Parallel application performance vulnerability analysis method and system based on fuzzy rule reasoning
An analysis method and technology of application performance, applied in special data processing applications, electrical digital data processing, instruments, etc., can solve the problems that the analysis results are not scientific, objective, affect performance, and misjudgment rate, etc., and achieve scalability. Parallel program performance analysis, the effect of promoting refining and summarizing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] Embodiment 1: The present invention’s parallel application performance vulnerability analysis method based on fuzzy rule reasoning firstly abstracts various situations that lead to inefficient parallel program performance, obtains a parallel program performance characteristic model, and constructs a parallel program performance vulnerability characteristic model reasoning rule base, and then
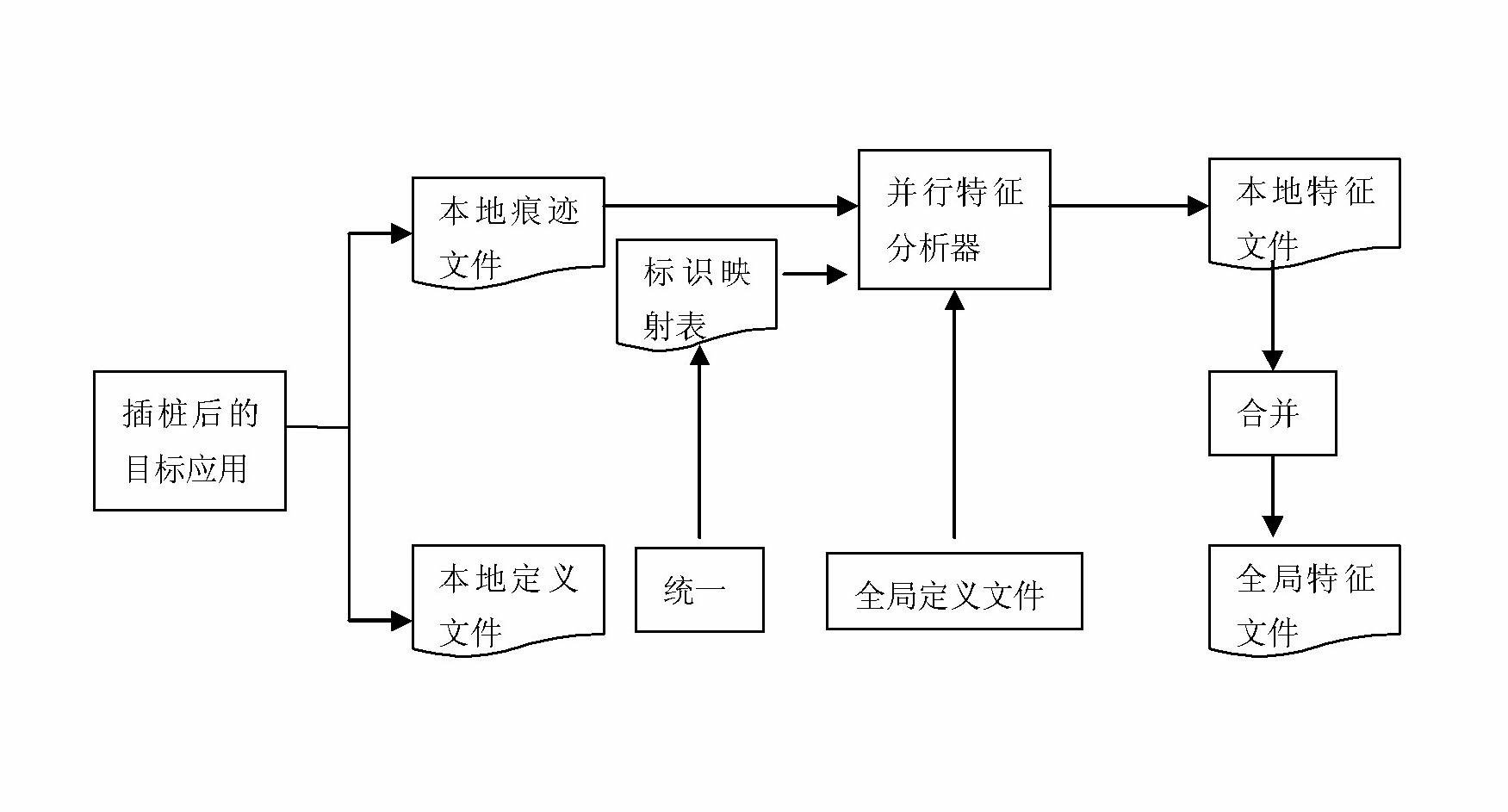
[0023] 1) Use the replay-based parallel trace analysis method to extract trace file features. Through distributed storage and parallel processing technology, replay the original communication on the same number of CPUs as the actual execution of the application program, so that each process can independently analyze the local Trace data, when traversing the trace data, according to the importance of each event area and related system resources, identify the required features and generate feature files;
[0024] 2) Introduce the fuzzy mathematics method into the definition and reas...
Embodiment 2
[0025] Embodiment two: this embodiment combines Figure 1 to Figure 4 , to further illustrate the specific implementation of the method for analyzing the vulnerability of parallel application performance based on fuzzy rule reasoning in the present invention. The analytical methods include:
[0026] 1. Mode definition
[0027] In order to better describe performance vulnerabilities, various execution behaviors that affect program execution performance are abstracted to form a performance model, which establishes a basis for the definition of rules.
[0028] (1) Abstract mechanism
[0029] A compound event is a collection of events in a trace file that satisfy conditions related to a specific performance problem. Although there are different types of events, each with different properties, each event provides at least a time property and a position property that represents the flow of control that caused it to occur. This representation of program execution is called the "e...
Embodiment 3
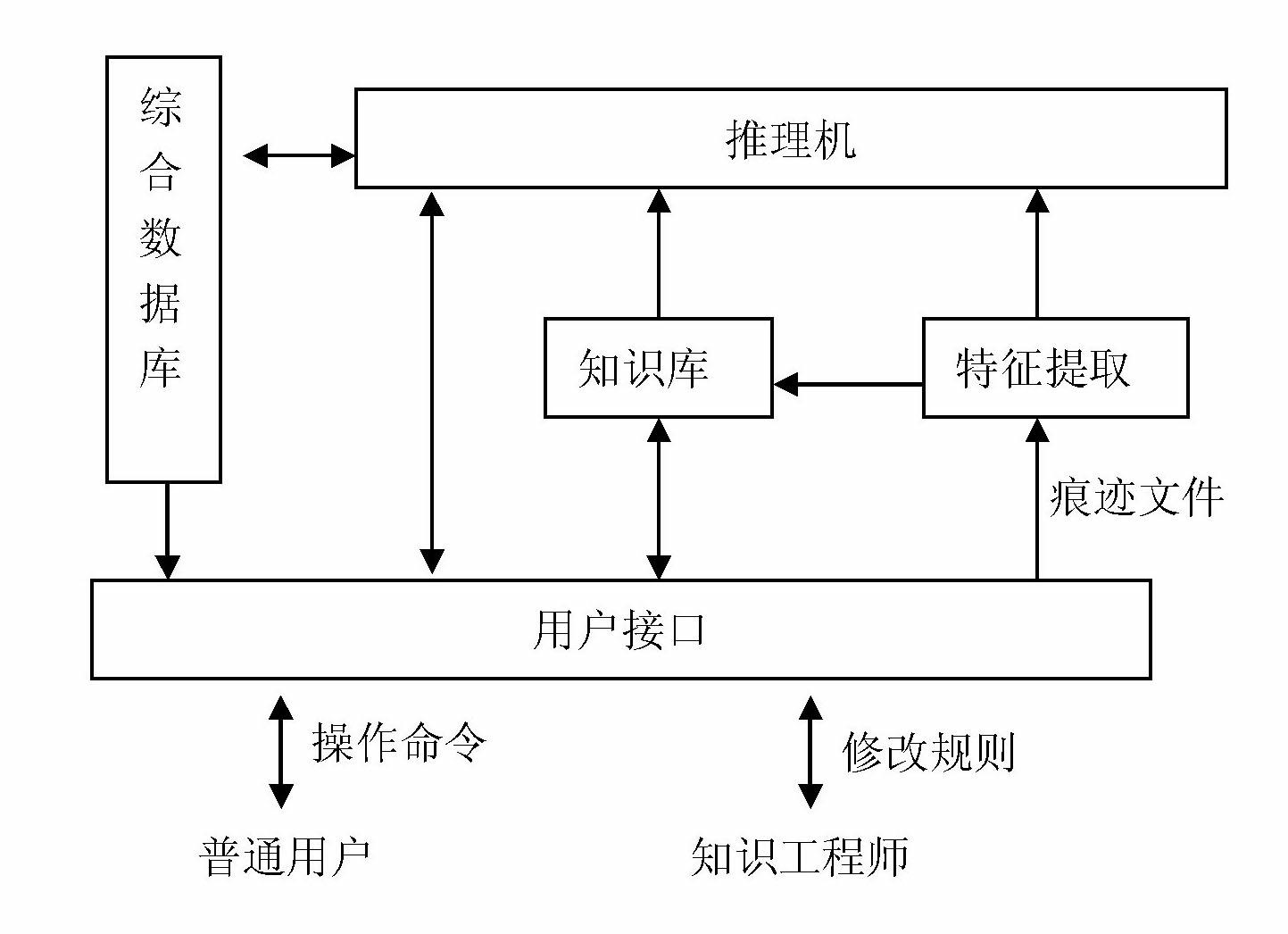
[0087] Embodiment three: see figure 1 , this embodiment is a parallel application performance vulnerability analysis system based on fuzzy rule reasoning, which realizes auxiliary decision-making for parallel application performance vulnerability analysis and discovery, and its system composition is as follows figure 1 Shown: The system is mainly composed of inference engine, knowledge base, feature extraction module, comprehensive database and user interface module.
[0088] The knowledge base stores judgmental knowledge of expert experience used for reasoning of conclusions and problem solving, as well as various control knowledge in the process of reasoning and solving. The core of the system is knowledge, and its performance depends on the quantity, quality and representation of knowledge in the knowledge base. The knowledge representation method determines the organizational structure of the knowledge base and directly affects the work efficiency of the whole system.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com