Method for symmetric cryptographic algorithm to resist side-channel analysis
A symmetric cryptographic algorithm and cryptographic technology, applied in the field of symmetric cryptographic algorithm resistance to side channel analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
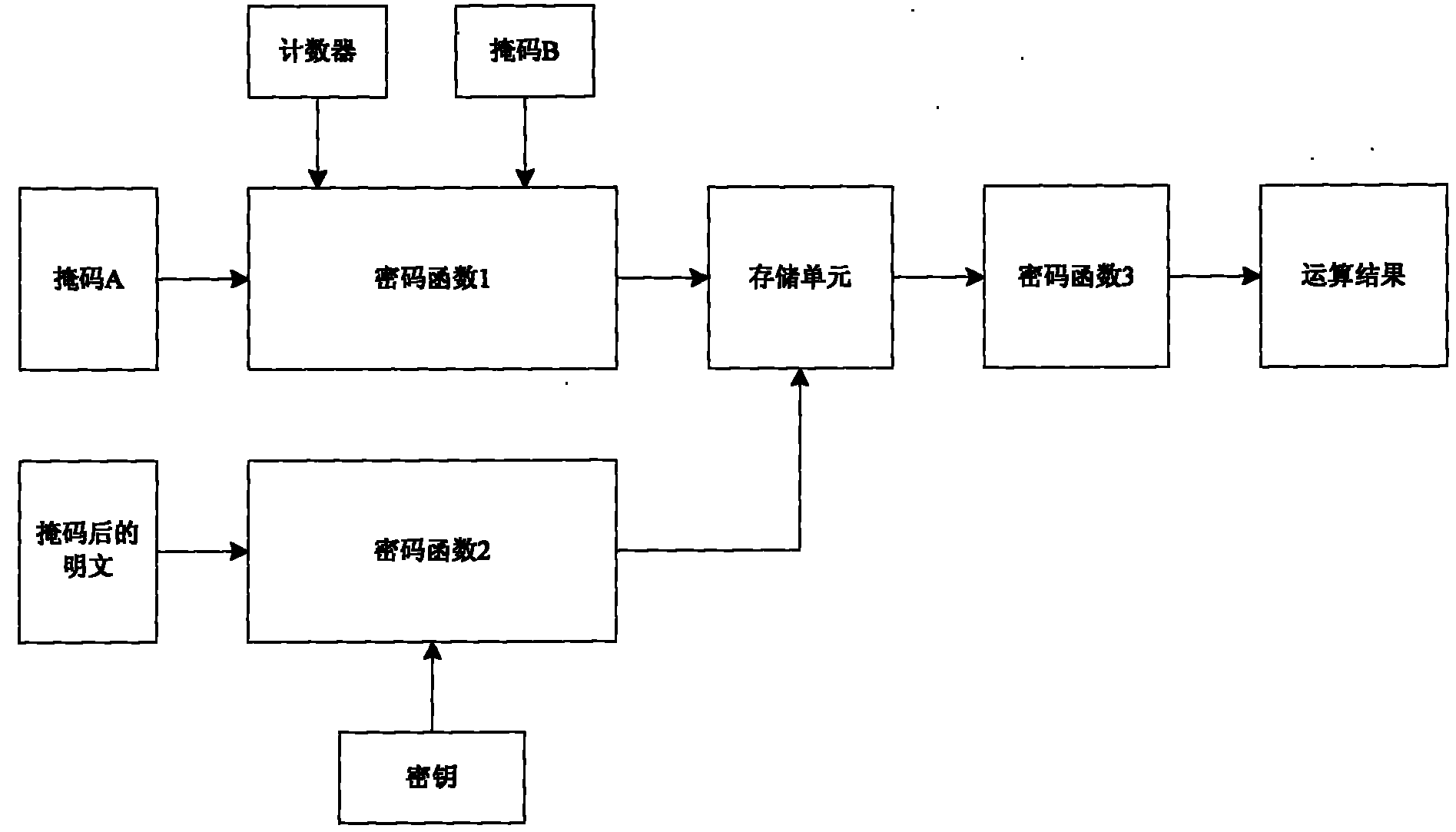
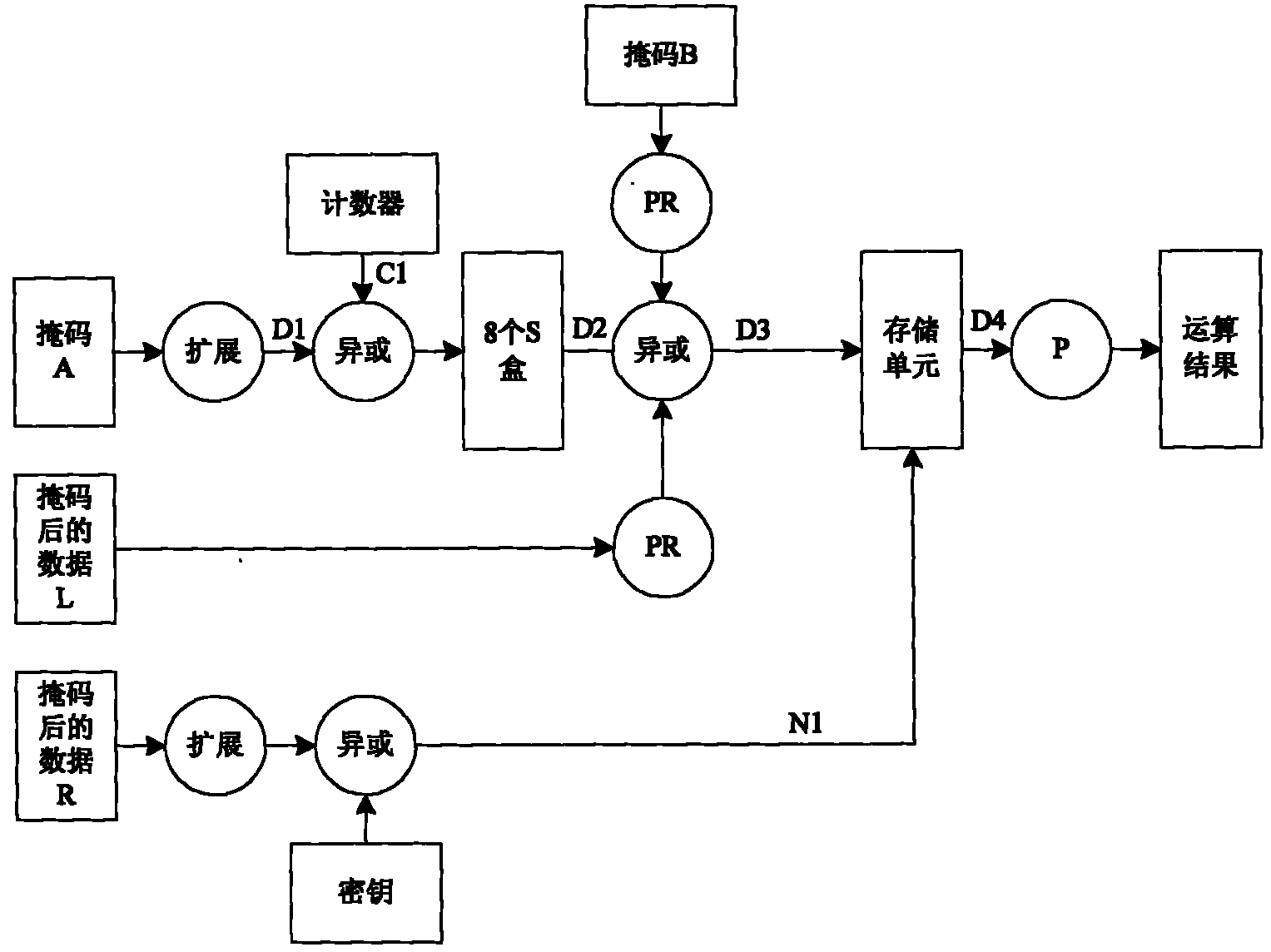
[0010] The present invention is applicable to a variety of symmetric encryption algorithms. The specific implementation of the method of the present invention will be described below by taking the common DES algorithm among the symmetric encryption algorithms as an example.
[0011] The original calculation process of the DES algorithm is to divide the 64-bit plaintext into left L0 and right R0, each with 32 bits, and the right half of the data R0 is extended to 48-bit width through the expansion transformation E, and then it is different from the 48-bit wide round key Key1. Or, the generated 48-bit data is divided into 6-bit groups, a total of 8 groups, and 32-bit data is generated through 8 6-in and 4-out SBOXs. The result is transformed by P and then XORed with the left half of the data L0 to generate a round operation result R1=L0^F(R0, key1), R0 is swapped to the left half to generate L1=R0. Repeat this step until 16 rounds of calculations are completed.
[0012] Applyin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com