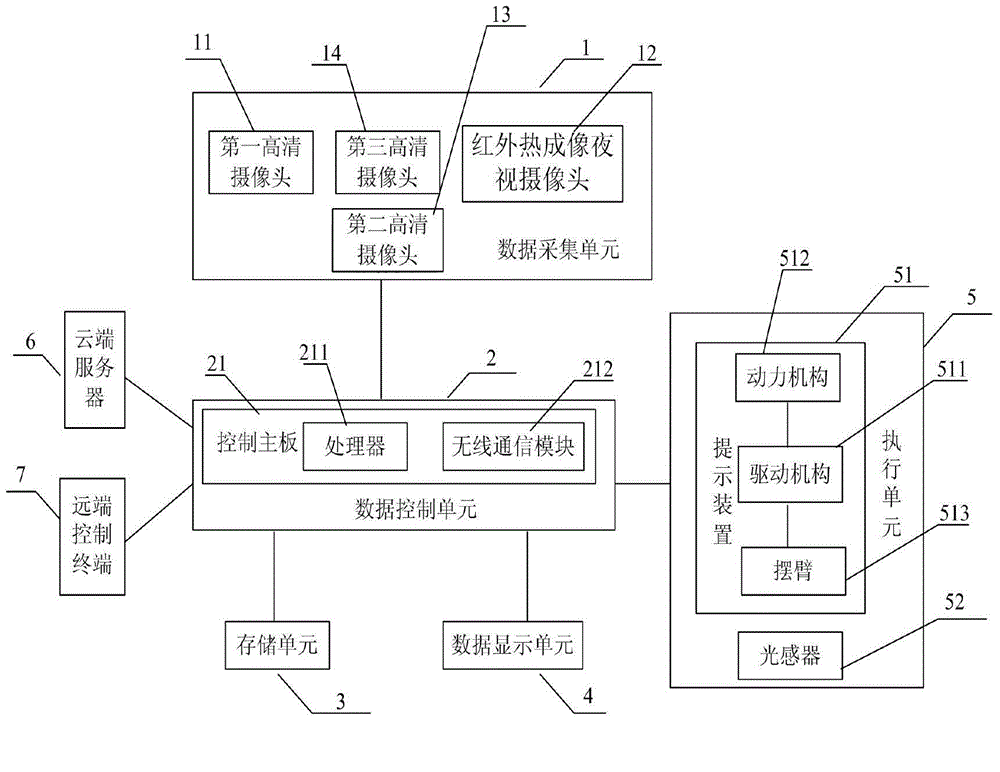
InactiveCN104786934AEfficient detectionEffective identificationSignalling/lighting devicesOptical viewingData informationVehicle driving
The invention discloses a vehicle driving data management system for acquiring and analyzing driving data of a vehicle to be managed in a driving process to realize functions of safety pre-warning and storage. The vehicle driving data management system comprises a data acquiring unit, a data control unit, a storage unit, an execution unit and a remote control terminal, wherein the data acquiring unit comprises an infrared thermal imaging night vision camera and a first high-definition camera for acquiring external environment information in a vehicle driving direction; the data control unit comprises a control mainboard, and a processor arranged on the control mainboard; the storage unit is connected with a processor for realizing real-time storage of the data information acquired by the data acquiring unit; and the execution unit is connected with the processor, and comprises a prompt device arranged in front of the vehicle to be managed to realize safety pre-warning, and a light sensor and a cloud server. The invention further discloses a realization method of the vehicle driving data management system.
Owner:MIANYANG AOLISI ELECTROMECHANICAL TECH CO LTD
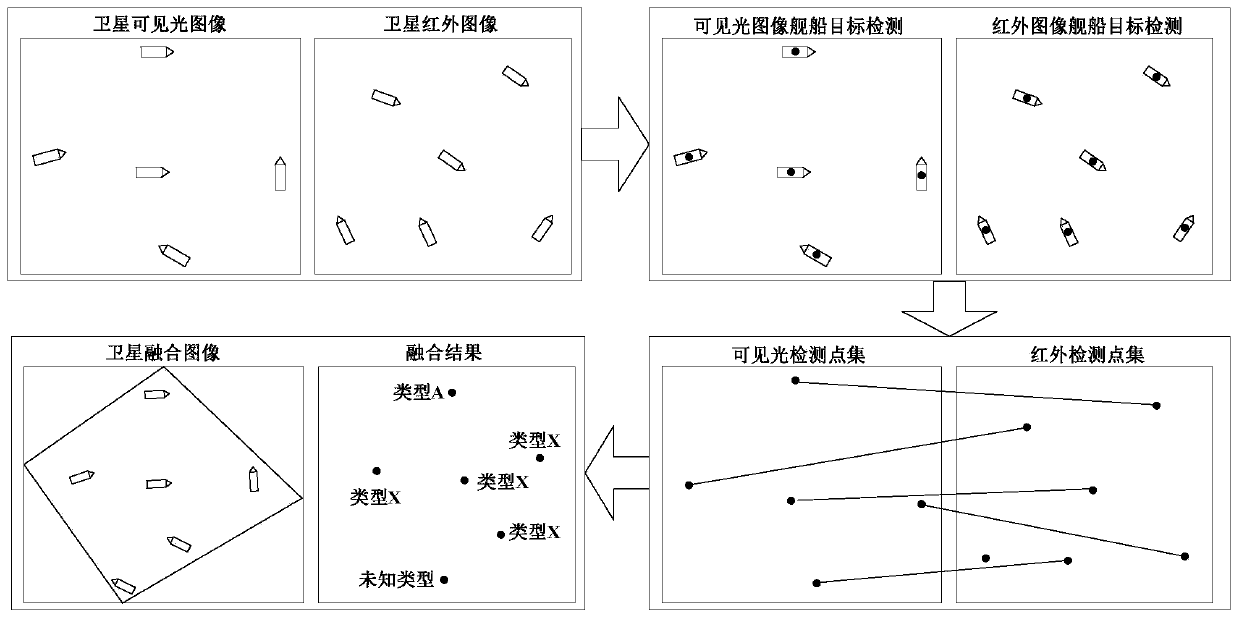
Marine target information fusion method based on satellite infrared and visible light images
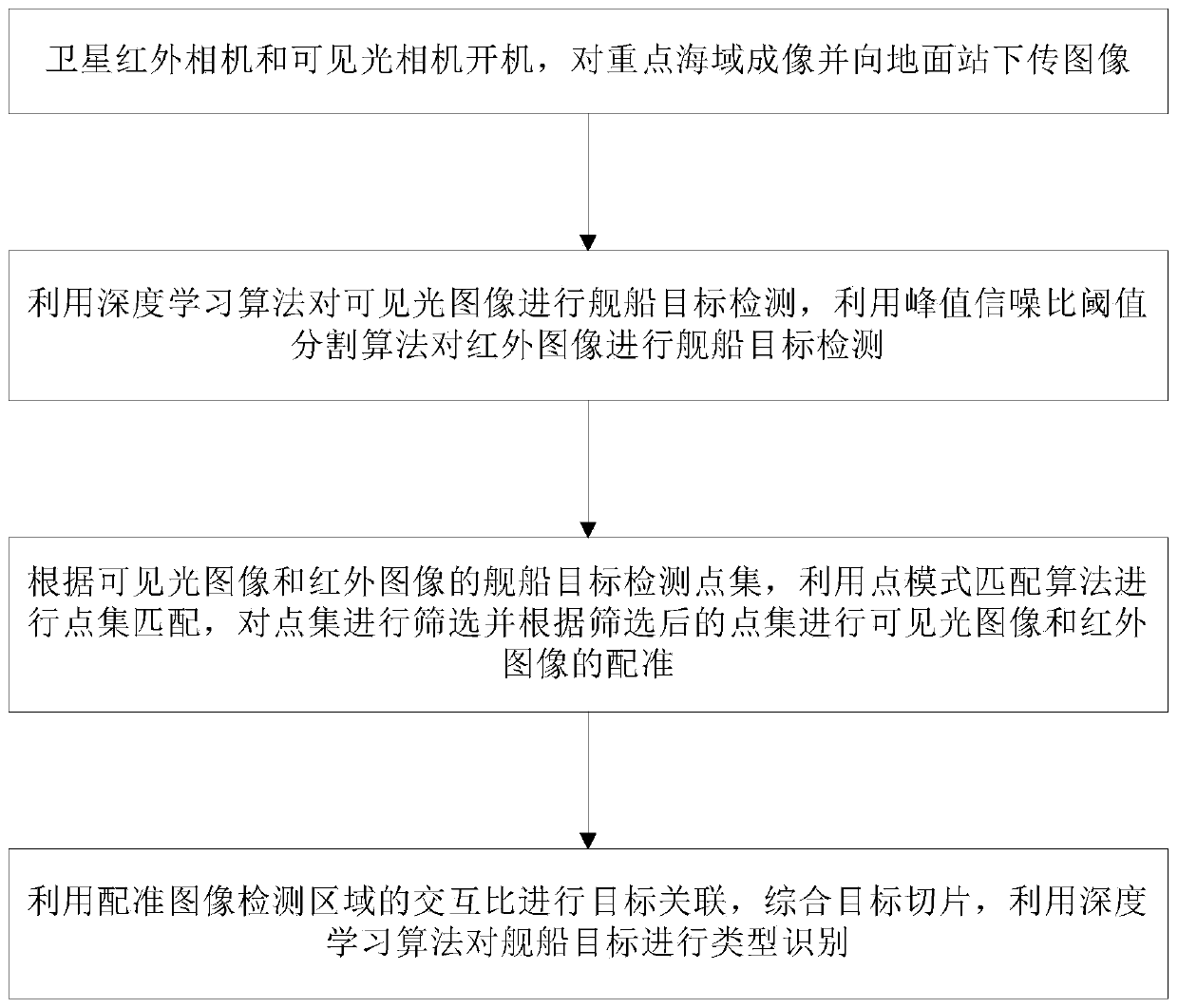
ActiveCN111582089AImprove perceptionStrong fault toleranceScene recognitionNeural architecturesImage detectionGround station
The invention discloses a marine target information fusion method based on satellite infrared and visible light images, and the method comprises the steps: starting a satellite infrared camera and a visible light camera, carrying out the imaging of a key sea area, and downloading an image to a ground station; and performing ship target detection on the visible light image by using a deep learningalgorithm, and performing ship target detection on the infrared image by using a peak signal-to-noise ratio threshold segmentation algorithm; according to the ship target detection point sets of the visible light image and the infrared image, performing point set matching by using a point mode matching algorithm, screening the point sets, and performing registration of the visible light image andthe infrared image according to the screened point sets; and performing target association by using the interaction ratio of the registered image detection area, integrating target slices, and performing type identification on the ship target by using a deep learning algorithm. According to the marine target information fusion method based on the satellite infrared and visible light images, effective discovery and identification of ship targets can be realized.
Owner:NAT INNOVATION INST OF DEFENSE TECH PLA ACAD OF MILITARY SCI
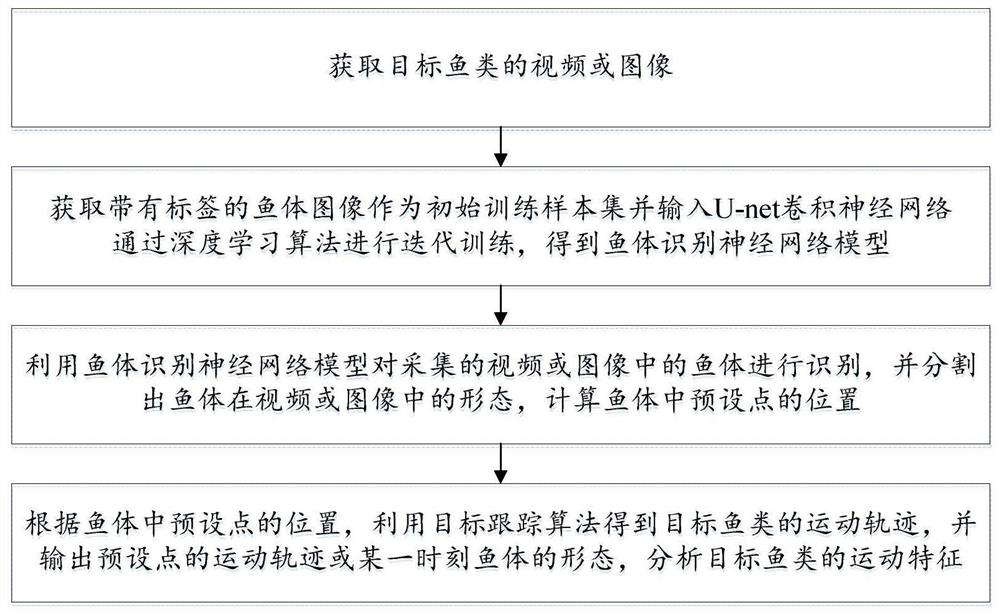
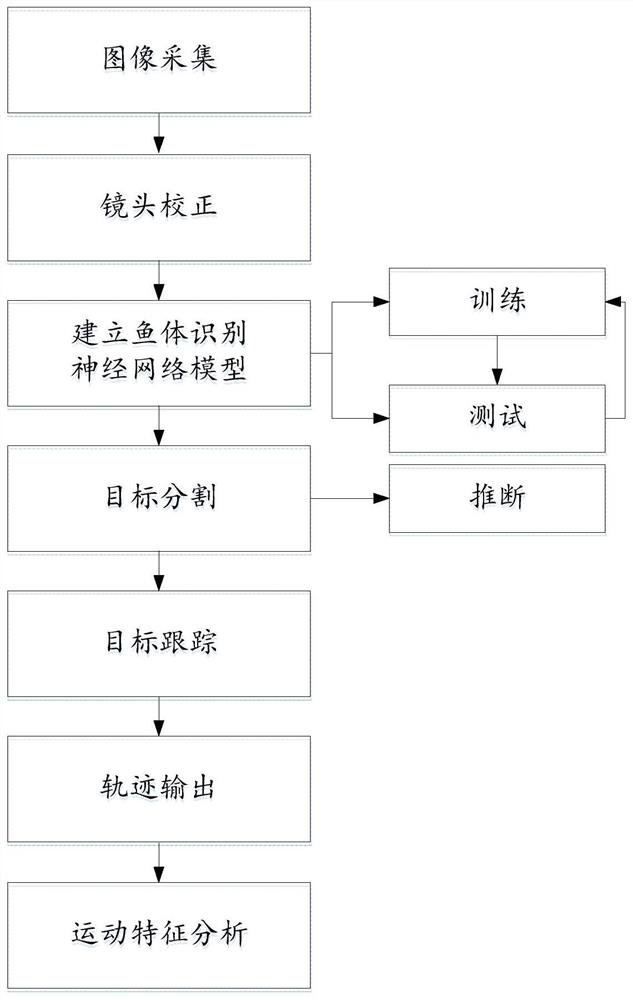
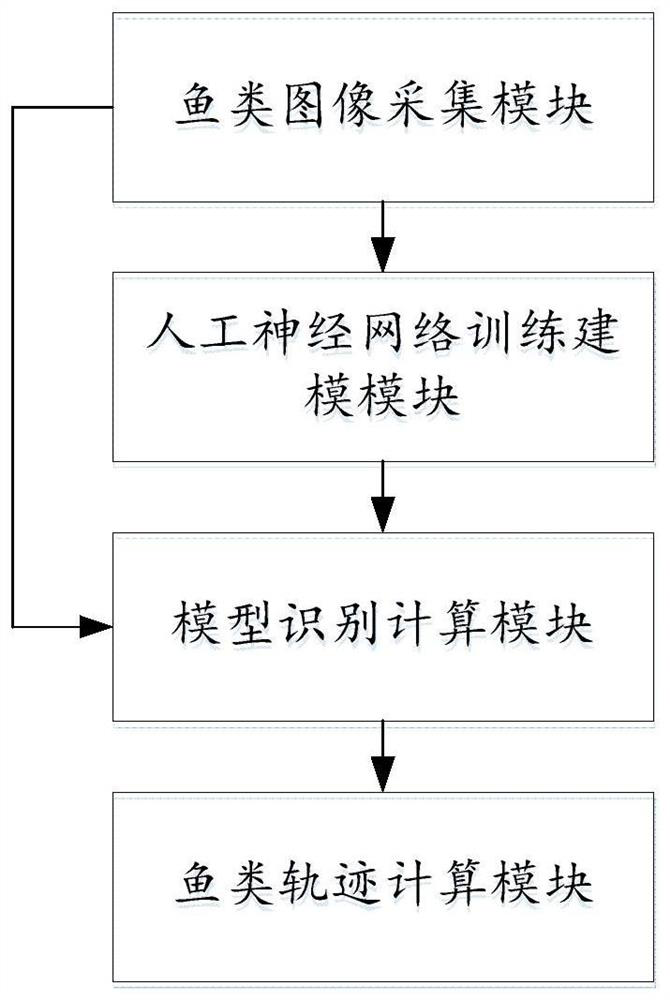
Fish trajectory tracking method and system based on artificial neural network
PendingCN112070799AThe output is controllableLower quality requirementsImage analysisNeural architecturesMirror reflectionObject tracking algorithm
The invention relates to a fish trajectory tracking method and system based on an artificial neural network. The method comprises the following steps of S1, acquiring a video or an image of a target fish; S2, obtaining a fish body image with a label as an initial training sample set, inputting the initial training sample set into a Unet convolutional neural network, and carrying out iterative training through a deep learning algorithm to obtain a fish body recognition neural network model; S3, recognizing a fish body in the acquired video or image of the target fish by utilizing a fish body recognition neural network model, segmenting a fish body form, and calculating the position of a preset point in the fish body; and S4, obtaining the motion trail of the target fish by using a target tracking algorithm, and analyzing the motion characteristics of the target fish. The method can accurately perform identification and trajectory tracking on the fish body, and thereby dependence of an experiment on an illumination condition is reduced, influence of mirror reflection and water surface fluctuation of the fish tank are overcome, high calculation efficiency is realized, the method can be applied to a long-time experiment video, and identification and trajectory tracking effects are improved.
Owner:TSINGHUA UNIV
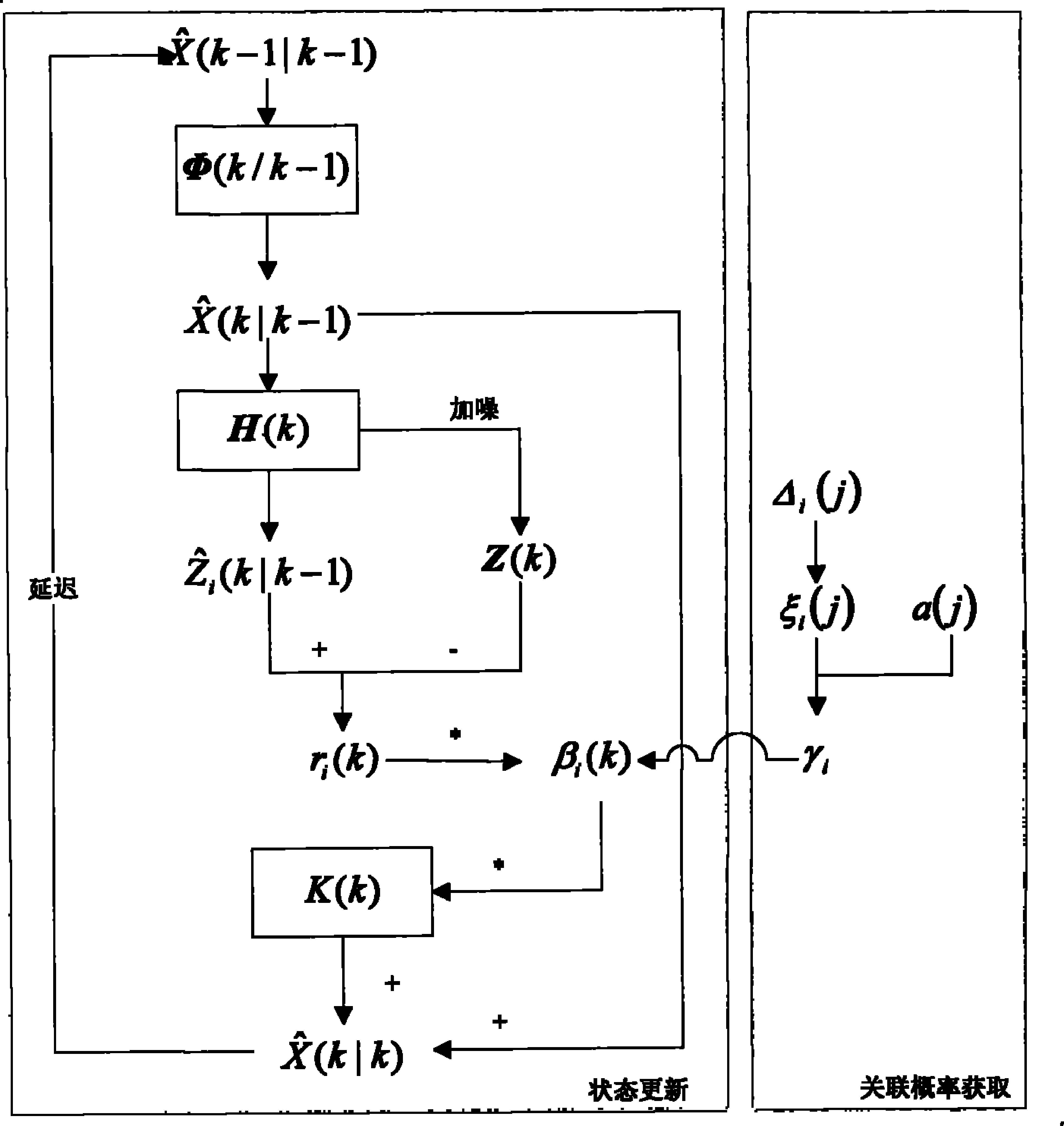
Target tracking and identification device and method based on entropy-weighted gray correlation
InactiveCN101883425AHigh precisionImprove stabilityNetwork topologiesDigital signal processingGoal recognition
The invention provides target tracking and identification device and method based on entropy-weighted gray correlation. The target tracking and identification device comprises a sensor network, a serial port chip, a field programmable gate array (FPGA), a digital signal processor (DSP) and a synchronous dynamic random access memory (SDRAM), wherein the DSP is used for carrying out entropy weighting, gray correlation, target state updating and target identification to data; the FPGA is used for preprocessing the data transmitted by the serial port chip and controlling the communication of the DSP and the serial port chip; the serial port chip is used for transmitting the data of the sensor network to the FPGA; and the SDRAM is used for storing target tracking and identifying results. The invention obtains the entropy-weighted gray correlation by utilizing target feature information provided by the sensor network to carry out state updating and identity identification to targets, and can still track and identify the targets under the condition that the sensor generates failures or the targets are lost.
Owner:HARBIN ENG UNIV
Pirate application detection method, device and system
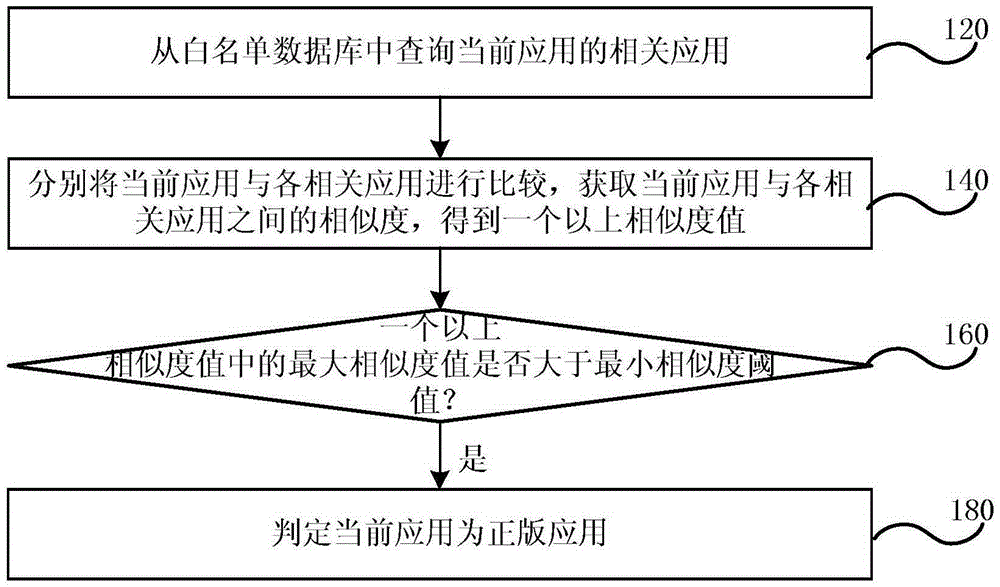
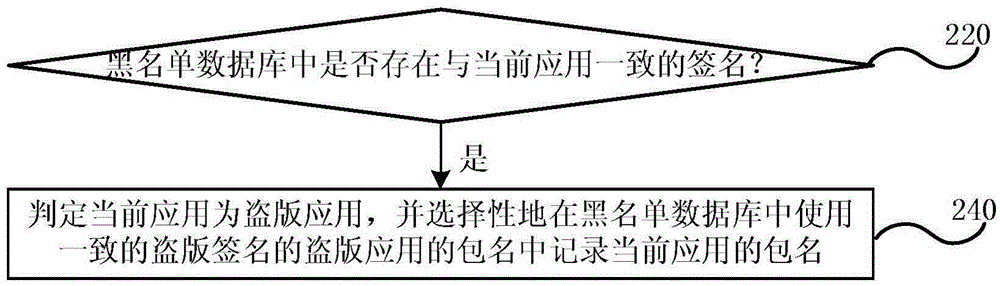
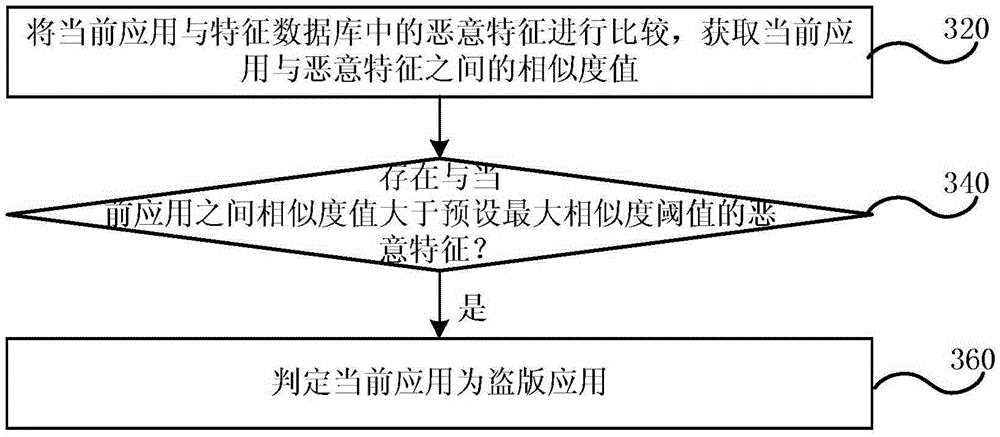
ActiveCN105426706AEffective detectionEffective identificationProgram/content distribution protectionData miningPackage.name
The embodiment of the invention discloses a pirate application detection method, device and system. The method comprises the following steps: inquiring a relevant application of a current application from a white list database, wherein the relevant application comprises any one same or similar application and an application which is the same with a developer in application characteristic information, and the application characteristic information comprises the name, the package name and the function of the application; storing more than one piece of legal copy application information in the white list database, wherein each piece of legal copy application information comprises the name, the package name, the signature, the version number and the developer information of at least one legal copy application; independently comparing the current application with each relevant application to obtain a similarity between the current application and each relevant application to obtain more than one similarity value; comparing whether a maximum similarity value in the more than one similarity value is greater than a preset minimum similarity threshold value or not; and if the maximum similarity value is greater than the preset minimum similarity threshold value, judging the current application is the legal copy application. The embodiment of the invention can detect the private application.
Owner:BEIJING QIHOO TECH CO LTD
Intelligent fiber perimeter intrusion alarm system
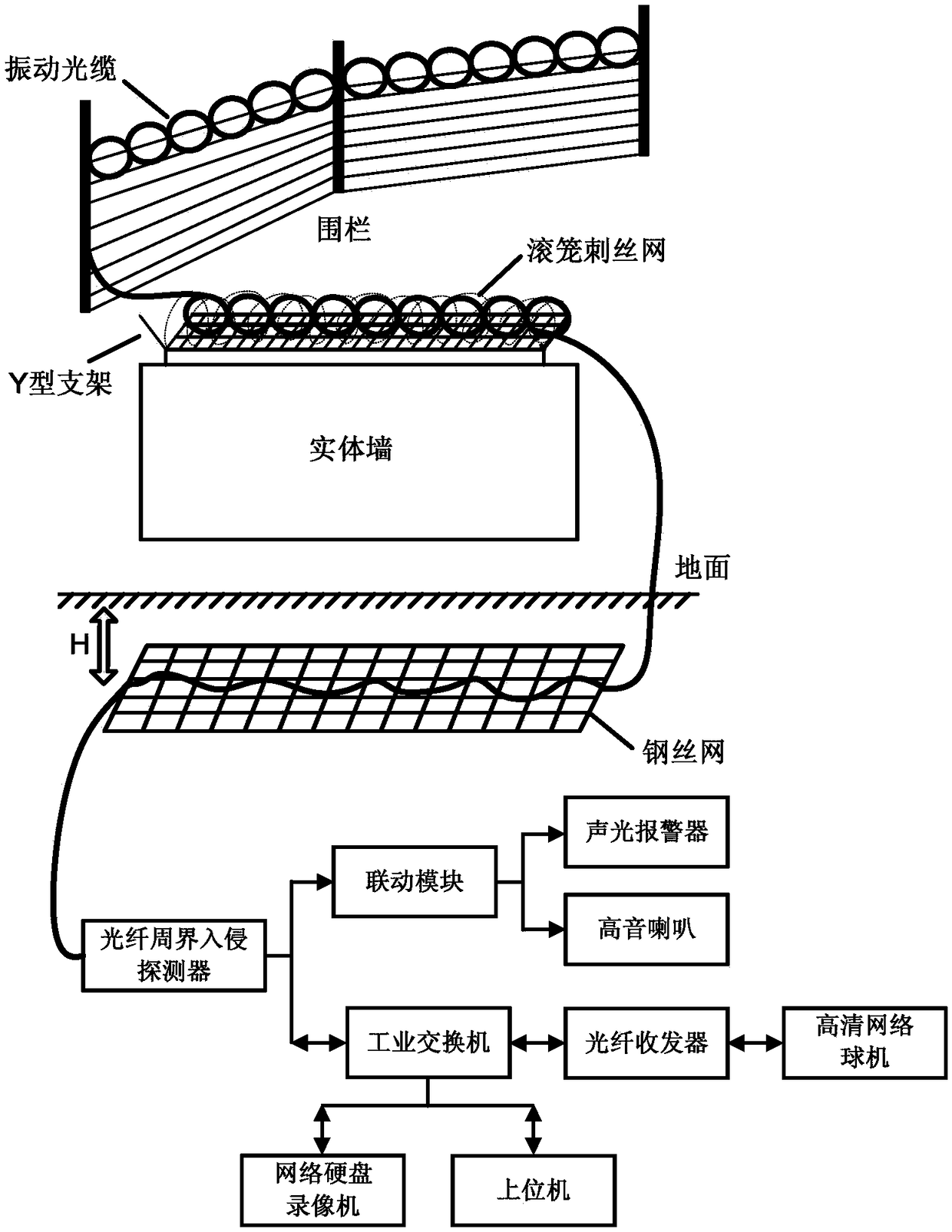
InactiveCN109118689AImprove perceptionRealize perimeter security protectionTelevision system detailsColor television detailsTransceiverLoudspeaker
The invention discloses an intelligent fiber perimeter intrusion alarm system, and the system includes a vibrating cable, a wire mesh, a Y-shaped bracket, a rolling cage barbed wire, a fiber perimeterintrusion detector, a linkage module, a network hard disk recorder, an industrial switch, a fiber optic transceiver, a high-definition network dome, a sound and light alarm, a loudspeaker and an upper computer. Among them, the vibrating cable is hung on a fence or a wall in a ring-shaped manner, and is arranged underground in a sinusoidal manner to realize the detection of an intrusion behavior,and an optical signal with the vibration information is transmitted to the fiber perimeter intrusion detector through an artificial neural network for processing. After the intrusion behavior of a person or a vehicle, the local high-definition network dome camera is controlled by the linkage module, the network hard disk recorder, the industrial switch and the optical transceiver to perform videorecording and expelling through the loudspeaker. Meanwhile, the sound and light alarm is used to alert the user, thereby achieving the local user monitoring.
Owner:BEIJING INST OF AEROSPACE CONTROL DEVICES
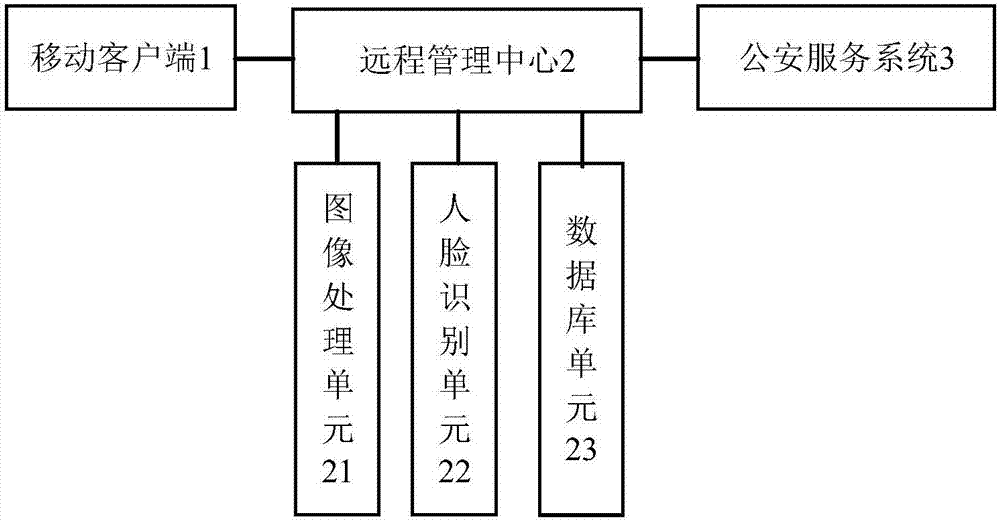
Effective missing children finding system
ActiveCN106920256AAchieve the purpose of seekingEfficient collectionImage enhancementImage analysisReal time displayComputer science
The invention discloses an effective missing children finding system which includes mobile clients, a remote management center and a public security service system. The public security service system is intended for uploading reference photos of a child who is determined to be missing and relevant identity information to the remote management center. The mobile client is intended for real-time displaying the reference photo of the missing child at the present to users. Also, users can photograph a child if the child is the missing child through the mobile clients and upload the photos to the remote management center. The photos are matched with the reference photos of the missing children that are saved in the remote management center. If the matching is successful, the result of the successful matching is uploaded to the public security service system. According to the invention, the system has the beneficial advantages that the system can effectively acquire and identify face information of the missing child by establishing modules and realizes the purpose of finding the missing child by matching the photos with the reference photos of the missing child that are saved in a database.
Owner:张志航
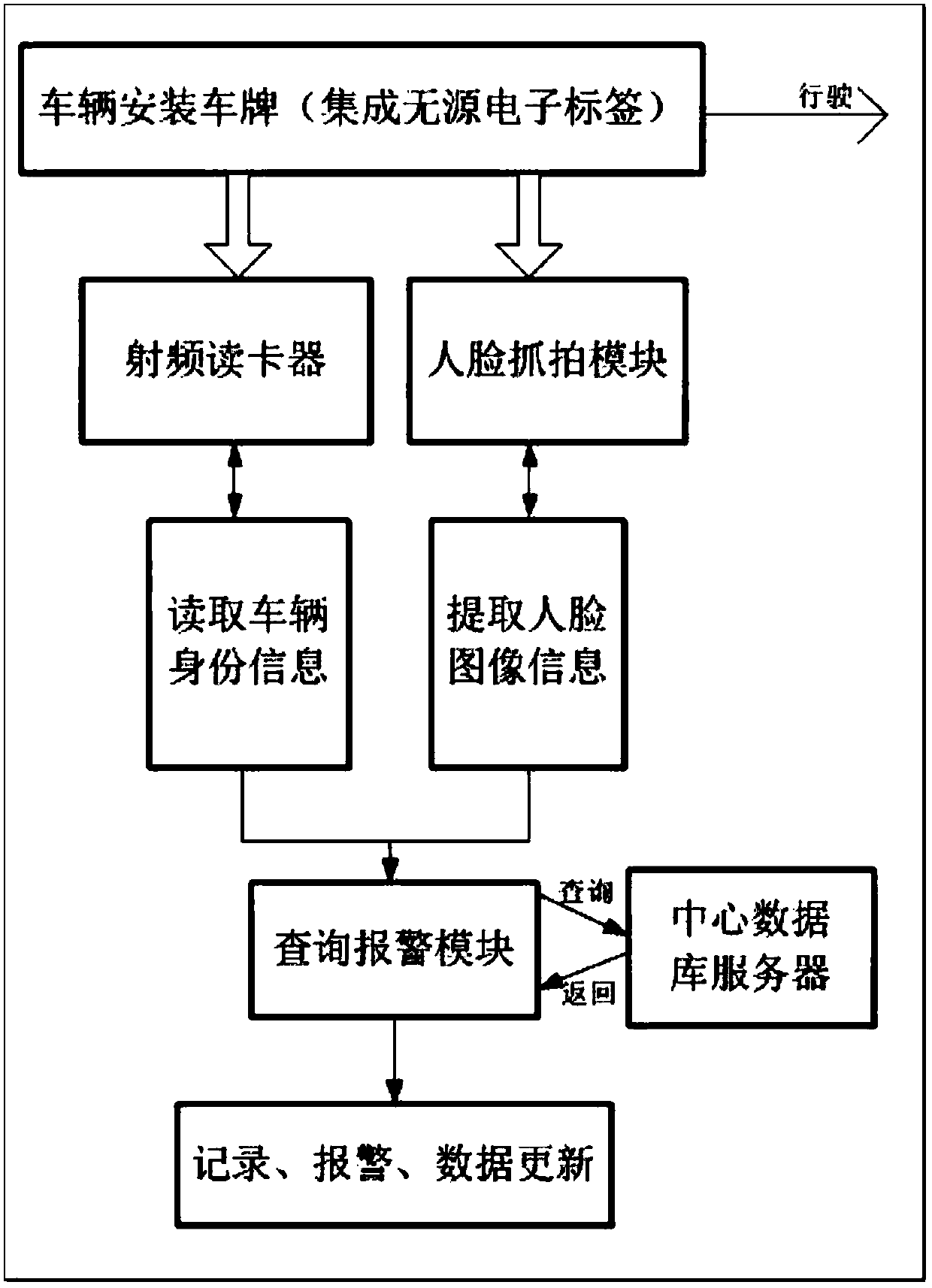
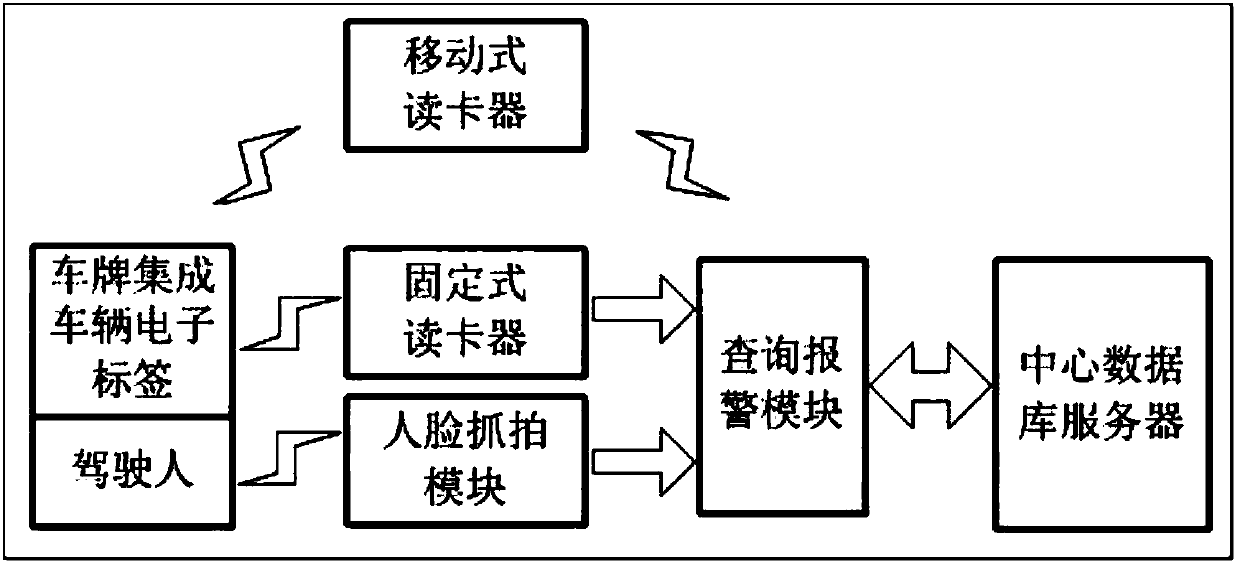
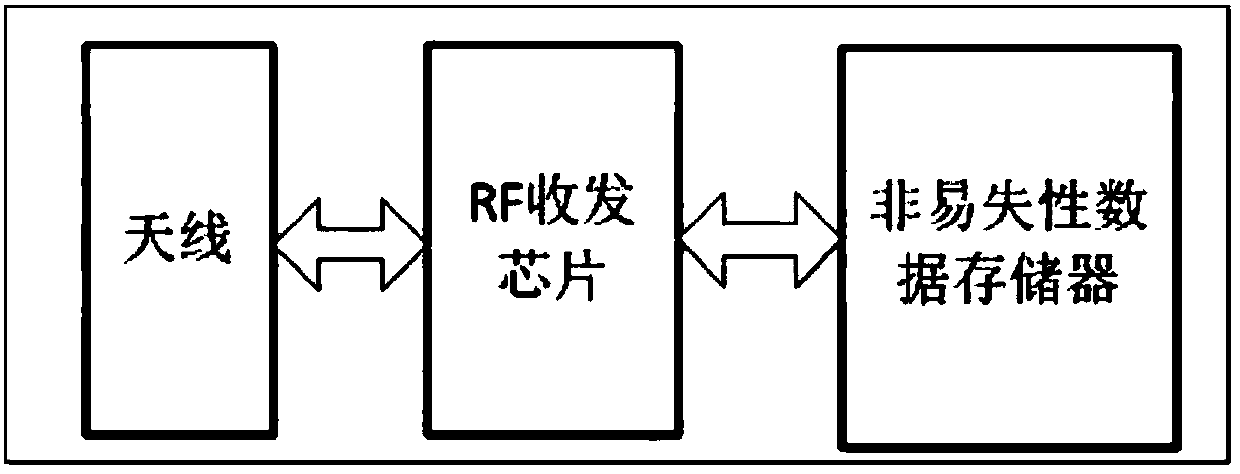
Electric bicycle, motorcycle and motor tricycle monitoring management system and method thereof
InactiveCN107798510ADoes not affect normal drivingHigh precisionCo-operative working arrangementsCharacter and pattern recognitionMotorized tricycleCentral database
The invention discloses an electric bicycle, motorcycle and motor tricycle monitoring management system and a detection method thereof. The system comprises a radio-frequency identification tag, a radio-frequency card reader, a capture module, a query alarm module and a central database server, wherein the radio-frequency card reader transmits read tag information of the radio-frequency identification tag to the query alarm module; the capture module transmits obtained image information to the query alarm module; the query alarm module compares the obtained tag information and image information, and sends the information to the central database server for performing query processing; and the central database server transmits a query result back to the query alarm module for performing analysis processing to realize vehicle and driver monitoring management. The system is convenient in operation, does not workers to perform check one by one, has the advantages of high precision, high efficiency and the like, and provides powerful guarantee for managing behaviors of vehicle stealing, illegal driving and the like.
Owner:北京市振隆科技股份有限公司
Method for identifying entities named by Cambodian on basis of cross-language resource
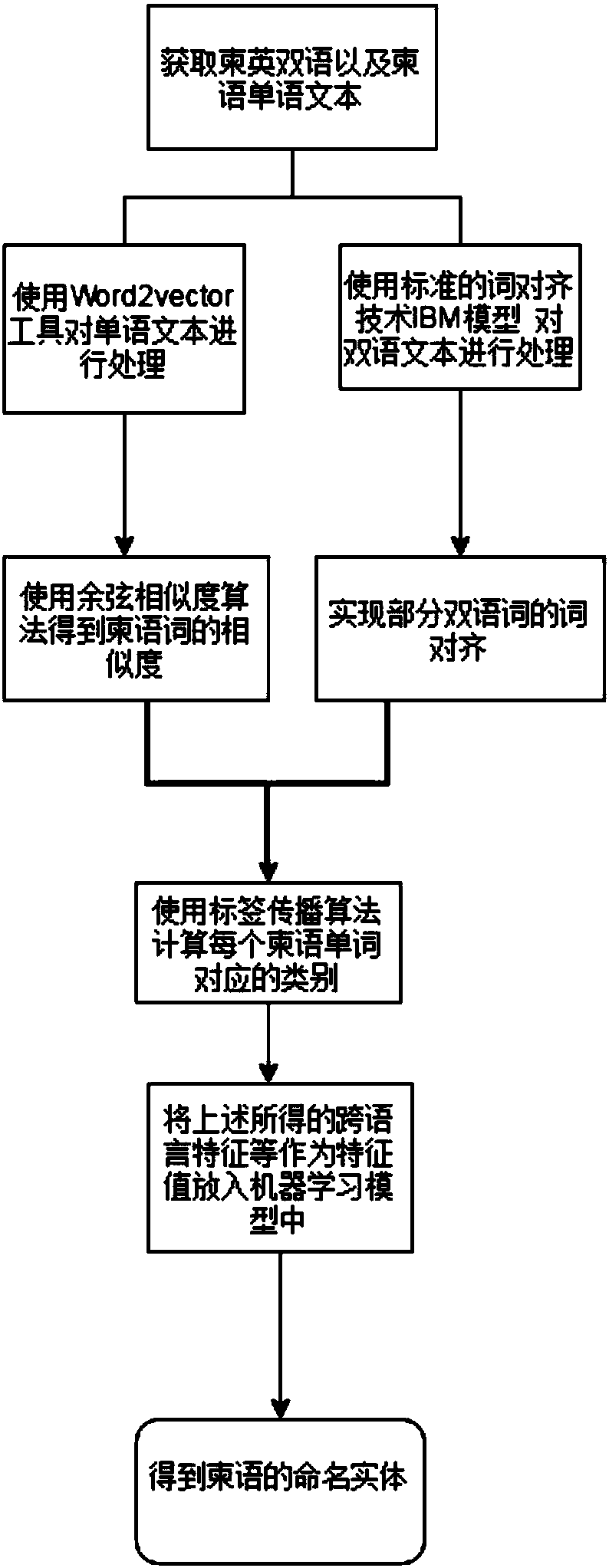
ActiveCN107861947AEffective identificationEfficient identificationNatural language data processingSpecial data processing applicationsText corpusBilingual corpus
The invention relates to a method for identifying entities named by Cambodian on the basis of a cross-language resource, and belongs to the technical field of natural language processing. The method includes the steps of firstly, obtaining an English-Cambodian bilingual parallel text corpus and a Cambodian monolingual text corpus; secondly, using a tool Word2vec to process Cambodian monolingual text to obtain a vector representation of Cambodian words; thirdly, adopting a cosine method to calculate the similarity values among the Cambodian words, and meanwhile using an IBM model to achieve word alignment between the Cambodian words and English words; utilizing a label propagation algorithm in a bilingual image model to process the Cambodian-English bilingual corpus to obtain a corresponding class of the Cambodian words in the text, and then adopting the corresponding class as a cross-language characteristic and applying the cross-language characteristic, word property characteristics,mark characteristics and word characteristics for marking the names of people and the names of locations to a machine learning model; finally, achieving identification of the named entities for the obtained corpora.
Owner:KUNMING UNIV OF SCI & TECH
Well lid theft detection method
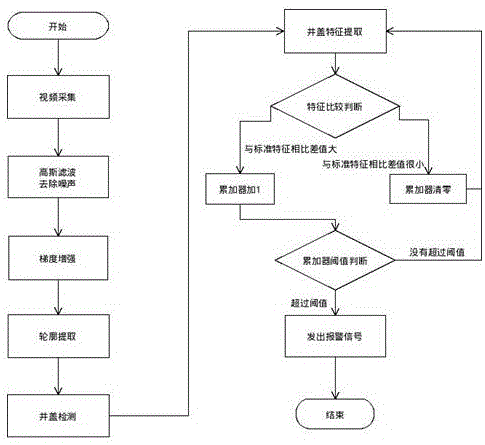
InactiveCN106446807AAvoid influenceEffective identificationCharacter and pattern recognitionEllipseFalse detection
The invention discloses a well lid theft detection method. The method comprises the steps of obtaining a video sequence image containing a well lid from a monitoring device; determining an ellipse coinciding with the edge of the well lid through an image processing algorithm; performing calculation according to features in an ellipse range of the video sequence image to obtain a reference feature value; obtaining the video sequence image from the monitoring device at an interval of first preset time, and performing calculation according to the features in the ellipse range of the video sequence image to obtain a comparison feature value; performing comparison to obtain a difference value between the comparison feature value and the reference feature value, if the difference value is greater than a reference error value, adding 1 to an accumulator, and if the difference value is smaller than the reference error value, resetting the accumulator; and if a count of the accumulator exceeds a reference threshold, outputting a theft signal. According to the method, a detection algorithm provided by the invention still can perform effective identification and locating on a deformed well lid image, the detection speed and accuracy is increased and improved, the calculation complexity is lowered, and a calculation mechanism of the accumulator can effectively avoid a false detection phenomenon.
Owner:CHENGDU TOPPLUSVISION TECH CO LTD
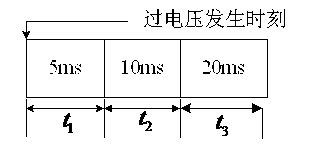
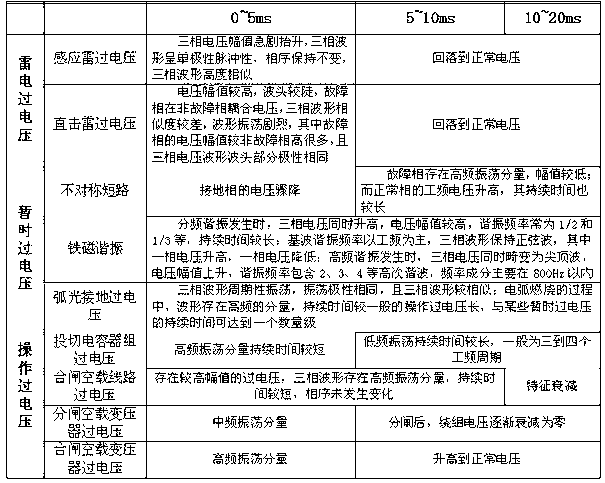
Power grid overvoltage identification method by adopting multi-parameter ratio codes
InactiveCN102735947AEffective identificationClear thinkingCurrent/voltage measurementPower gridData processing
Owner:ELECTRIC POWER SCI RES INST OF GUIZHOU POWER GRID CO LTD +1
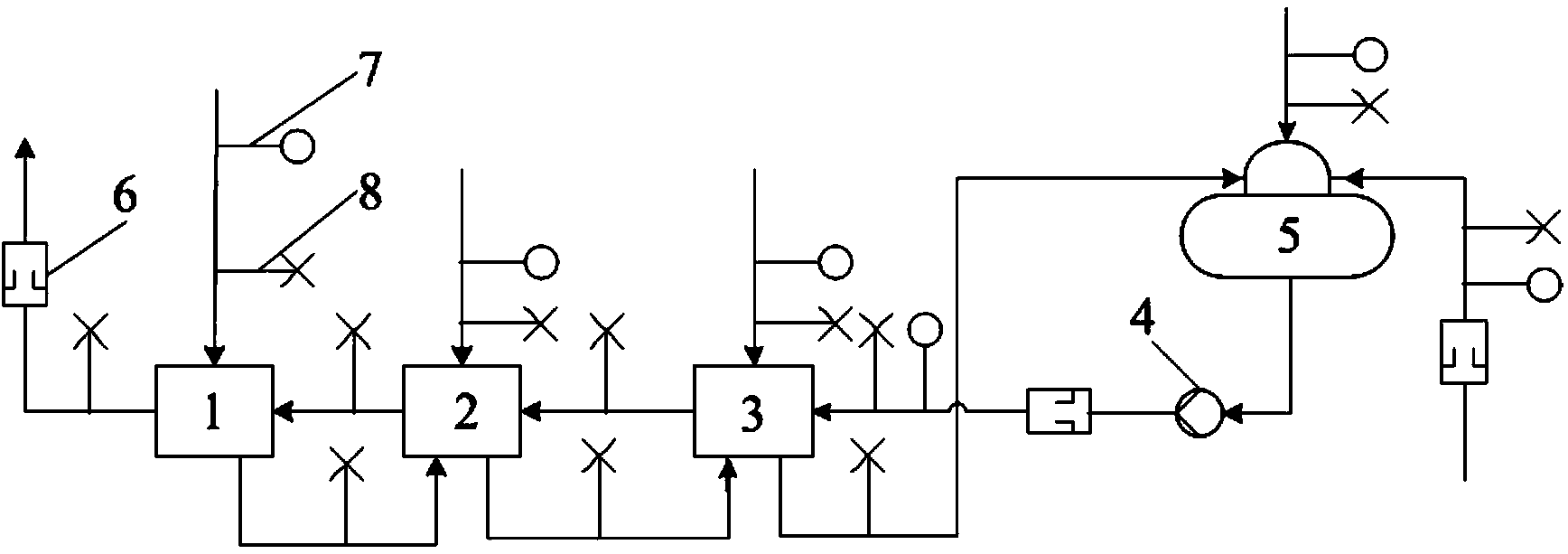
Method for monitoring flow meter faults of turbine system
ActiveCN103674189AEffective detectionEffective identificationTesting/calibration apparatusTurbineDetection threshold
The invention provides a method for monitoring flow meter faults of a turbine system and belongs to the field of online monitoring of a turbine. A data coordination method is adopted by the method so that broken-down flow meters can be monitored and identified. The method specifically comprises the steps that (1) data coordination calculation is conducted through steady-state condition measured data according to the uncertainty of measured values of measured parameters and a system constraint equation; (2) the minimum objective function value of data coordination is compared with a fault detection threshold value, whether the flow meters break down or not is judged; (3) if it is detected that the flow meters break down, fault identification is conducted on the flow meters one by one, the measured parameters corresponding to the flow meters serve as non-measured parameters, and the minimum objective function value of data coordination is calculated again; the new minimum objective function value is compared with the fault detection threshold value, so that the broken-down flow meter is identified. According to the method for monitoring the flow meter faults of the turbine system, redundant flow measurement information in the turbine system can be effectively used for detecting and identifying the flow meter faults and the method has the advantages of being easy to achieve, efficient and low in cost.
Owner:TSINGHUA UNIV
Push method based on data mining
InactiveCN106339456AImprove experienceIncrease flexibilitySpecial data processing applicationsData dredgingPersonalization
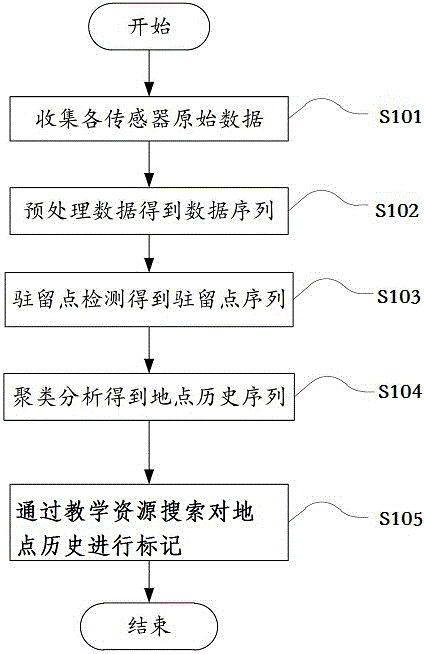
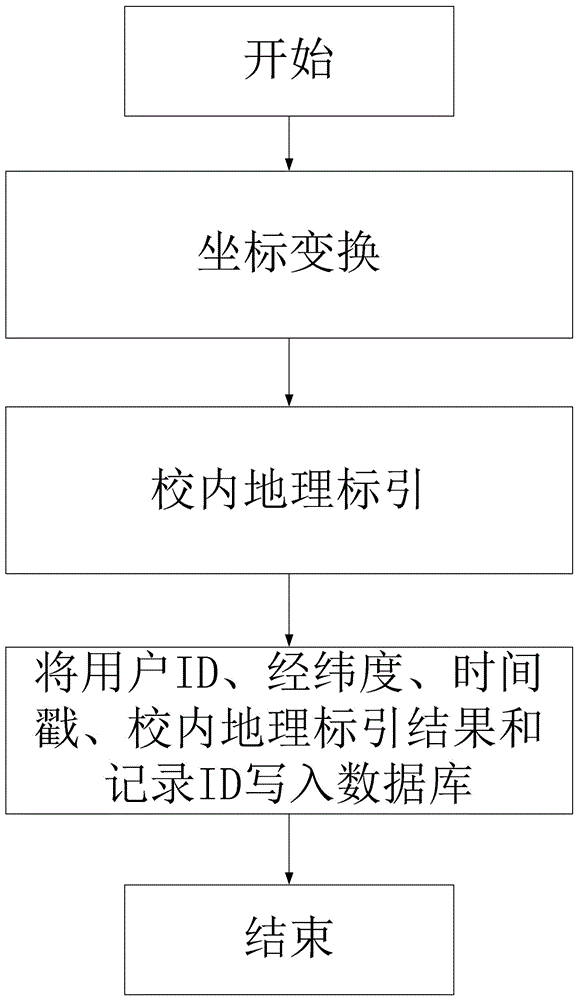
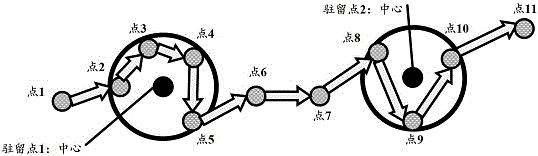
The invention discloses a push method based on data mining. The push method comprises the steps of summarizing learning plan data and teaching resource data of a user through a cloud computing platform; collecting original data from all sensors of student mobile devices; performing data preprocessing on the original data and obtaining a data sequence; obtaining a lingering point sequence according to a lingering point detection method; performing cluster analysis on the lingering point sequence to obtain a site historical sequence; performing teaching resource search on each piece of data in the site historical sequence, and marking site history; matching and generating a message which is based on time, position and teaching resource data according to the data sequence, the marked site history and the learning plan data, and pushing the message to the user. The push method has the effect of pushing rich, in-time, accurate and individual teaching information to learners.
Owner:CHONGQING CREATION VOCATIONAL COLLEGE
Building deformation monitoring and collapse early warning system
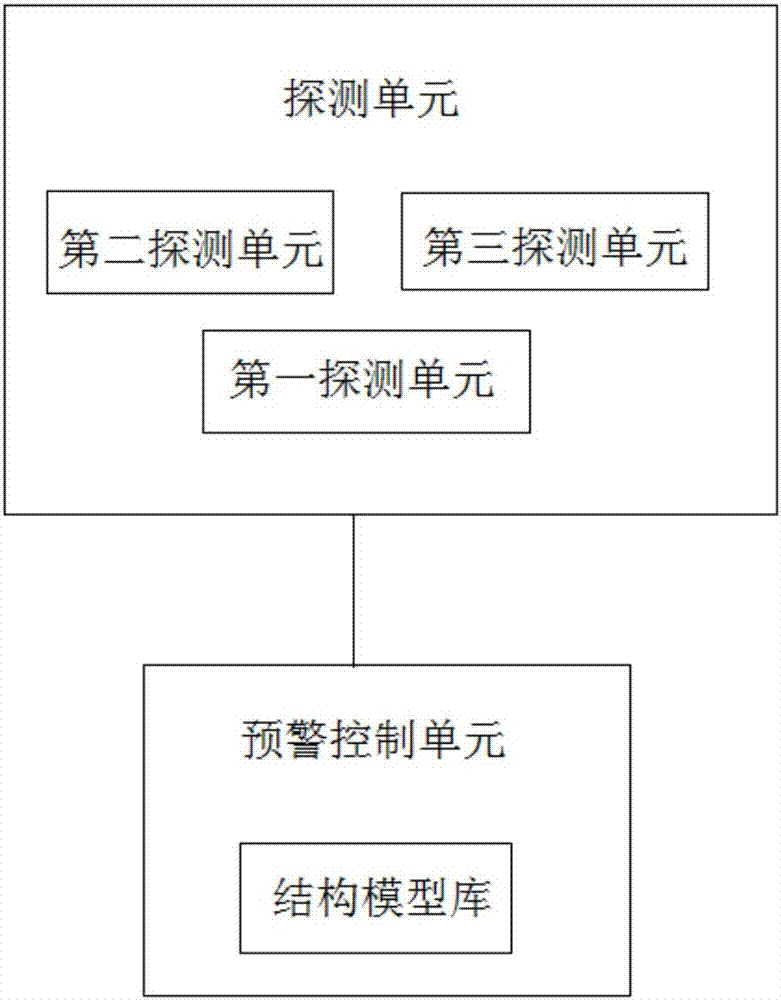
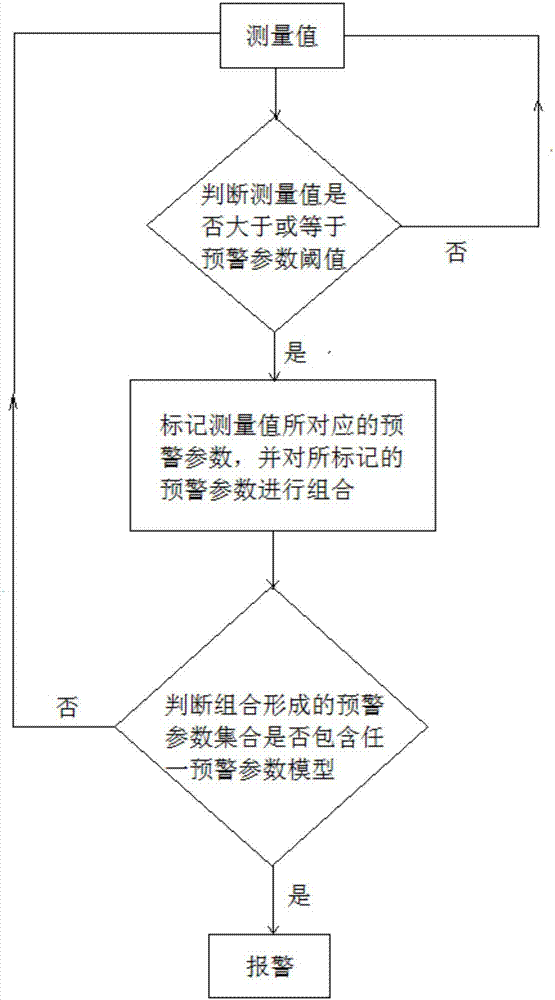
ActiveCN107063168AImprove accuracyEffective identificationMeasurement devicesAlarmsEarly warning systemMeasurement point
The invention discloses a building deformation monitoring and collapse early warning system. The system comprises a building structure displacement detection unit and an early warning control unit. The building structure displacement detection unit comprises a first detection unit, which is used to detect displacement and / or speed of a measured point of a building. The first detection unit comprises at least one long distance detection component, which is used to acquire the displacement and / or speed changing process of the at least one measured point. The early warning control unit is used for early warning control according to the measurement result of the displacement detection unit. The building deformation monitoring and collapse early warning system is used to realize the remote non-contact, accurate monitoring of the deformation of the building, and is used to realize the timely and accurate early warning according to monitored building deformation data.
Owner:应急管理部四川消防研究所
Fine-grained vehicle model detection and identification method based on data equilibrium strategy and intensive attention network
ActiveCN108830254AEffective detectionEffective identificationRoad vehicles traffic controlCharacter and pattern recognitionMachine learningData mining
The present invention relates to a fine-grained vehicle model detection and identification method based on a data equilibrium strategy and an intensive attention network. The method comprises the steps of: obtaining a vehicle model data set, marking the obtained vehicle model data set, and getting ready for training vehicle model detection and identification of the model; employing the data equilibrium strategy to perform data equilibrium processing of the collected vehicle model data set; employing the vehicle model data set after data equilibrium processing to train the intensive attention network; and finally, input an image to be detected into a trained intensive attention network, and employing the trained intensive attention network to perform detection and identification of the image to be detected.
Owner:FUZHOU UNIVERSITY
Shunting service risk control system
InactiveCN103029727AEffective identificationPrevent shunting accidentsRailway traffic control systemsEngineeringRisk Control
The invention provides a shunting service risk control system which comprises a train which prepares to perform shunting service in a station yard, a vehicle-mounted detection device arranged on the train, a vehicle-mounted train prevention and control master control device, a vehicle-mounted high-precision positioning device, a ground train prevention and control master control device and a ground high-precision positioning device which are arranged in the station, and a train operation dispatching command system (TDCS) and a transportation management information system (TMIS) which are connected with the ground train prevention and control master control device. According to the system, the train position information acquired by the detection, blue and white lamp and track occupancy information and preset information in the TDCS system are subjected to error correction and comparison, so that the train is correspondingly controlled, and the train safety in the process of performing shunting service is guaranteed.
Owner:西北铁道电子股份有限公司
Train communication network flow identification method based on deep learning
InactiveCN113037646AEffective identificationEffective classificationNeural architecturesData switching networksInternet trafficEngineering
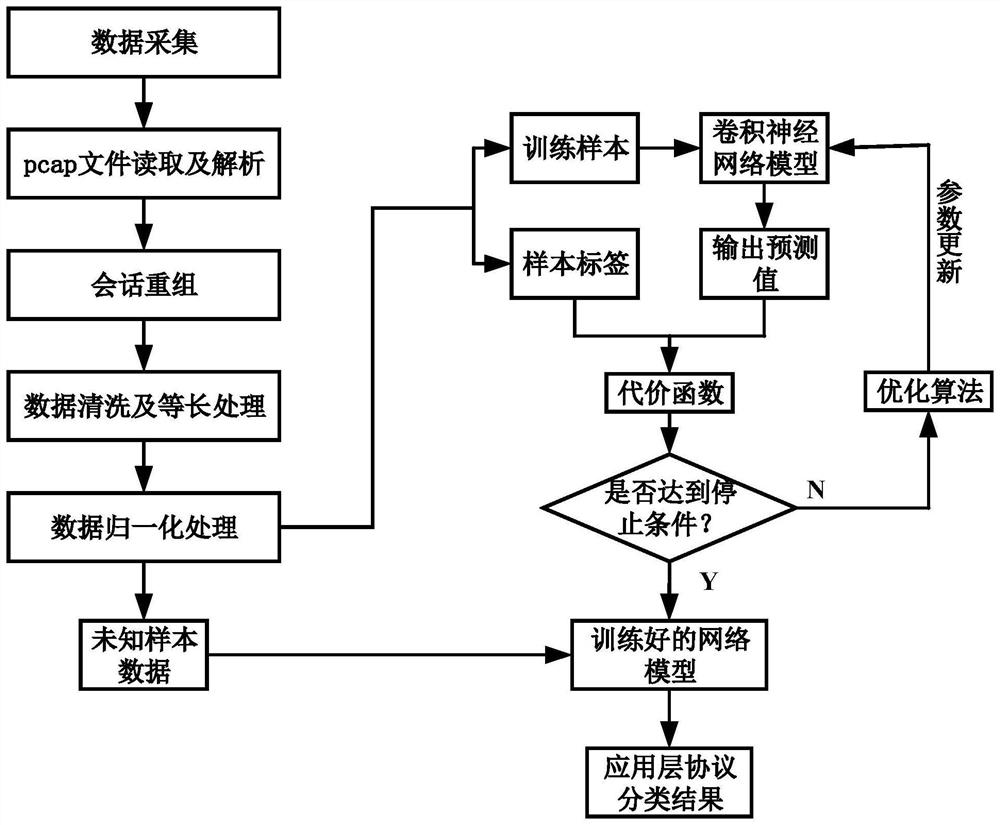
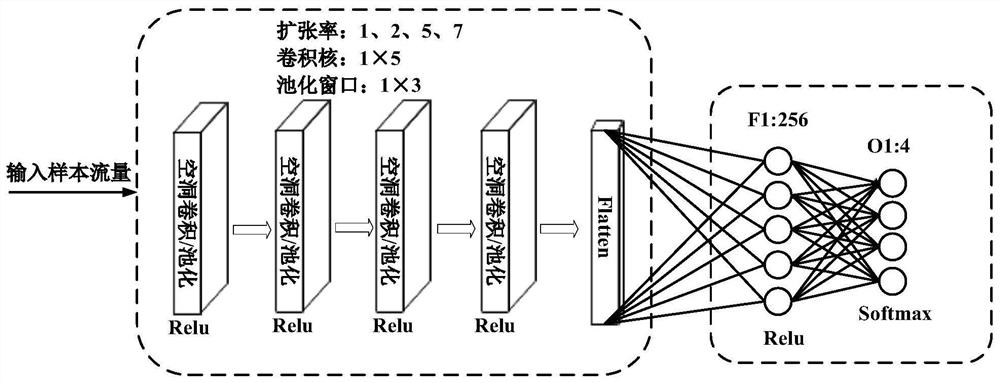
The invention discloses a train communication network flow identification method based on deep learning, and the method specifically comprises the steps: collecting train communication network flow data through a package capturing tool, reading and analyzing a pcap file, carrying out the session recombination, data cleaning, equal-length processing and normalization processing, carrying out the annotation of a label for sample data, and training the one-dimensional convolutional neural network by using the sample data; and finally, achieving the effective classification of the traditional application layer protocols and the railway private protocols in the train communication network traffic only by inputting unknown traffic into the trained model. According to the invention, effective identification and classification of common application layer protocols and railway private protocols in a train control and service network are realized; useful feature information can be extracted more accurately, and higher precision, precision ratio and recall ratio are achieved.
Owner:SOUTHWEST JIAOTONG UNIV
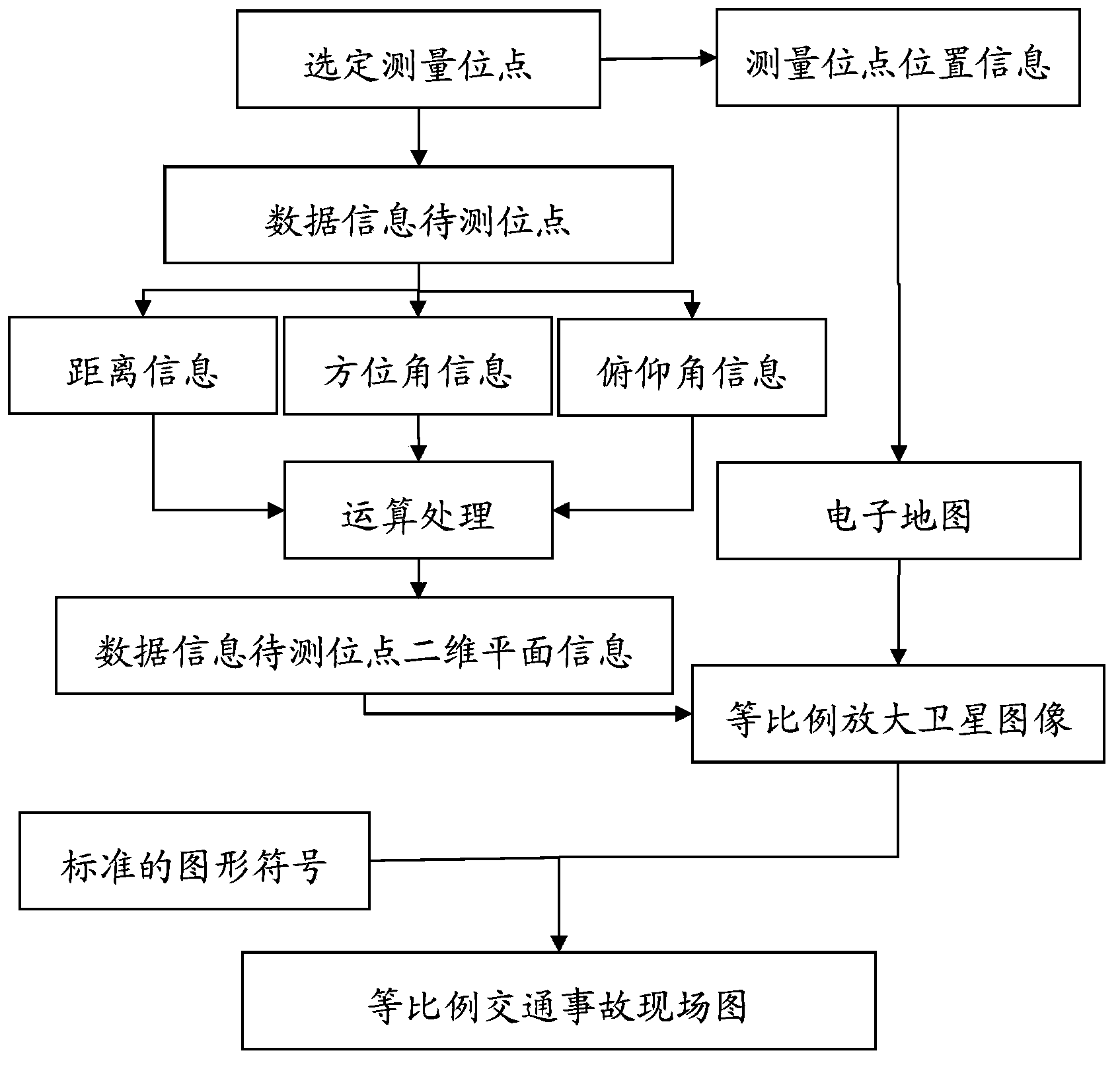
Accident spot map generation method based on electronic map and data acquisition system
InactiveCN103400498AScientific and simple technical meansFast fixationRoad vehicles traffic controlData informationData acquisition
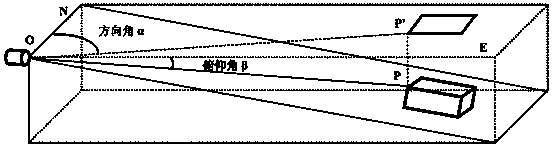
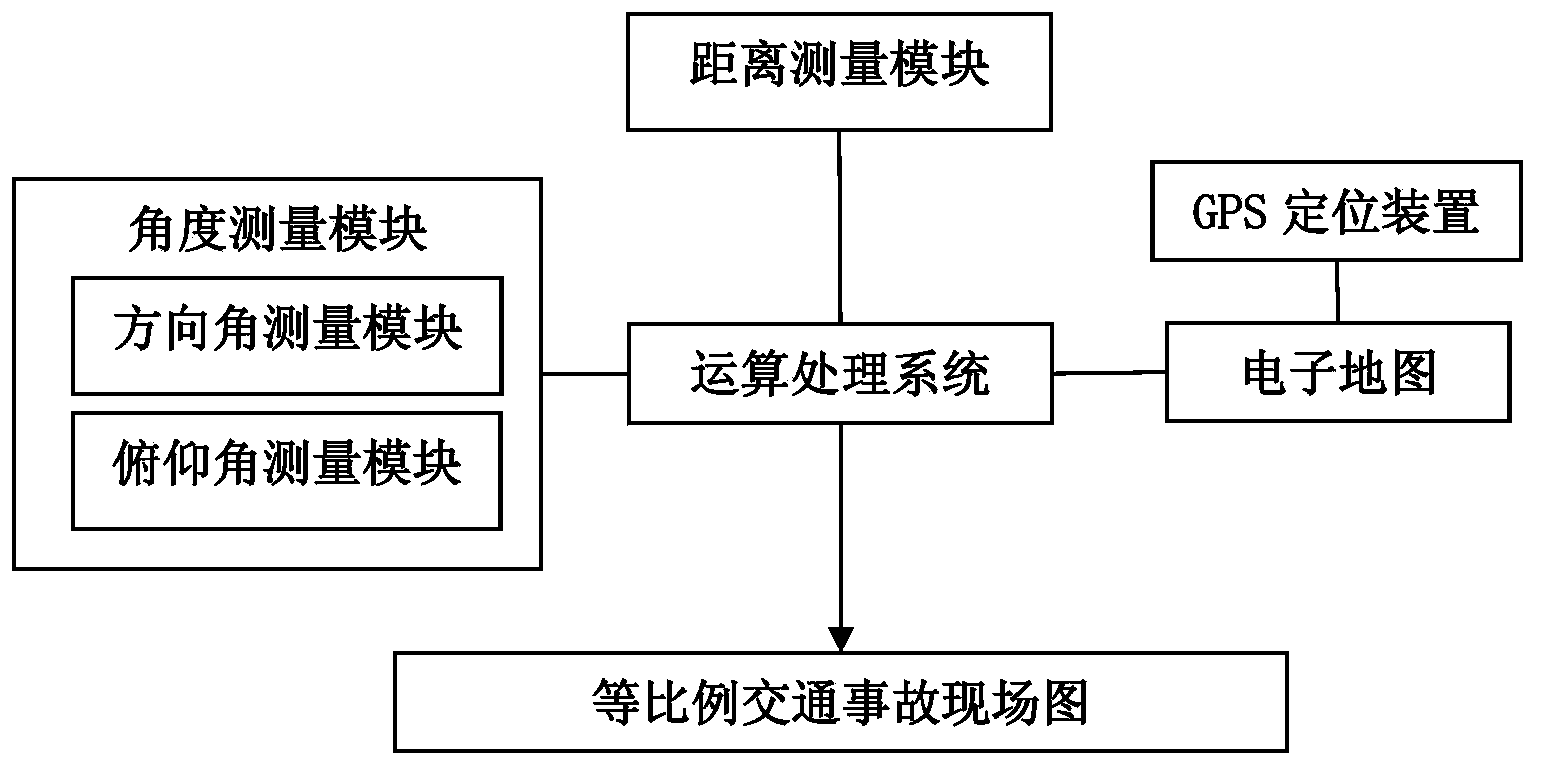
The invention provides an accident spot map generation method based on an electronic map and a data acquisition system and relates to the technical field of traffic accident spot information acquisition and analysis application. The accident spot map generation method requires the following components: a GPS positioning device, a data acquisition system and an operation treatment system, wherein the GPS positioning device is used for acquiring the position information of accident spots; the data acquisition system is used for acquiring the distance information and the angle information between an accident spot measurement site and a data information to-be-detected site, and particularly comprises a distance measuring module and an angle measuring module; the operation treatment system is used for processing the acquired distance information and angle information. Satellite images near the measurement site are acquired through the electronic map, and together with the image processing technology, an equal-proportion traffic accident spot map is created to provide more scientific, simpler and more convenient technical measures for traffic accident field survey and traffic accident spot map drawing.
Owner:THE THIRD AFFILIATED HOSPITAL OF THIRD MILITARY MEDICAL UNIV OF PLA
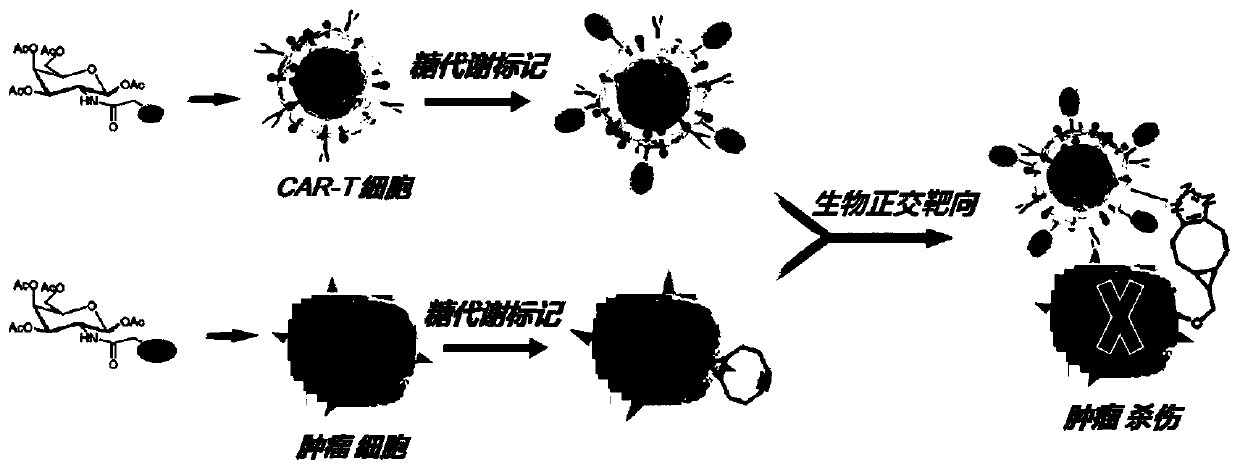
Manually target-modified CAR-T cells and preparation method and application thereof
ActiveCN110157682AImprove functional activityOvercoming off-target phenomenaImmunoglobulin superfamilyAntibody mimetics/scaffoldsT-Cell SpecificityBiological activation
The invention relates to the technical field of biological engineering, in particular to metabolically modified CAR-T cells and a preparation method and application thereof. According to the method, through biological orthogonal metabolic modification, the CAR-T cells can be effectively targeted and drawn to a tumor site in vivo; in-vivo targeting and drawing leads to combination of specific CAR molecules on the CAR-T cells with tumor antigens on the tumor site, correspondingly the specific activation of the CAR-T cells is stimulated, and a more efficient tumor killing capability is achieved.
Owner:SHENZHEN INST OF ADVANCED TECH
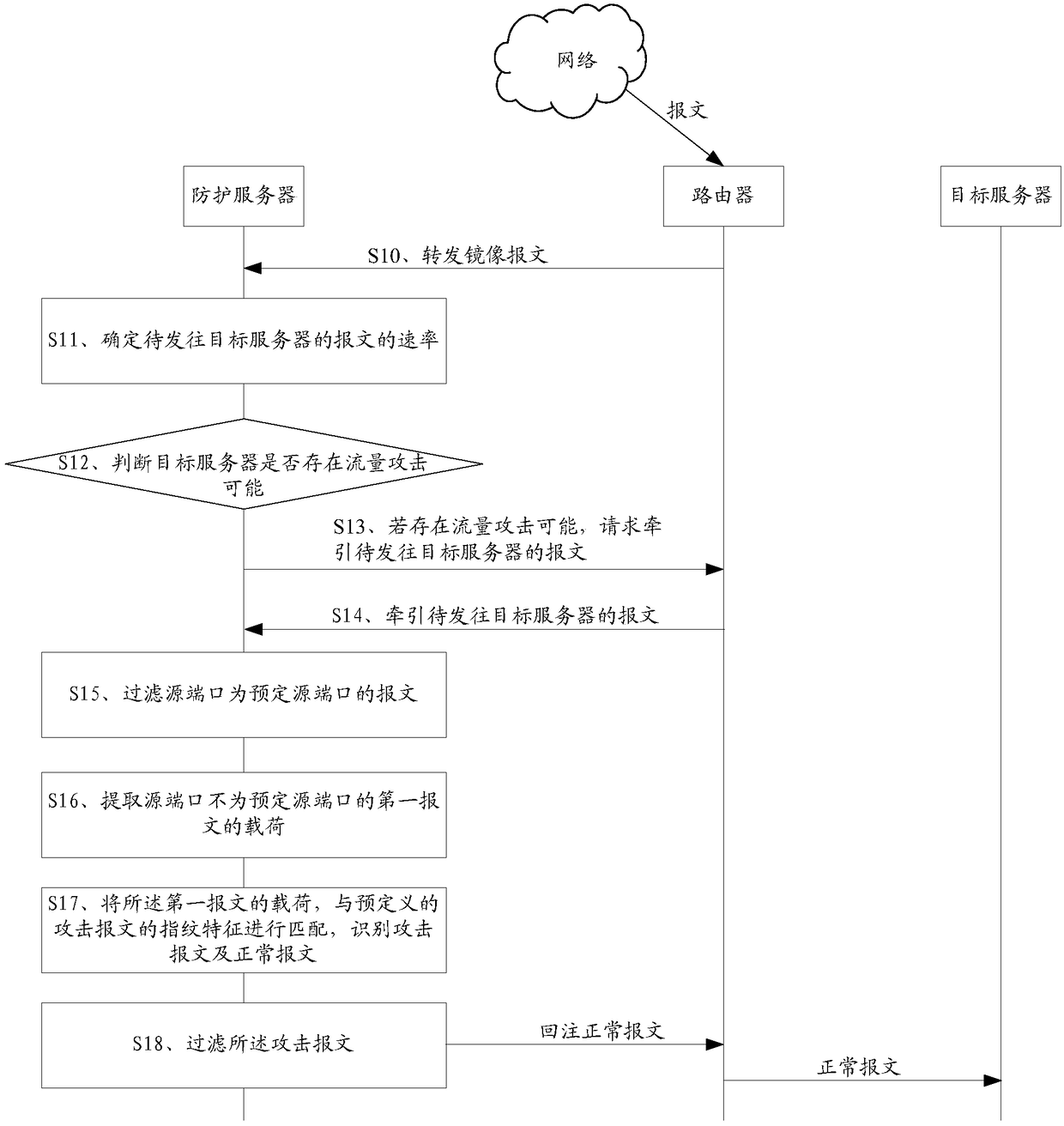
Traffic attack protection method and device, protection server and storage medium
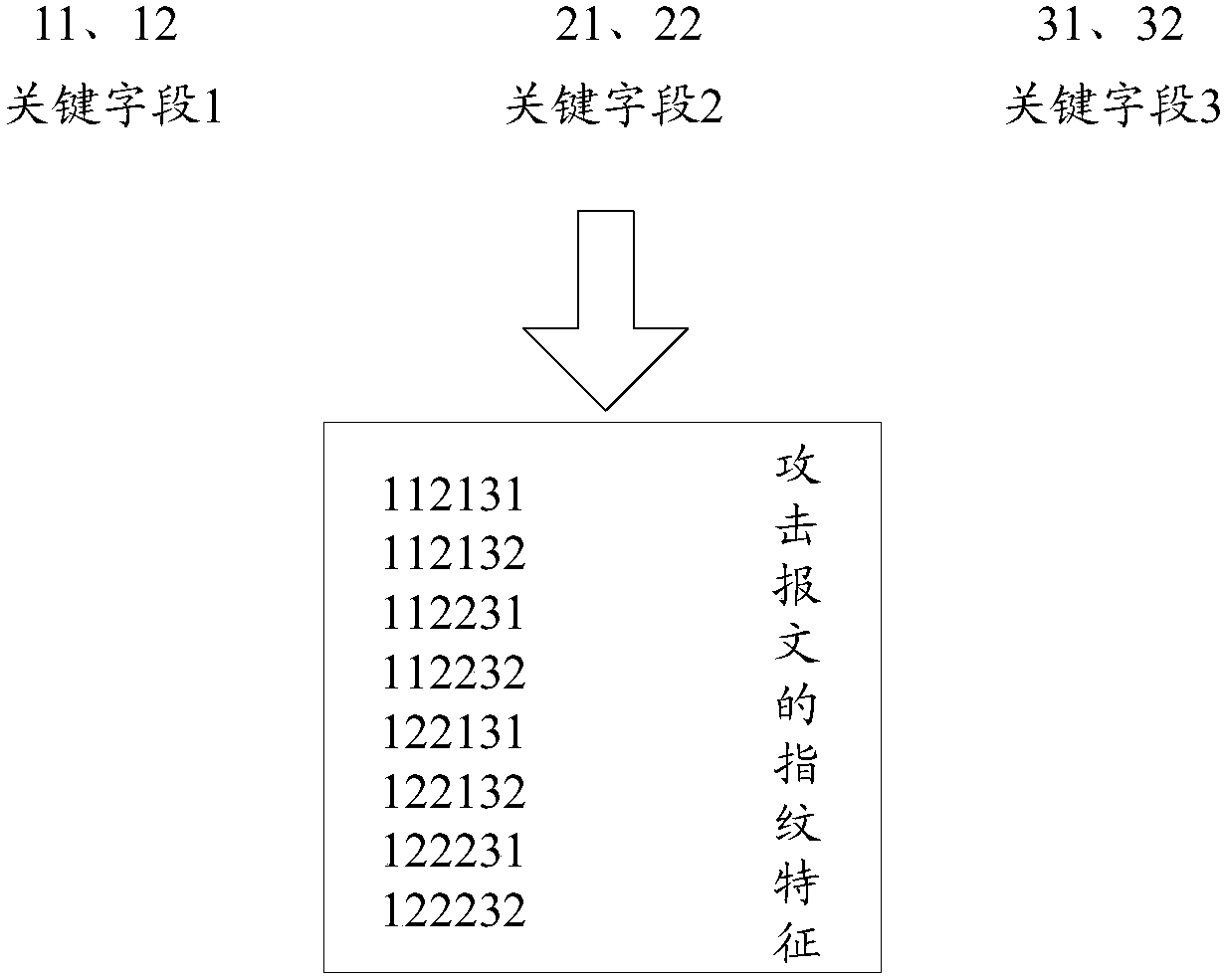
ActiveCN108566384AEffective identificationImprove filtering effectData switching networksService provisionProbable Case
Embodiments of the invention provide a traffic attack protection method and device, a protection server and a storage medium. The method comprises the following steps of acquiring a message to be sentto a target server under a condition that a traffic attack possibility exists in the target server; at least extracting a load of a message whose source port is not a preset source port from the message to be sent to the target server in order to obtain the load of a message to be matched; matching the load of the message to be matched with fingerprint features of a pre-defined attack message, and determining the attack message from the message to be matched, wherein the determined load of the attack message is provided with a character string corresponding to each key field defined by the fingerprint features; and filtering the attack message. According to the embodiments of the invention, the accuracy of traffic attack protection can be improved, a protection effect of the traffic attack is improved, and the normal service provision of the target server is guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
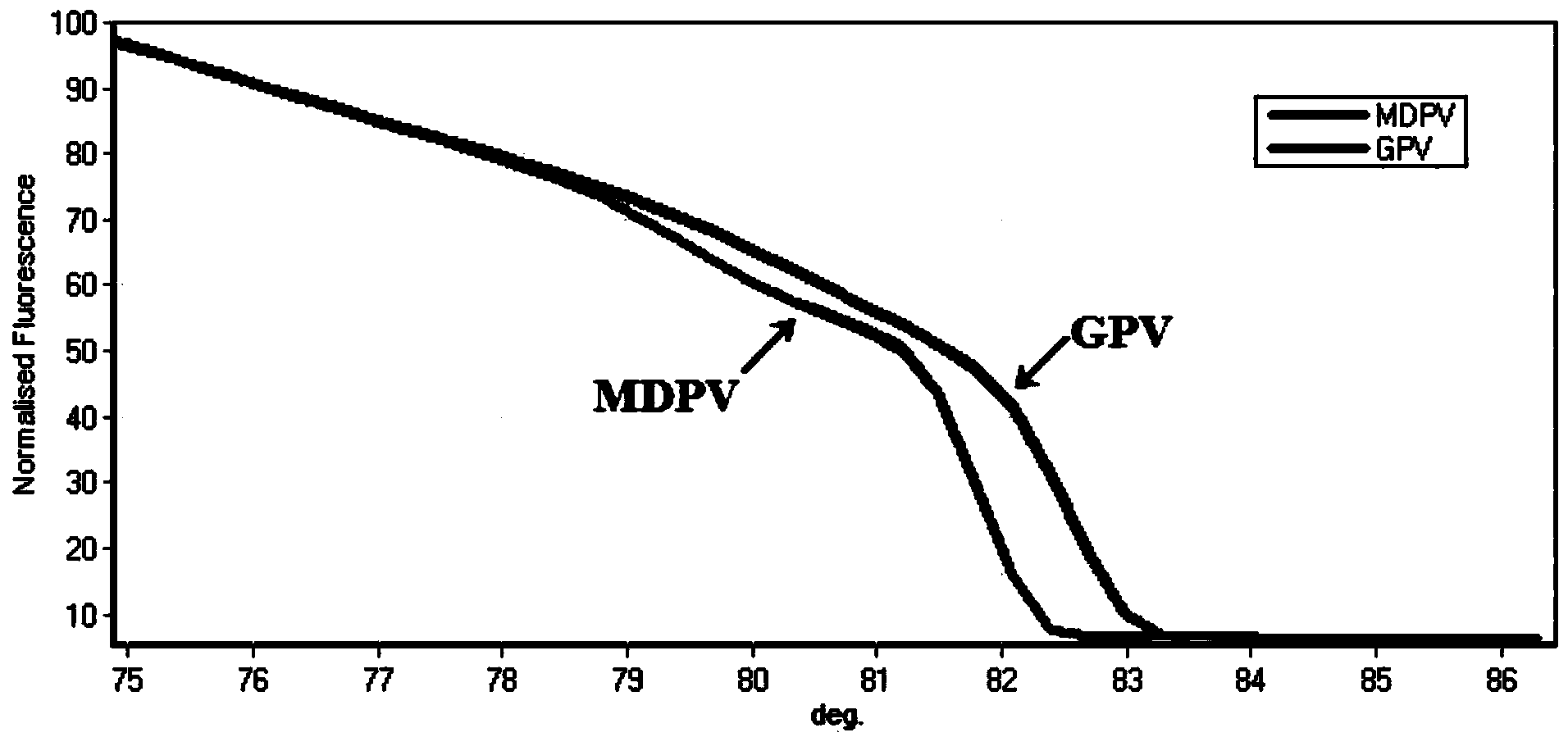
HRM (High Resolution Melt) identification method, kit and primer group for muscovy duck parvovirus and goose parvovirus
ActiveCN103866048AImprove stability and repeatabilityEffective identificationMicrobiological testing/measurementMicroorganism based processesViral genomesPolymerase chain reaction
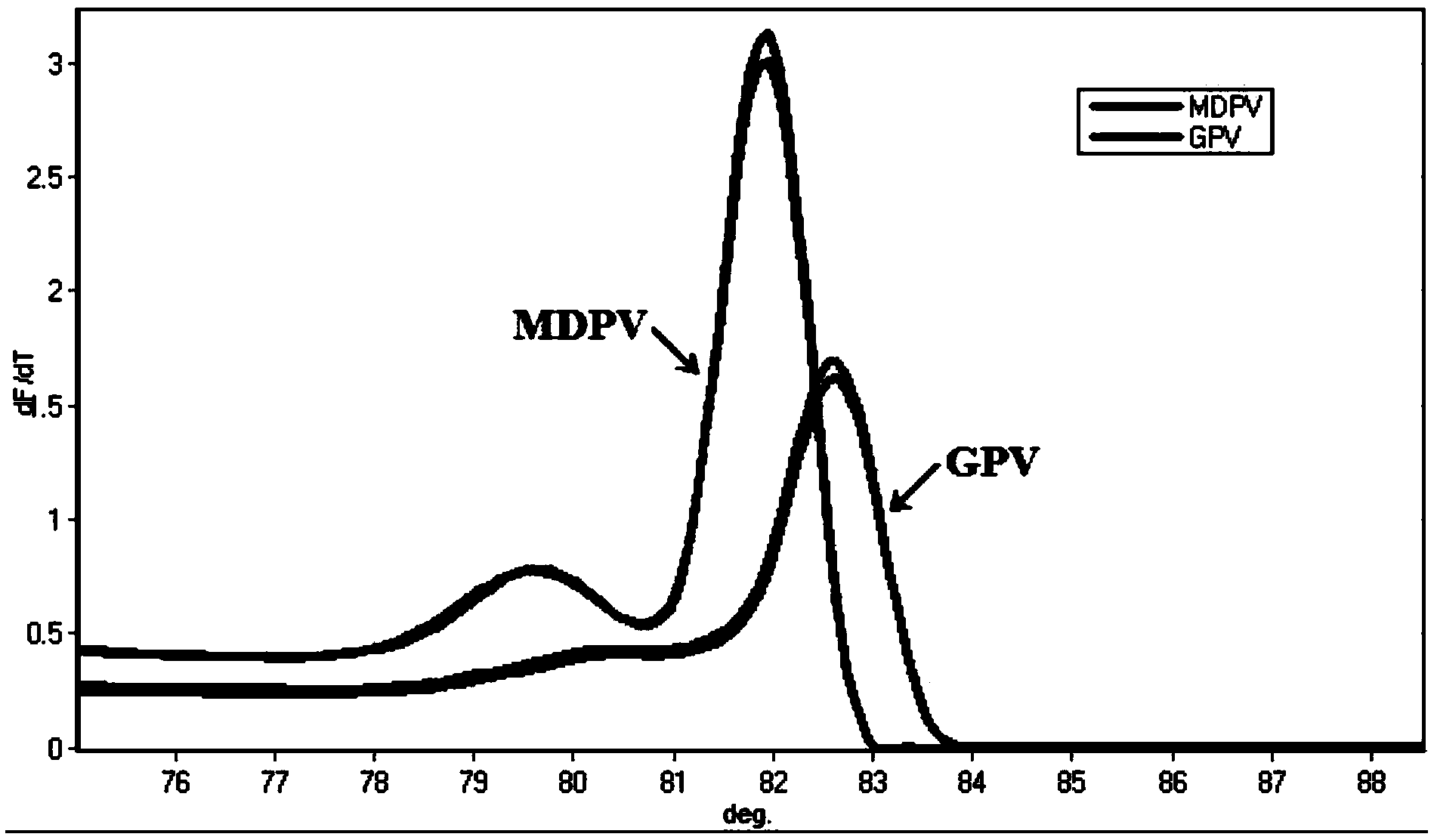
The invention discloses an HRM identification method, a kit and a primer group for muscovy duck parvovirus (MDPV) and goose parvovirus (GPV). A test method comprises the following steps: (1) designing a group of universal PCR primers capable of being used for simultaneously augmenting the muscovy duck parvovirus and the goose parvovirus; (2) extracting DNA (Deoxyribonucleic Acid) of a viral genome from a to-be-tested sample as template DNA; (3) treating the template DNA through a PCR (Polymerase Chain Reaction) amplification process by use of the primer group mentioned in the step (1); (4) treating an amplification product through HRM analysis, and identifying the MDPV and the GPV. The method disclosed by the invention can be used for rapidly and effectively identifying the MDPV and the GPV; high test speed and high throughput are achieved; the test of a PCR product of a 96 / 384 pore plate can be finished within 5-10 minutes, so that the test time is greatly shortened; no injury is caused to the PCR product, and subsequent analysis, such as sequencing and gel electrophoresis, can be implemented after the test.
Owner:INST OF ANIMAL HEALTH GUANGDONG ACADEMY OF AGRI SCI
Loess landform ditch line extraction method based on mean neighborhood
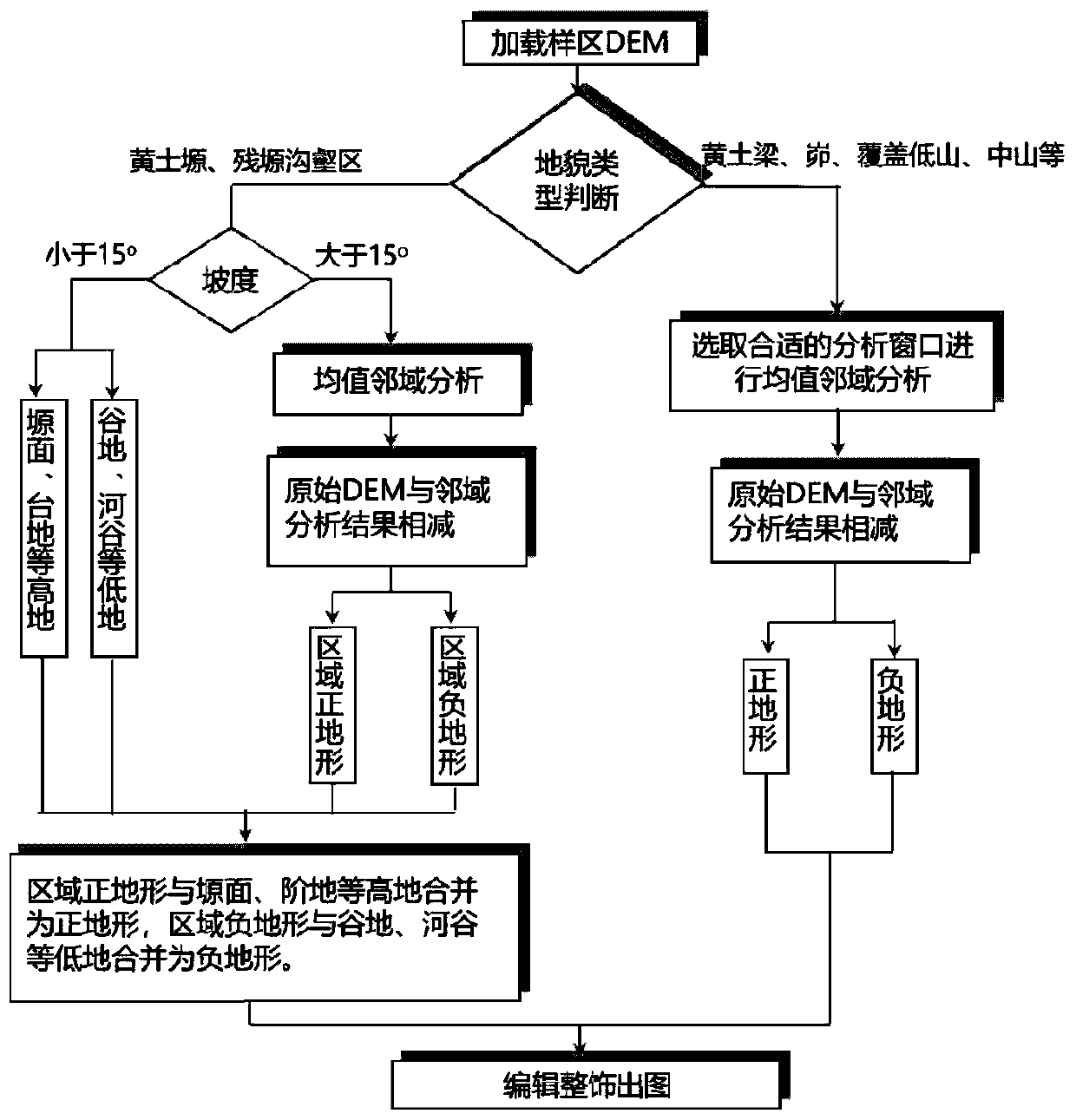
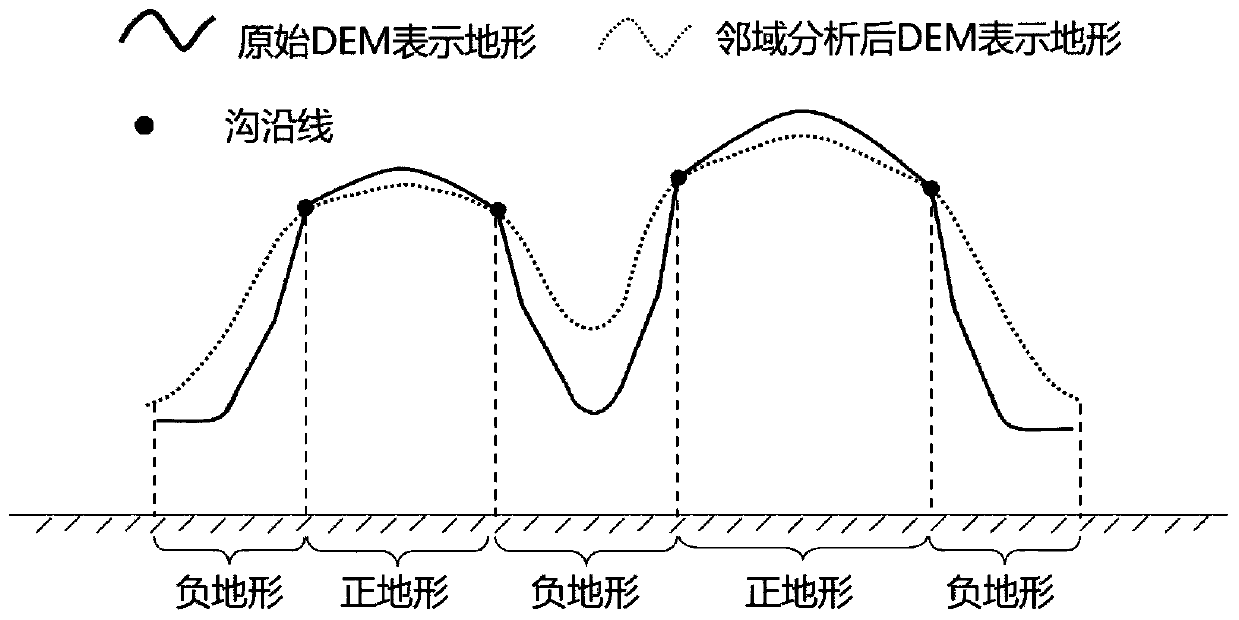
PendingCN110188398AAccurate data analysisThe recognition effect is accurateDesign optimisation/simulationSpecial data processing applicationsTerrainDitch
The invention discloses a loess geomorphic ditch line extraction method based on a mean neighborhood, which comprises the following steps of firstly, taking the high-resolution grid DEM data of a research region as the basic data, and selecting a proper analysis window to carry out the mean neighborhood analysis according to the geomorphic type of the research region; subtracting the original DEMdata of the research area from a neighborhood analysis result, and extracting the planar data of a normal terrain area; and finally, editing and modifying the orthotopographic map spots, converting the orthotopographic map spots into the line data, and screening out the ditch lines according to the geographic meaning of the ditch lines to obtain a final ditch line extraction result. According to the method for extracting the loess landform ditch line based on the DEM data and the mean neighborhood, the more accurate and effective extraction of the loess landform ditch lines can be achieved, meanwhile, an existing ditch line extraction method system is supplemented, and the method has the guidance and practical significance for the loess plateau research in actual work.
Owner:南京泛在地理信息产业研究院有限公司 +1
Server system based on address code of indoor equipment and realization method of server system
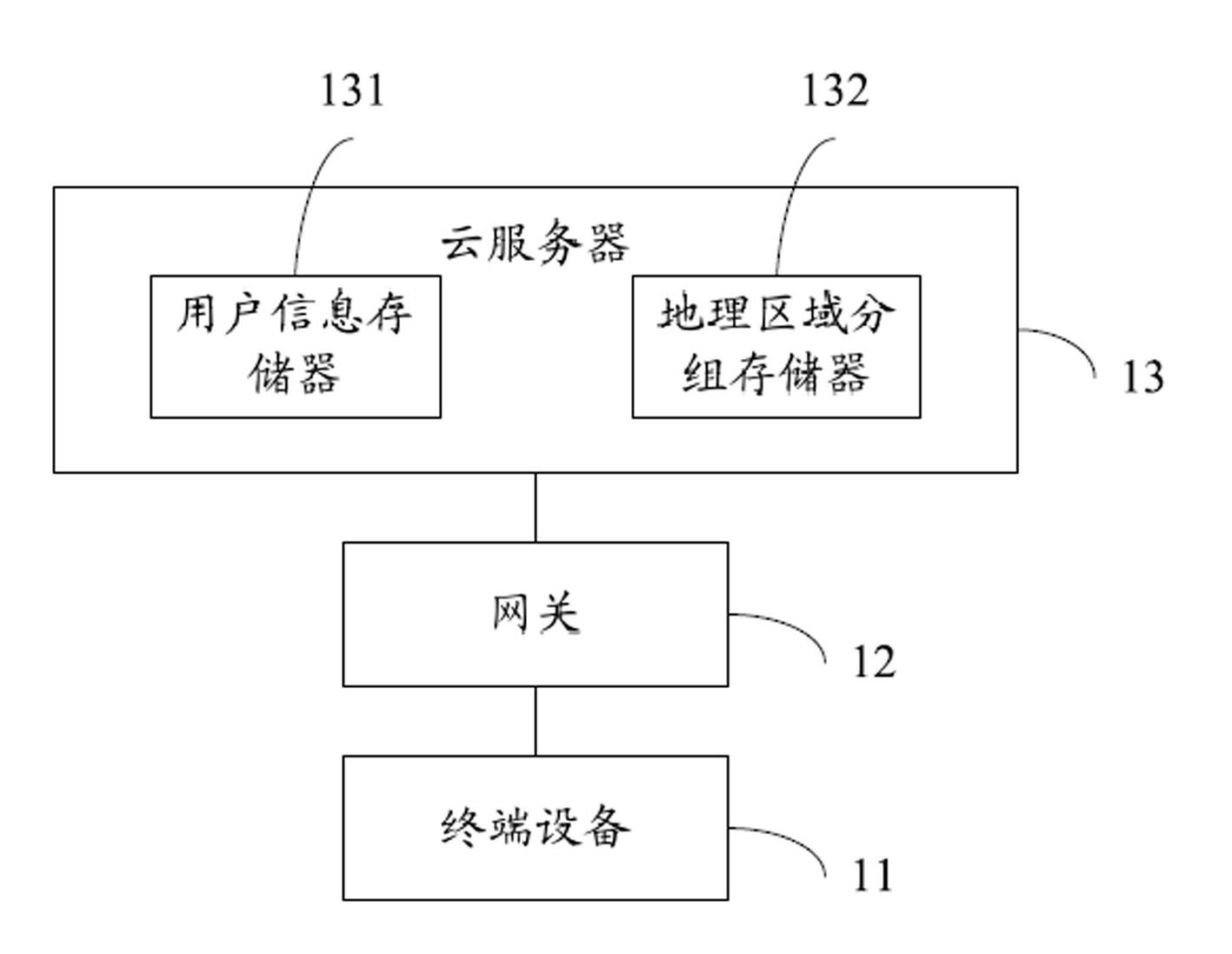
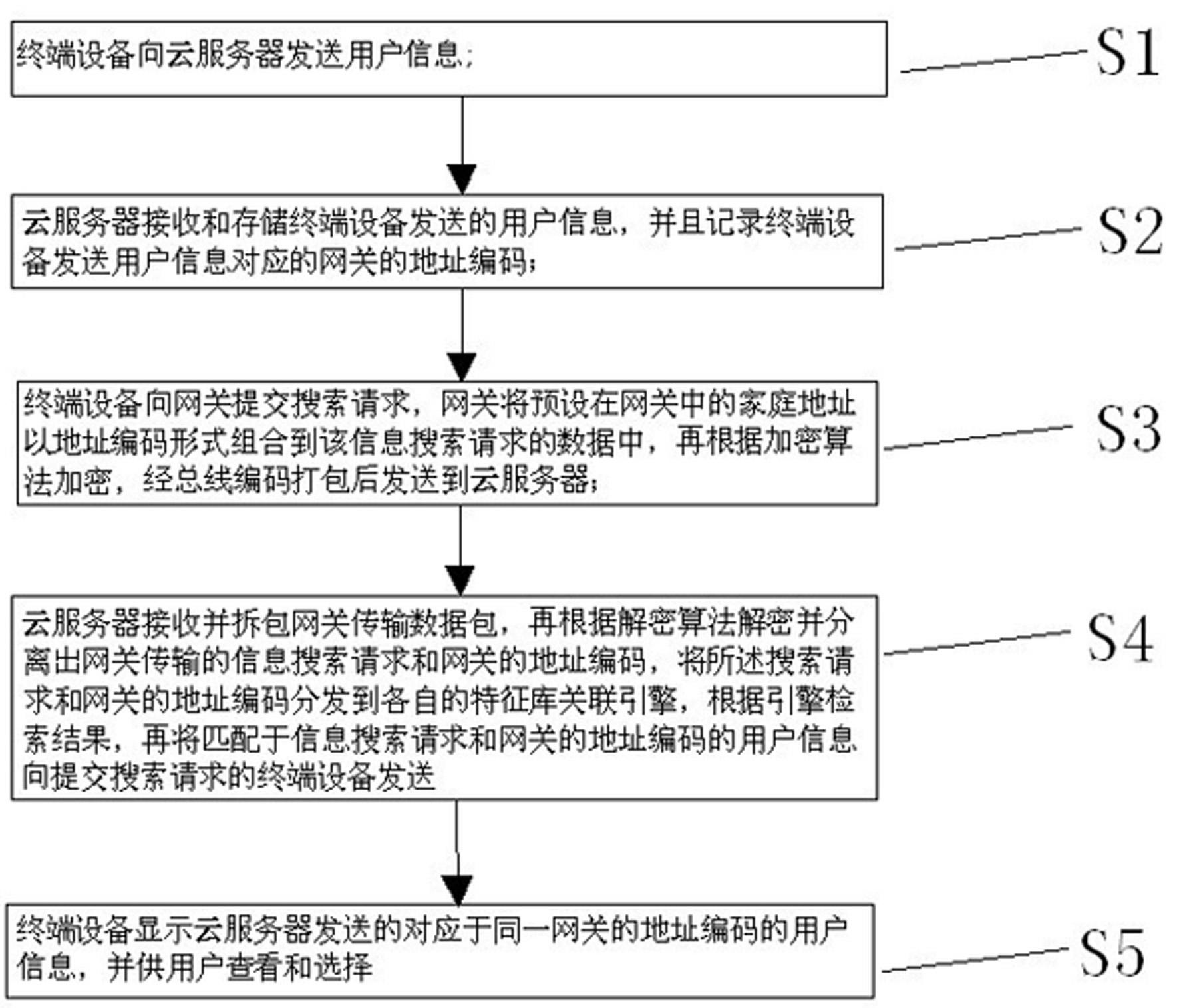
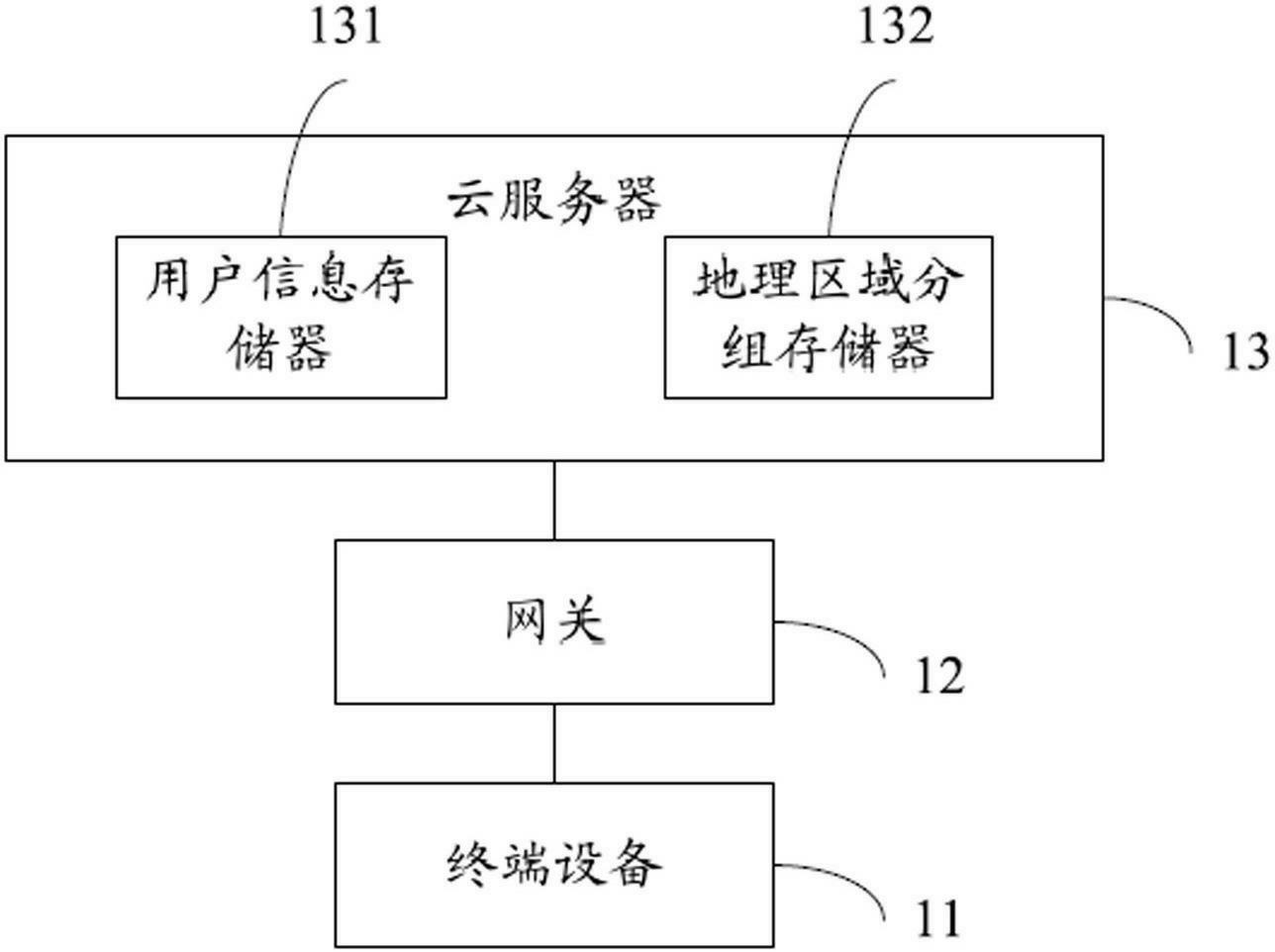
InactiveCN102624747AEffective identificationEfficient additionTransmissionNetwork packetTerminal equipment
The invention discloses a server system based on an address code of indoor equipment, which comprises terminal equipment, a gateway and a cloud server, wherein the terminal equipment is used for transmitting user information and for submitting a search request; the gateway is used for receiving and transmitting data transmitted and submitted by the terminal equipment; the cloud server is used for receiving and storing the user information transmitted by the terminal equipment, recording an address code of a gateway corresponding to the user information transmitted by the terminal equipment, receiving and unpacking an encrypted data packet transmitted by the gateway, then decoding and separating the search request and an address code of the gateway to be respectively transmitted to a characteristic library correlation engine, and transmitting the matched user information to the terminal equipment submitting the search request. The invention also provides a method for realizing the server system based on the address code of the indoor equipment. Due to the adoption of the server system and the method, users in the same community can be effectively identified and added, and moreover, whether the users belong to the same network or not can be verified.
Owner:XIAMEN SEED ELECTRONICS TECH
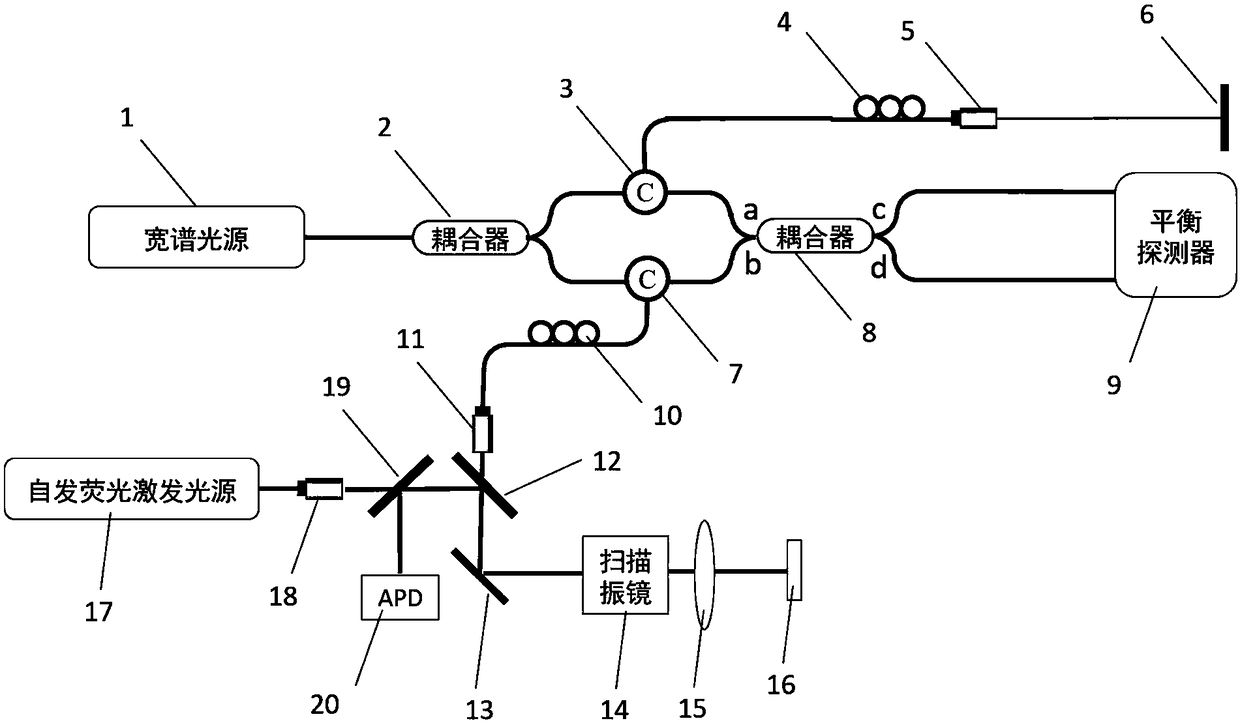
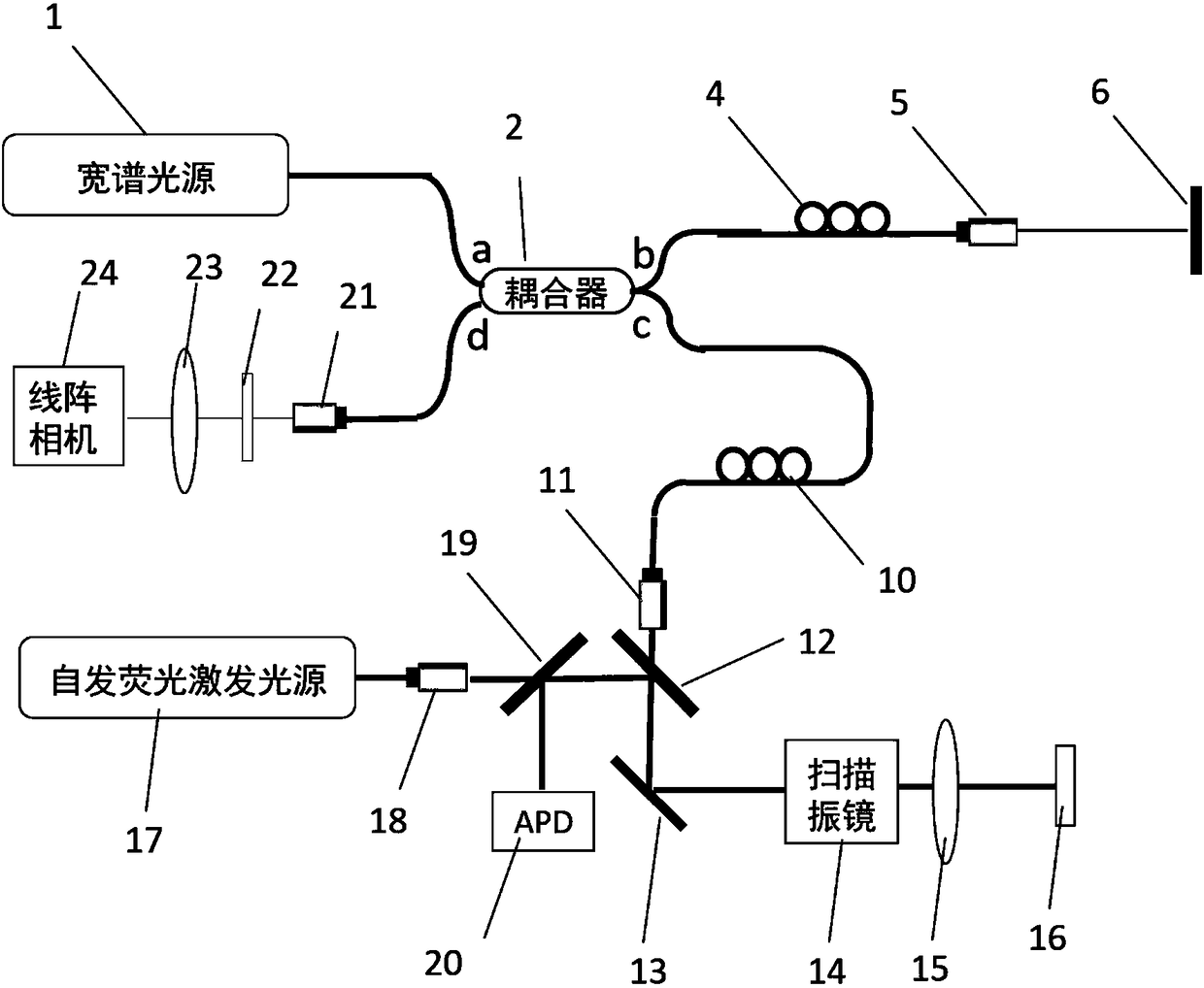
Thyroid gland neck tissue classifying and identifying system and method based on autofluorescence technology and optical coherence tomography
PendingCN108523849AEffective classificationEffective identificationDiagnostics using fluorescence emissionDiagnostics using tomographyThyroid gland operationsLymph fluid
Provided are a thyroid gland neck tissue classifying and identifying system and method based on an autofluorescence technology and an optical coherence tomography. The system organically integrates anautofluorescence system and an optical coherence tomography system, utilizes high-sensitivity tissue element resolution capability of the autofluorescence system and high-resolution tissue structureimaging of the optical coherence tomography system to achieve quick, identifier-free, nondestructive, high-sensitivity and real-time thyroid gland neck tissue classification and identification. By adopting the thyroid gland neck tissue classifying and identifying system and method, the classification and identification efficiency and accuracy of doctors to parathyroid glands, thyroid glands, fat,lymph glands and other neck tissues in clinic thyroid gland operation can be effectively improved, the doctors can be assisted to protect the parathyroid glands and thoroughly remove the lymph glands.
Owner:NANKAI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com