Communication method based on inter-column security communication network protocol of reactor protection system
A technology for reactor protection and communication network, which is applied in the communication field based on the safety communication network protocol between columns of a reactor protection system, can solve the problems of uncertain transmission time of data frames, can not meet the real-time communication between columns, etc. Identify, avoid cyber conflict and competition, and avoid the effects of uncertainty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
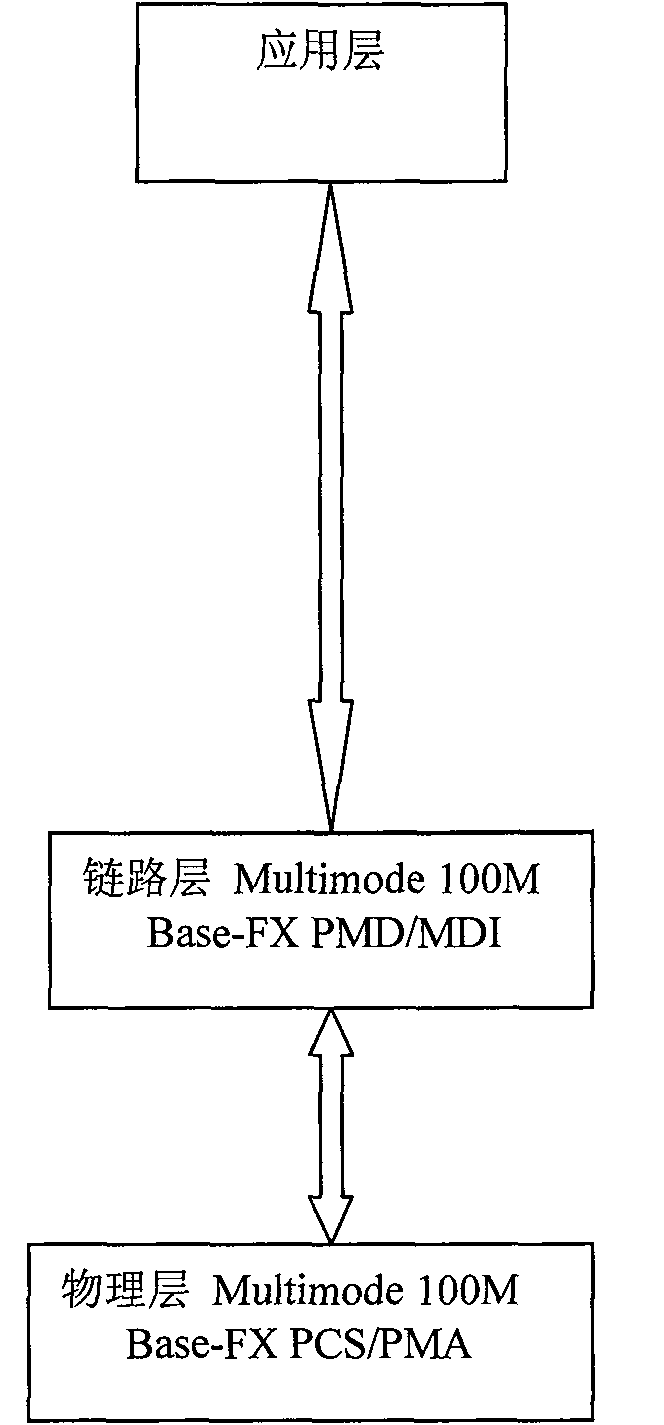
[0030] The security network protocol complies with the network interconnection model OSI (Open System Interconnect) researched by the ISO (International Organization for Standardization) organization in 1985 in terms of architecture and service definition. like figure 2 The shown secure network protocol consists of three network layers: application layer, data link layer and physical layer. The realization method of the MAC sublayer describing the physical layer and the data link layer follows the IEEE802.3 standard; the receiving and sending of data use the standard Ethernet interface. The application layer protocol defines the structure of the data frame and the realization requirements of the network equipment, and clearly defines the hardware equipment such as the specific physical medium. This embodiment is described according to the order that the high level sends a request to the low level, and the low level provides services for the high level.
[0031] In terms of ...
Embodiment 2
[0037] In terms of the application layer, the protocol requires both parties to use asynchronous communication, and the receiver cannot send a response frame to the sender. Both sending and receiving of network devices use 10ms. When reading network data, you can only use periodic query to read network data frames, and you cannot use interrupts to read network data. The total length of the application layer data frame is defined as 512 bytes, and the data frame of the application layer is specified.
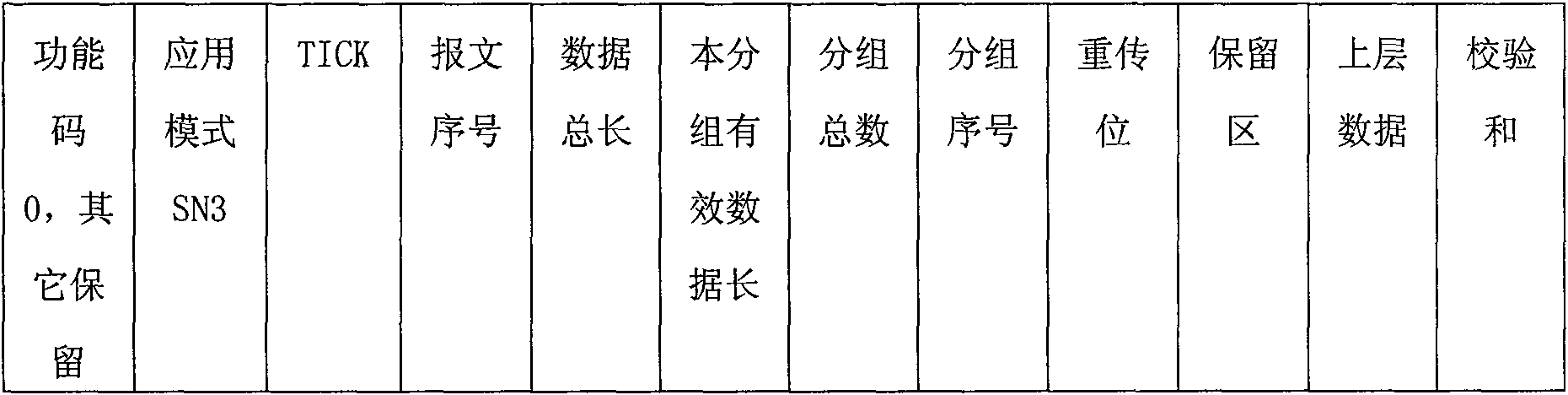
[0038] like Figure 4 The function code shown has a specific mark on the data mode, which is used to distinguish whether the content in the data communication is a control command or the collected protected data information; the application mode subdivides the mark of the protocol occasion; determines the amount of data in this occasion and the The response speed in the occasion; the four-byte TICK code is used to identify the data packet, which is convenient for sending the da...
Embodiment 3
[0041] In terms of the application layer, the protocol requires both parties to use asynchronous communication, and the receiver cannot send a response frame to the sender. Both transmission and reception of network devices use 25ms. When reading network data, you can only use periodic query to read network data frames, and you cannot use interrupts to read network data. The total length of the application layer data frame is defined as 1000 bytes, and the data frame of the application layer is specified.
[0042] like Figure 4 The function code shown has a specific mark on the data mode, which is used to distinguish whether the content in the data communication is a control command or the collected protected data information; the application mode subdivides the mark of the protocol occasion; determines the amount of data in this occasion and the The response speed in the occasion; the four-byte TICK code is used to identify the data packet, which is convenient for sending ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com