Method for running programs in isolation manner on basis of local virtualization mechanism
A technology of local virtualization and operation method, applied in the field of program isolation operation based on the local virtualization mechanism, can solve the problem that the program isolation operation method cannot satisfy the execution of untrusted software at the same time, achieve safe isolation operation and avoid access conflicts Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
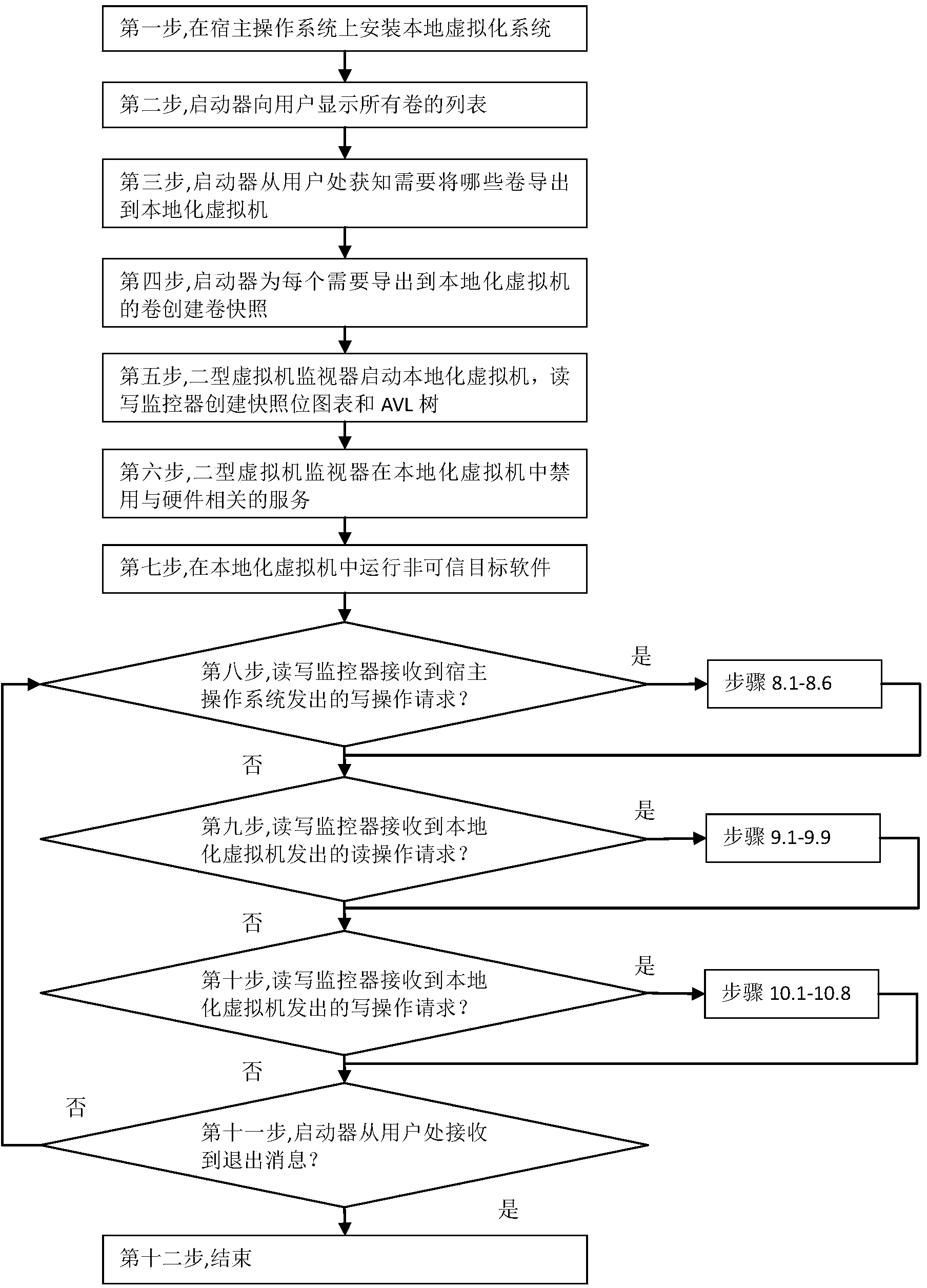
[0059] figure 1 Is the general flowchart of the present invention.
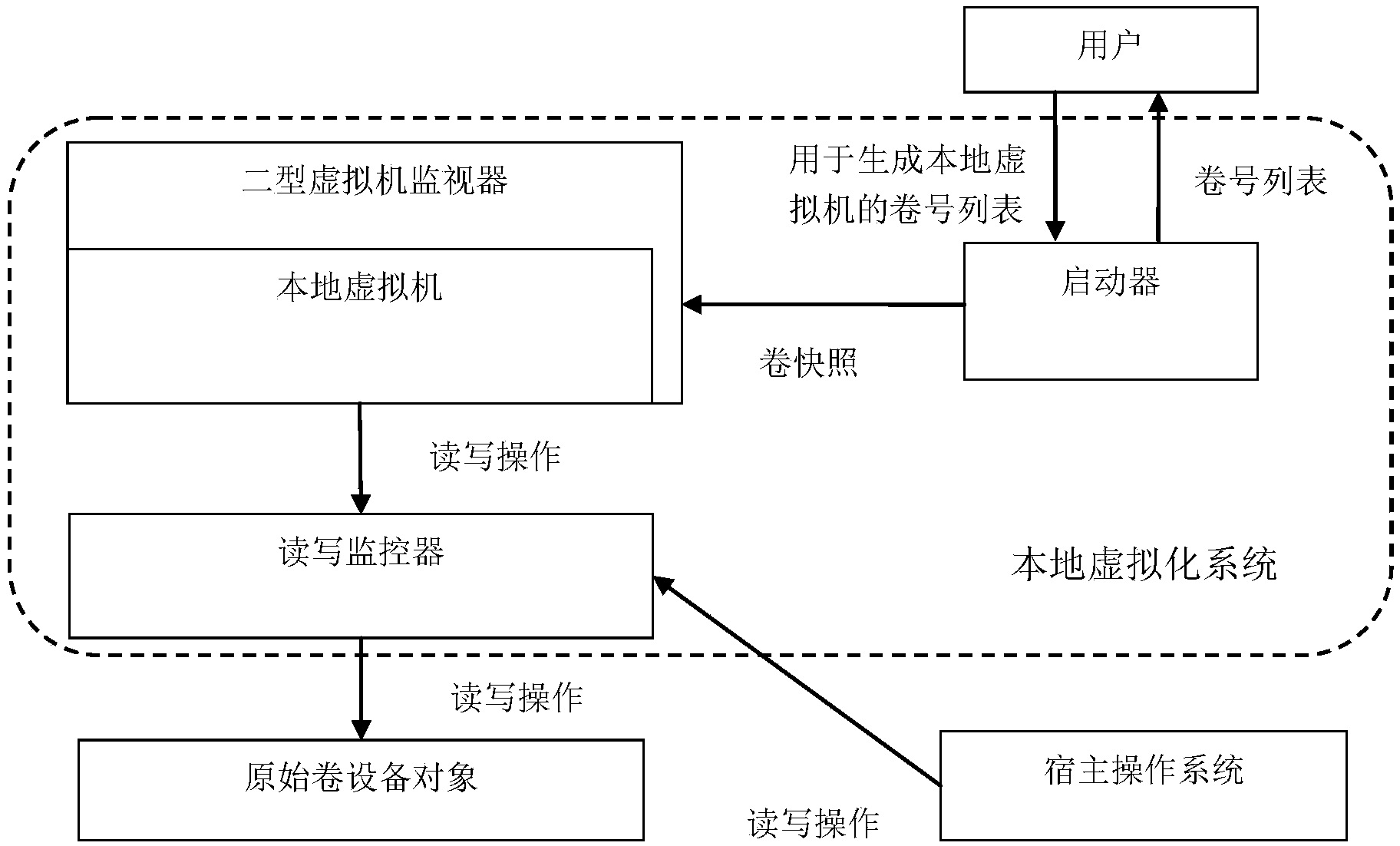
[0060] figure 2 Schematic diagram of the local virtualization system established for the first step.
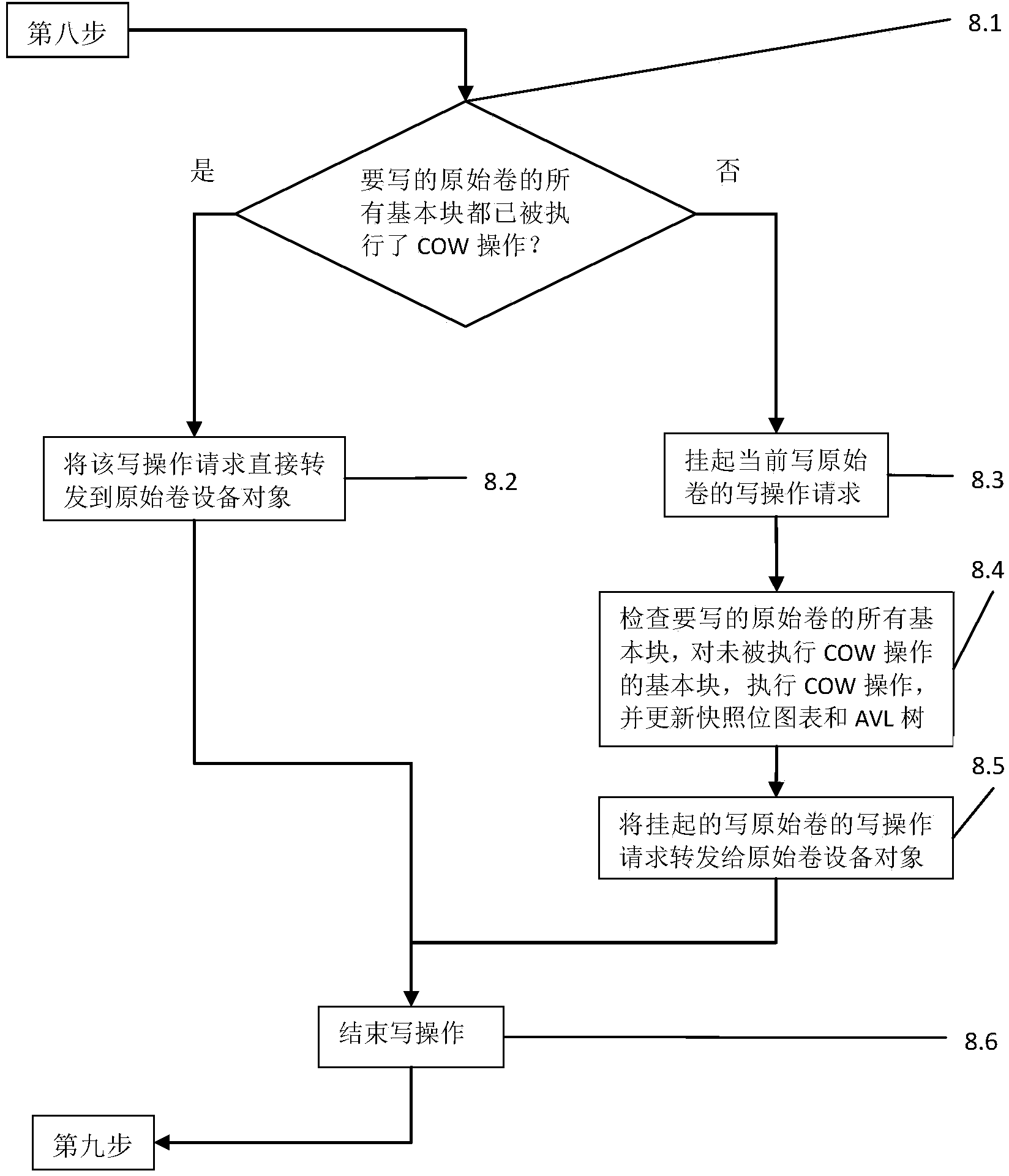
[0061] image 3 For steps 8.1-8.6 process.
[0062] Figure 4 For steps 9.1-9.9 process.
[0063] Figure 5 For steps 10.1-10.8 process.
[0064] The first step is to install a local virtualization system on the host operating system. The local virtualization system is composed of three software modules: a type-2 virtual machine monitor, a launcher, and a read-write monitor.
[0065] The launcher presents a list of volume numbers of all local volumes to the user, and obtains from the user the original volume numbers used to generate the local virtual machine. The initiator creates a volume snapshot (that is, a consistent copy of the original volume corresponding to a given moment) based on the original volume volume number, and sends the volume snapshot to the Type 2 hypervisor.
[0066] The type-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com