A multi-stage secure routing method based on network coding in delay-tolerant networks
A network coding and delay-tolerant network technology, applied in the field of multi-stage secure routing algorithms, can solve the problems that network coding performance and security cannot be balanced, traditional routing schemes are not suitable for damaged delay-tolerant network environments, and nodes in actual environments may not be reliable.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0097] Network Coding Implementation
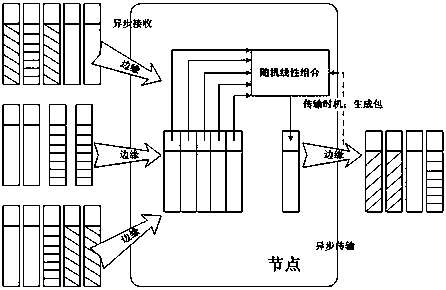
[0098] Network coding supports relay nodes to re-encode data packets. When a source node sends a data packet to a destination node, all or part of the rest of the relay nodes on the path between the two nodes are combined and forwarded with a certain probability to receive a linearly encoded packet of the message (similar to in XOR operation) to the next node, such as figure 1 shown. A sufficiently linear and independent encoding beam is received at the destination node, and the decoding matrix is converted into a triangular form using the Gaussian elimination method (used to solve thousands of equations and unknowns, and the extremely large equations of millions of equations are solved by iterative method) matrix, and finally decode all the original messages. Compared with traditional schemes, network coding can calculate scheduling strategies to optimize the use of limited available network resources, improve network system throughp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com