Method for extracting, analyzing and searching network flow and content
A network traffic and content technology, applied in the Internet field, can solve the problems of a wide range of restored data, inability to fully restore traffic information, and high requirements for original data integrity, to achieve the effect of facilitating effective information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
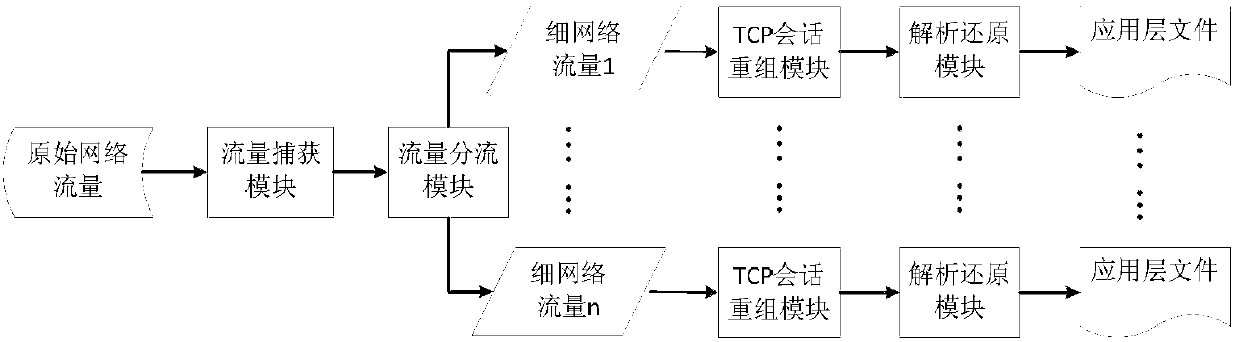
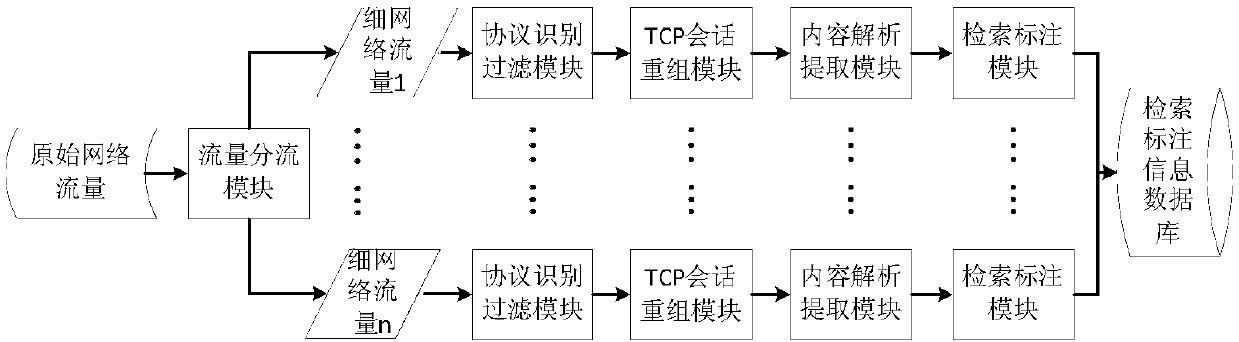
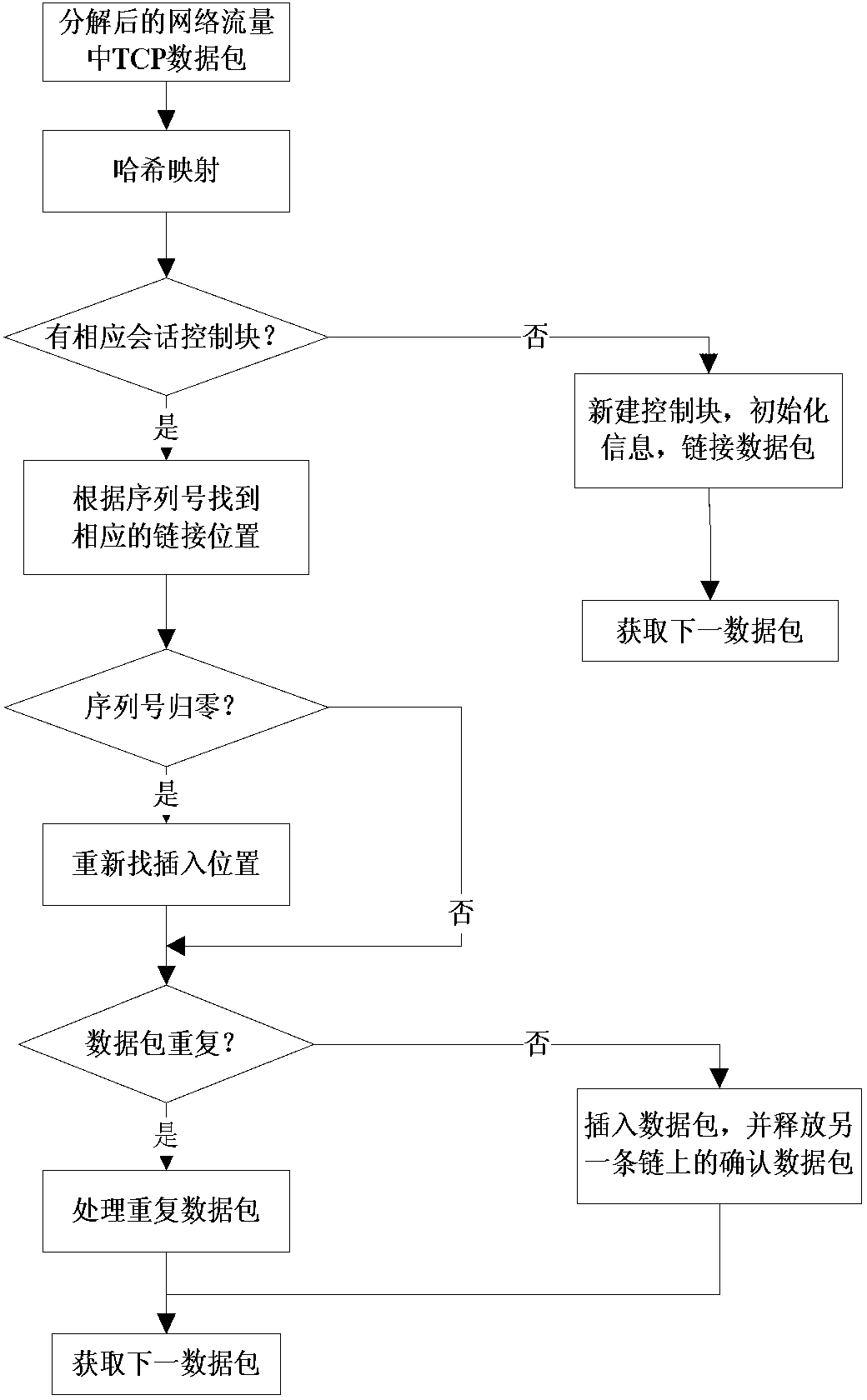
[0022] Such as figure 2 As shown, the network traffic content extraction and analysis retrieval method proposed by the present invention is used for content extraction and key information analysis retrieval of original network traffic, including the following steps:
[0023] The first step is to use the traffic distribution module to process the original data packets in the traffic files captured and stored from the high-speed network, set the corresponding number of data processing queues n according to the number of server computing cores, and hash the triplets of data packets Greek operation, splitting the original traffic to n data processing queues for processing separately. Wherein, the triplet includes the source IP address (SIP) and destination IP address (DIP) of the data message and the protocol number of the IP message.
[0024...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com