Method for encryption authentication on Ad hoc network transmission layer protocol
A network transport layer, encryption and authentication technology, applied in wireless network protocol, network traffic/resource management, advanced technology, etc., can solve the problem of high encryption strength of XOR operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
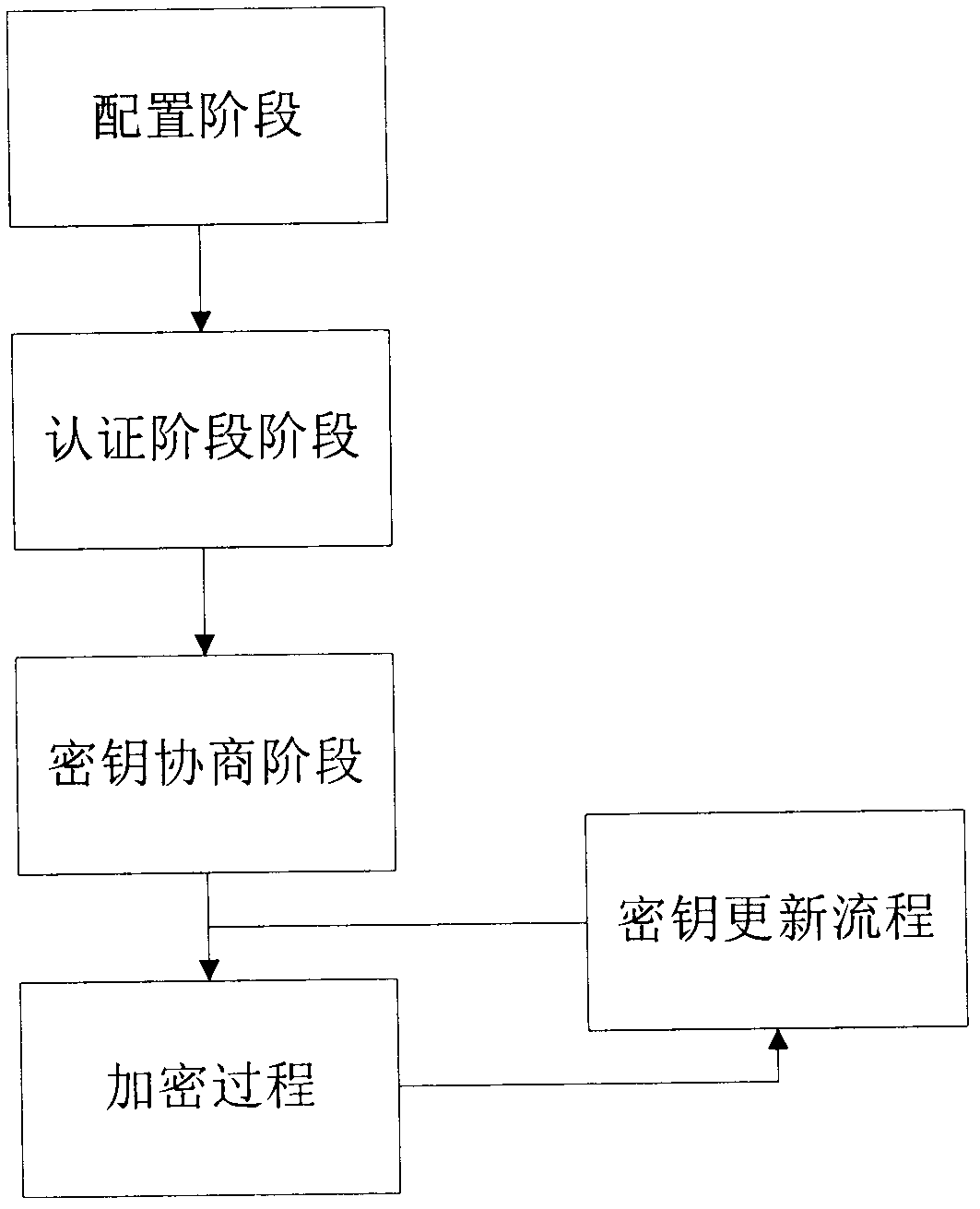
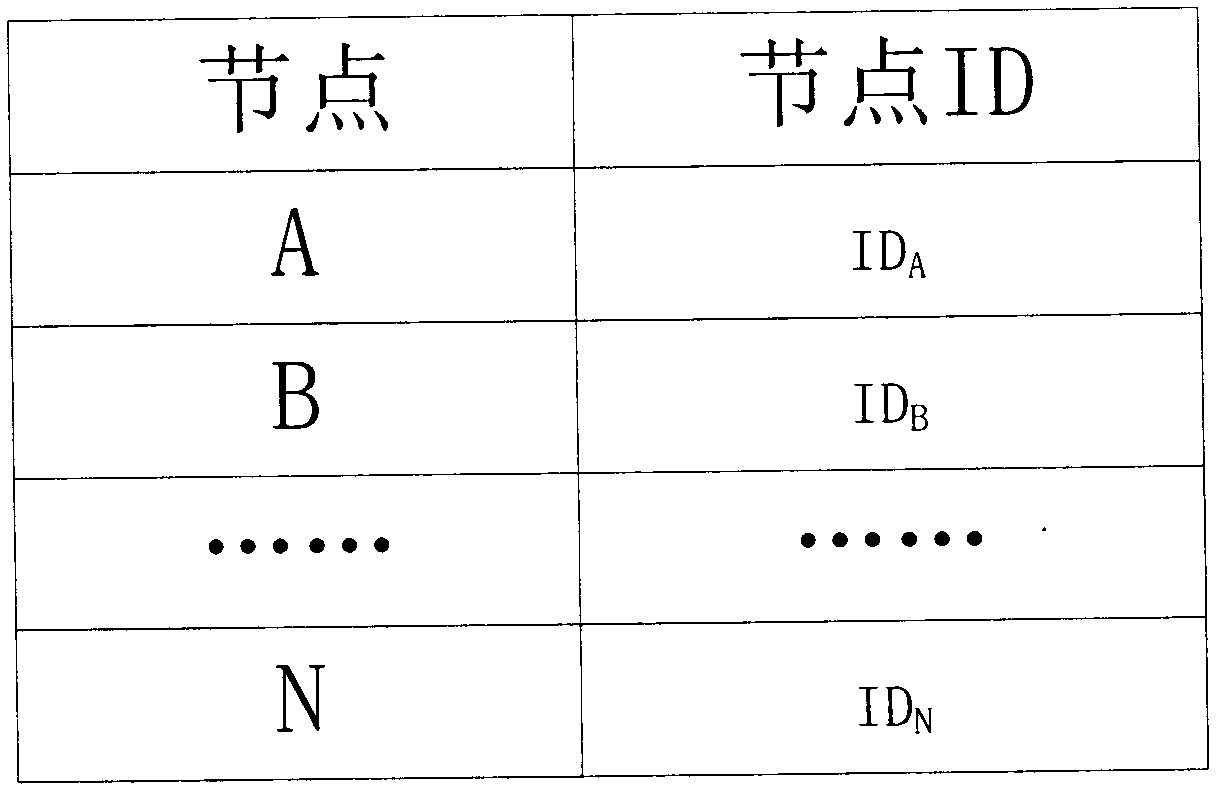
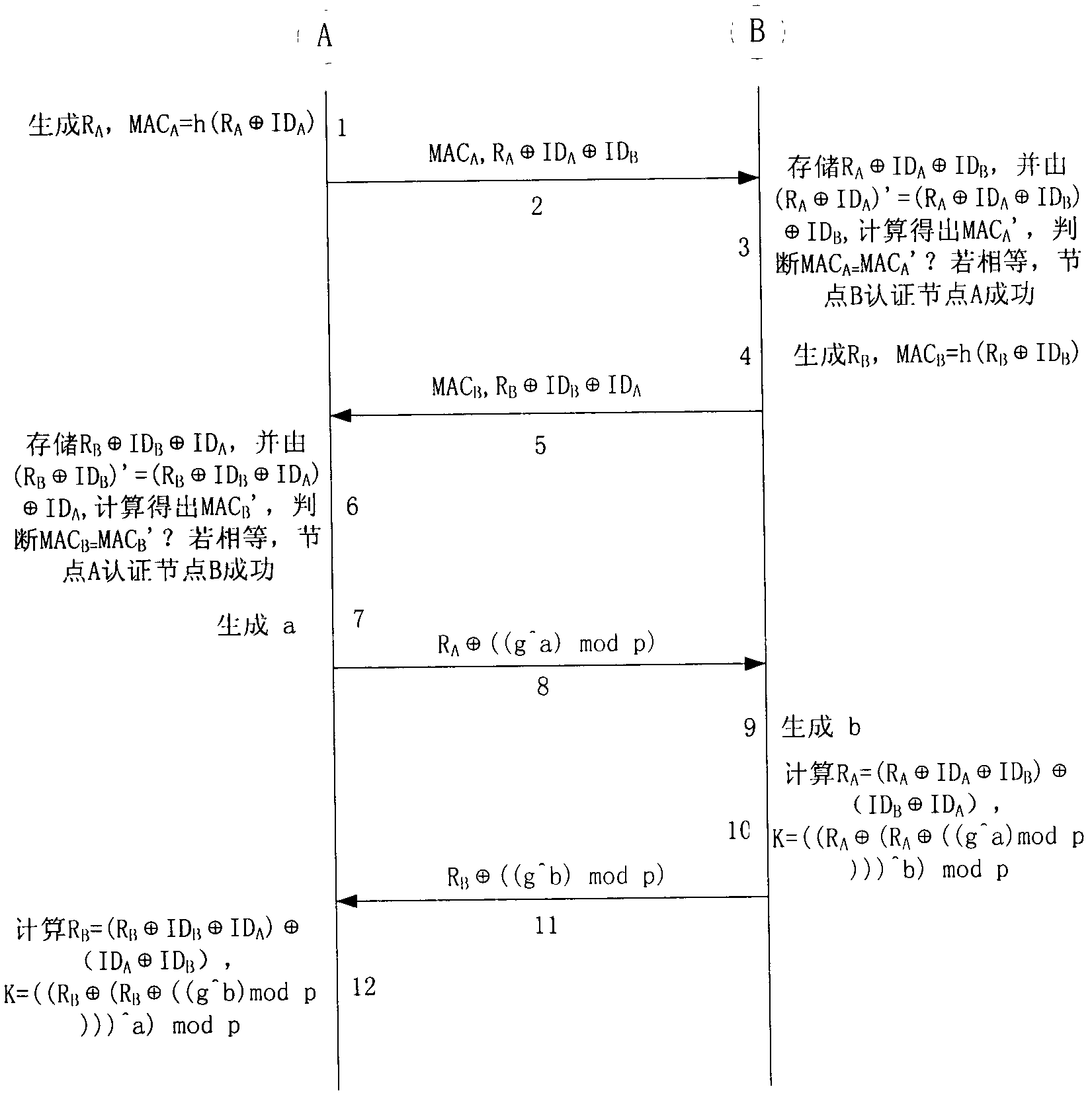
[0056] Because the present invention is mainly to set forth the thought that method realizes, concrete realization can adopt the most suitable realization method according to concrete implementation environment (network environment, node type etc.), can adopt when introducing the specific implementation manner of technical scheme of the present invention below Some specific methods (such as specific hash functions, etc.), but the actual implementation is not limited to the above methods. The specific implementation of the encryption and authentication method on the transport layer between two nodes will be described intuitively below in conjunction with the accompanying drawings, figure 1 It is a flowchart of the encryption authentication method; figure 2 is the node ID table; image 3 Encryption process for authentication; Figure 4 for the key update process. The specific implementation process is as follows.
[0057] Encryption and authentication methods on a kind of A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com