Dynamic malicious software detection method based on virtual machine and sensitive Native application programming interface (API) calling perception
A malware and dynamic detection technology, applied in computer security devices, instruments, electronic digital data processing, etc., can solve the problems of low false alarm rate and false alarm rate, static detection method is difficult to detect malware, and the accuracy rate is reduced. , to achieve the effect of high detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
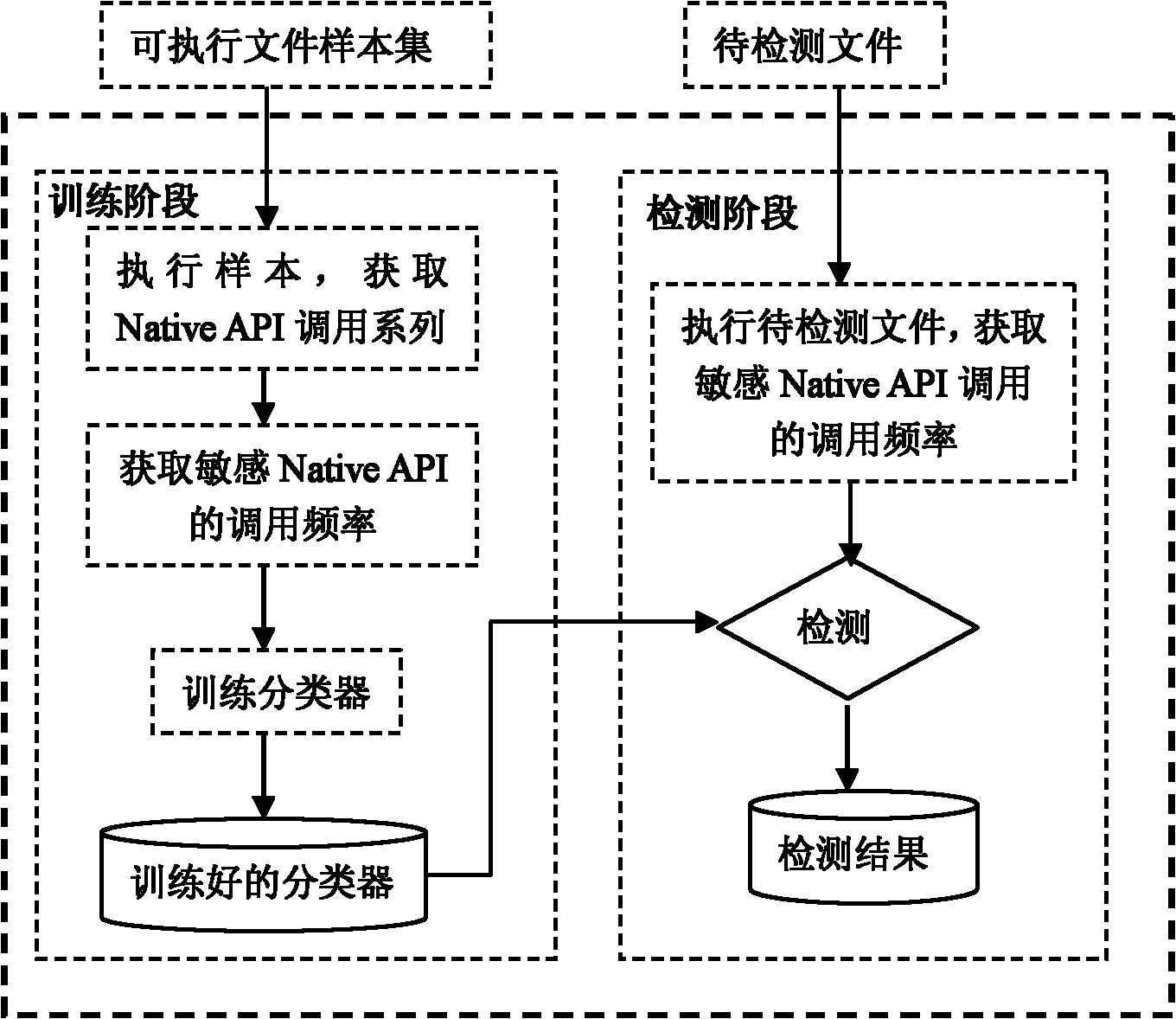
[0032] Detection model and basic idea:
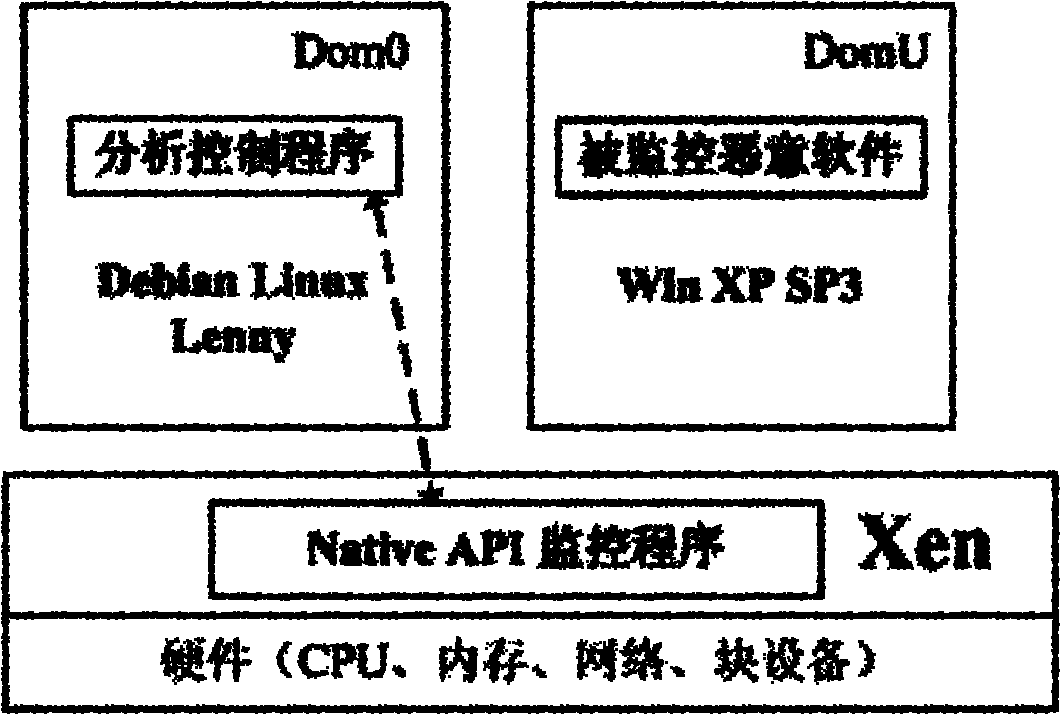
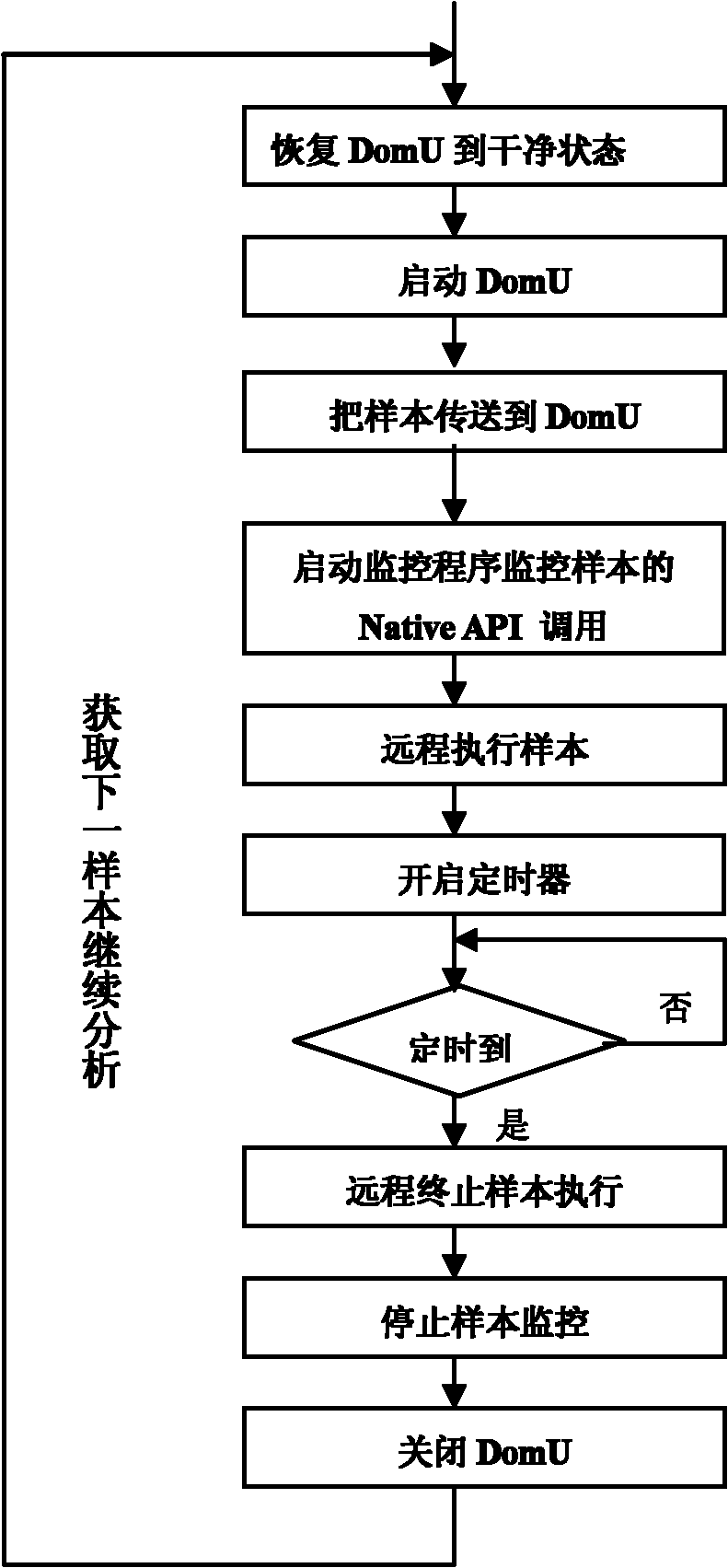
[0033] The idea on which the present invention is based is that malicious software must have some special functions, which makes the behavior of malicious software different from ordinary programs. Therefore, the behavior of the monitoring program can be used as a feasible method to judge whether the program is malicious software. Malware differs from normal programs mainly in that it performs some special actions to spread and damage the system. Whether it is binary executable virus, script virus or macro virus, they are all programs, which need to call various functions provided by the operating system to achieve the purpose of propagating itself and destroying the system. Various malicious behaviors of malware are manifested as various API calls in the implementation code. If the API calls corresponding to these behaviors can be detected, the corresponding dynamic behaviors have been detected. Therefore, it is an effective method t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com