System and method for detecting APT attacks based on DNS log analysis
A technology of attack detection and DNS query, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of defense measures loopholes, all massive data analysis, missed APT attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings. This embodiment is implemented under the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following the embodiment.
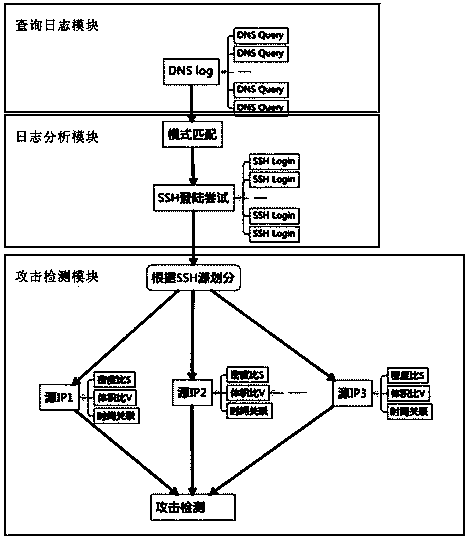
[0036] A kind of APT attack detection system based on DNS log analysis of the present invention is specifically as follows figure 1 As shown, it includes DNS query log record module, log analysis module and attack detection module. in,
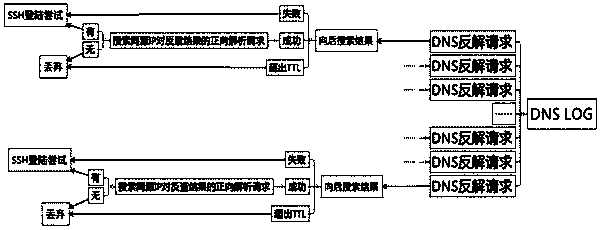
[0037] DNS query log recording module: it is used to record the DNS query action DNS to form a DNS log. The query action mainly includes query time time, source IP address ipsrc and query content qname;
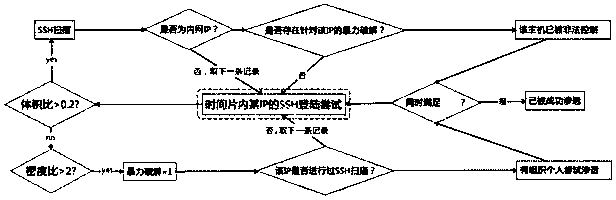
[0038] Log analysis module: used to convert DNS query action requests into SSH login attempt information, and calculate the time density...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com