Parallel vulnerability mining method based on open source library and text mining
A vulnerability mining and text mining technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve problems such as increased economic losses and increased harm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The present invention is further described as follows in conjunction with accompanying drawings and embodiments.
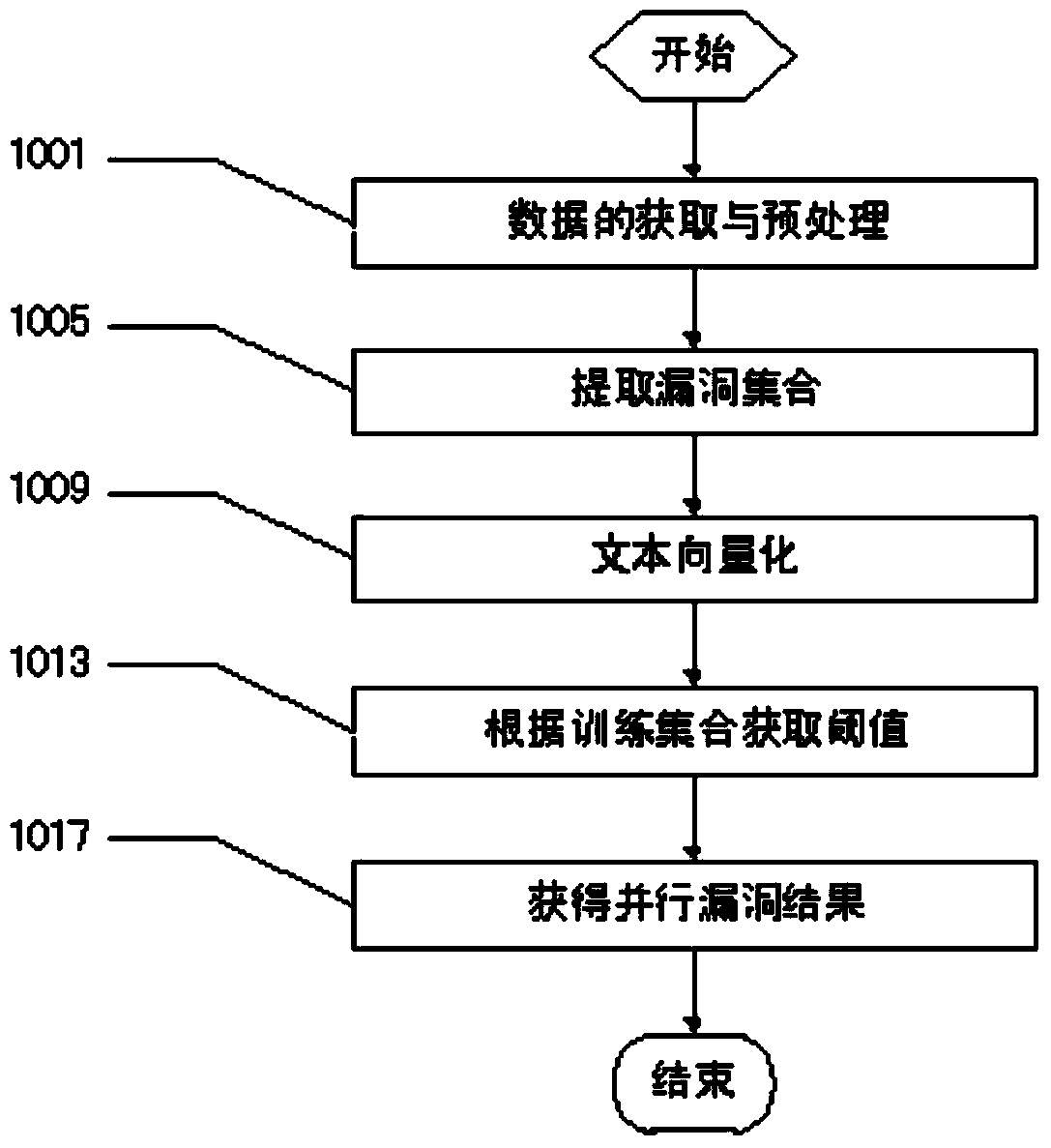
[0045] figure 1 It is a flowchart of the present invention, illustrating an embodiment of parallel vulnerability discovery. The parallel vulnerability discovery begins with obtaining and preprocessing vulnerability data. The second step is to extract the vulnerability set. The third step is the vectorization of vulnerability information. The fourth step is to use the training set to obtain the threshold. The fifth step is to obtain parallel vulnerability results.
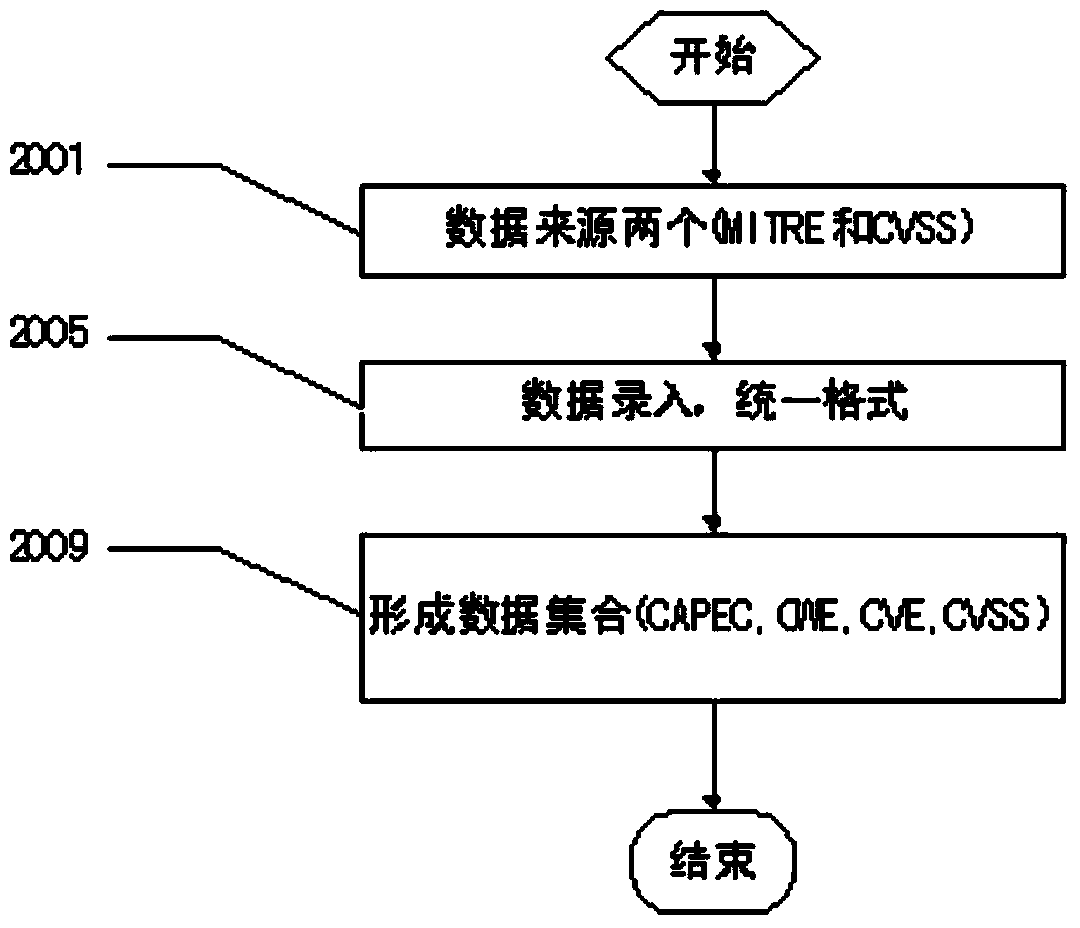
[0046] figure 2 for figure 1 The flow chart of data acquisition and preprocessing in the figure illustrates an embodiment of how to acquire vulnerability data and perform preprocessing. The process starts with obtaining data from two public data sources (MITRE and CVSS), and then enters the original data into the system, operates in a unified format, and forms four data sets (CAPEC, CWE, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com