Communication terminal and system and authority management method
A communication terminal and authority management technology, applied in wireless communication, transmission system, digital transmission system, etc., can solve the problem of difficulty in proper and effective management of WiFi mobile device access authority, achieve efficient authentication process, simple management, increase The effect of password authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
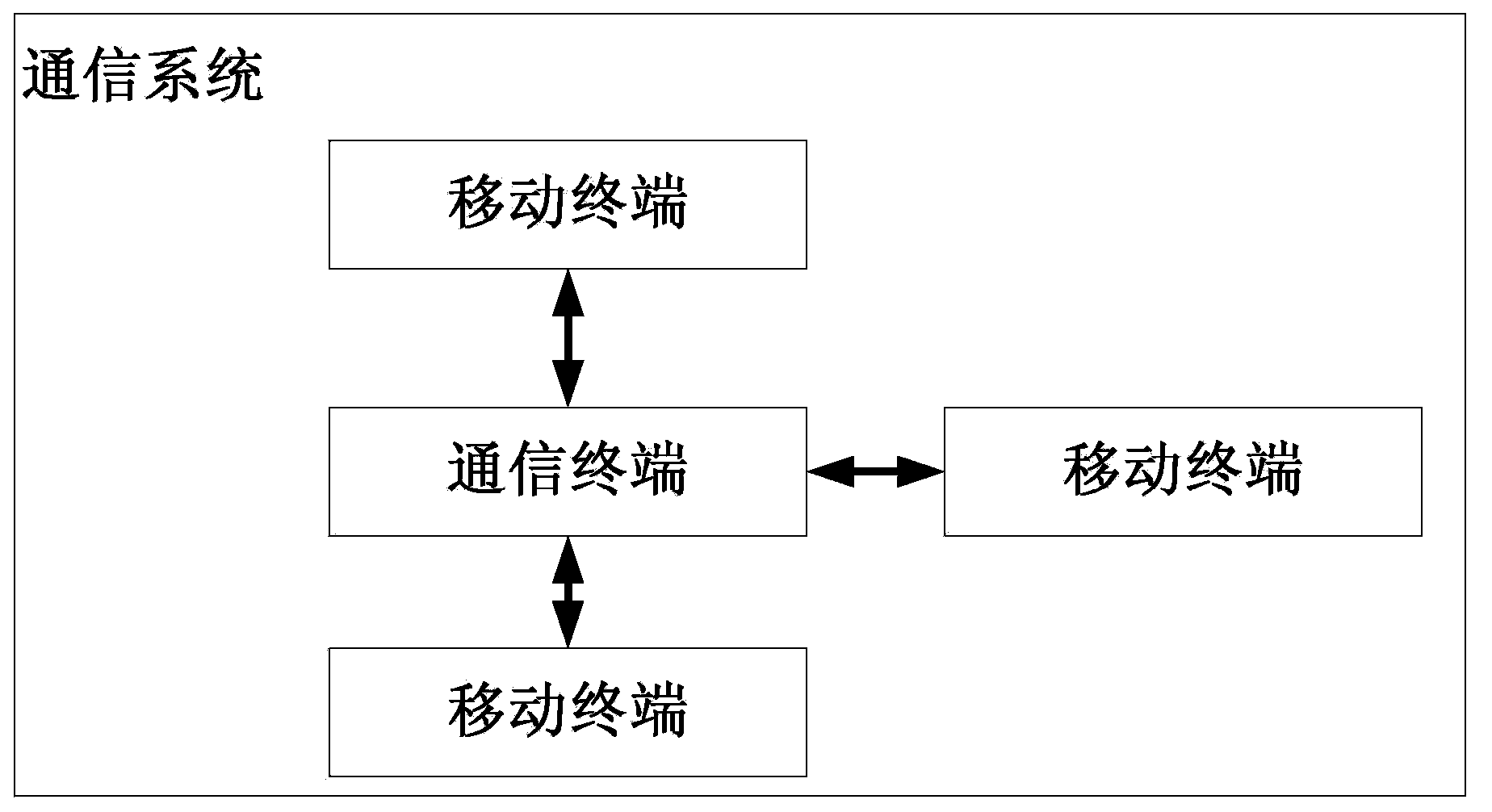
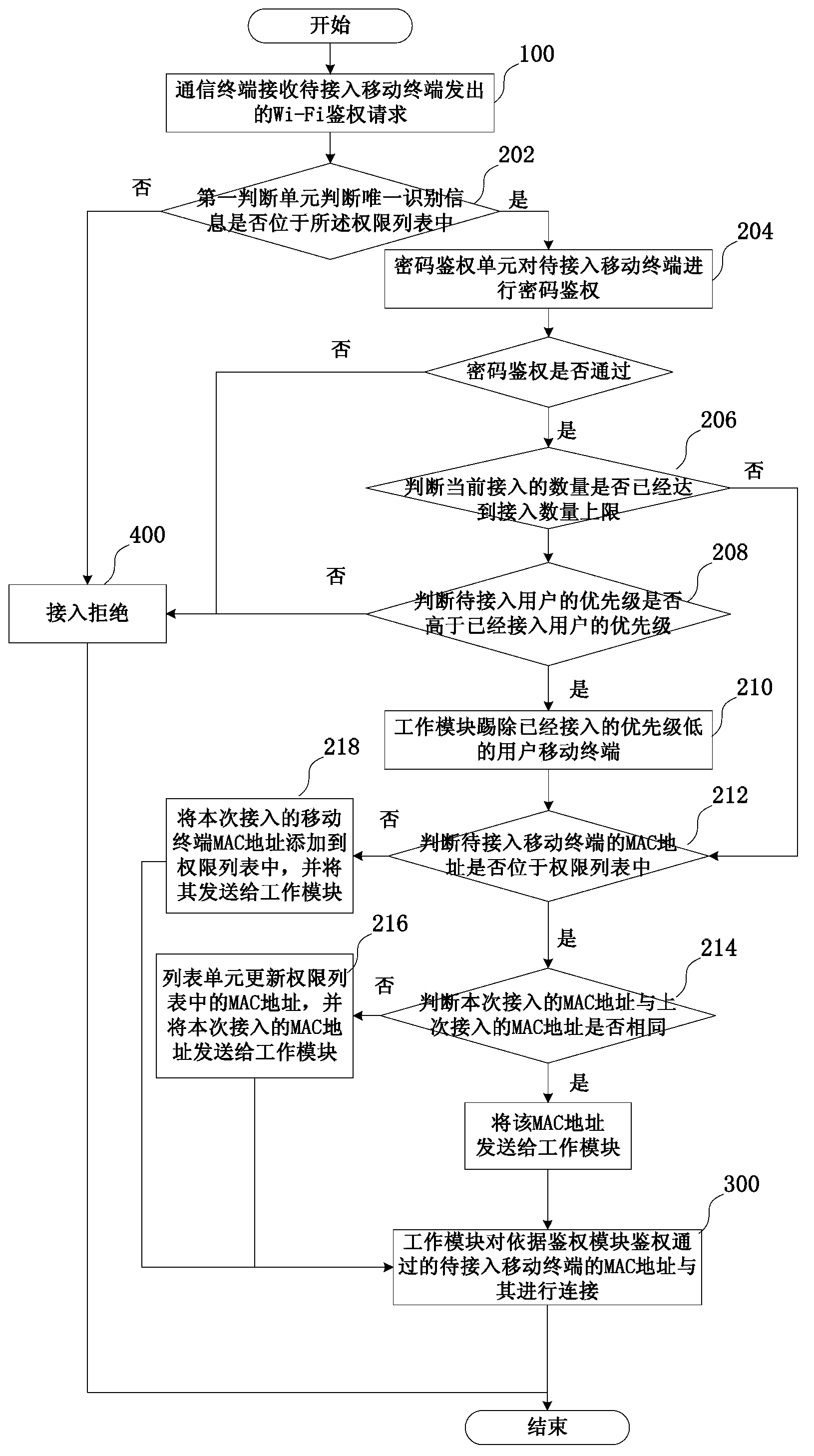
[0038]The overall idea of the present invention is: by setting a permission list for managing user permissions in the communication terminal of the WiFi hotspot, storing the unique identification information of the identity of the user who is allowed to access in the list; The authentication request contains the unique identification information of the user. The communication terminal compares the identification information with the identification information in its authorization list. If the two match, it extracts the MAC address of the terminal to connect. If the terminal is the first time If the mobile terminal has logged in before, it will directly extract the MAC address in the authentication request to connect, and save the MAC address in the permission list. If the mobile terminal has logged in before, the MAC address of this access Compare the incoming MAC addresses, if the two are the same, connect directly according to the MAC address, but if the two are not the sam...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com