Method and system for mobile device voiceprint registration and authentication
A mobile device, voiceprint technology, applied in transmission systems, electrical components, voice analysis, etc., can solve problems such as inability to protect user privacy, difficult to guarantee real-time performance, and reduced user experience, so as to increase a good experience and ensure user experience. and normal use, the effect of reducing computing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
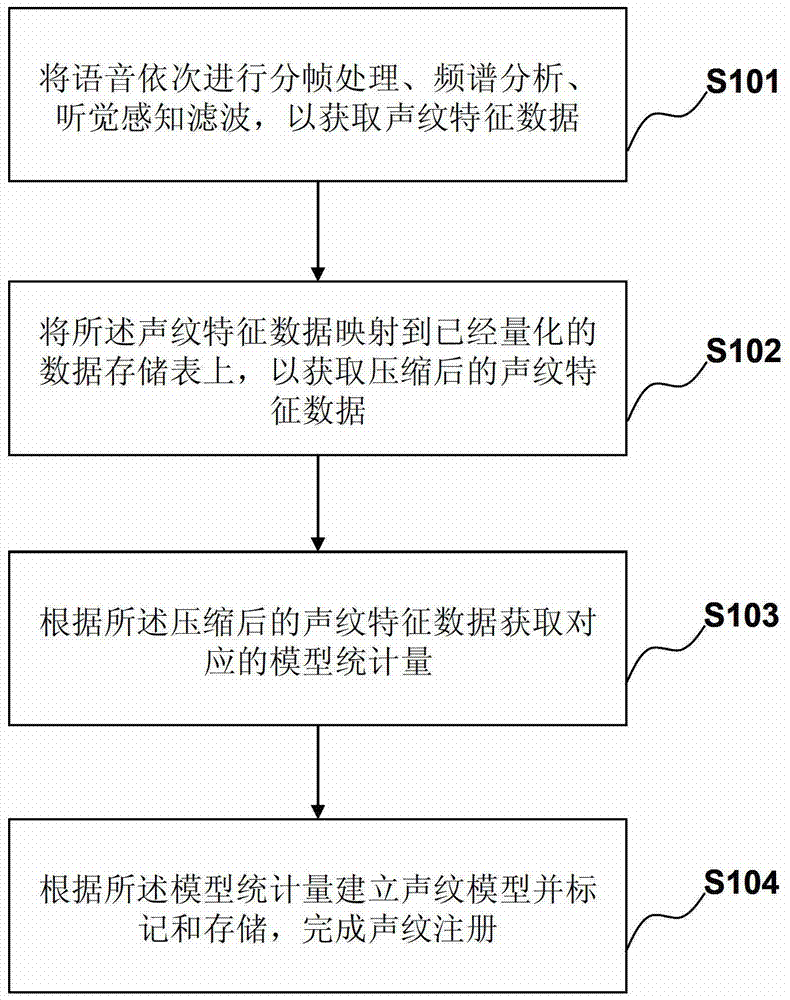
[0085] see figure 1 , is a flow chart of a method in Embodiment 1 of the present invention. This embodiment provides a mobile device voiceprint registration method, the method comprising:
[0086] S101: Process the voice into frames, perform frequency spectrum analysis, and perform auditory perception filtering in order to obtain voiceprint feature data. To realize the application of voiceprint encryption on mobile devices such as mobile phones, the first and most important thing is to register the voiceprint. Voiceprint registration needs to obtain voiceprint feature data first, and the basic process is as follows: First, the user's recording data is divided into frames, and each frame of voice is calculated for spectrum analysis. When estimating the impact of noise on the voice spectrum, an auditory perception mechanism is introduced. , to estimate the influence of noise on each frame of speech spectrum, and thus to construct the corresponding filter parameters, and finall...
Embodiment 2
[0115] see Figure 4 , is a flow chart of the method in Embodiment 2 of the present invention. This embodiment provides a method for voiceprint authentication of a mobile device. This embodiment corresponds to Embodiment 1. The first three steps of this embodiment are the same as S101~S103 in Embodiment 1. The difference is that in Embodiment 1, after S103 obtains the model statistics of voiceprint, the connected The next step is S104, which is to register the voiceprint; and in this embodiment, after obtaining the model statistics of the voiceprint, the next steps are:
[0116] S105: Compare the model statistics with the stored voiceprint model, and then perform authentication according to the obtained matching degree.
[0117] That is, input a piece of voice, and then compare and match with the registered voiceprint features after extracting the relevant features of the voiceprint through the above method, so as to judge whether it is the voiceprint of the same person and ...
Embodiment 3
[0119] The process of voiceprint registration and authentication will be further described below in combination with the above-mentioned embodiments, and specifically taking a mobile phone with an Android system as an example.
[0120] A common problem with lock screen applications on Android phones is that they cannot be locked. By pressing home or pulling down the status bar, you can skip the lock screen interface and directly enter the system. The screen lock function of application like this is exactly false, does not reach the purpose of screen lock, and the privacy in user's mobile phone is also difficult to be protected. This embodiment allows users to define their own passwords, and the system can also randomly generate a digital password to provide to the user. When the user uses it, he does not need to remember the password, as long as he reads the prompt text at a normal speech rate, the system extracts the password according to the user's voice. The user's voicepri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com