Computer network environment isolation system implemented by using software
A computer network and software implementation technology, applied in computer security devices, internal/peripheral computer component protection, calculation, etc., can solve the problems of inconvenient operation and high cost, and achieve the effect of good compatibility and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
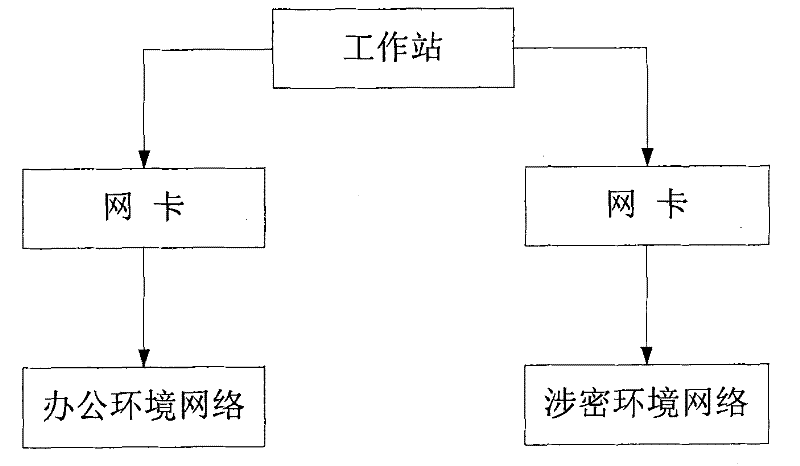
[0019] figure 1 Shows the hardware structural diagram of realizing computer environment isolation among the present invention, as figure 1 As shown, the computer is equipped with two physical network cards, and the network environment is dual wiring, wherein the one network card is connected to a non-secret network (such as an office subnet, the internet, etc.), and the other network card is connected to a secret network. Further, on the computer, a secret-related working environment is created through a virtual platform creation module: a virtual operating system is created through process monitoring and virtual desktop technology, and the virtual disk in the virtual operating system is used as a working disk in a secret-related working environment, Define the user name and password for entering the confidential environment; all data gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com