ROP attack detection method and system based on virtual machine
An attack detection and virtual machine technology, applied in the field of system security, can solve the problems of ROP attack protection failure, insufficient detection and prevention methods, etc., and achieve the effects of protection availability, low false positive rate and high detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
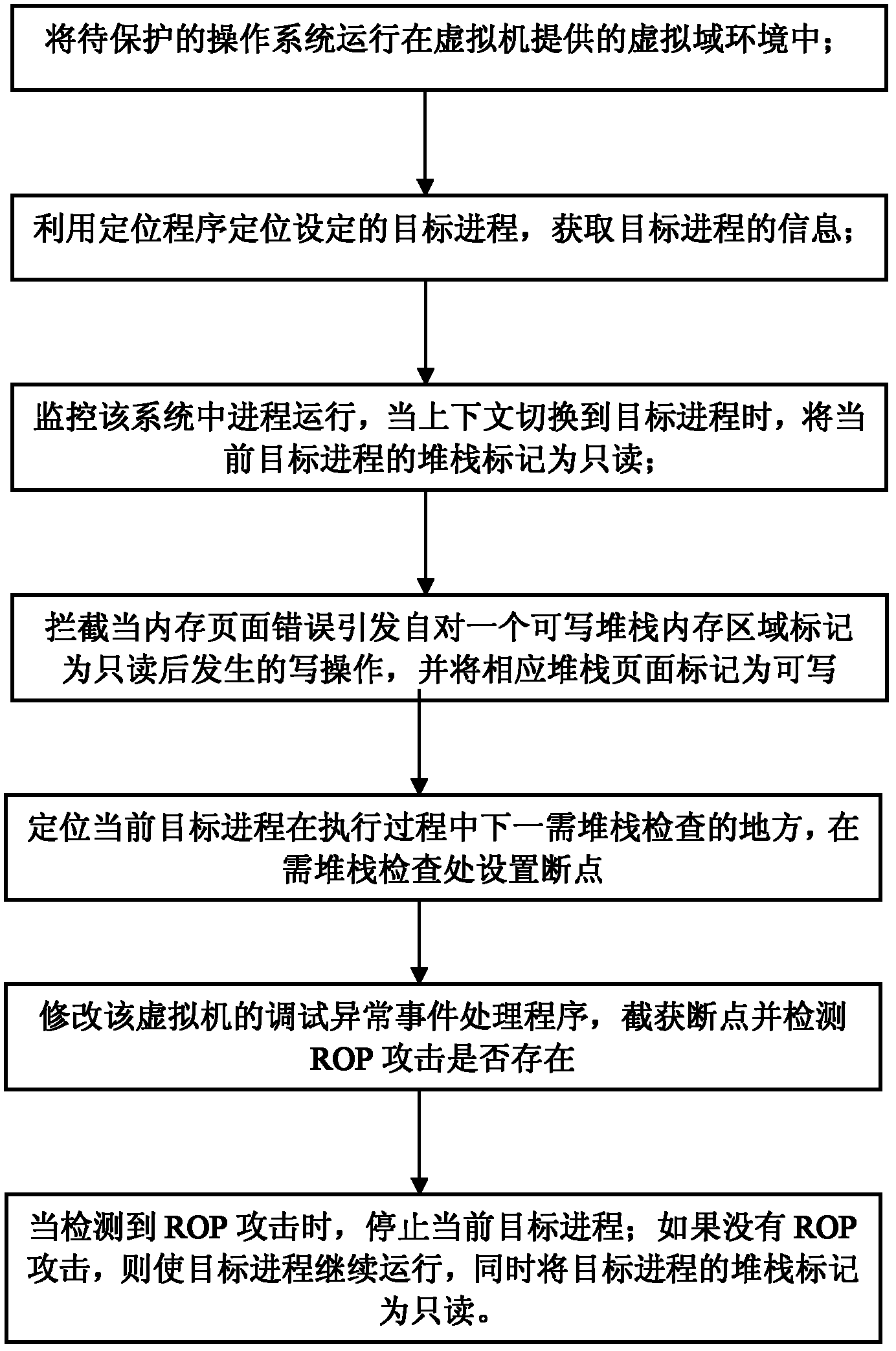
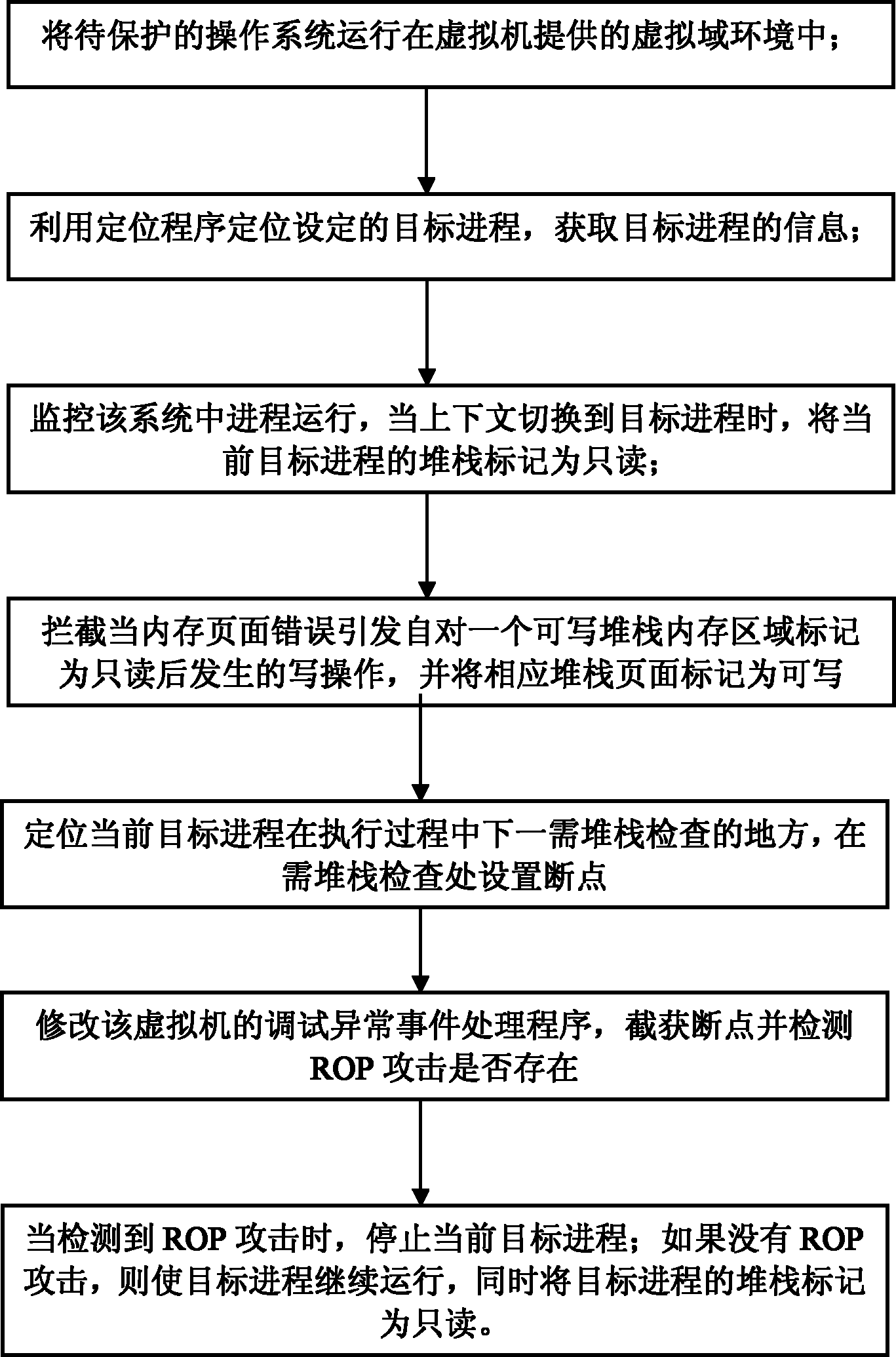
[0040] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
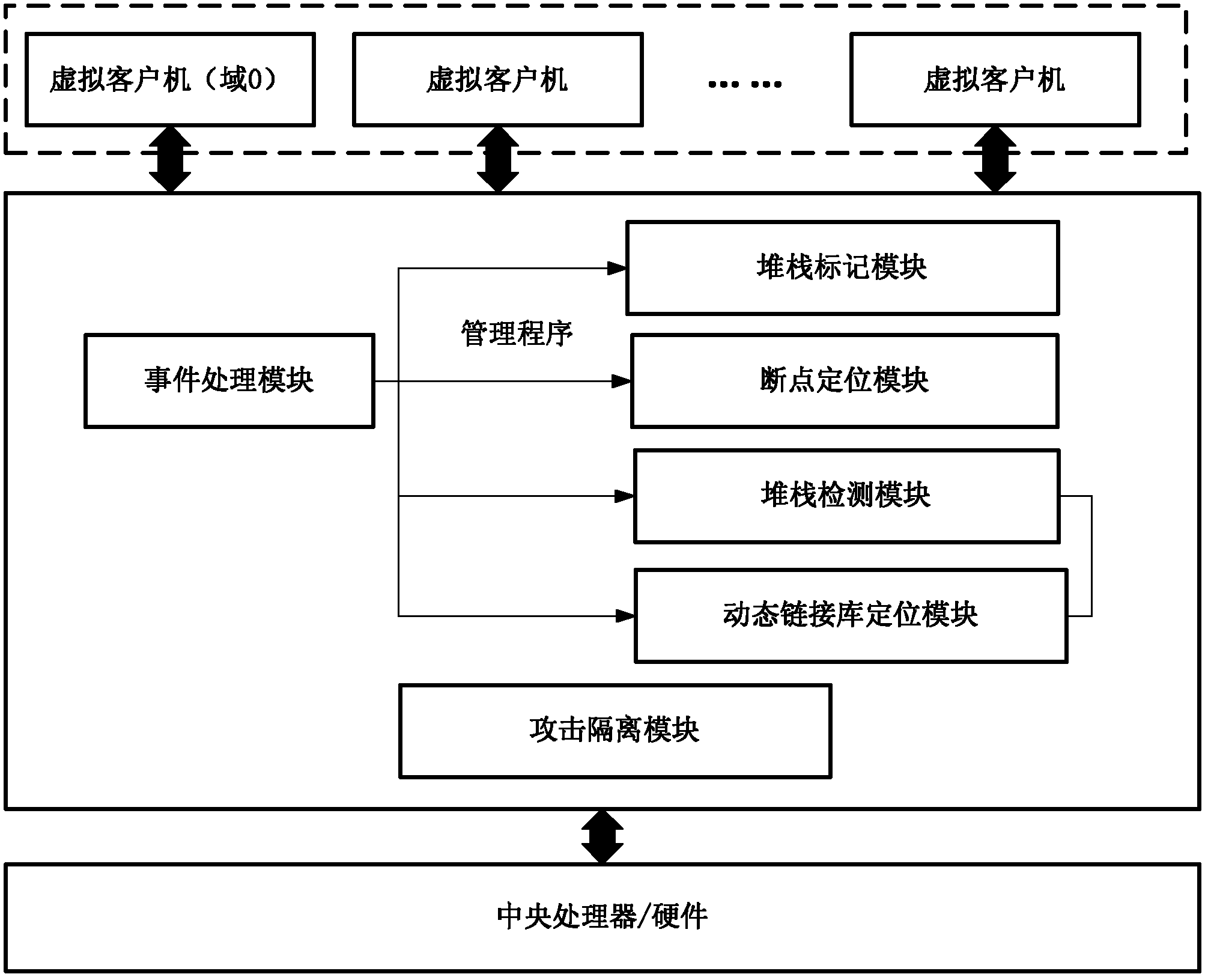
[0041] Such as figure 2 Shown, the ROP attack defense system based on virtual machine of the present invention, this system is based on virtual machine, is made up of six main parts: event processing module, stack mark module, breakpoint location module, stack inspection module, dynamic link library location module and attack isolation module. In order to realize the interception of stack write operation and check of stack content in the process of ROP detection and attack defense, three event handlers in the virtual machine are modified in the event processing module. When the context is switched to the process to be protected and the stack inspection is performed, the stack marking module is responsible for marking the stack as read-only, thereby causing a page fault so that the write operation to the stack can be intercepted and processed. The bre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com