Double-interface encryption memory card and management method and system of data in double-interface encryption memory card
An encrypted storage, dual-interface technology, applied in the field of data processing, can solve the problems of poor non-contact interface transmission rate, unsuitable for storing a large amount of data, slow data transmission speed, etc., to achieve high-speed data transmission, improve security, prevent data leaked effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
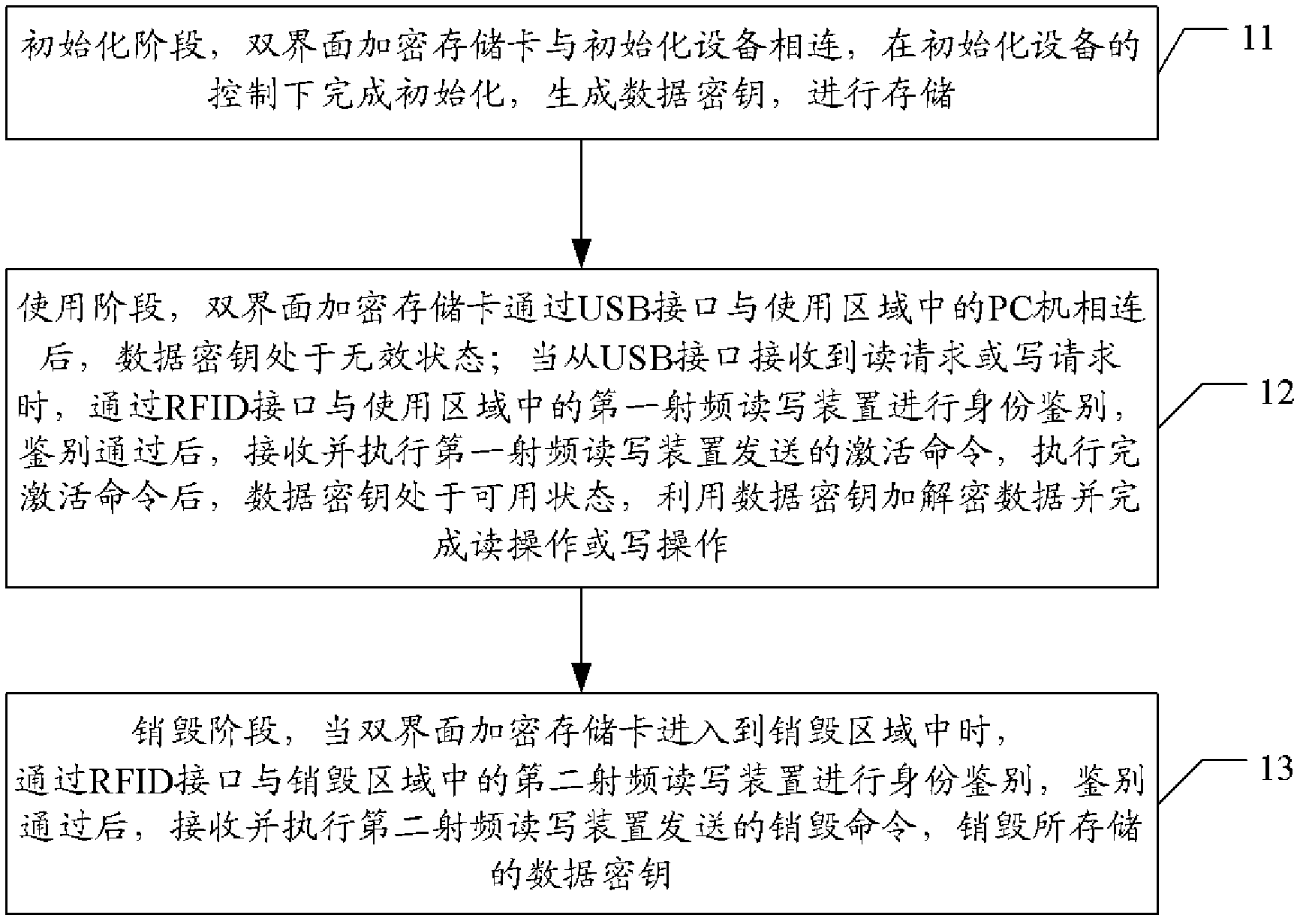
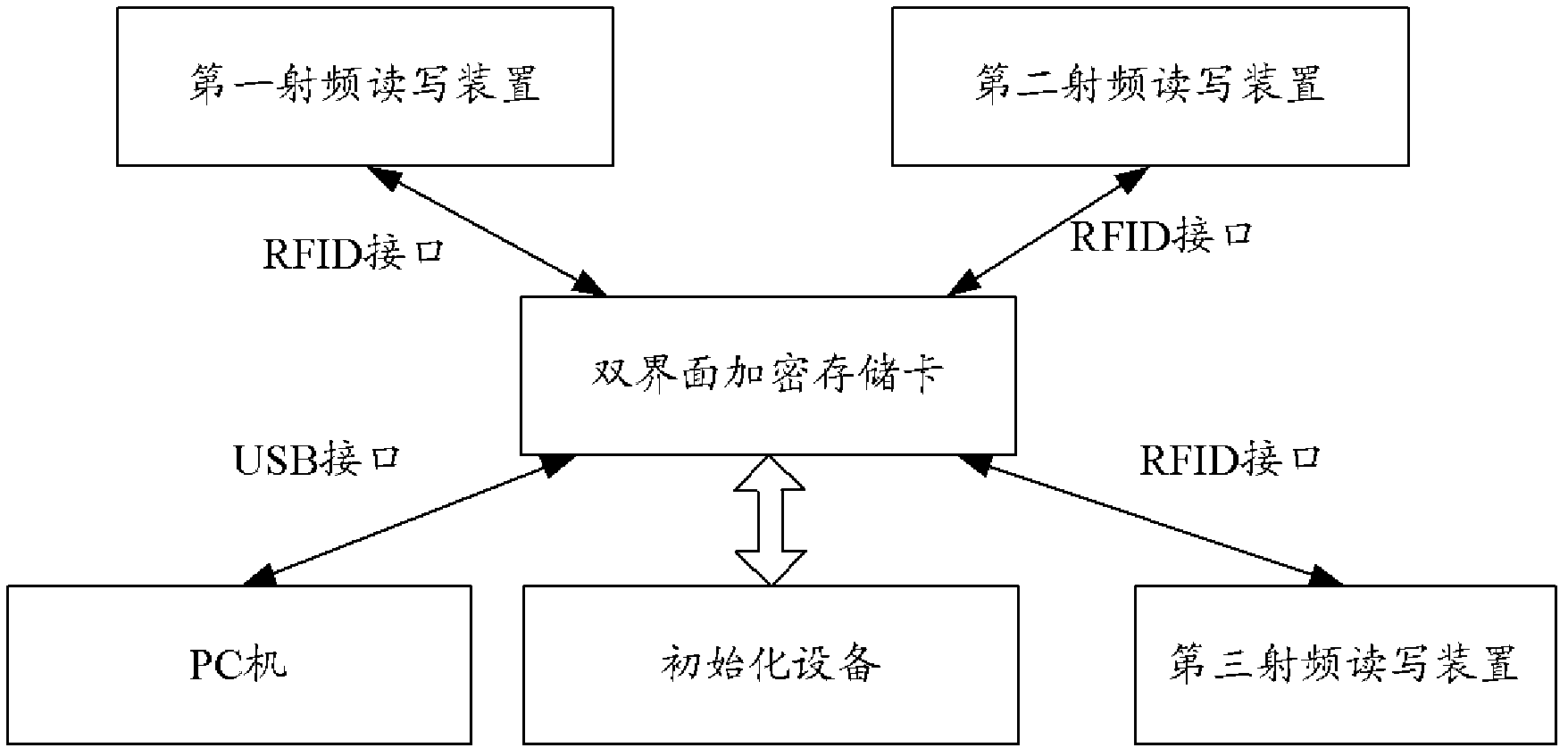
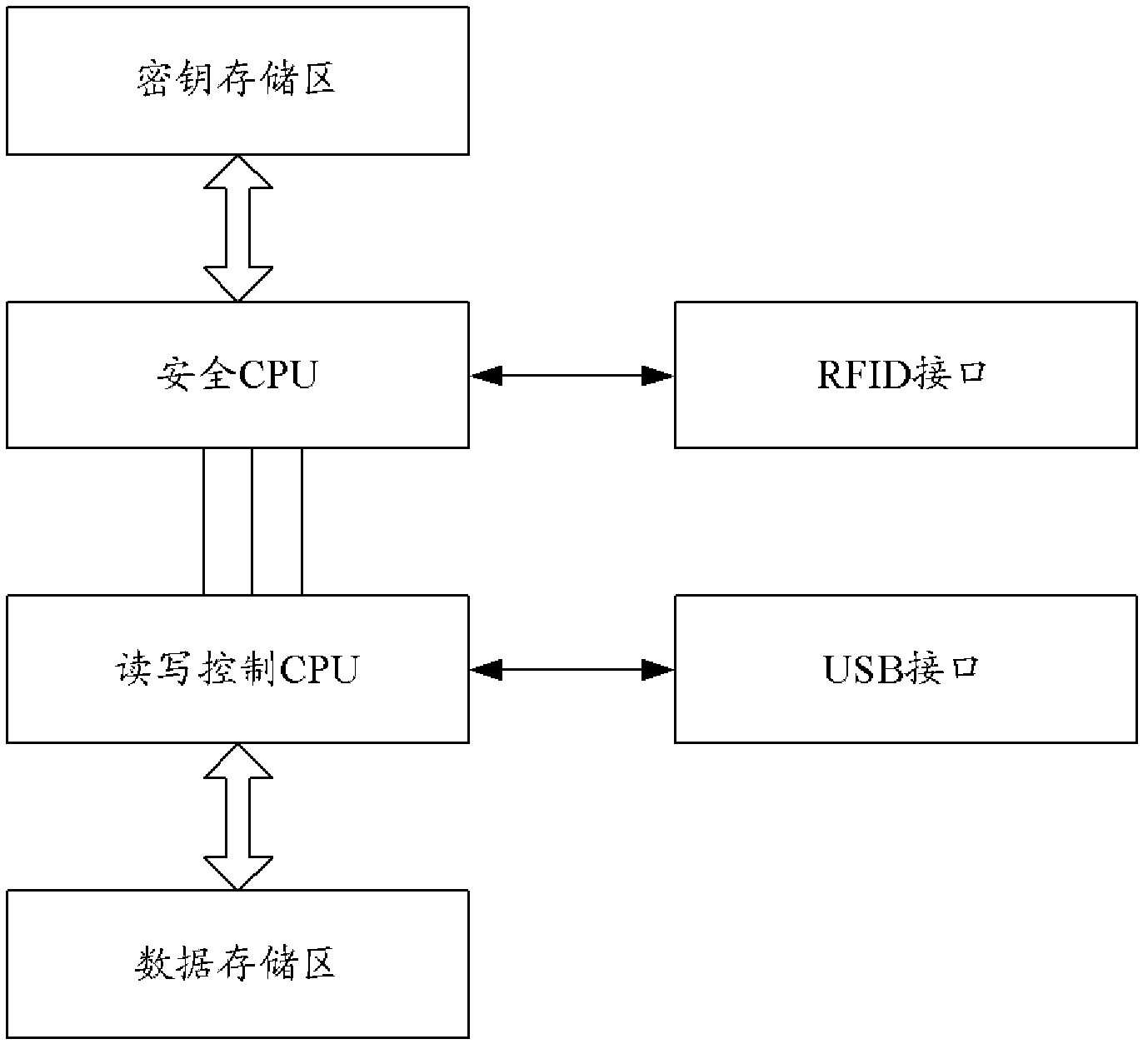
[0035] Aiming at the problems existing in the prior art, the present invention provides a dual-interface encryption memory card and a data management method and system therein. The dual-interface encrypted memory card has two interfaces at the same time, which are USB interface and radio frequency identification (RFID, Radio Frequency Identification) interface. The USB interface is used to connect with a PC for data reading and writing, and the RFID interface is used to receive and send radio frequency signals. , receive security commands from radio frequency signals, and store data in the card after encryption.
[0036] In order to make the technical solution of the present invention more clear and understandable, the solution of the present invention will be further described in detail below with reference to the accompanying drawings and examples.
[0037] figure 1 It is a flow chart of an embodiment of the data management method in the dual-interface encryption memory car...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com