Multi-image encrypting and decrypting method based on ghost imaging and public key cryptography
A technology of public key cryptography and encryption method, which is applied in image communication, electrical components, etc., can solve the problem of lack of research on multi-image encryption technology, and achieve the effect of saving costs and simplifying the system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0030] Such as figure 1 Shown, basic scheme of the present invention is:
[0031] The encryption process is as follows:
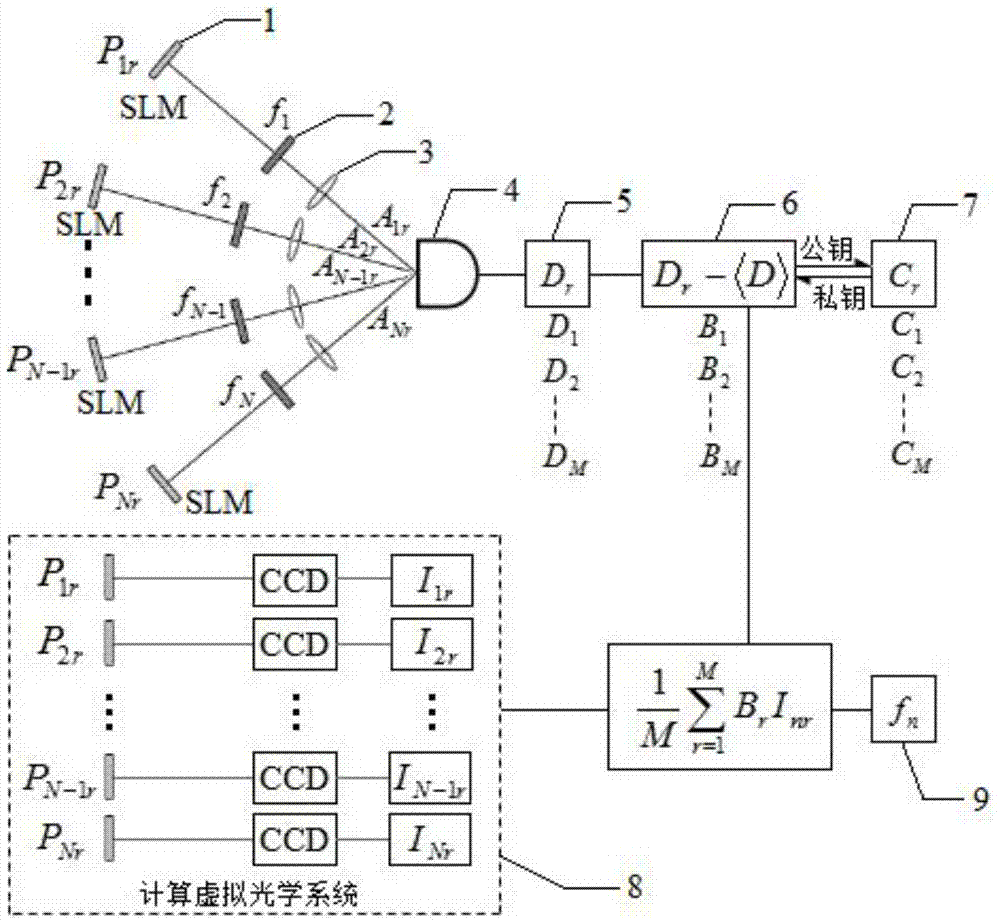
[0032] 1. First, multiple images are detected by a non-resolution bucket detector. The optical system is composed of several light paths, one light path is an SLM1, the image to be encrypted 2, and the convex lens is composed of 3, and each light path converges on the barrel detector 4.
[0033] 2. Using multiple random phase plates (P 1r ,P 2r ,...,P Nr ) light intensity information in its Fresnel domain (I 1r ,I 2r ,...,I Nr ) for N images to be encrypted (f 1 , f 2 ,..., f N ) are randomly modulated respectively, where P 1r ,P 2r ,...,P Nr Independent of each other, not related to each other. The modulated information converges on the barrel detector through the convex lens, and the barrel detector ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com