PE (portable executable) file pack detection method based on static characteristics
A technology of static features and detection methods, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of single judgment index and low accuracy of detection rules, and achieve high accuracy and good packing detection ability. , the effect of enriching file characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
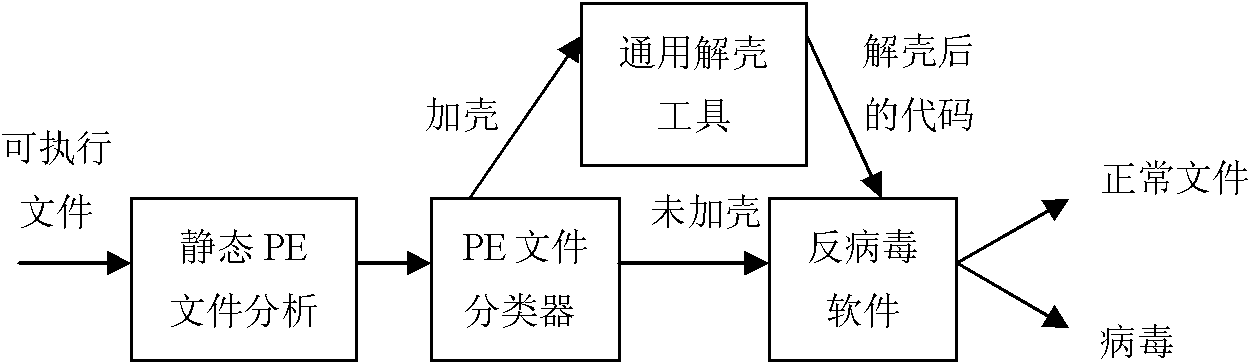
[0034] When the general-purpose unpacking tool detects malware, because it does not know in advance whether the PE file to be detected is packed, all PE files to be detected have to try to unpack them through actual execution before being detected by anti-virus software. shell. This introduces the problem of large amount of calculation and time-consuming. Aiming at this problem, the present invention proposes to detect whether the target PE file is packed or not before actually executing the target PE file to unpack it. Only PE files that are detected as packed are handed over to the general unpacking tool for unpacking processing; while PE files detected as unpacked are directly handed over to the anti-virus software for detection without being processed by the general unpacking tool.
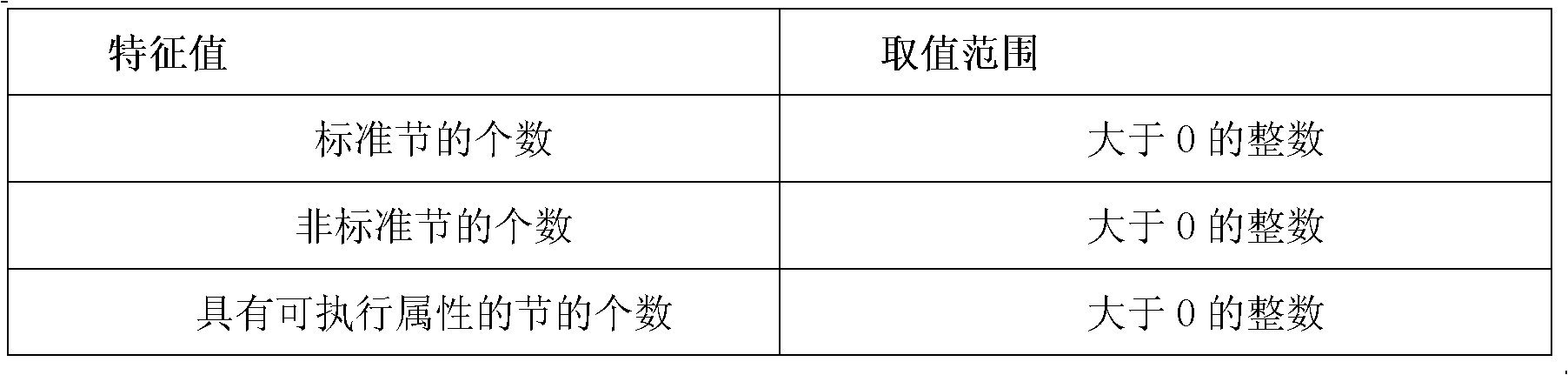
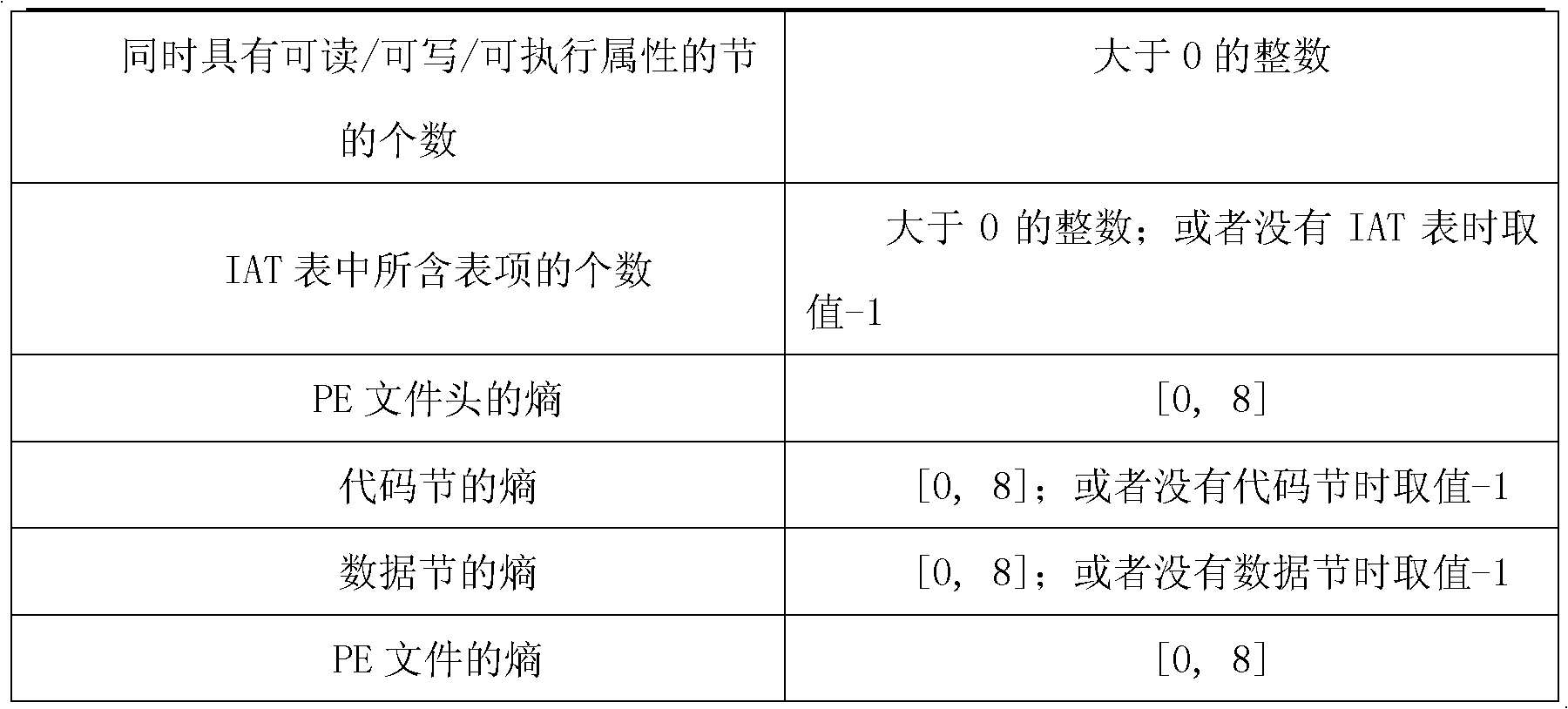
[0035] Virus creators often generate new packer tools by rewriting packer tools, so that traditional signature-based packer detection tools have the disadvantage of a high false negative rate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com