Wireless sensor network intrusion tolerance method and system based on tree topology
A wireless sensor network and tree topology technology, applied in wireless communication, network topology, electrical components, etc., can solve the problems of high false alarm rate, false alarm rate time delay, inability to prevent intrusion damage, etc. in the intrusion detection system, and achieve The effect of prolonging the lifetime and reducing network resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in detail below with reference to the drawings and embodiments.
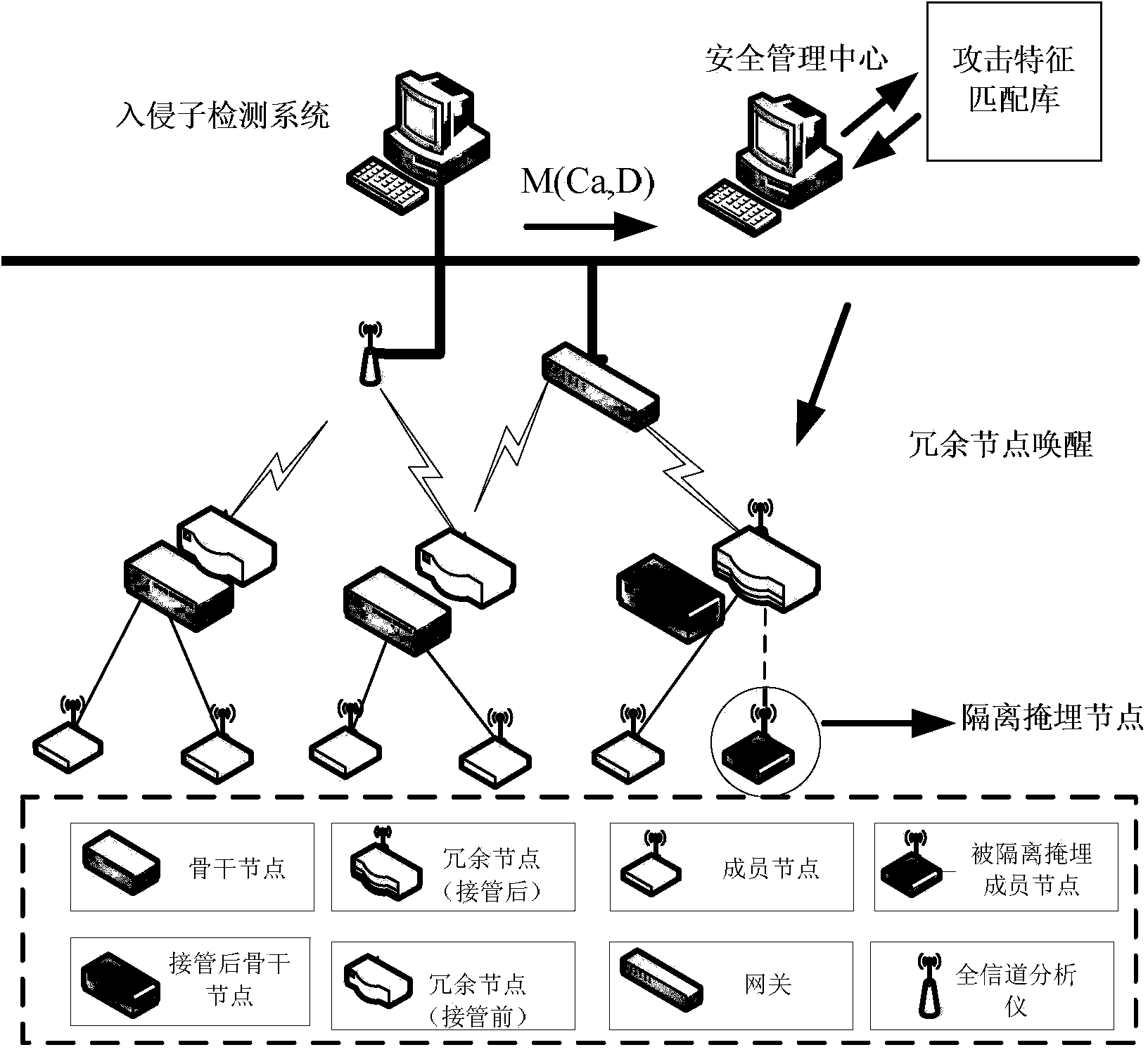
[0021] like figure 1 As shown, the intrusion tolerance system involved in the present invention includes: a full channel analyzer, an intrusion detection subsystem, an attack signature matching library, a security management center, a gateway, a backbone node, a redundant node and a member node.
[0022] The full channel analyzer monitors the data traffic and energy information of the entire wireless sensor network, and sends the monitored information to the intrusion detection subsystem;
[0023] Based on the information from the full-channel analyzer, the intrusion detection subsystem conducts real-time data analysis, extracts data features, judges whether it is attacked by intrusion, and reports the judgment result to the security management center;
[0024] The security management center is responsible for allocating the resources required for the entire network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com