Zombie network detection method, device and processor
A botnet and detection method technology, which is applied in the field of botnet detection methods, devices and processors, can solve the problems that detection algorithms cannot perform effective detection, etc., and achieve the effects of reducing workload, reducing data volume, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
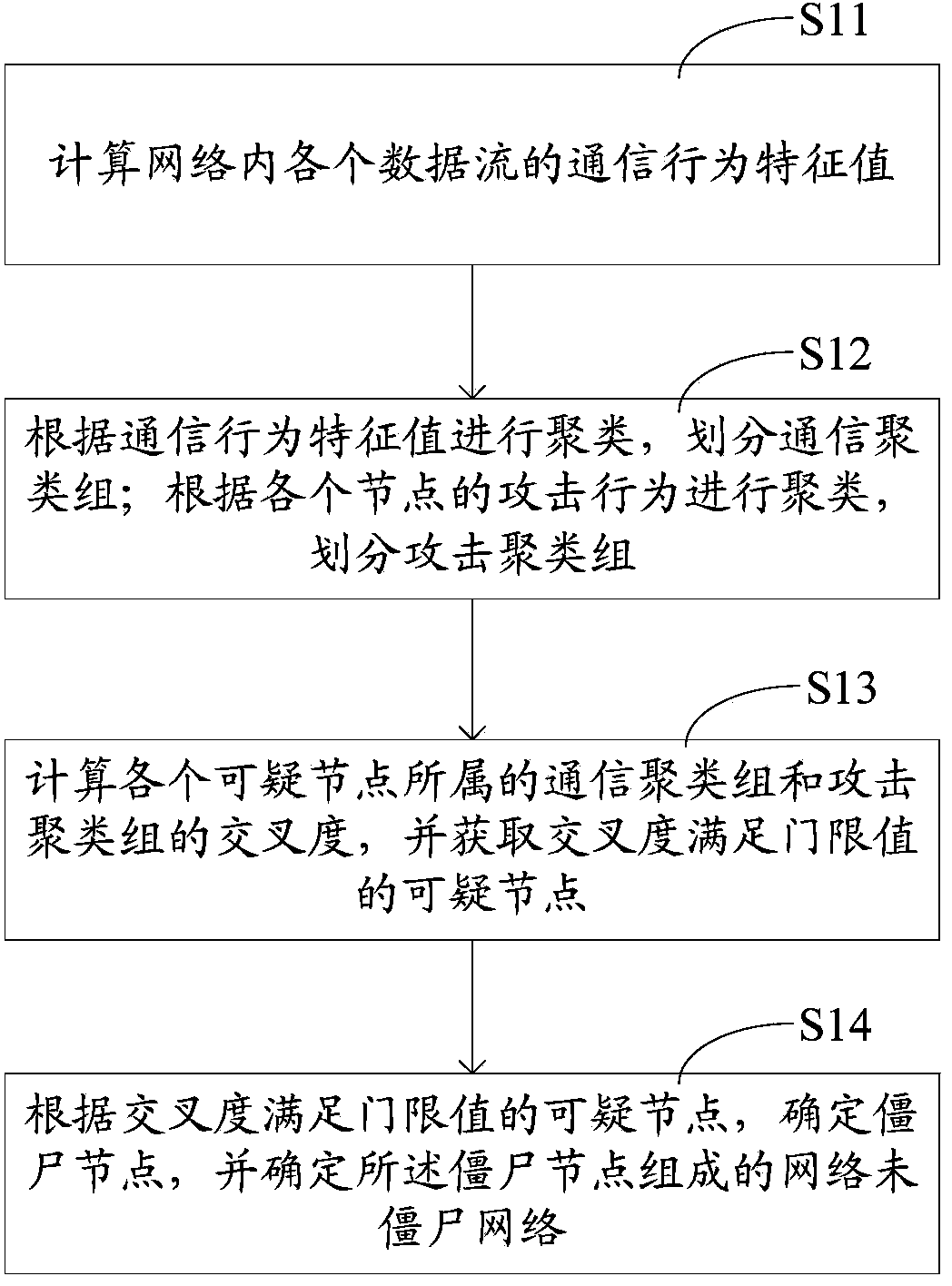
[0051] This application discloses a method for detecting a botnet, so as to realize the detection of the botnet. see figure 1 As shown in the schematic diagram of the workflow, the botnet detection method includes:
[0052] Step S11 , calculating the communication behavior characteristic values of each data flow in the network, the communication behavior characteristic values including: the average number of bytes per packet and the average number of bytes per second.
[0053] The communication of each node is reflected on the network through data flow, and the basic unit is data flow. A typical example is a TCP-based communication: (1) establish a connection through a three-way handshake; (2) perform data transmission; (3) release the connection through four handshakes. Therefore, in order to analyze the similarity between the communication behaviors of each node, the present application analyzes each data flow in the network.
[0054] For each data flow, this applicat...
Embodiment 2
[0121] Embodiment 2 of the present application discloses a botnet detection device, see Figure 4 As shown in the structural diagram, the botnet detection device includes: a feature value calculation module 11, a clustering module 12, a cross-clustering module 13 and a detection module 14, wherein,
[0122] The characteristic value calculation module 11 is used to calculate the communication behavior characteristic value of each data flow in the network, and the communication behavior characteristic value includes: the average number of bytes per packet and the average number of bytes per second;
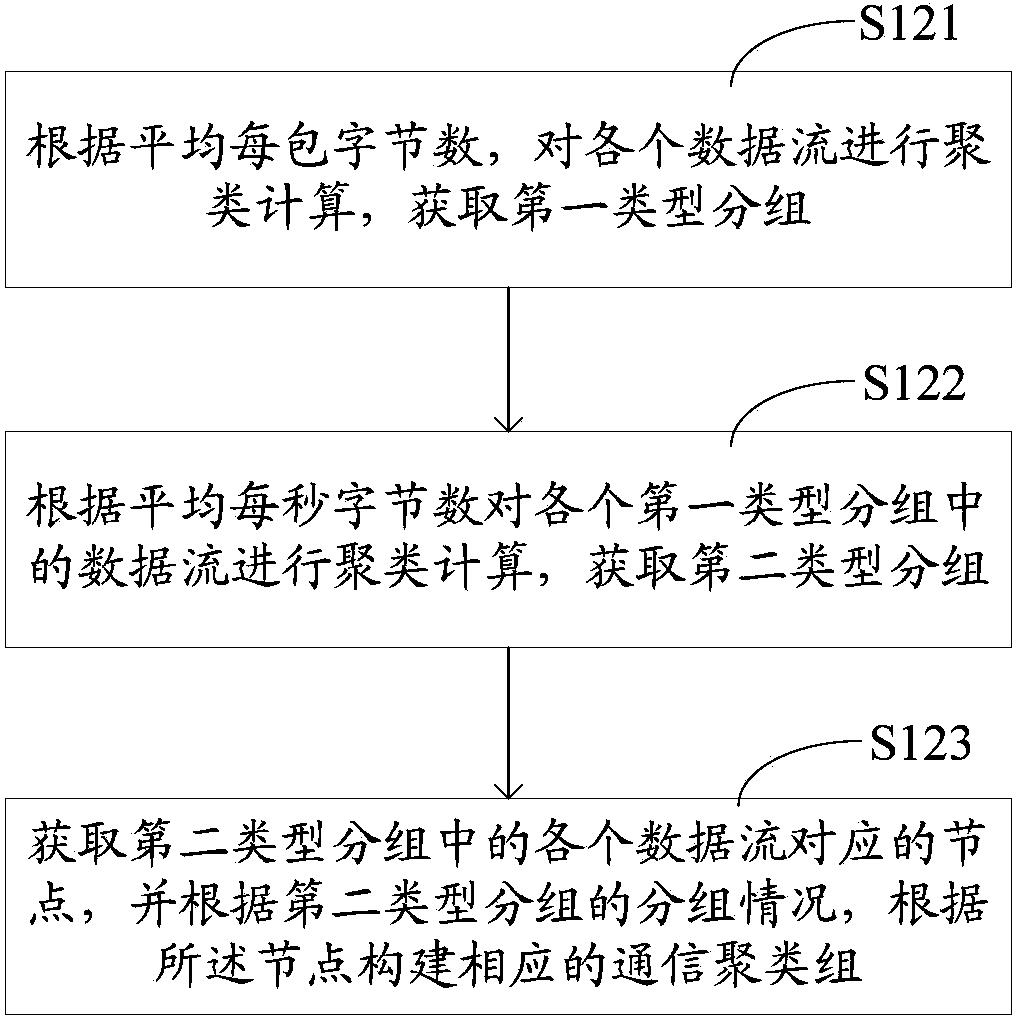
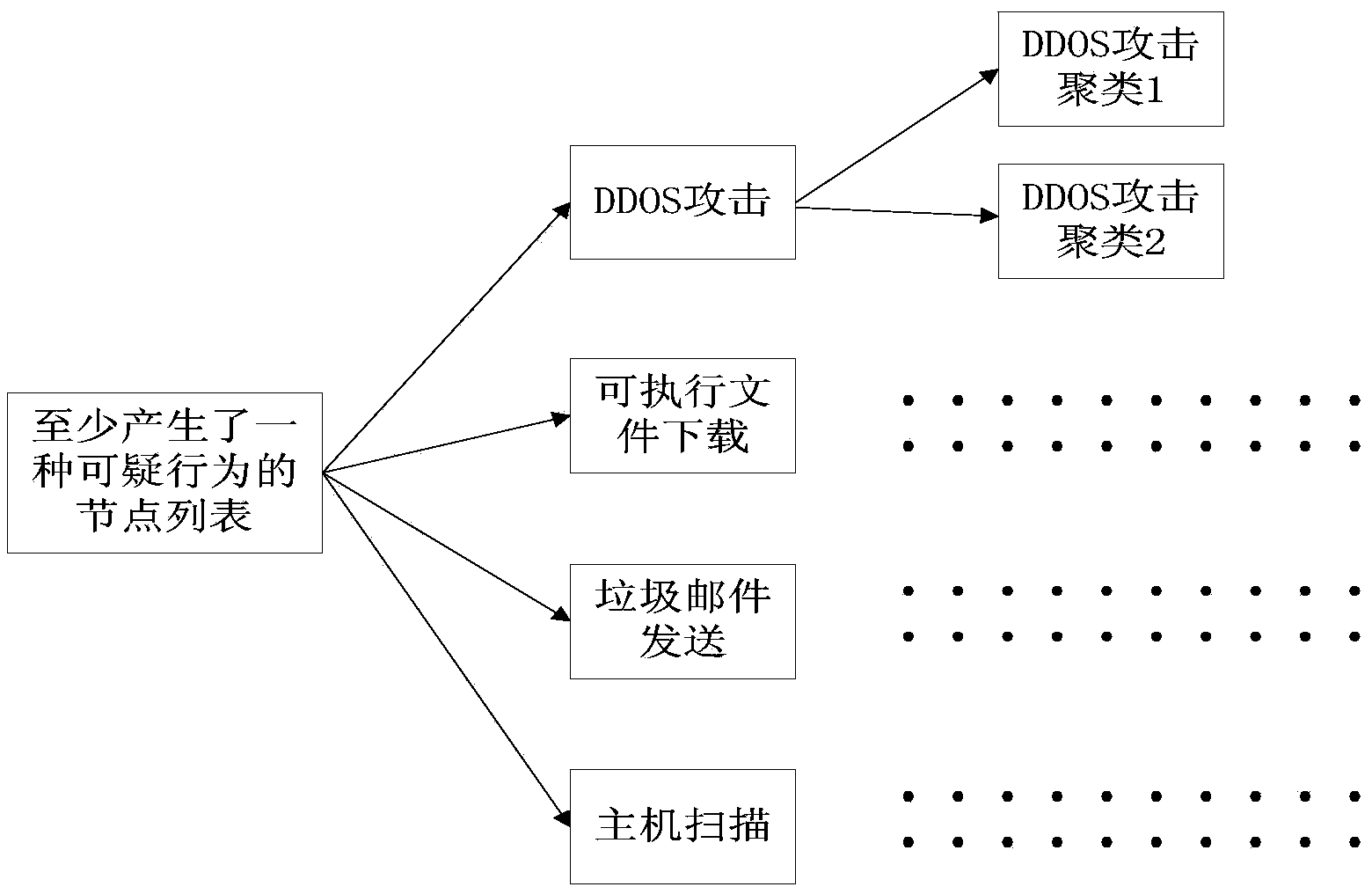
[0123] The clustering module 12 is configured to perform clustering according to the characteristic value of the communication behavior, and divide the nodes corresponding to the respective data streams into a plurality of communication clustering groups, wherein the nodes in each communication clustering group have similar communication behavior, and the number of nodes contained i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com