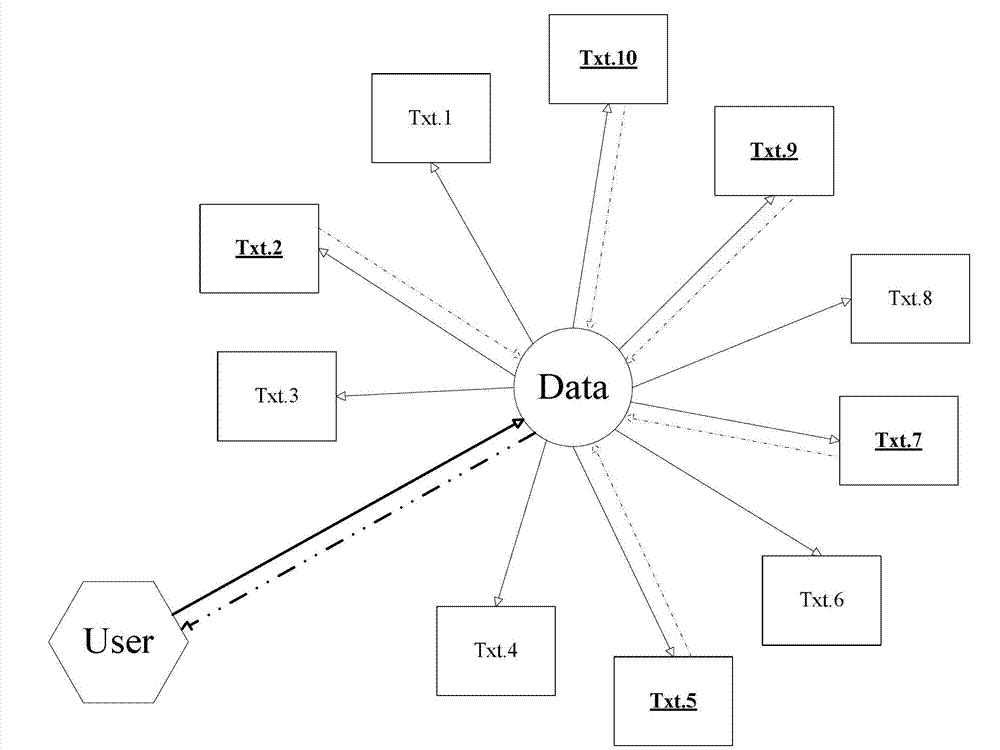
Data access method
A data access and data storage technology, applied in the direction of digital data protection, can solve the problems of increased time cost, high user requirements, and no longer applicable, and achieve the effect of reducing the probability of leakage, enhancing privacy and high availability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to describe the present invention more specifically, the technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0035] A data access method, comprising the steps of:
[0036] data storage:
[0037] (1) Convert each byte of the data Data input by the user User into a 5-dimensional feature vector through radical splitting;
[0038] First, construct the polynomial of degree 5 as follows:
[0039] x 5 +a 4 x 4 +a 3 x 3 +a 2 x 2 +a 1 x+a 0 =0
[0040] Then, the above polynomial of degree 5 is transformed into the following expression:
[0041] (x-r 1 )(x-r 2 )(x-r 3 )(x-r 4 )(x-r 5 )=0
[0042] Among them, r 1 ~ r 5 are the k roots of the 5th degree polynomial, then r 1 ×r 2 ×r 3 ×r 4 ×r 5 =a 0 ;
[0043] Finally, let the byte value (0~255) of any byte be a 0 , and randomly generate r 1 ~ r 4 value, and then find r 5 ; make r 1 ~ r 5 is th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com