An authentication method and device
A technology for authenticating equipment and authentication methods, which is applied in the field of communication, can solve problems such as WLAN security reduction, MAC address counterfeiting, duplication, etc., and achieve the effect of improving experience and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
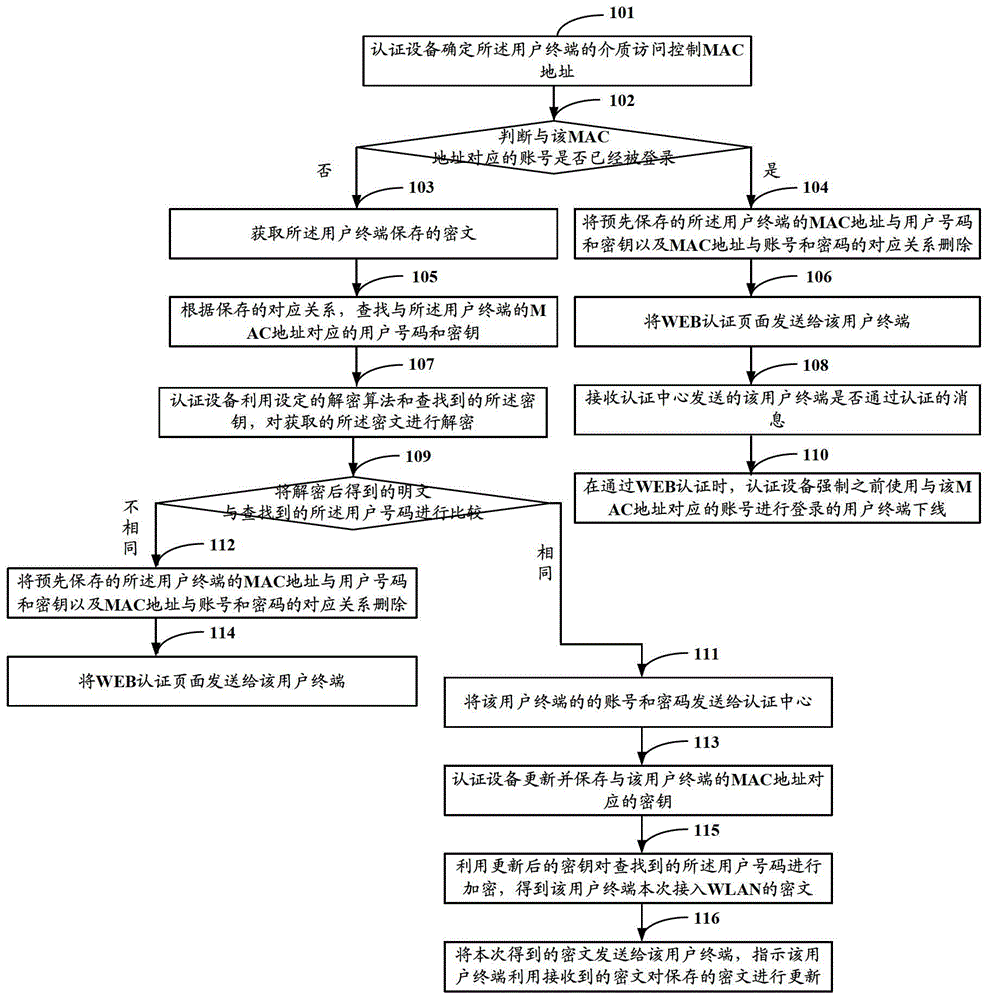
[0030] Such as figure 1 As shown, it is a flowchart of the authentication method in Embodiment 1 of the present invention, and the method includes the following steps:
[0031] Step 101: When a user terminal accesses a WLAN, the authentication device determines the MAC address of the user terminal.
[0032] The MAC can be obtained from the HTTP request carrying the MAC address sent by the user terminal.
[0033] Step 102: The authentication device judges whether the account corresponding to the MAC address has been logged in, if not, execute step 103, and if yes, execute step 104.
[0034] It should be noted that this step 102 is a preferred step, and its purpose is to prevent repeated logins of the same account. When the same account is logged in repeatedly, the user who logged in before may be an illegal user, or the user logged in in step 101 may be an illegal user. The following Step 104, step 106, and step 108 are to check whether the user logging in with the account co...
Embodiment 2
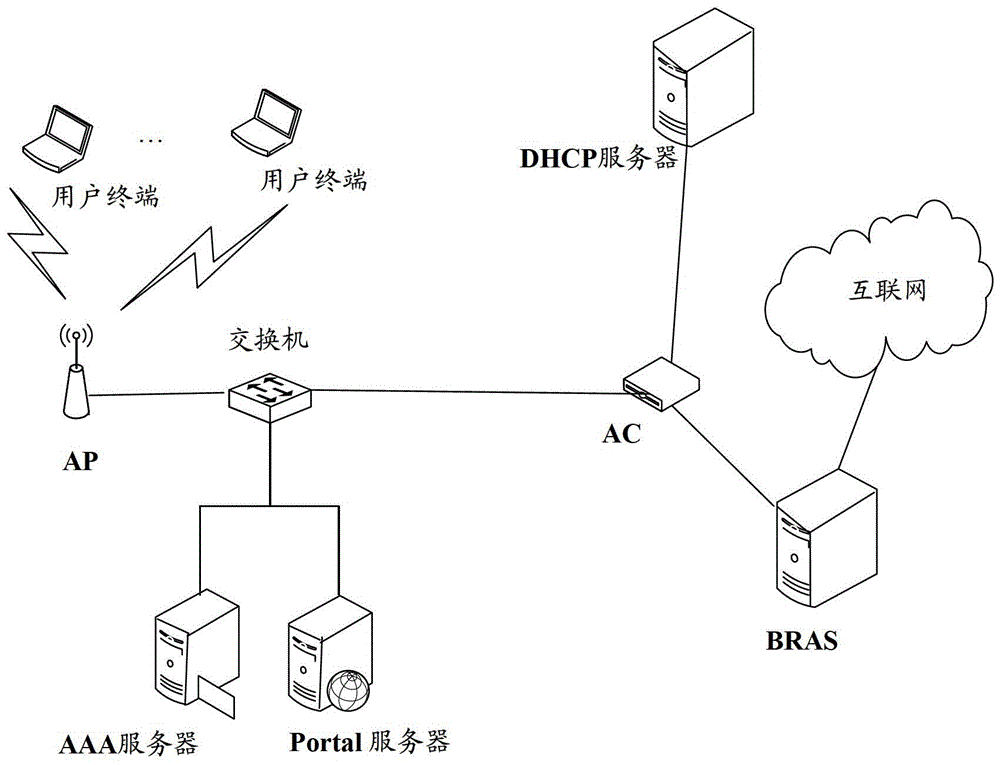
[0067] first to figure 2 The networking architecture of the WLAN shown is introduced. figure 2 Including: user terminal, wireless access point (Access Point, AP), wireless controller (Access Controller, AC), switch, portal (Portal) server, authentication, authorization and accounting (Authentication, Authorization, Accounting, AAA) server, Broadband Remote Access Server (BRAS) server, Dynamic Host Configuration Protocol (Dynamic Host Configuration Protocol, DHCP) server.
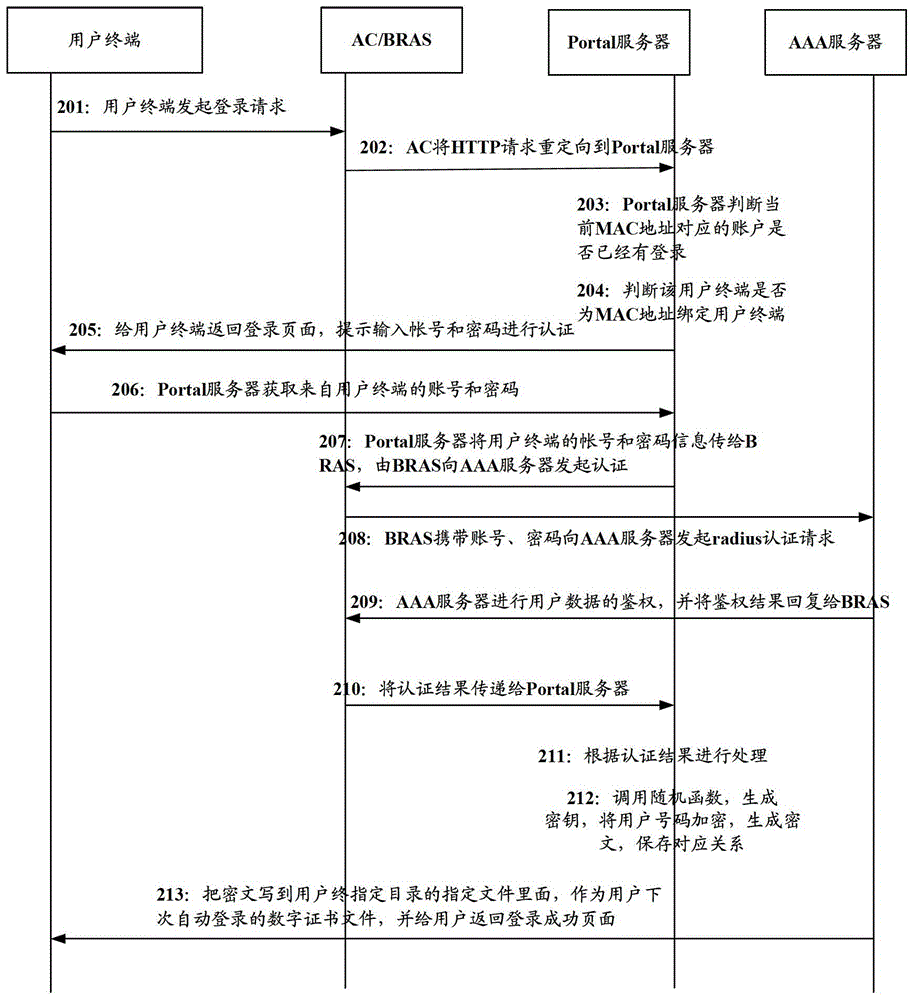
[0068] exist figure 2 On the basis of the shown WLAN networking architecture, the flow chart of the authentication method in Embodiment 2 of the present invention, as shown in image 3 As shown, it specifically includes the following steps:
[0069] Step 201: The user terminal (personal computer, smart phone, tablet computer, etc.) initiates a login request, associates with the AC, obtains the login IP address, and sends an HTTP request to the AC. The HTTP request carries the user terminal's ID MAC ad...
Embodiment 3
[0092] Such as Figure 4 As shown, it is a flowchart of the authentication method in Embodiment 3 of the present invention, which specifically includes the following steps:
[0093] Step 301: A user terminal (personal computer, smart phone, tablet computer, etc.) initiates a login request, associates with the AC, obtains the login IP address, and sends an HTTP request to the AC. The HTTP request carries the user terminal's ID MAC address.
[0094] Step 302: the AC redirects the HTTP request to a portal (Portal) server.
[0095] Step 303: The Portal server judges whether the account corresponding to the current MAC address has already logged in. If there is a login, it means that the MAC address is repeated, and the user terminal needs to re-enter the account number and password for authentication, and execute step 204 in the second embodiment. If not If login, go to step 304.
[0096] Step 304: The Portal server searches the existing record MAC address binding database acco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com