Virtual machine simultaneous-locating detection method based on hidden channel under cloud environment
A covert channel and detection method technology, applied in the field of virtual machines and network security, can solve the problems of reduced effectiveness and inability to effectively detect co-residents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
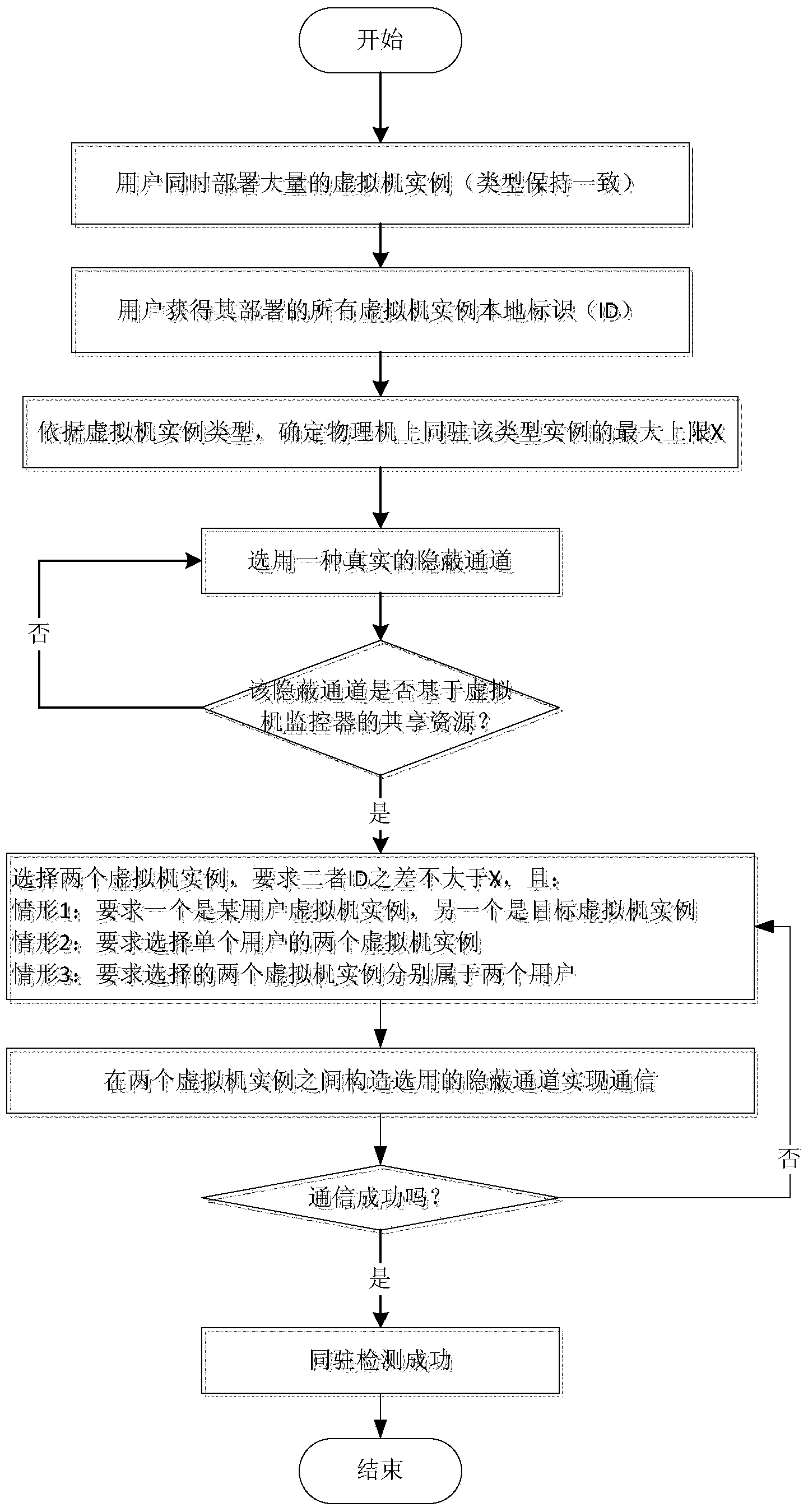
[0063] In actual situations, if a single tenant (or two cooperative users) deploys multiple instances of the same type at the same time, and hopes that two or more of the instances can reside on the same physical machine to meet the tenant's own specific computing needs;
[0064] Or two cooperating users, one of which user A has pre-deployed a virtual machine on the cloud platform, and the other cooperating user B hopes to deploy a large number of virtual machine instances of the same type as user A's virtual machine instance to integrate his own virtual machine with The pre-deployed virtual machine of user A resides on the same physical machine, and the upper limit of the virtual machine of this physical machine is X.
[0065] In these several situations, using the co-resident detection method of the present invention can easily find a pair or multiple virtual machine instances co-resident.
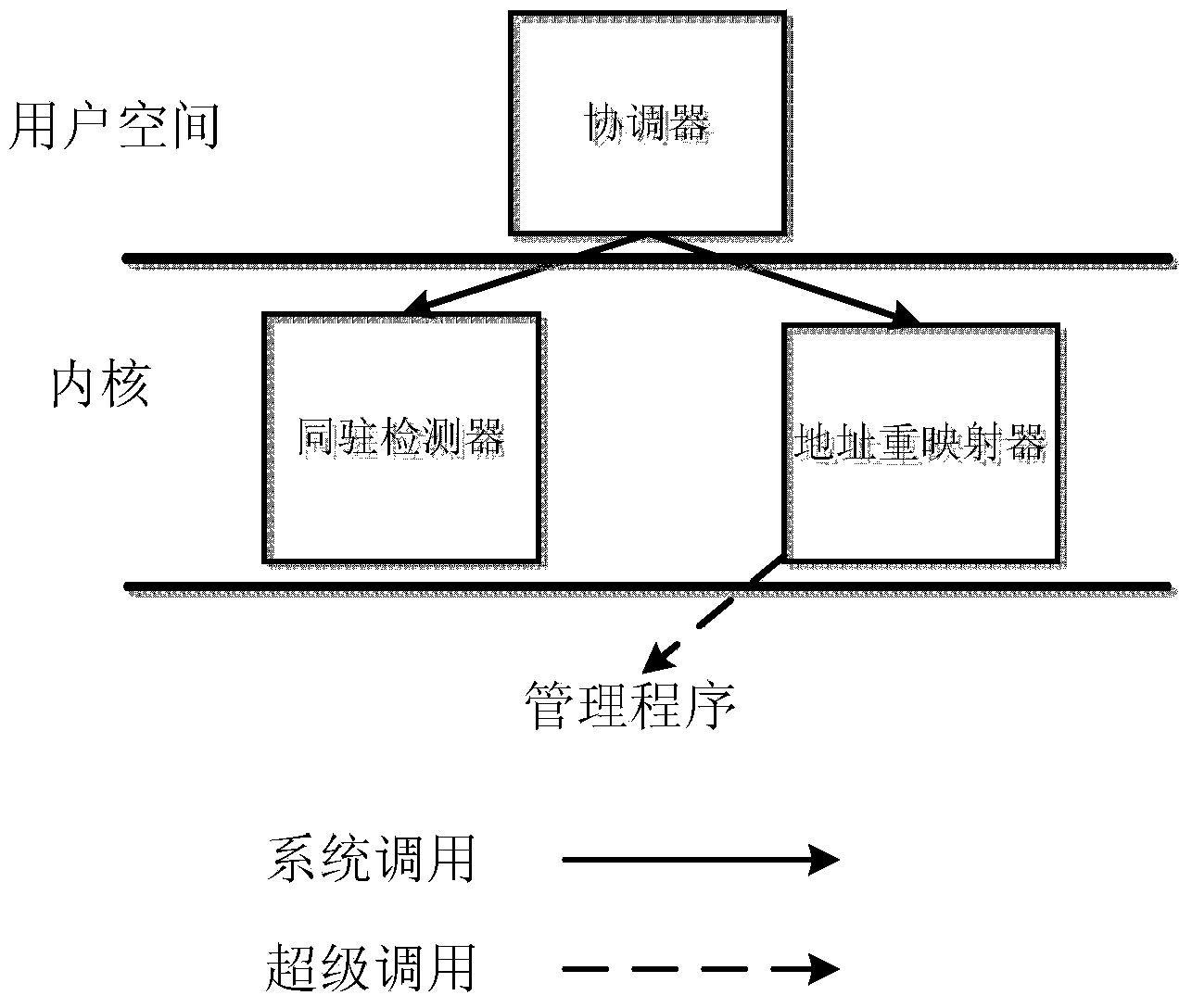
[0066] Taking the cloud platform (EC2) based on Xen virtualization technology as an...
Embodiment 2
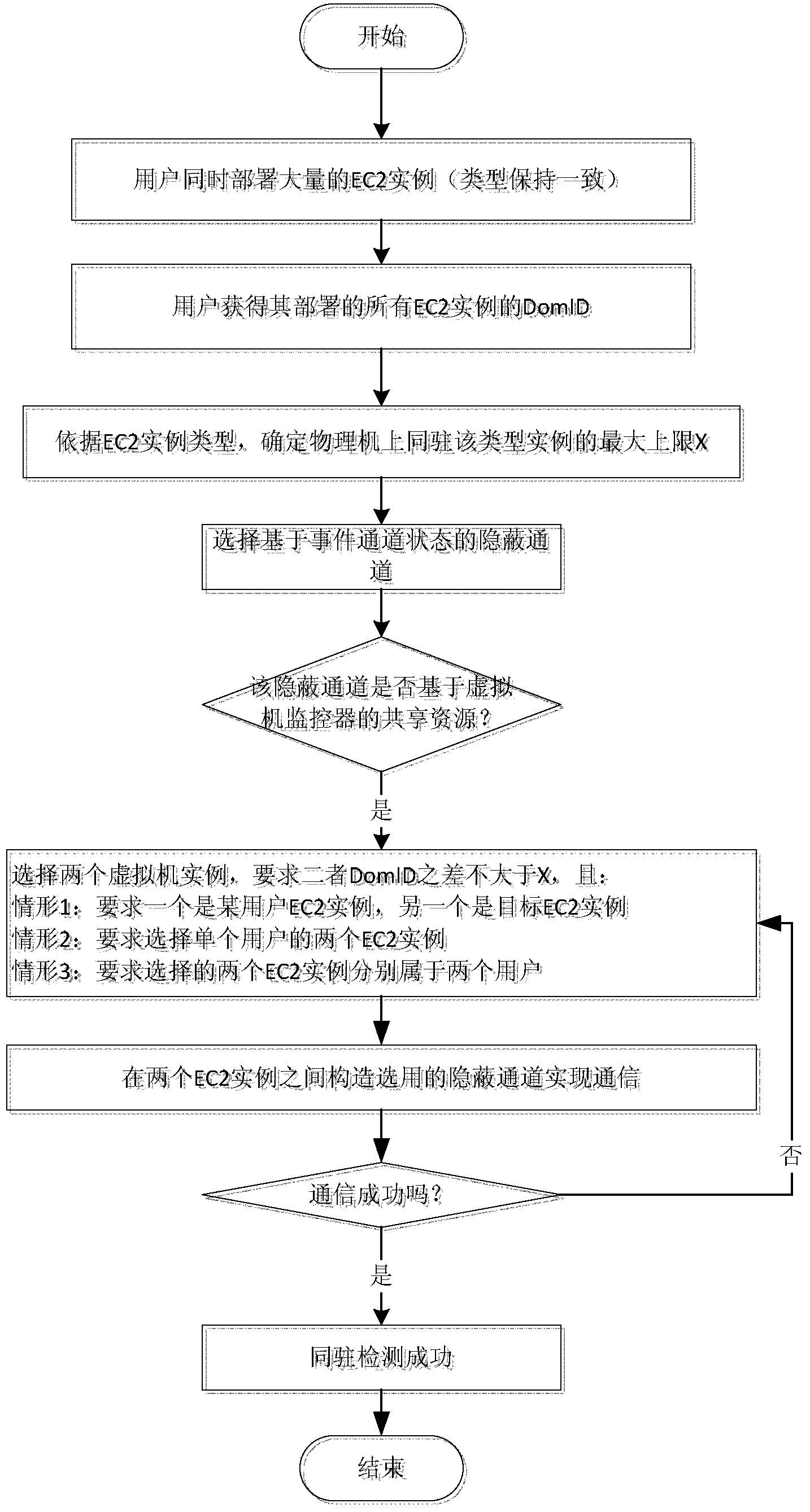
[0072] In fact, some cloud service providers (such as EC2) claim to users that they provide users with dedicated and exclusive services, and the instances created by users are physically isolated from the instances of other tenants. That is, the user exclusively owns a physical machine, and all instances created by the user run on the physical machine. Compared with ordinary rented services, this dedicated service charges more, but is the cloud service provider honest enough?
[0073] In this case, the co-resident detection method of the present invention can quickly detect whether the dedicated instance is co-resident, and check whether the cloud service provider really provides physical isolation for the user.
[0074] like Figure 4 As shown, the user creates multiple dedicated instances and obtains the DomIDs of these instances respectively. The method of obtaining the DomID is the same as that in Example 1; because it is a verification experiment, there is no need...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com