Data packet processing method and device
A processing method and data packet technology, applied in the field of communication, can solve problems such as abnormal network egress, and achieve the effect of improving flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] Figure 4 It is a schematic diagram of an enterprise connecting an internal network with an external network through a router according to Embodiment 1 of the present invention, as shown in Figure 4 As shown in the figure, an enterprise link is a multi-export and multi-routing load scenario, and the egress is divided into two types of lines: Telecom and China Netcom. Figure 4 The telecom server and China Netcom server are used to simulate two server addresses respectively. The user requests that the line going to China Netcom should first use China Netcom, and the line going to China Telecom should first use China Telecom, but for some sensitive service traffic (such as HTTP or ICMP service) must use China Netcom line; when there is a problem with the link on one side, it can automatically switch to other lines, with the priority of the same line; for example, if a line of Netcom is interrupted, other Netcom lines of Netcom will be switched first; if there is no other...
Embodiment 2
[0069] In this embodiment, a method for implementing flexible policy routing loads by using labels in security rules is provided. By expanding the security rule table and routing table of the security gateway, a routing table with table identification is added to the network system, and the security The routing identification index (ID) can be configured in the advanced options of the rule. When a data packet is querying a rule, after matching a specific rule, it needs to query the identification index (ID) of the rule. If the identification index (ID) is not configured in the rule, the routing search will be performed according to the conventional routing search method. If the rule is configured If the specific identification index (ID) is specified, the SKB (Socket Buffer)→MARK field of the data packet is assigned to the corresponding identification index (ID). After the security rule module is processed, it enters the routing module, and the routing module MARK value to the...
Embodiment 3
[0087] This embodiment provides a method for implementing flexible policy routing loads by using labels in security rules. In the implementation process, it is divided into two stages: the network administrator configures the firewall device and firewall security rules, and the data processing flow of the routing load module.
[0088] Phase 1: The network administrator configures the firewall. Specifically, the configuration method of label-based advanced intelligent policy routing load may include:
[0089] Step 1, pre-define the destination address resources in the network system, define a telecom address resource addr_wt, the IP addresses are 124.127.118.26, 124.127.118.26, 124.127.118.26; define a Netcom address resource addr_dx, the IP address is 220.161.5.100 , 220.161.5.101, 220.161.5.102;
[0090] Step 2: Define a labeled routing load table item in the network system, add two policy routing table items respectively, the serial numbers are 1 and 2, and the identificat...
PUM
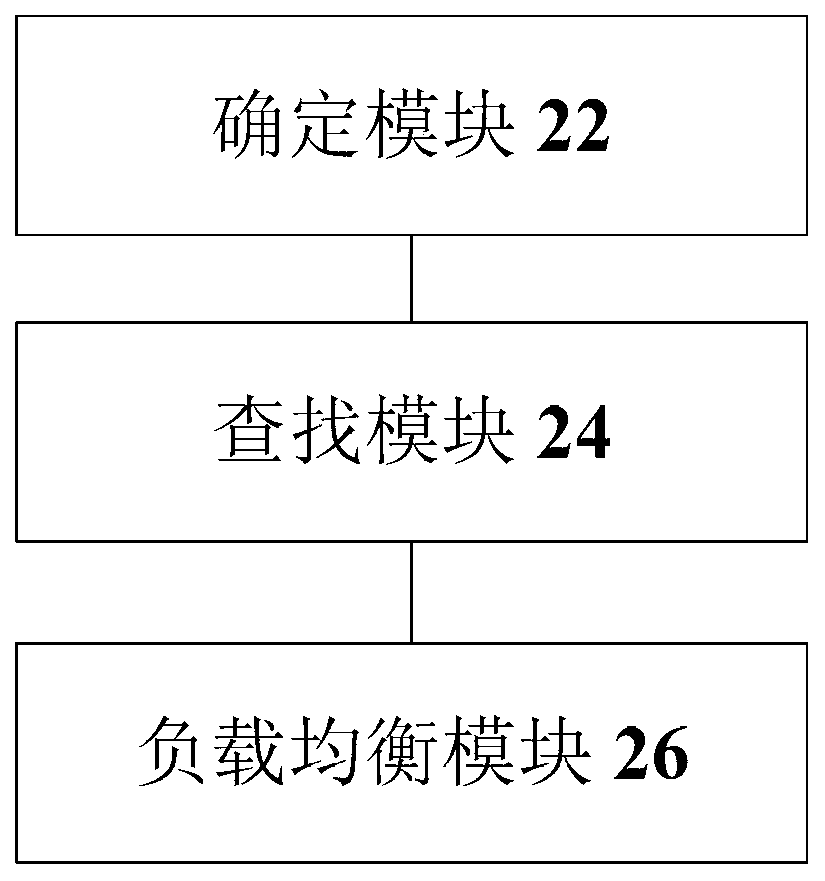
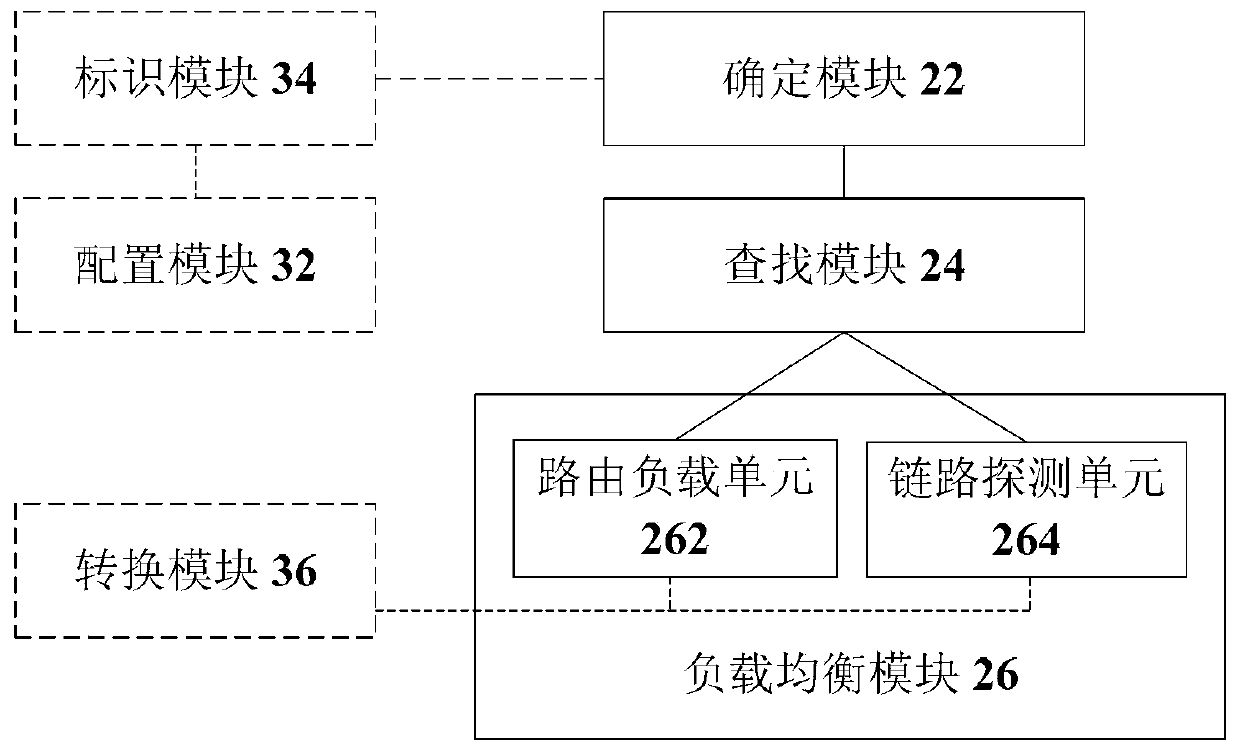
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com