Method and system for controlling terminal unit
A technology for terminal equipment and control terminals, applied in transmission systems, instruments, electrical digital data processing, etc., can solve the problem that the network side cannot reverse control data to terminal equipment, etc., to improve efficiency, enhance comprehensive command and remote dispatch effect of ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] The public security intranet framework corresponding to the embodiment of the present invention includes a VPN (Virtual Private Network, virtual private network), a secure access platform, and a public security intranet; wherein, the VPN is the basis of the operator in the 3G (third generation mobile communication) network The private network constructed by adding tunneling technology and security encryption technology on the Internet; the secure access platform is deployed on the border of the public security intranet, which is built by the Ministry of Public Security in accordance with the security access specifications of the network border and adopts the method of distinguishing link security defense with border protection, The boundary access platform for identity authentication, application security, security isolation, and the platform's own security protection functions realizes the isolation between the VPN and the public security intranet; Independent network, ...
Embodiment 2
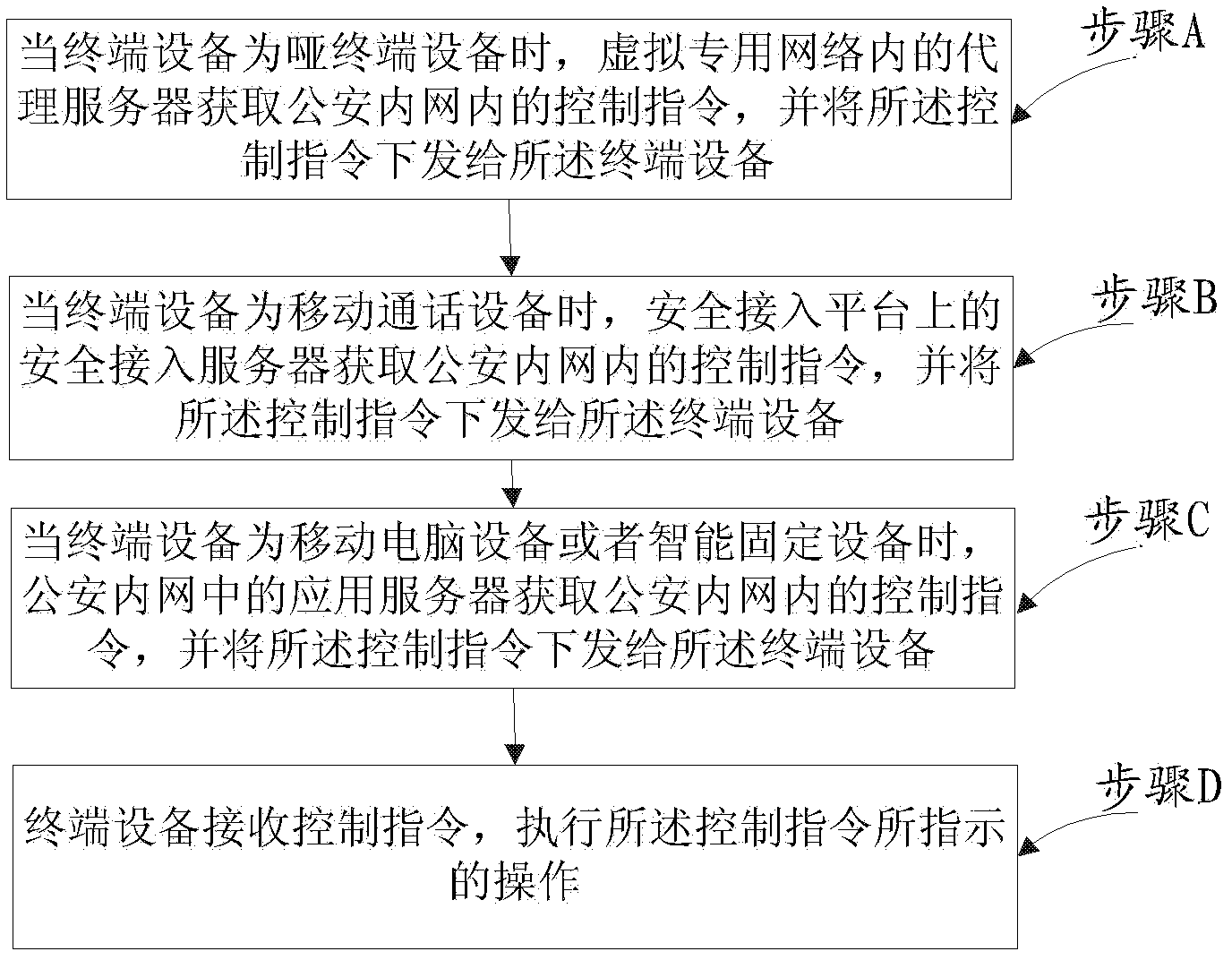
[0117] see Figure 5 , a system for controlling terminal equipment, the system comprising:
[0118] The proxy server 401 in the virtual private network is used to obtain control instructions in the public security intranet when the terminal equipment 404 is a dumb terminal equipment, and issue the control instructions to the terminal equipment 404;
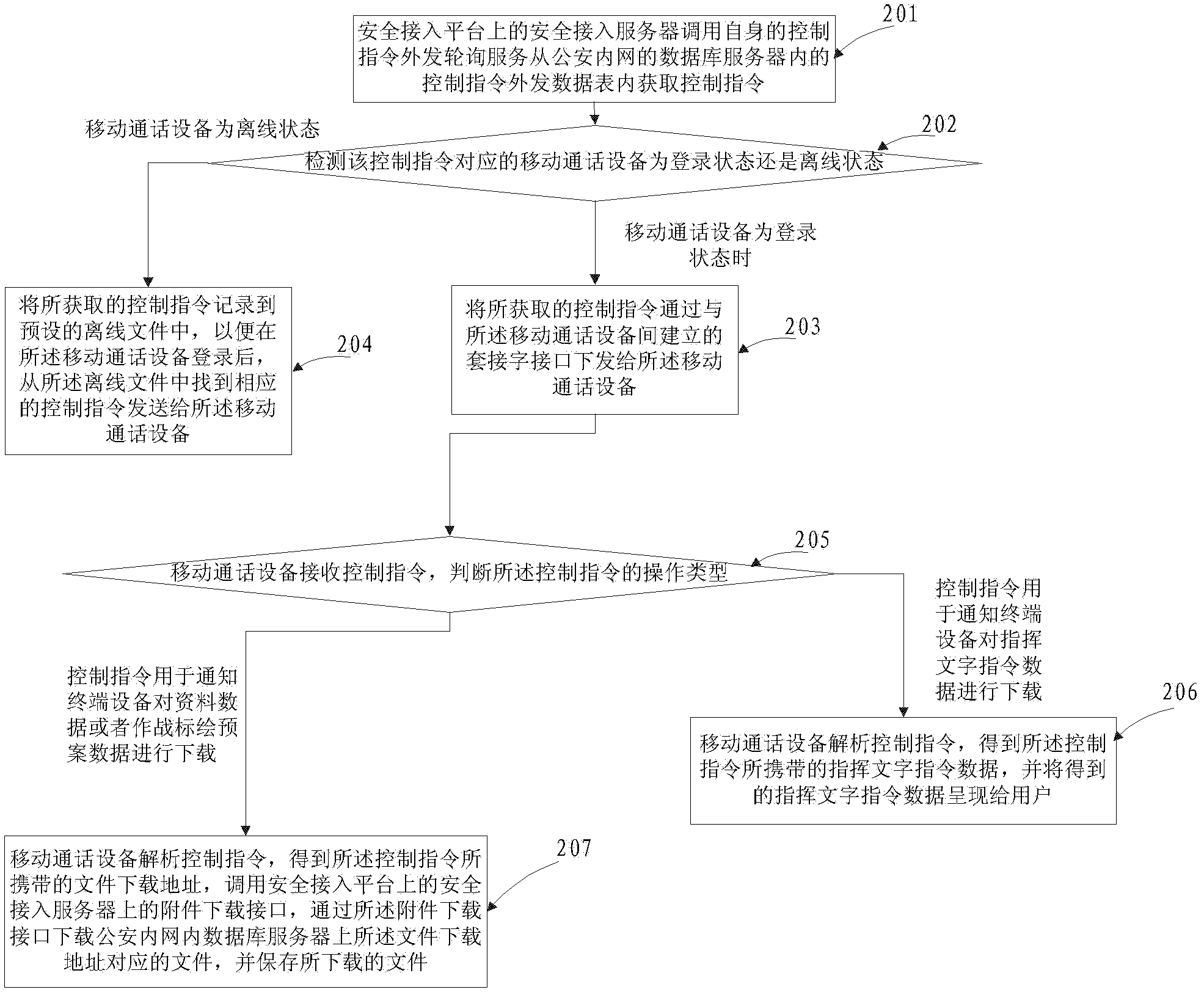
[0119] The secure access server 402 on the secure access platform is used to obtain control commands in the public security intranet when the terminal device 404 is a mobile communication device, and issue the control commands to the terminal device 404;
[0120] The application server 403 in the public security intranet is used to obtain control instructions in the public security intranet when the terminal device 404 is a mobile computer device or an intelligent fixed device, and issue the control instructions to the terminal device 404;
[0121] The terminal device 404 is configured to receive the control instruction, and exec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com