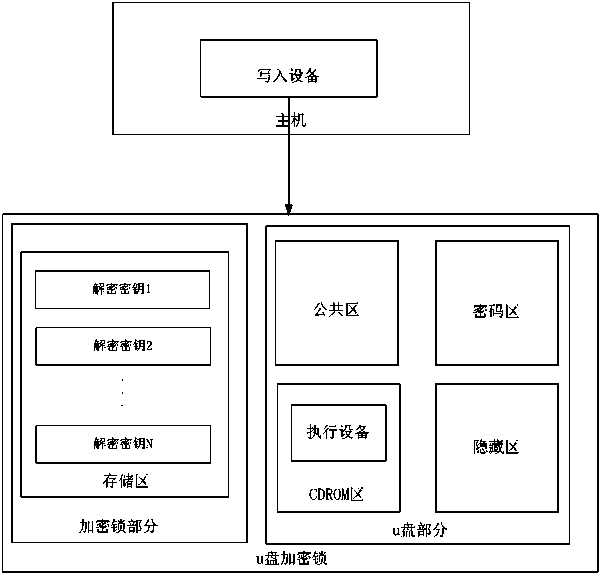
Data file protecting method and device
A data file and protection system technology, applied in the field of information security, can solve the problems of easy leakage of data information, increase the difficulty of debugging and cracking, prevent memory DUMP, and improve execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
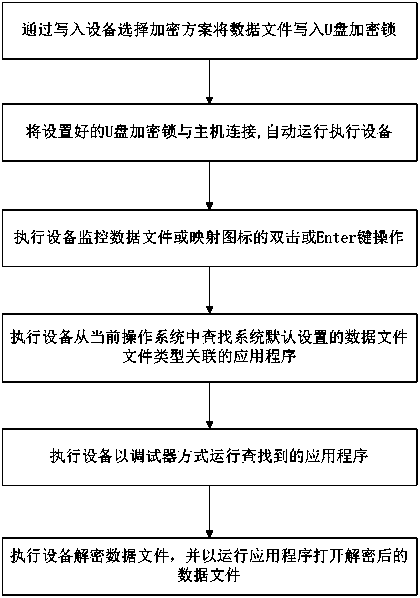
[0106] image 3 It is a flow chart of the preferred embodiment 1 of a data file protection method according to the present invention.
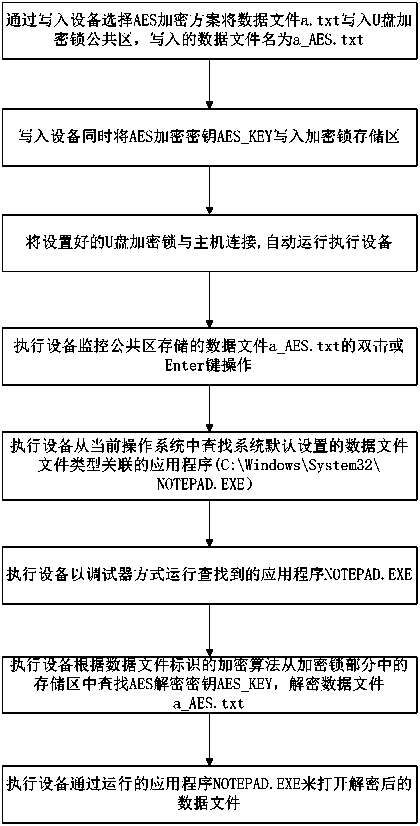
[0107] see image 3 , the host operating system in this embodiment is Windows, the data file to be protected is a text file a.txt with an extension name of .txt, and the application program associated with the text file is stored in the registry of the Windows system as NOTEPAD. Program), assuming the path is C:\Windows\System32\NOTEPAD.EXE, the naming format of the data file written in the U disk part of the U disk dongle is: file name + "_" + "encryption algorithm keyword (such as AES) "+"."+"file extension". According to an embodiment of the present invention, the protection method of this data file comprises:
[0108] 1. Select the AES encryption scheme through the writing device to write the data file a.txt into the public area of the U disk part of the U disk dongle, and the data file written into the U disk part of the U disk dongl...
Embodiment 2
[0117] Figure 4 It is a flow chart of the preferred embodiment 2 of a data file protection method according to the present invention.
[0118] see Figure 4 , the difference between embodiment 2 and embodiment 1 lies in step 1 and step 2, and step 1-2 of this embodiment is:
[0119] 1. The key information of all encryption schemes written to the device is preset in the storage area of the dongle part of the U disk dongle;
[0120] 2. Select the AES encryption scheme through the writing device to write the data file a.txt into the public area of the U disk dongle, the file name remains unchanged, and at the same time generate a mapping table of the corresponding relationship between the data file and the encryption algorithm in the U disk dongle;
[0121] The remaining steps are similar to Example 1, including:
[0122] 3. Connect the set U disk dongle to the host, and automatically run the execution device;
[0123] 4. Execute the double-click or Enter key operation o...
Embodiment 3
[0131] Figure 5 It is a flow chart of the preferred embodiment 3 of a data file protection method according to the present invention.
[0132] Such as Figure 5 As shown, the operating system of this embodiment is Windows, and the data file is a file (i.e. a word file) with an extension of . System32\WINWORD.EXE. According to an embodiment of the present invention, the data file protection method includes:
[0133] 1. Select the DES encryption scheme through the writing device to write the data file b.doc into the hidden area of the U disk in the U disk dongle, and at the same time generate a mapping icon for the content of the data file stored in the hidden area in the password area of the U disk. Assuming that the icon name is still b.doc, the map icon attribute stores the location of the data file content stored in the map hidden area;
[0134] 2. The writing device writes the DES encryption key DES_KEY into the storage area of the dongle part of the U disk dongl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com