Terminal admission control method based on switch port management
A technology of access control and switch, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of ARP spoofing, difficulty, unimaginable, etc., and achieve the effect of ensuring integrity and accurate access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
preparation example Construction
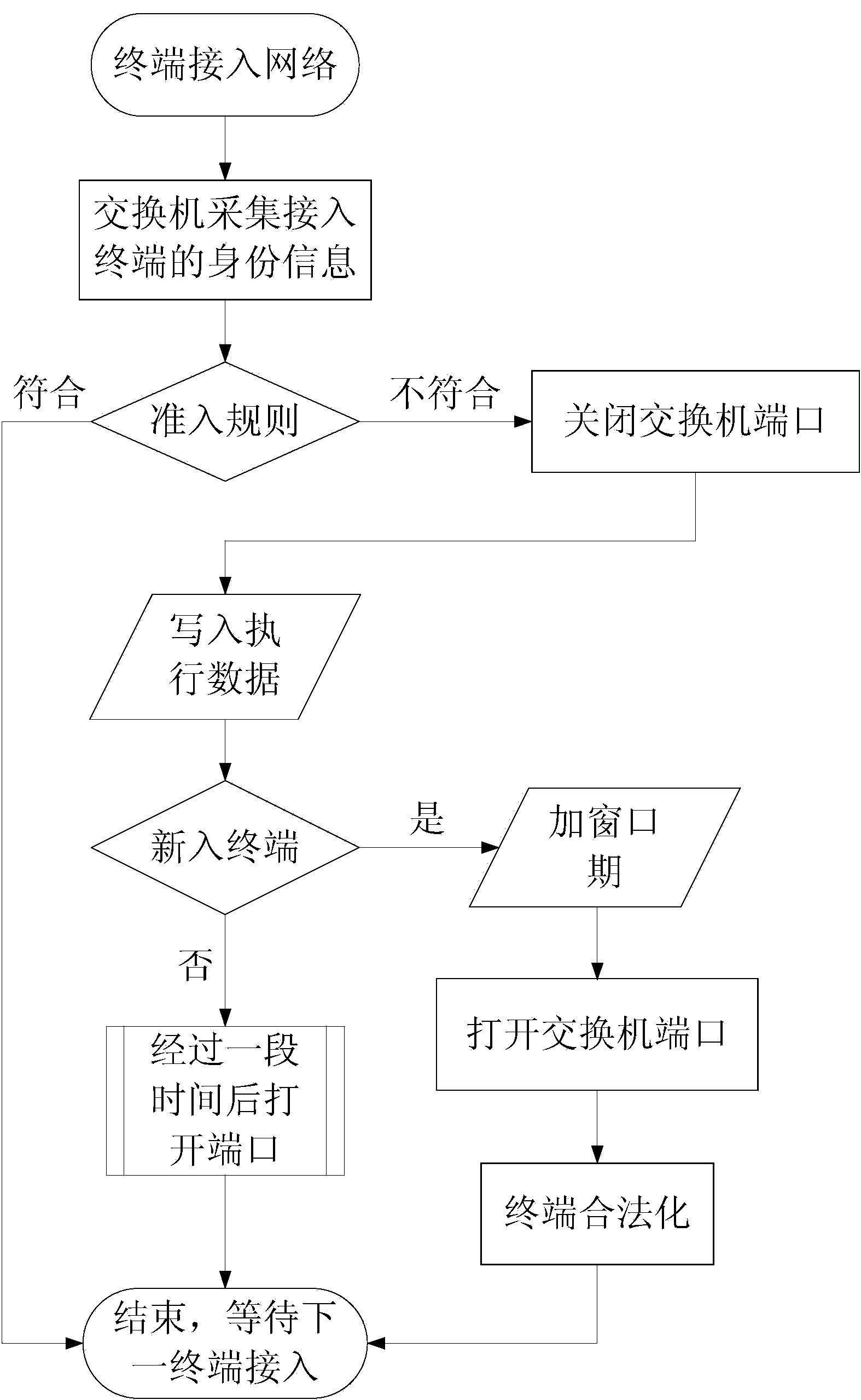
[0048] In a preferred embodiment, figure 1 It exemplarily shows a schematic flow chart of a preparation method of a terminal admission control method based on switch port management in the present invention, including:
[0049] A: After a new terminal is connected to the network, the identity information of the newly connected terminal is collected through the switch;
[0050] B: the switch extracts the unique identifier in the identity information of the terminal; the switch associates the terminal with a port of the switch;
[0051] C: comparing the unique identifier with the MAC address in the access database on the server side, querying the preset access database, and judging the identity information of the terminal;
[0052] If the unique identifier is found in the access database, the terminal is legal and no action is taken;
[0053] If the unique identifier cannot be found in the access database, it is an illegal terminal or external terminal, immediately close the p...
specific Embodiment
[0074] HUB device management:
[0075] When collecting terminal information, the present invention associates the MAC of the terminal with the port of the switch. When a switched port corresponds to two or more MACs, it indicates that a HUB is connected to the port. When this situation is found, the present invention will close the switch port.
[0076] Virtual machine MAC management:
[0077] It should be noted that when a virtual machine is installed and running on a legal terminal in the intranet, there will be two MACs on the switch port corresponding to the terminal (one for the terminal and the other for the virtual machine). situation, the present invention automatically filters the virtual machine MAC according to the built-in MAC address range, and then performs multi-MAC detection.
[0078] Terminal MAC address management:
[0079]Because the MAC address on the network card used for networking on the computer is not fixed and cannot be changed in the system, once ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com