Network object and event integral monitoring method based on GIS (Geographic Information System) super cloud computing
A network monitoring and network technology, applied in the field of network information security, can solve the problems such as the difficulty of spatial positioning and prevention monitoring, the inability to meet the needs of big data processing efficiency and real-time, and the inability to obtain network-related data distributed in time and space. To achieve the effect of security governance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
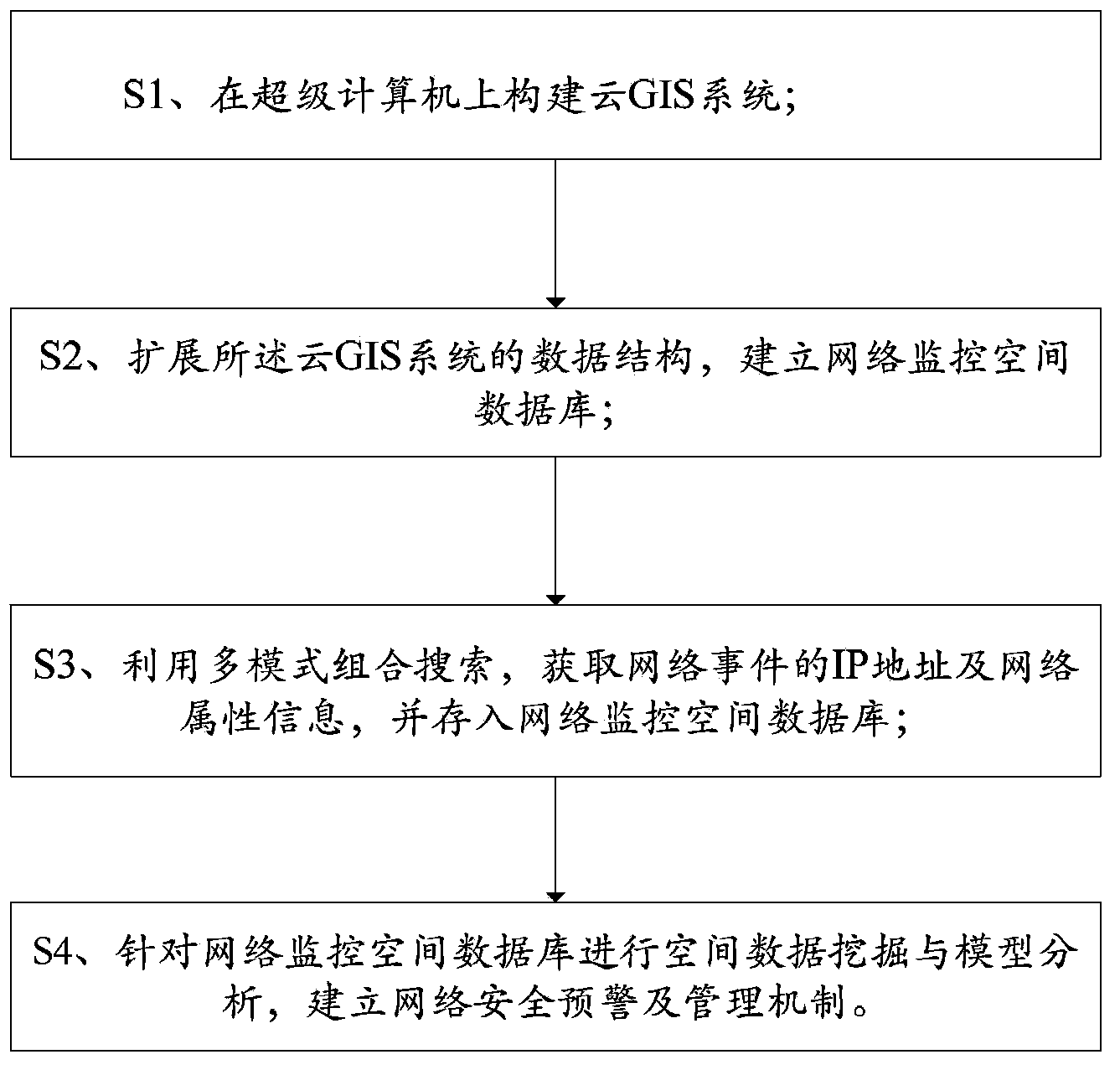
[0030] The present embodiment provides an integrated monitoring method based on cloud GIS, comprising the following steps:
[0031] S1. Build a cloud GIS system on a supercomputer;
[0032] S2. Expanding the data structure of the above-mentioned cloud GIS system, integrating the IP database into the above-mentioned cloud GIS system, expanding the spatial geographic information (x, y) into three-dimensional spatial geographic information (x, y, IP), and establishing a network monitoring spatial database.
[0033] The above-mentioned extension also includes extending the real attribute information of the network object to "real-virtual" attribute information, and the above-mentioned "virtual" attribute information is the network attribute information of the above-mentioned network object.
[0034] The above-mentioned real attribute information is the real space attribute where the above-mentioned network object is located, including area attribute information, street attribute i...
Embodiment 2
[0040] On the basis of embodiment 1, the integrated monitoring method based on cloud GIS comprises the following steps:
[0041] S1. Build a cloud GIS system on a supercomputer;
[0042] Usually the above-mentioned supercomputer is composed of hundreds or even more processors, which can handle large-scale and complex computing tasks that ordinary computers cannot complete. Most of them use a heterogeneous fusion system combining CPU and GPU. The hardware part is mainly composed of distributed processing system, communication system, input and output system, monitoring and diagnosis system and infrastructure system, and the software part is mainly composed of operating system, compiling system, parallel program development environment and scientific computing visualization system. The above-mentioned cloud GIS uses the cloud computing architecture for GIS to realize functions such as collection, storage, processing, and application of spatial data and its attributes.
[0043] ...
Embodiment 3
[0054] This embodiment provides an integrated monitoring method based on cloud GIS, an example of integrated monitoring of cybercrime events based on cloud environment, including the following steps:
[0055] S1. Build a cloud GIS system on a supercomputer;
[0056] S2, expanding the data structure of the above-mentioned cloud GIS system, and establishing a network monitoring spatial database;
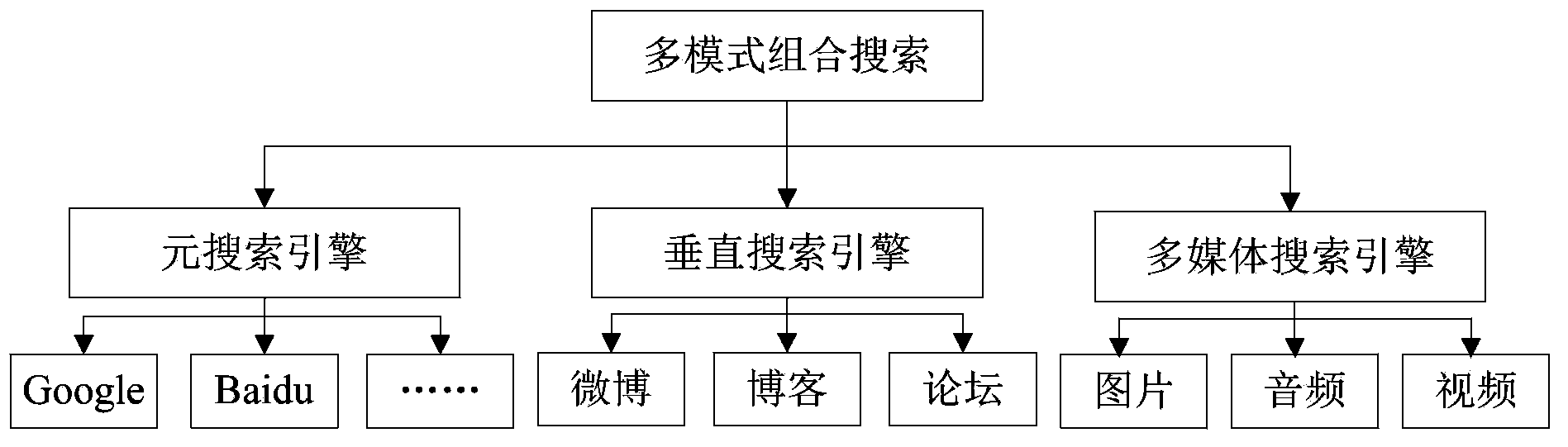
[0057] To establish a network monitoring spatial database, the process is as follows: store the actual spatial location (x, y), network spatial location (IP) and their attribute data of network objects and events in the cloud GIS system, and store the decimal IP After the address difference is filled with zeros (make up three digits, and zeros are filled when there is a gap), the middle separator is removed, so as to realize the conversion from IP to P value (for example, 1.1. , which can ensure that the IP value is transformed into a unique value P, and can be flexibly interchanged b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com