Method and device for authenticating in safety channel establishing process as well as intelligent card and terminal
A secure channel and authentication technology, applied in the field of smart cards and terminals, can solve the problems of many illegal attacks and easy failure of security modules
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
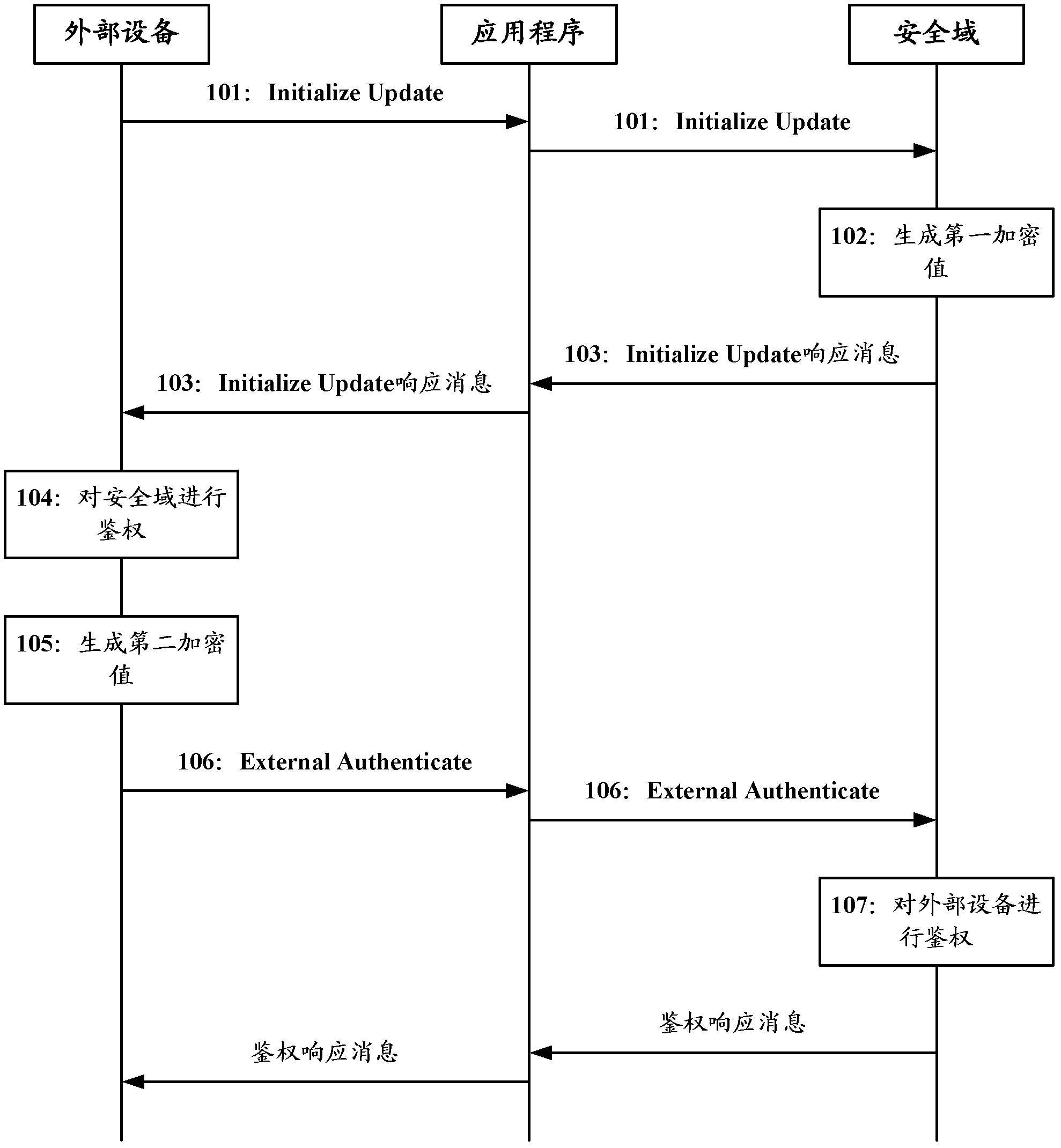
[0073] Such as figure 2 As shown in FIG. 1 , it is a schematic diagram of the steps of the authentication method in Embodiment 1 of the present invention when establishing a secure channel. In Embodiment 1, the authentication process of the external device in the security domain is used as an example for illustration. The security module itself or in the security module The authentication process of the application program to the external device is the same as that of the security domain to the external device.
[0074] The method comprises the steps of:
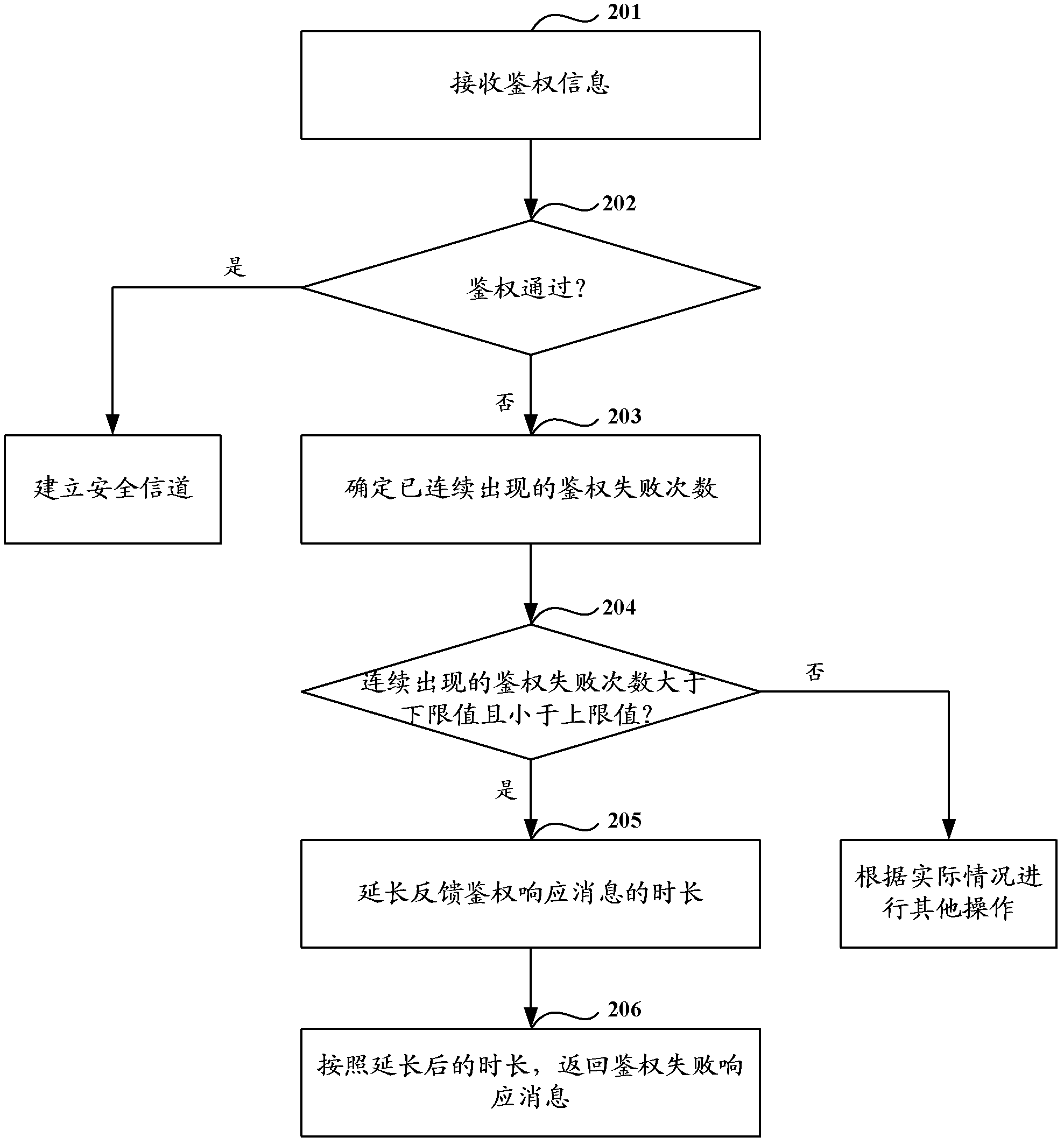
[0075] Step 201: Receive authentication information.
[0076] In this step, when the external device communicates with a security domain in the security module figure 1 In the security channel initialization stage shown, after the external device passes the authentication of the security domain, it can send authentication information for establishing a security channel to the security domain in the manner of step 105 and ...
Embodiment 2
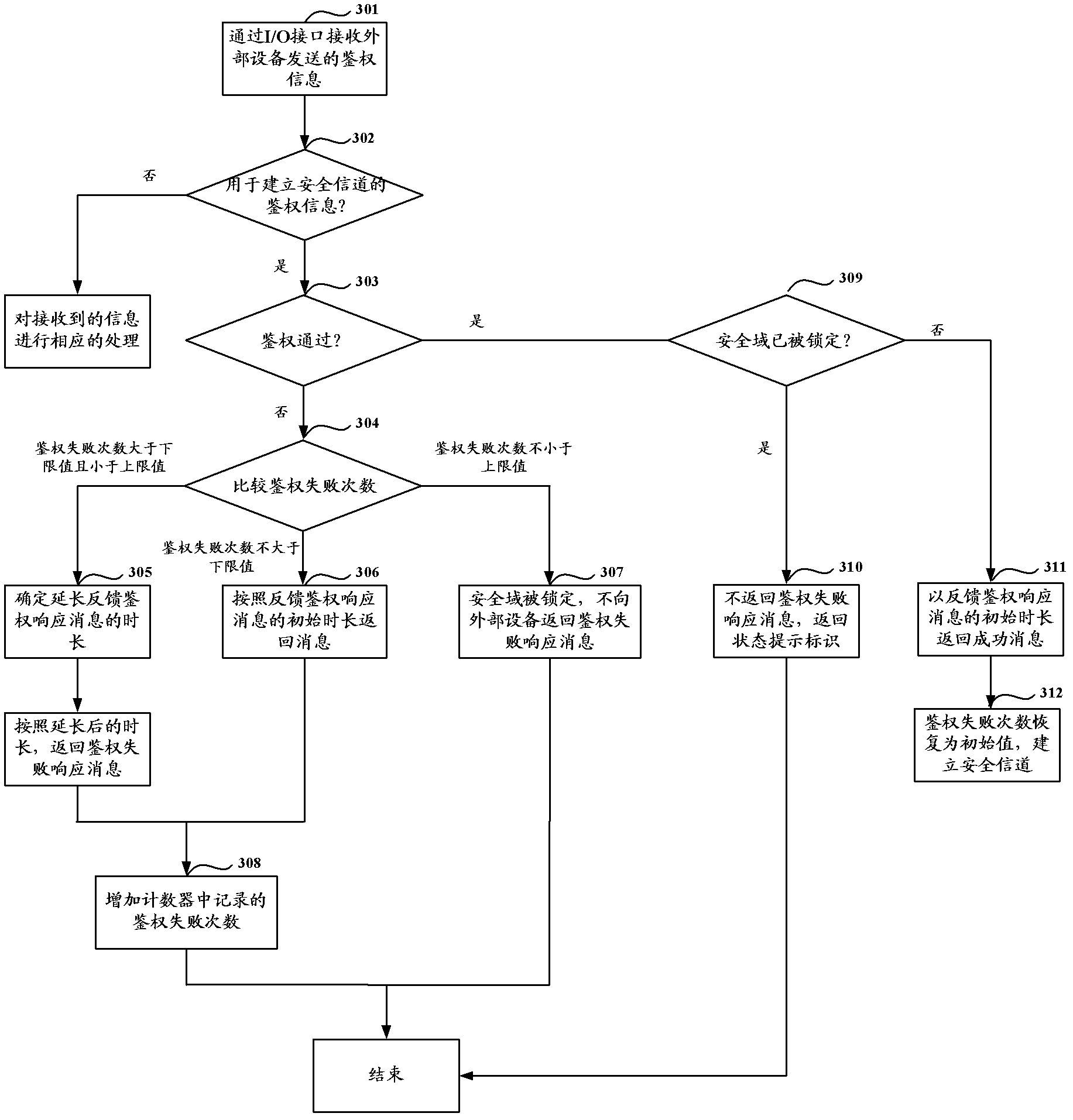
[0103] The second embodiment of the present invention uses a specific example to describe the solution of the first embodiment in detail, assuming that the solution of the second embodiment still takes the authentication of the external device by the security domain as an example.
[0104] In the scheme of the second embodiment, the maximum number of failures (i.e. the upper limit) of the security domain is Counter_max, and the lower limit of the security domain is Counter_min. In this embodiment, it is used to determine whether the security domain is attacked. The number of failures does not include the current authentication failure.
[0105] The scheme of this embodiment is as image 3 shown, including the following steps:
[0106] Step 301: Receive authentication information sent by an external device through an I / O interface.
[0107] Step 302: Analyze the authentication information to determine whether it is authentication information for establishing a secure channel,...
Embodiment 3
[0141] Embodiment 3 of the present invention provides a device for performing authentication when establishing a secure channel under the same inventive concept as Embodiment 1 and Embodiment 2, such as Figure 5 As shown, the device includes: an authentication module 11, a number of times determination module 12, a delay module 13 and a return module 14, wherein: the authentication module 11 is used to authenticate the authentication information used to establish a secure channel; the number of times The determination module 12 is used to determine the number of authentication failures that have occurred continuously when the authentication fails; the delay module 13 is used to extend the feedback authentication response when the determined number of authentication failures is greater than the lower limit and less than the upper limit. Duration of the message; the returning module 14 is configured to return an authentication failure response message according to the extended d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com