LXI instrument service monitoring method
A monitoring method and instrument technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve the problems of occupying process table entries and system resources, waste of server resources, etc., to reduce waiting time, reduce storage and operation space , the effect of fast running speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
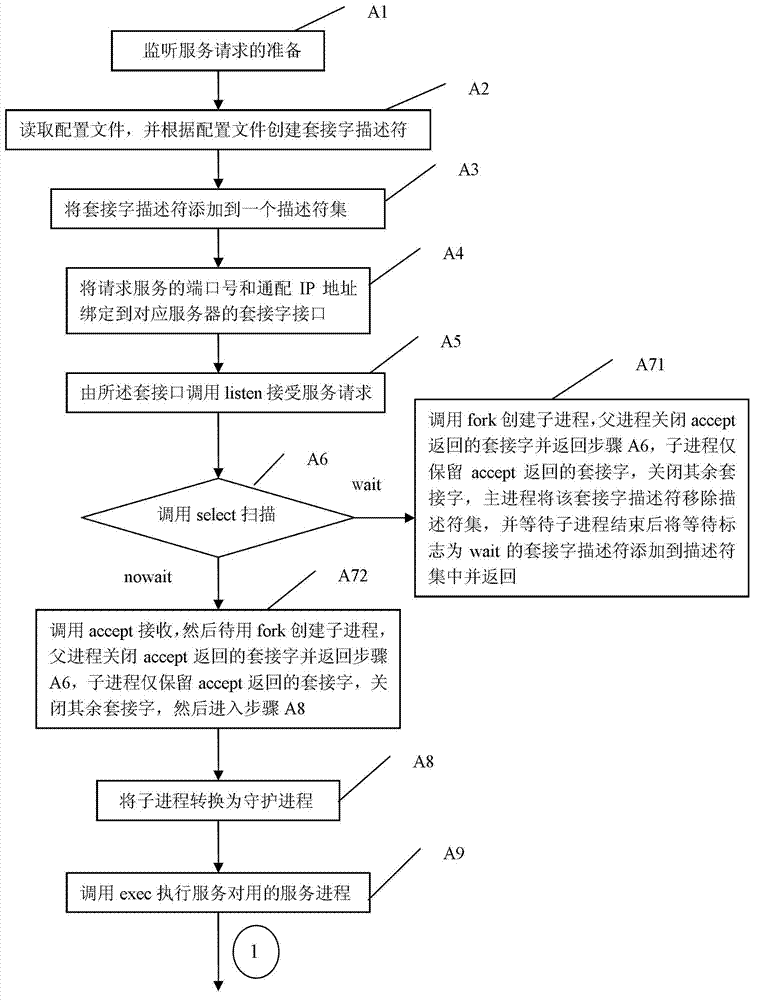
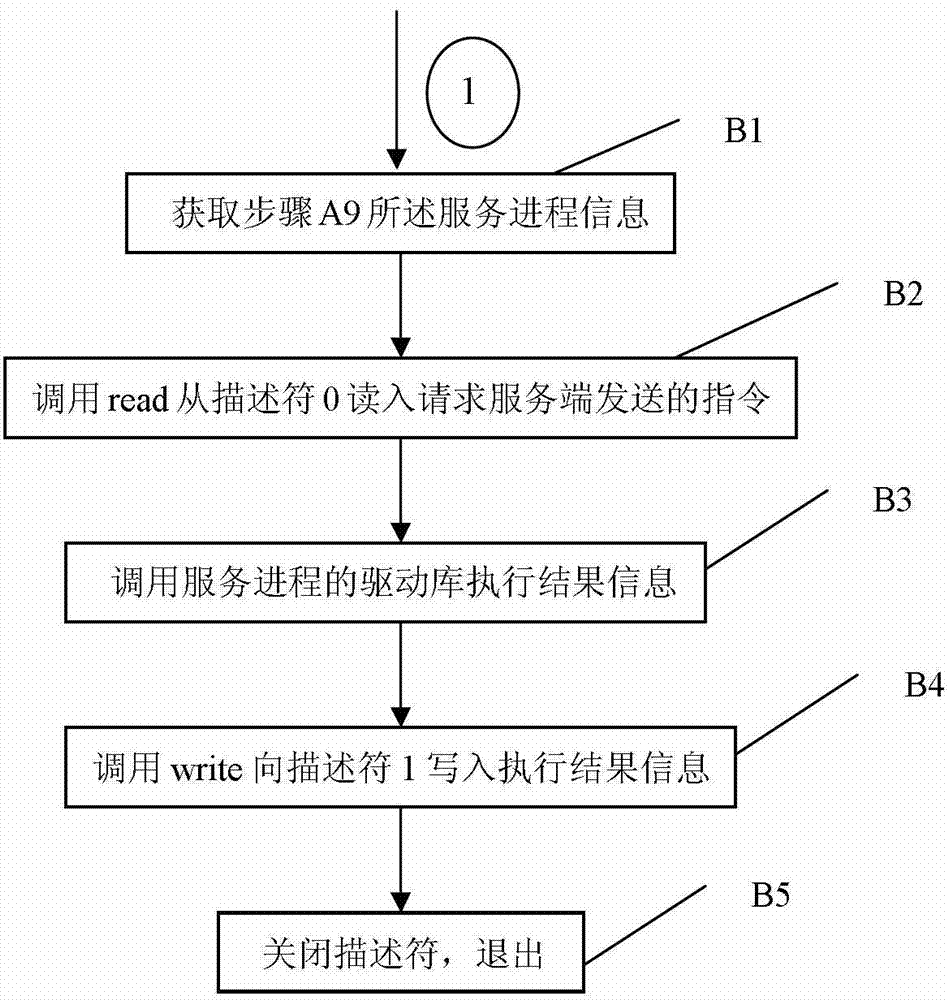
[0043] Specific implementation mode 1. Combination figure 1 This specific embodiment will be described. A service monitoring method of an LXI instrument, which includes a monitoring process A and a service process B:
[0044] The monitoring process A includes the following steps:
[0045] A1: Preparatory steps for listening to service requests;
[0046] A2: Steps for reading the configuration file and creating a socket descriptor according to the configuration file: reading the configuration file, parsing to obtain the attributes of each service request, and creating a corresponding socket for each service request according to the parsing result Descriptor;
[0047] A3: Steps for adding socket descriptors to a descriptor set;
[0048] A4: Steps for binding the port number and wildcard IP address of the requested service to the socket interface of the corresponding server;
[0049] A5: a step for calling listen to accept a service request by the socket interface;
[0050]...
specific Embodiment approach 2
[0093] Embodiment 2. This embodiment is different from Embodiment 1 in that the step A1 for preparing the service monitoring program includes the following steps:
[0094] A11 is a step for initializing global variables;
[0095] A12 is used to convert the process into a daemon process;
[0096] A13 steps for modifying process resource limits;
[0097] A14 Steps for installing signal processing functions.
[0098] The daemon process, also known as the daemon process (daemon), is a process that runs in the background and is not associated with any control terminal, and is a process with a long life span.
[0099] Because each process can query and change its own resource limit through the getrlimit (soft limit) and setrlimit (hard limit) functions. The operand of these two functions is a pointer to the following structure:
[0100]
[0101] The present invention sets the soft limit to ensure that the soft limit of the process is not RLIM_INFINITY, and rlim_cur is set to ...
specific Embodiment approach 3
[0110] Specific embodiment three, the difference between this specific embodiment and specific embodiment two is that the step A8 and the step A12 both include the following steps:
[0111] C1 is used to call umask to set the file mode creation mask to 0; this step is to prevent the inherited file mode creation mask from denying certain permissions;
[0112] C2 is used to call fork to create a child process and make the parent process exit; since the ID number of the child process is inherited from the process group ID of the parent process, it is not necessarily the leader process of the process group;
[0113] C3 is used to call setsid to create a session; through this step, the process becomes the first process of a new session, becomes the leader process of a new process group, and has no control terminal;
[0114] C4 is used to set the current working directory as the root directory; this step is to avoid that when the parent process works in a mounted file system, the work...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com