Collision avoidance method under CELL_FACH state, base station and terminal thereof
A conflict avoidance and base station technology, applied in wireless communication, electrical components, etc., can solve problems such as increasing system processing flow and delay, and decreasing system work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
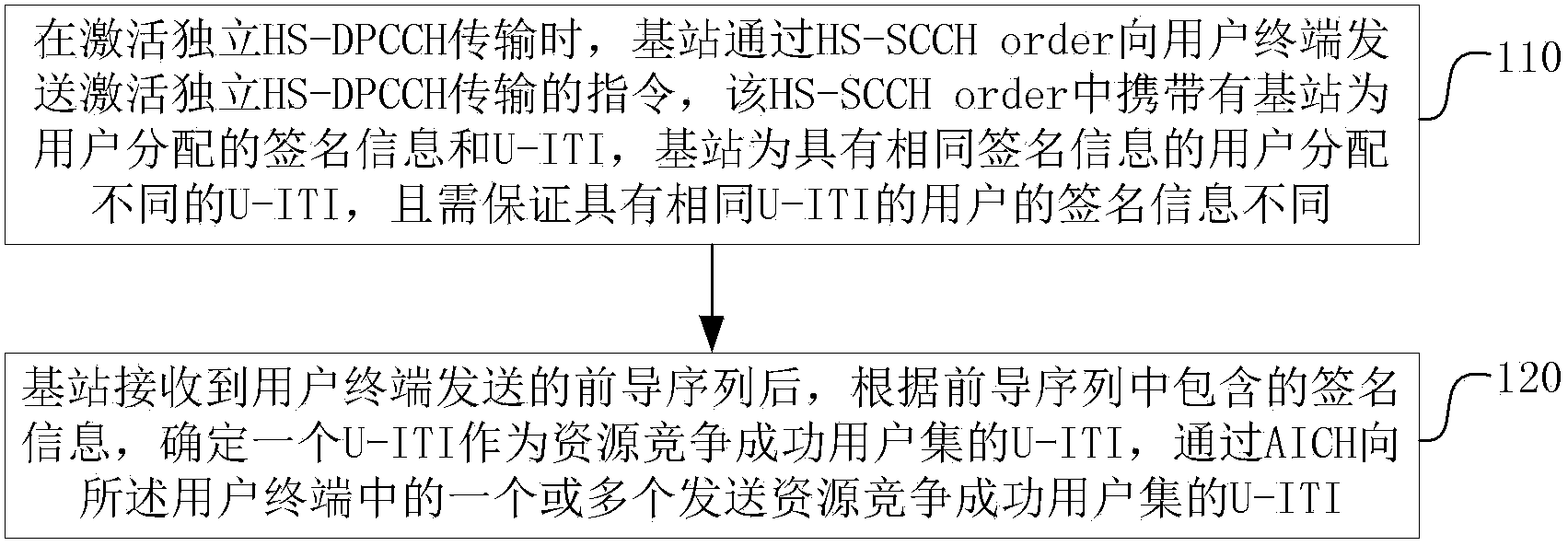
[0071] This embodiment introduces the collision avoidance method used in the HSDPA system CELL_FACH state, and the processing performed by the base station side, such as figure 1 shown, including the following steps:
[0072] Step 110, when activating the independent HS-DPCCH transmission, the base station sends an instruction to activate the independent HS-DPCCH transmission to the user terminal through the HS-SCCH order, and the HS-SCCH order carries the signature information assigned by the base station to the user and the user temporary group Internal identification information (U-ITI), the base station assigns different U-ITIs to users with the same signature information, and needs to ensure that the signature information of users with the same U-ITI is different;
[0073] The U-ITI is used to avoid resource conflicts among users. For the specific implementation of carrying the U-ITI through the HS-SCCH order, refer to the description of Embodiment 3. The base station a...
Embodiment 2
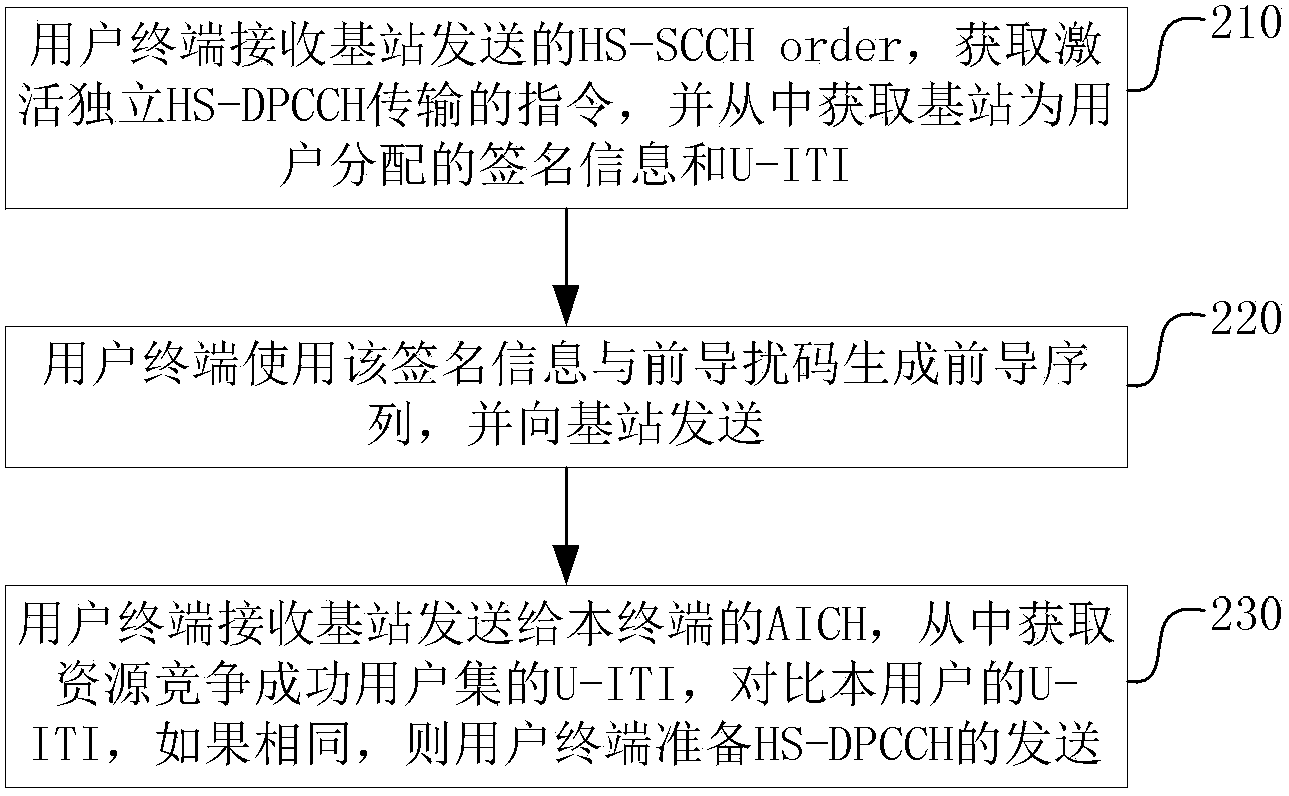
[0085] This embodiment introduces the collision avoidance method used in the HSDPA system CELL_FACH state, and the processing performed by the terminal side, such as image 3 shown, including the following steps:
[0086] Step 210, the user terminal receives the HS-SCCH order sent by the base station, obtains the instruction for activating independent HS-DPCCH transmission, and obtains the signature information and U-ITI allocated by the base station for the user;
[0087] Step 220, the user terminal uses the signature information and the preamble scrambling code to generate a preamble sequence and send it to the base station;
[0088] Step 230, the user terminal receives the AICH sent by the base station to the terminal, obtains the U-ITI of the user set that has successfully competed for resources, compares the U-ITI of the user, and if they are the same, the user terminal prepares to send the HS-DPCCH (using AICH HS-DPCCH transmission with the indicated resources).
[008...
Embodiment 3
[0097] This embodiment introduces how to carry signature information and U-ITI through HS-SCCH order.
[0098] The HS-SCCH order is a related instruction sent by the base station to the user through the HS-SCCH channel, and it is not associated with any specific downlink data. Table 1 is a schematic diagram of bit allocation of HS-SCCH order in the existing protocol. In the prior art, the HS-SCCH order has a total of 24 bits. Among them, 16 bits are used to carry user identification information (HS-DSCH Radio Network Identifier, H-RNTI) indicating that a specific user is in the network. The other 8 bits are used to carry instruction information, among which 2 bits are used to indicate the extended instruction type, 3 bits are used to indicate the basic instruction type (the instruction type in Table 1); and the remaining 3 bits are used to indicate specific instructions content. In the existing CELL_FACH state, since multi-carrier operation is not configured, and the premis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com