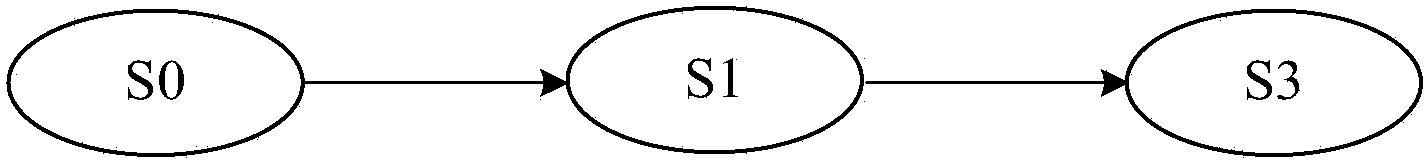Regularization state machine model design method with stateful protocol
A technology of state machine model and design method, which is applied in the field of security vulnerability detection, can solve problems such as low efficiency and large amount of test data, and achieve the effect of efficient testing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
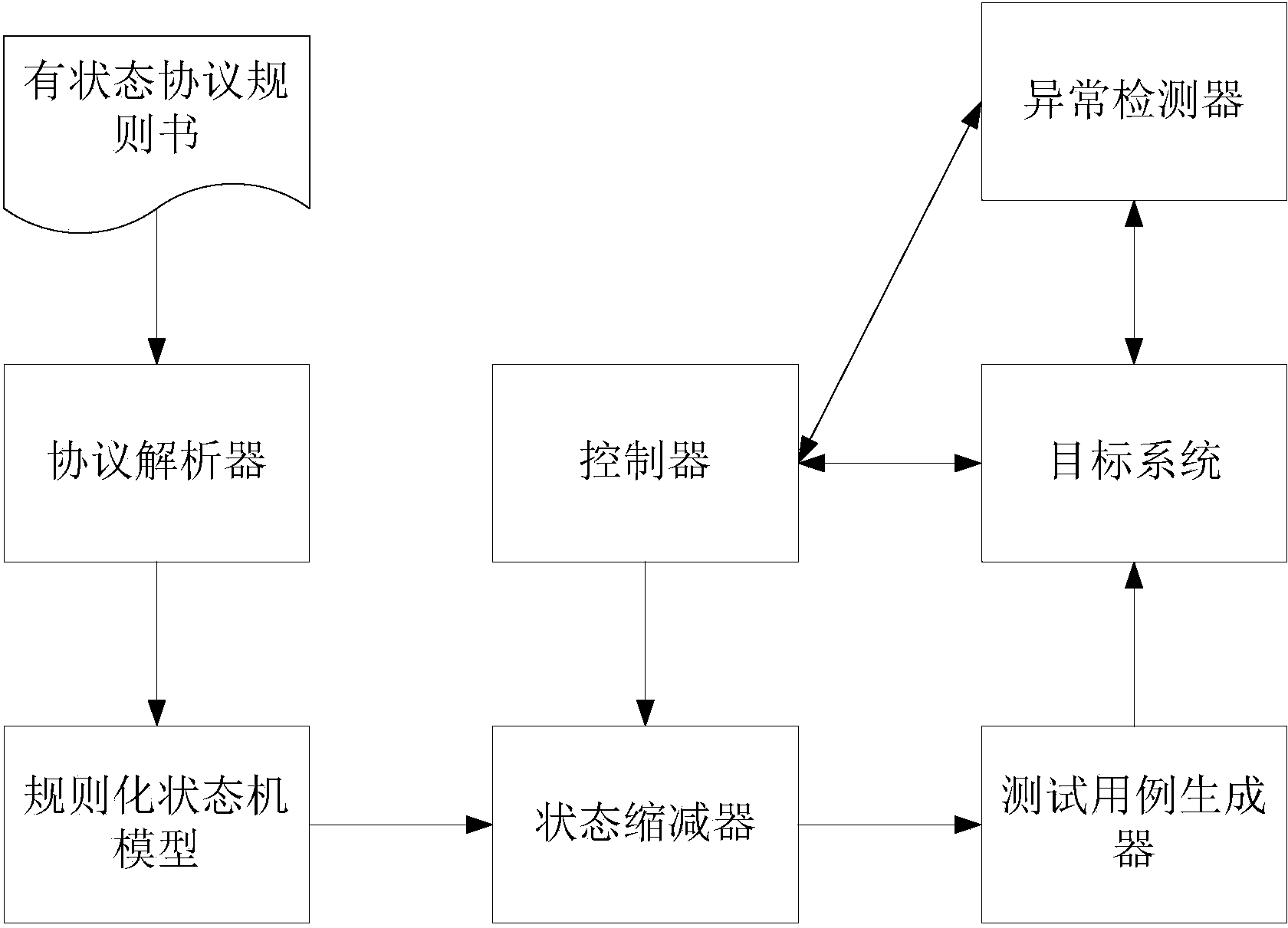
[0027] The present invention will be further described below in conjunction with the drawings and specific embodiments.
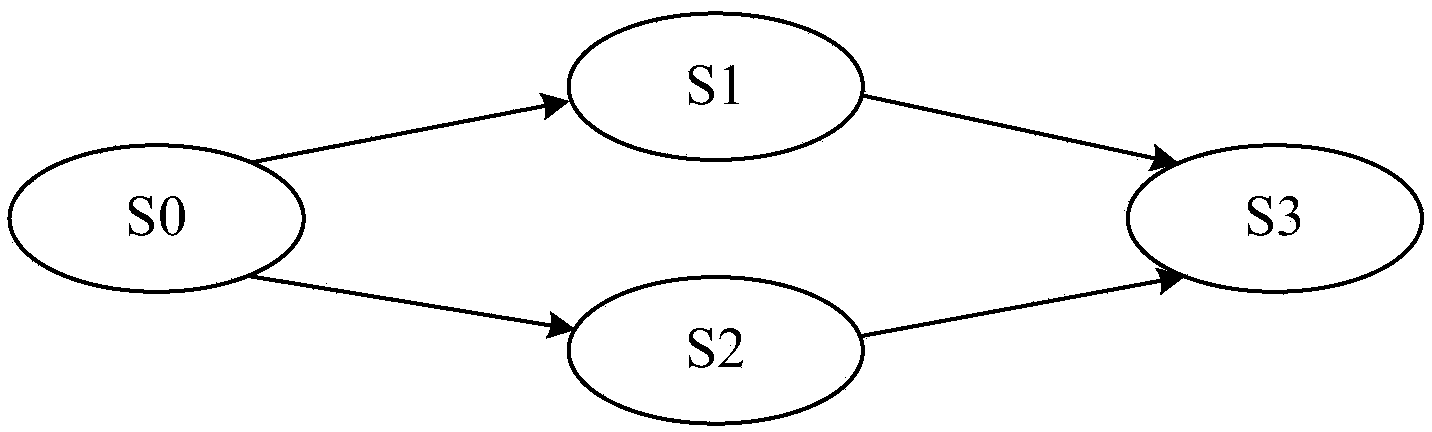
[0028] 1. Regularized state machine model
[0029] The formal description model of network protocol plays an important role in network protocol fuzz testing. The formal description model is a data model that expresses the network protocol in a way that is easier to understand and analyze its characteristics according to the text description of its protocol specification (such as RFC documents, etc.), which is convenient for network protocol testing. .
[0030] A stateful network protocol is a network protocol related to context information, data information and historical traces. The communication process of a stateful network protocol is very complicated, usually including handshake, authentication and other processes. Generally, the support for fuzz testing is not perfect. Most of the generated test data can only cover the first interaction state, and i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com