Optimization method based on embedded platform SM2 encryption algorithm
An encryption algorithm and optimization method technology, which is applied in the field of optimization based on the embedded platform SM2 encryption algorithm, can solve the problems of long modification period, large storage space, and large changes, so as to reduce memory usage, realize encryption functions, and solve transformation problems. problem effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
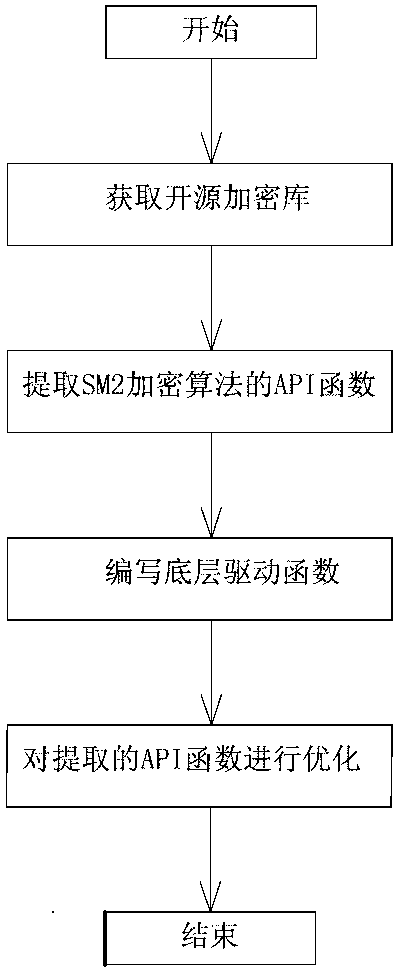
[0044] Such as figure 1 Shown, a kind of optimization method based on embedded platform SM2 encryption algorithm of the present invention comprises the following steps:
[0045] 1) Obtain an open source encryption library;
[0046] 2) Extract the API function of the SM2 encryption algorithm from the open source encryption library, and the extracted API function includes extracting all the subroutines related to the API function;
[0047] 3) Write the underlying driver function of the open-source encryption library algorithm, the writing of the underlying driver function at least includes writing the call interface function of the API function and the definition function of the CPU data direction.
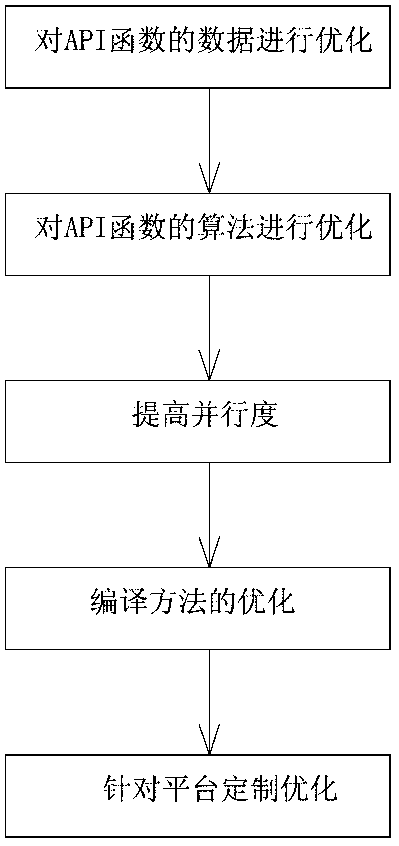
[0048] 4) Optimize the extracted API functions.
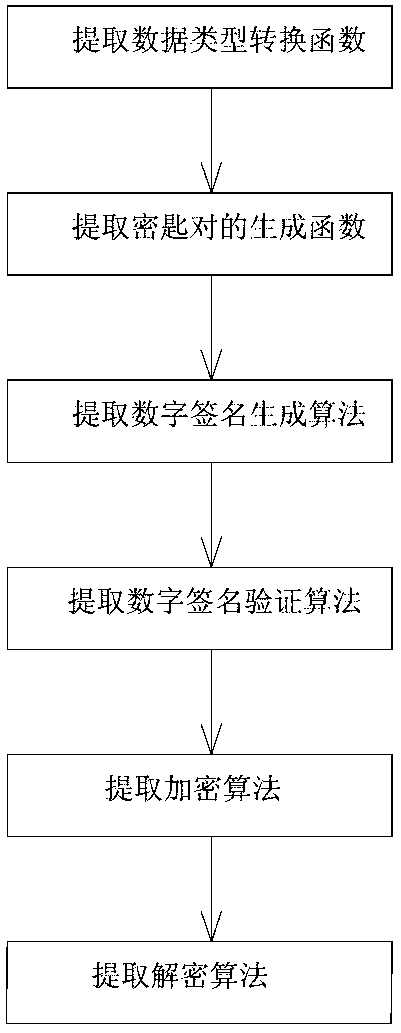
[0049] Such as figure 2 As shown, the step of extracting the API function at least includes the following process:
[0050] 21) Extract data type conversion function;
[0051] 22) Extract the generation function of the key pair...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com