Method of generating key
A technology of key generation and key generation device, applied in key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
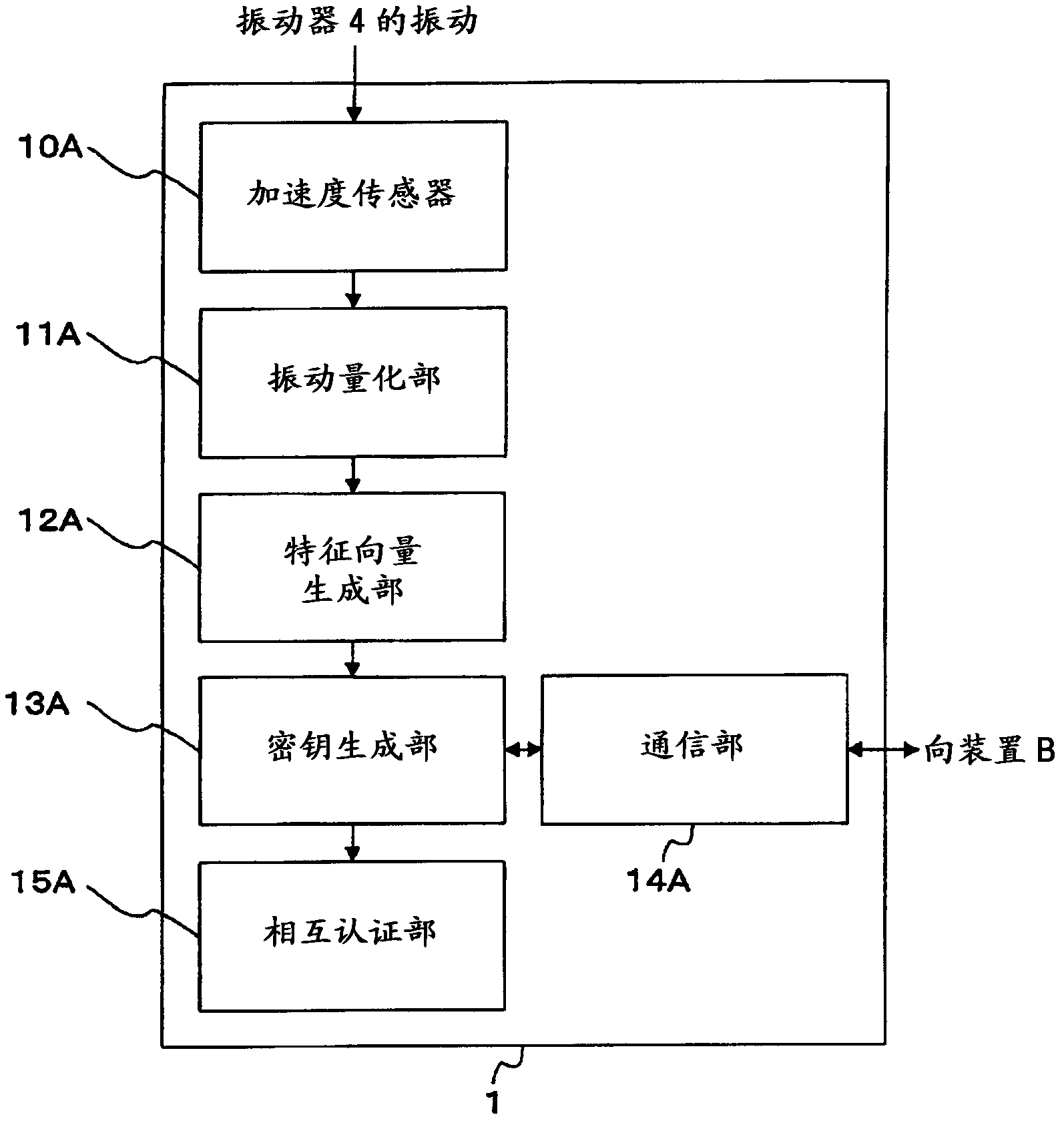
[0079] like Figure 11 As shown, the first device 20A (device A) of this embodiment is the same as the first device 1 in the key generation system 100 described above except that the first vibrator 21A and the first vibrator control unit 22A are incorporated. Structure. The first vibrator 21A and the first vibrator control unit 22A correspond to the vibrator 4 and the vibrator control unit 5 in the key generation system 100 described above, respectively.
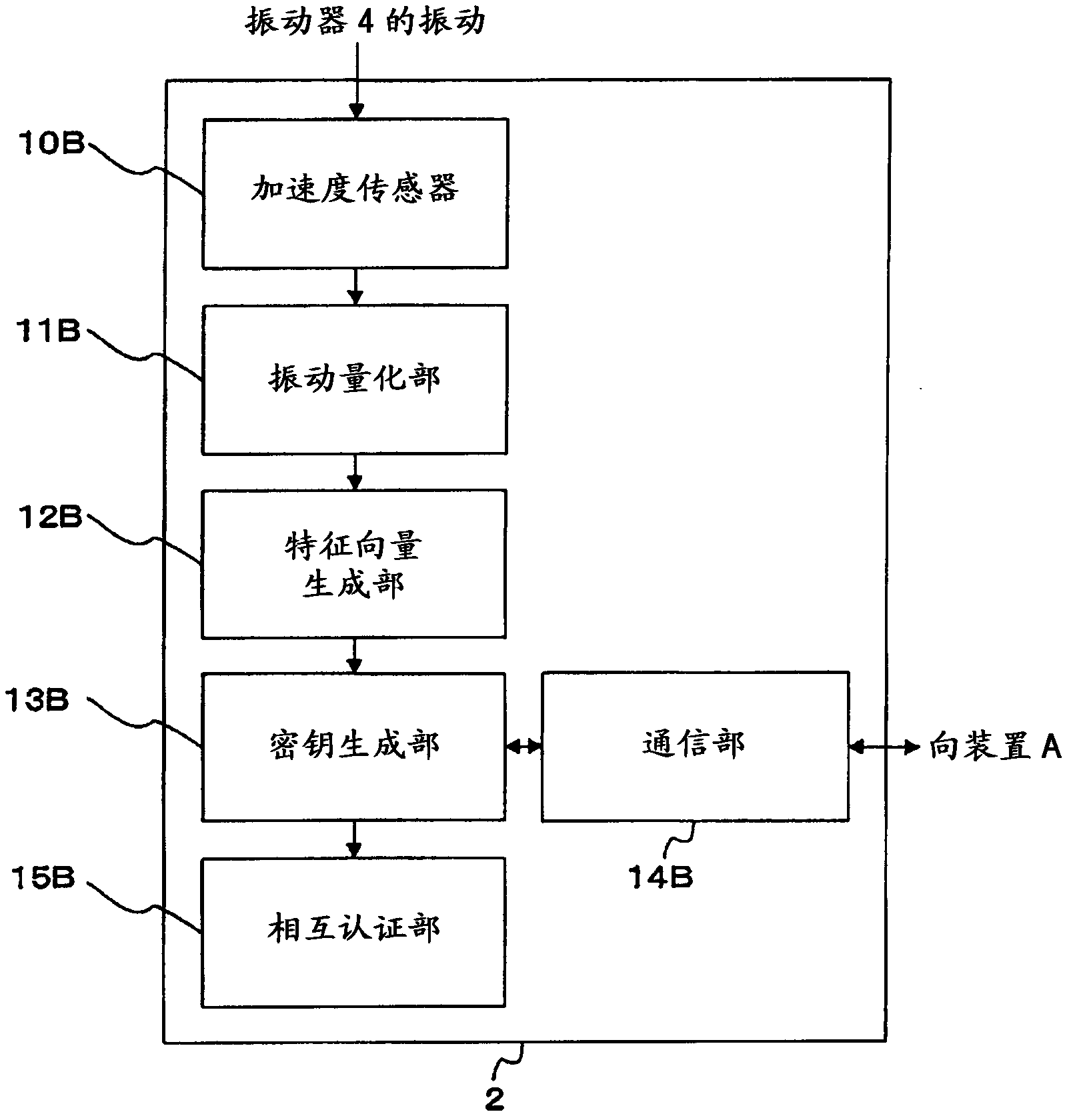
[0080] Similarly, if Figure 12 As shown, the second device 20B (device B) of this embodiment is the same as the second device 2 in the key generation system 100 described above except that the second vibrator 21B and the second vibrator control unit 22B are incorporated. Structure. The second vibrator 21B and the second vibrator control unit 22B correspond to the vibrator 4 and the vibrator control unit 5 in the key generation system 100 described above, respectively.
[0081] like Figure 11 as well as Figure 12 As ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com