3G accessed IMSI (international mobile subscriber identity) privacy protection method
A privacy protection and encryption key technology, applied in the field of 3G network communication security, can solve problems such as low efficiency, heavy computing burden of network equipment, and determination of user identity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Below in conjunction with specific embodiment, further illustrate the present invention, should be understood that these embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention, after having read the present invention, those skilled in the art will understand various equivalent forms of the present invention All modifications fall within the scope defined by the appended claims of the present application.
[0022] The implementation process of an IMSI privacy protection method for 3G access is as follows:
[0023] 1. System initialization
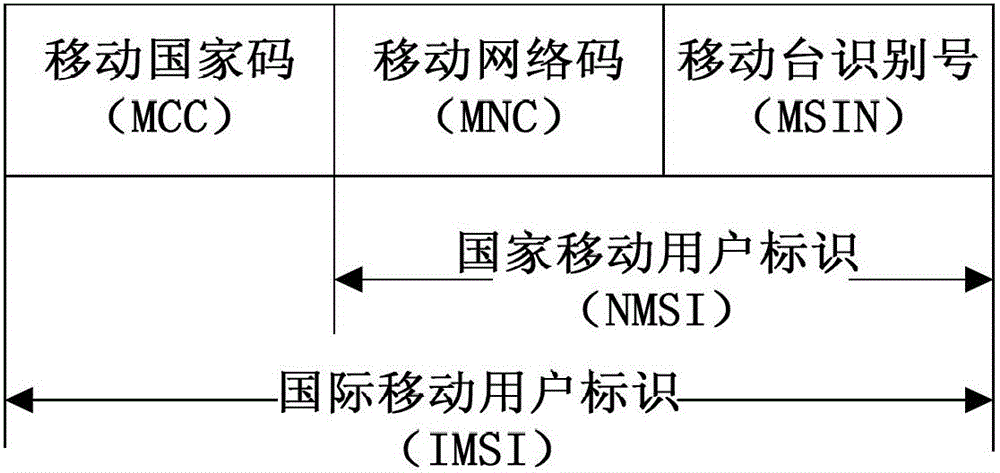
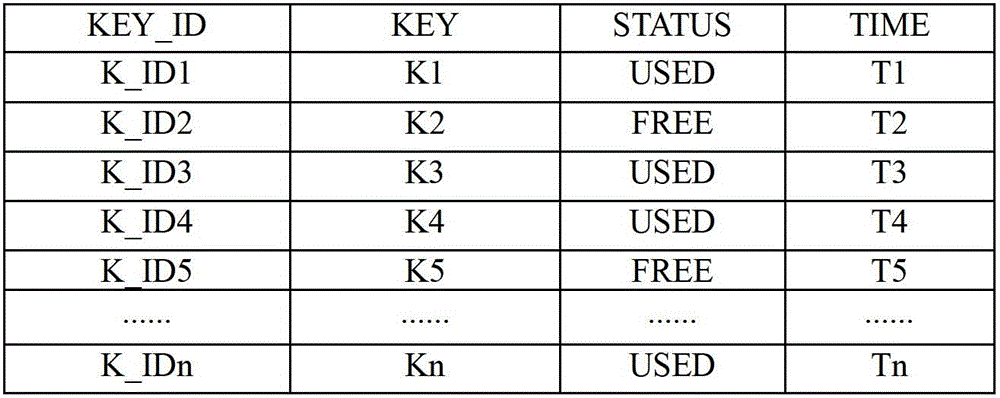
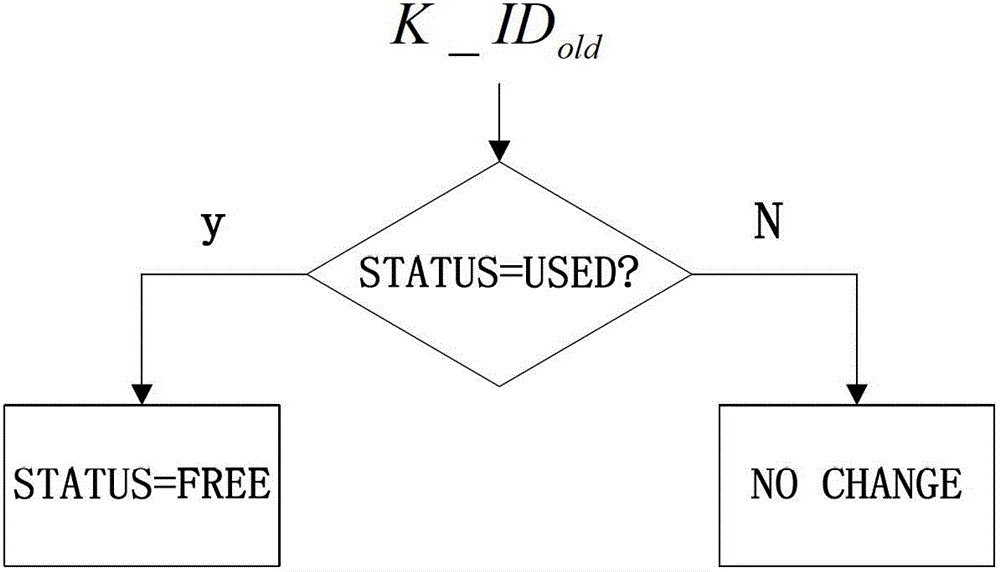
[0024] figure 1 It is a schematic diagram of an IMSI structure in an embodiment of the present invention, each MS has a different IMSI. Each HLR generates a keystore composed of multiple records. The size of the keystore is determined according to the number of MSs that the HLR belongs to. Each record includes four attributes, namely the key identification numbe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com