Simulation system and simulation method of social network service malicious code propagation
A social network and malicious code technology, applied in the field of social network malicious code propagation model simulation system, can solve problems such as large consumption of system resources, and achieve the effect of good universality and accurate description
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The technical scheme of the present invention will be described in detail below in conjunction with the drawings:
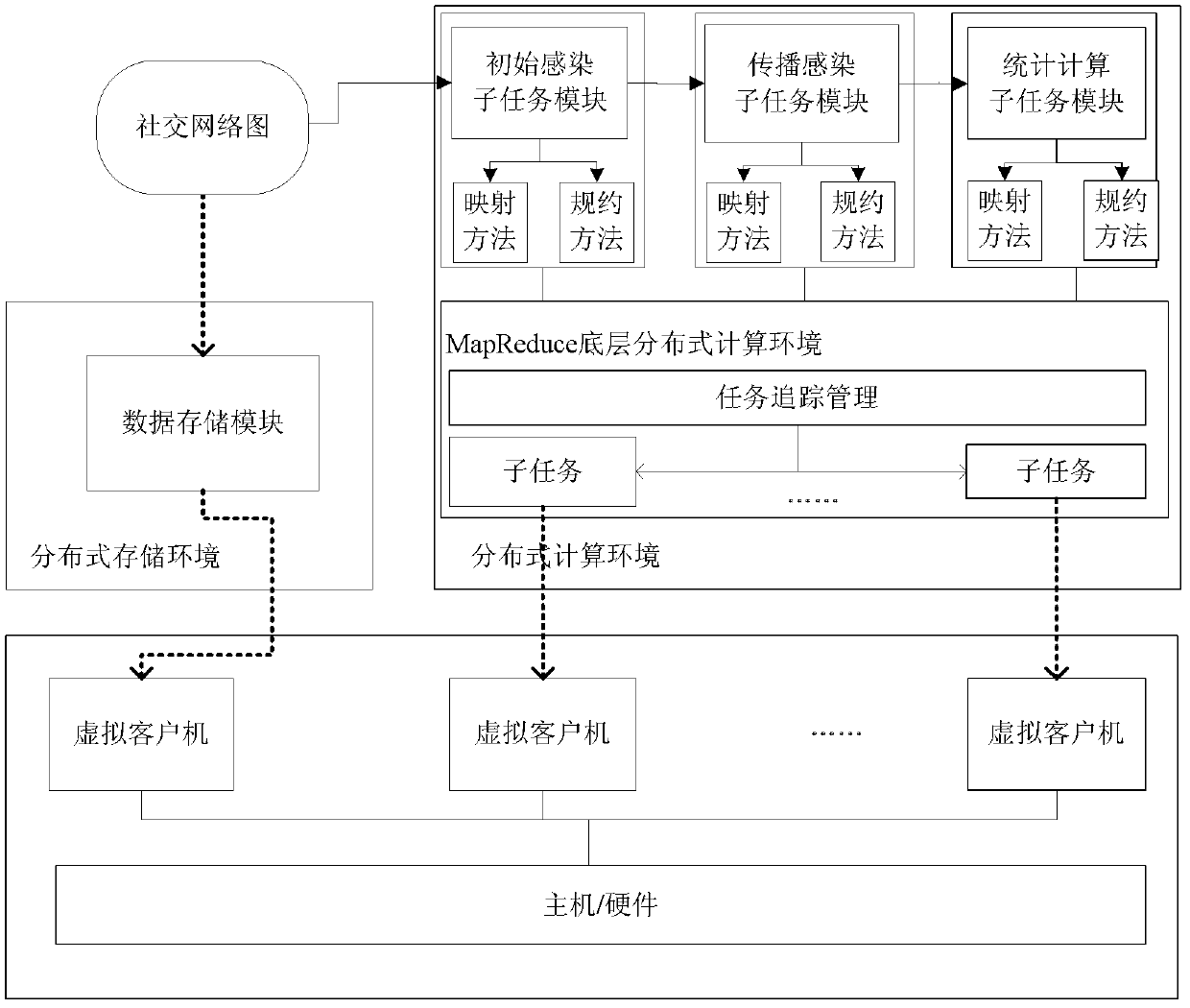
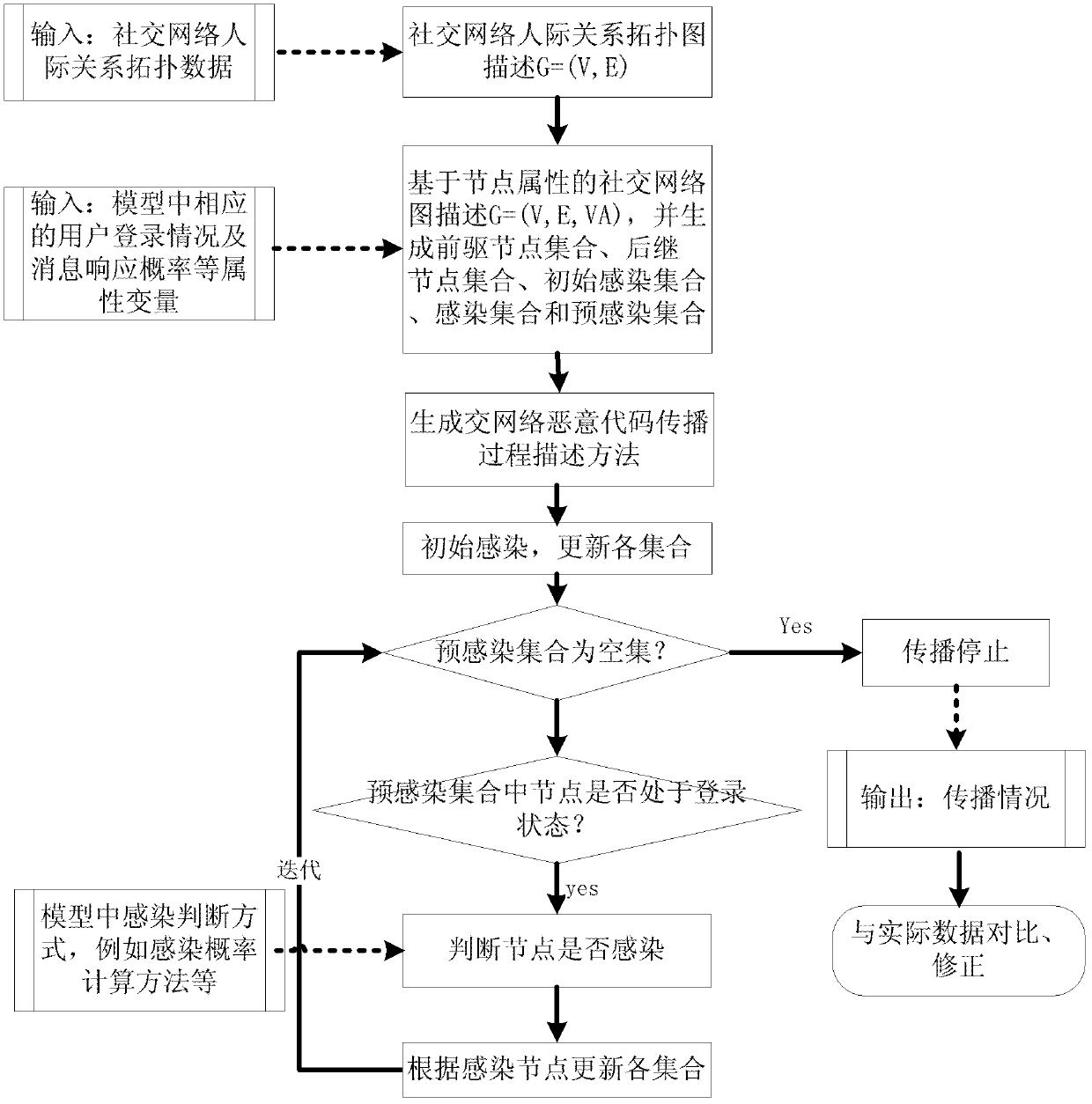
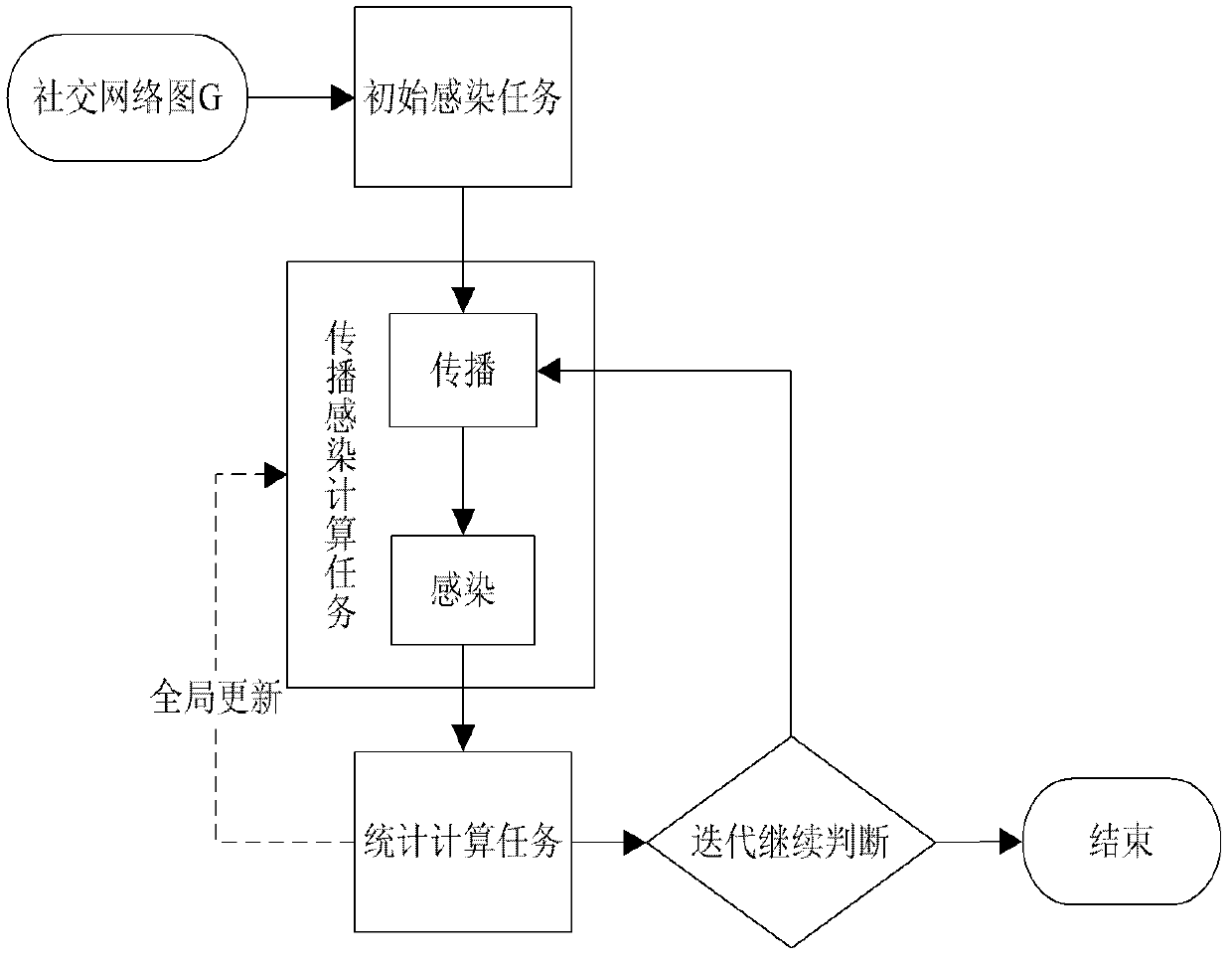
[0070] The simulation system of the present invention is such as figure 1 As shown, the system is implemented based on MapReduce technology. Virtualization technology is used at the hardware layer, virtual hosts are used to replace traditional physical hosts, and multiple virtual hosts are constructed and connected by Ethernet. In the storage module, a distributed storage environment is used to store the inputted social network graph topology data. Based on the MapReduc deployment of a distributed computing environment, the social network worm propagation is divided into three subtask modules: initial infection, propagation infection and statistical calculation, and the mapping and protocol calculation modules are defined for the three pre-divided tasks, and then according to The defined task sequence is submitted to the underlying distributed computing envi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com