Mobile terminal and wireless control method
A mobile terminal and wireless technology, applied in wireless communication, access restrictions, electrical components, etc., can solve problems such as the inability to limit the range of user activities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0040] I, the first embodiment (passive detection):
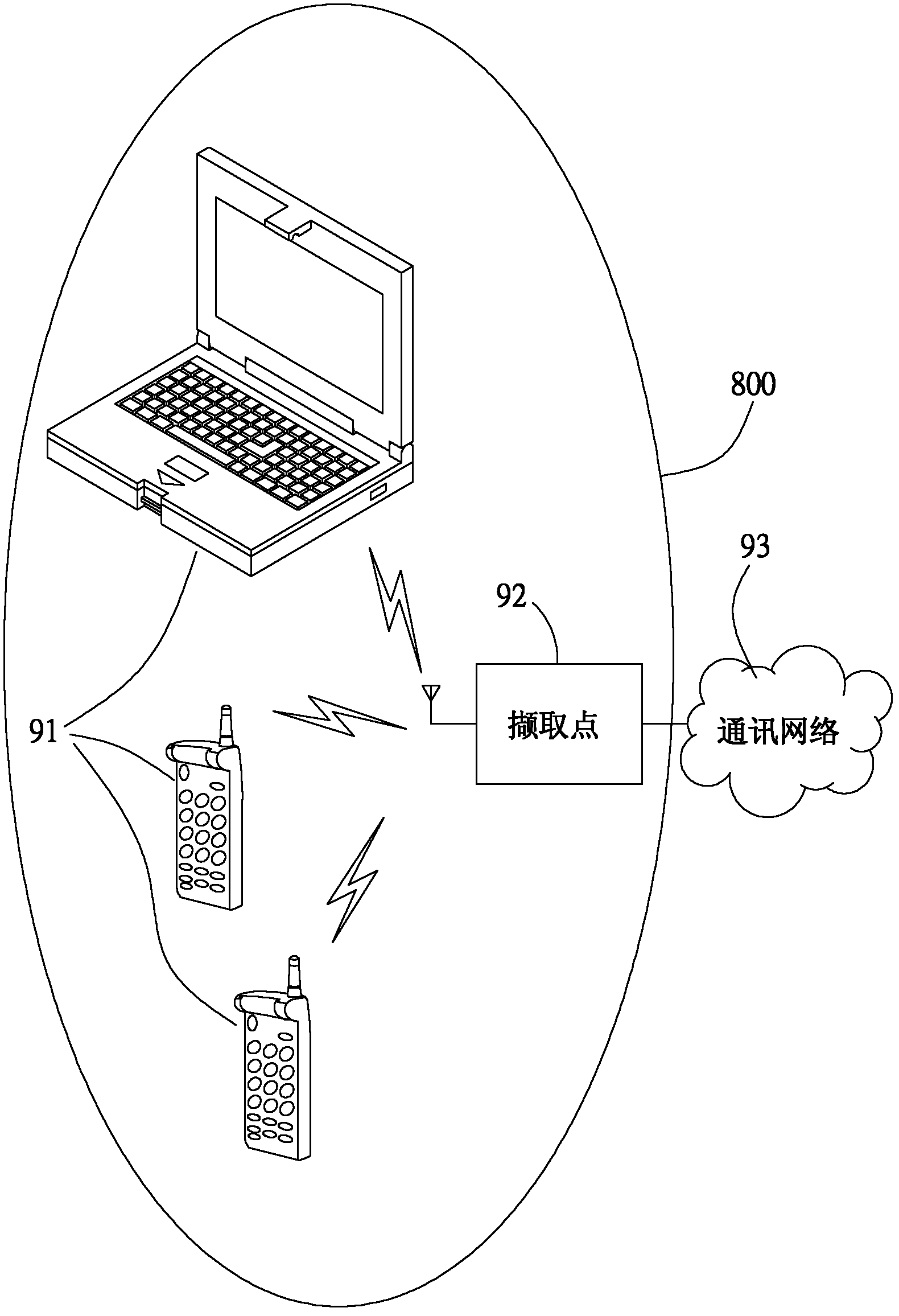
[0041] (1) After the network access device 2 (such as: the capture point) is powered on and connected to the communication network 300 (such as a router or a gateway), it can start to operate and output the beacon data 201 without interruption. The tag data 201 includes SSID information, supported transmission rates, and the MAC address of the wireless network access device 2 .
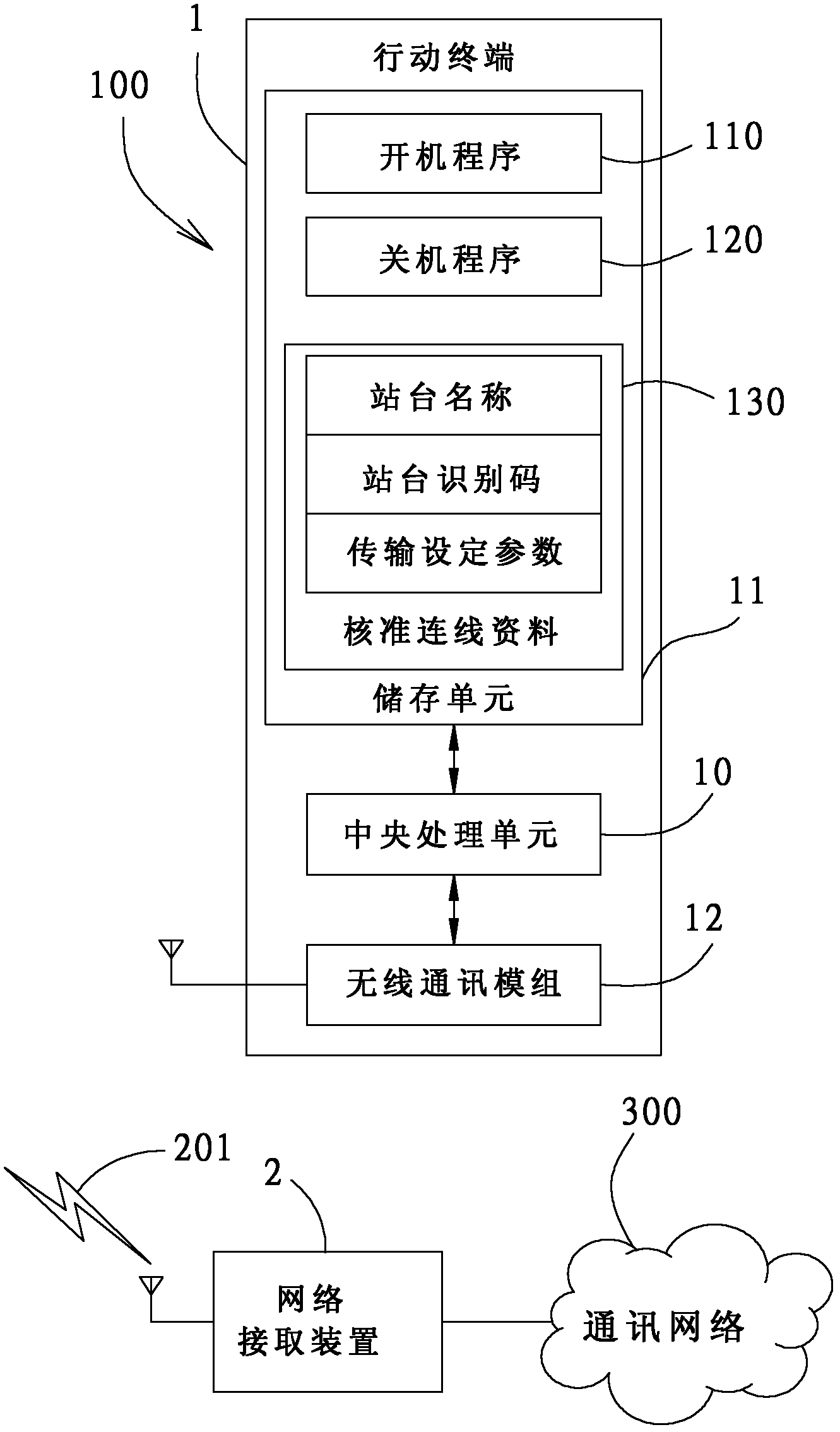
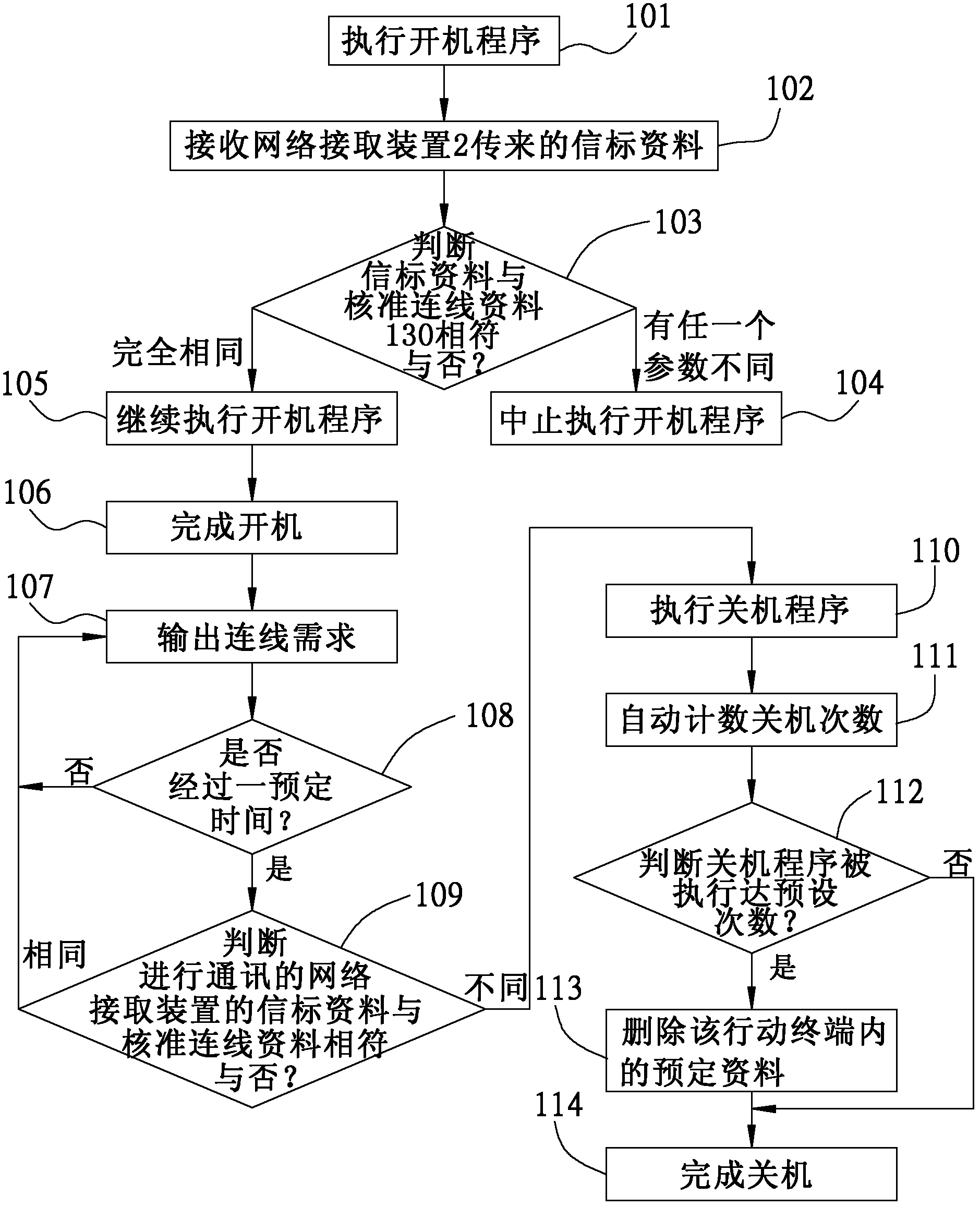
[0042] (2) The mobile terminal 1 has a built-in table (not shown in the figure), and there are several approved connection data 130 in the built-in table, and when the mobile terminal 1 is turned on, it will receive all network access within the transmittable range The beacon data 201 of the device 2, and then as long as one of the SSID information or the MAC address of the network access device 2 is different from the authorized connection data 130 in the built-in table, it will not be powered on.
[0043] (3) After the mobile terminal 1 is turne...
no. 2 example
[0045] II, the second embodiment (passive detection):
[0046] (1) After the network access device 2 (such as: the capture point) is powered on and connected to the communication network 300 (such as a router or a gateway), it can start to operate and output the beacon data 201 without interruption. The tag data 201 includes SSID information, supported transmission rates, and the MAC address of the wireless network access device 2 .
[0047] (2) The mobile terminal 1 has a built-in table with several approved connection data 130, and when the mobile terminal 1 is turned on, it will receive beacons from all network access devices 2 within the transmission range Data 201, then when only one of the SSID information or MAC address of these network access devices 2 is the same as the approved connection data 130 in the built-in table, it will be turned on.
[0048] (3) The user 5 can see the names of all network access devices 2 within the transmission range in the WIFI network co...
no. 3 example
[0051] III. The third embodiment (active detection):
[0052] (1) The mobile terminal 1 sends a client connection request signal when it is turned on, and receives response signals from all network access devices 2 within the transmission range. Wherein, the response signal is the beacon data 201 , including SSID information, supported transmission rate, and the MAC address of the wireless network access device 2 .
[0053] (2) The mobile terminal 1 has a built-in table with several approved connection data 130. The mobile terminal 1 judges that only one of the SSID messages or MAC addresses of these network access devices 2 matches the built-in table. If the approved connection data 130 in the computer is not the same time, it will not be started.
[0054] (3) After the mobile terminal 1 is turned on, the user 5 can see the names of all network access devices 2 with approved connection data 130 in the WIFI network connection list 401 of the mobile terminal 1, so that the use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com