Integrated circuit hardware Trojan detection method and system
A hardware Trojan detection and integrated circuit technology, applied in electronic circuit testing and other directions, can solve the problems of high cost and low efficiency of hardware Trojan detection, and achieve the effect of reducing cost and improving detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The specific implementation of the integrated circuit hardware Trojan horse detection method and system provided by the present invention will be described in detail below in conjunction with the accompanying drawings.
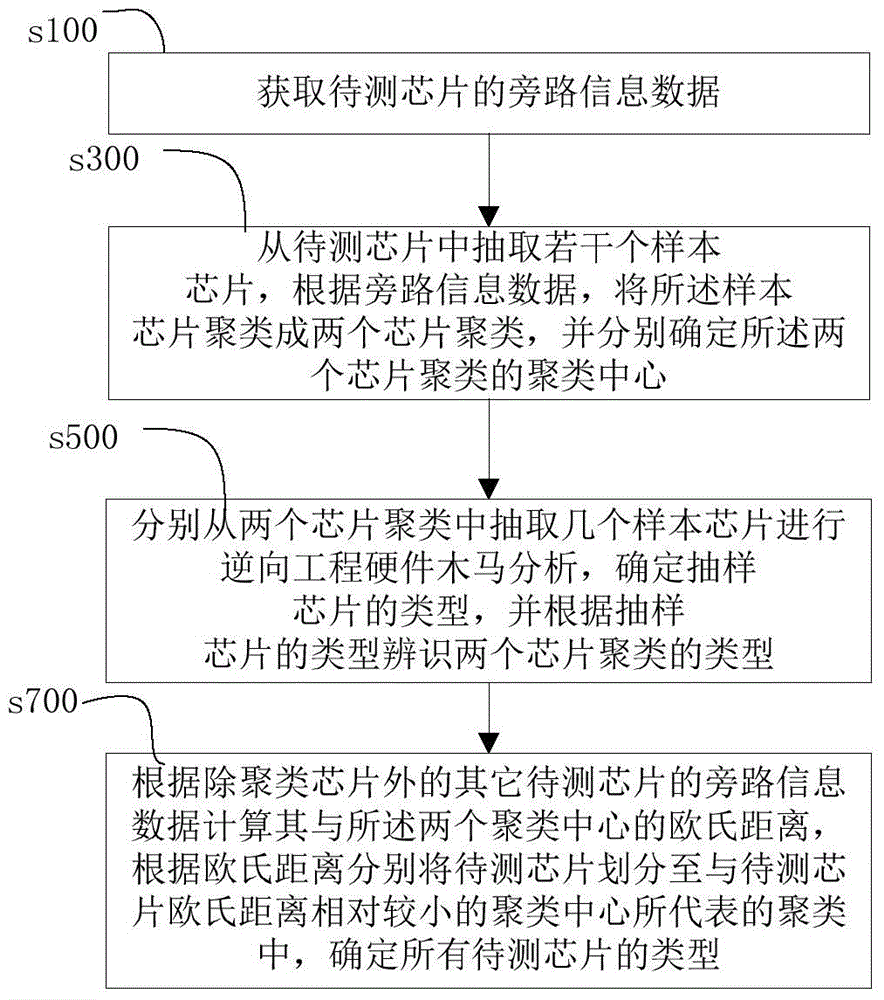
[0025] refer to figure 1 , figure 1 Shown is a flowchart of an integrated circuit hardware Trojan horse detection method of an embodiment, as shown in the figure, the integrated circuit hardware Trojan horse detection method provided by this embodiment includes the following steps:
[0026] s100, obtaining bypass information data of the chip to be tested;
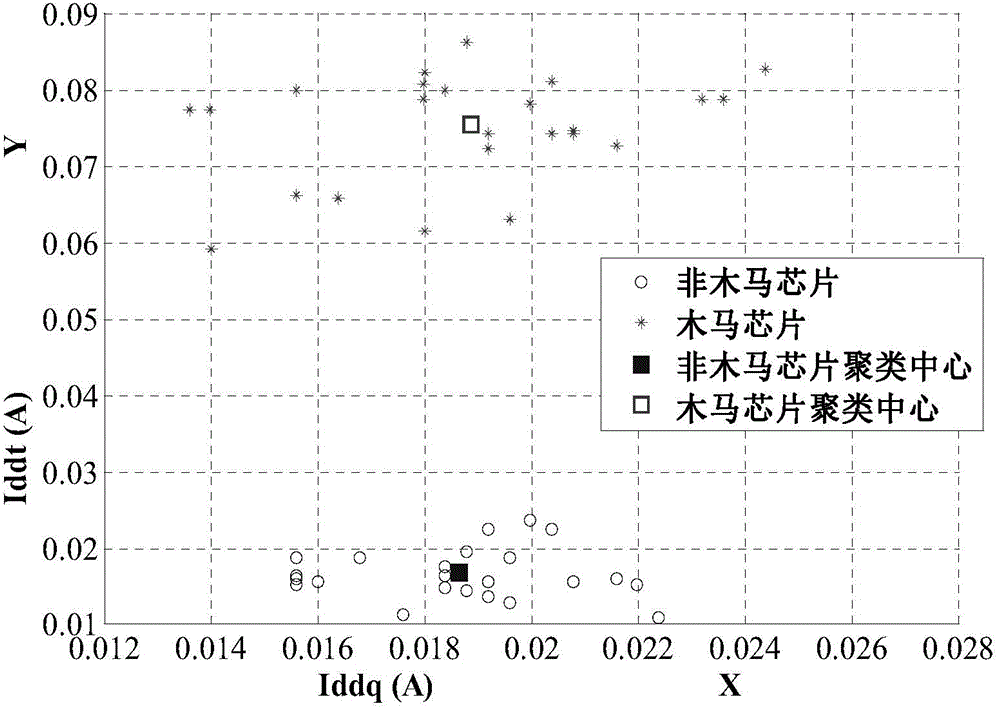
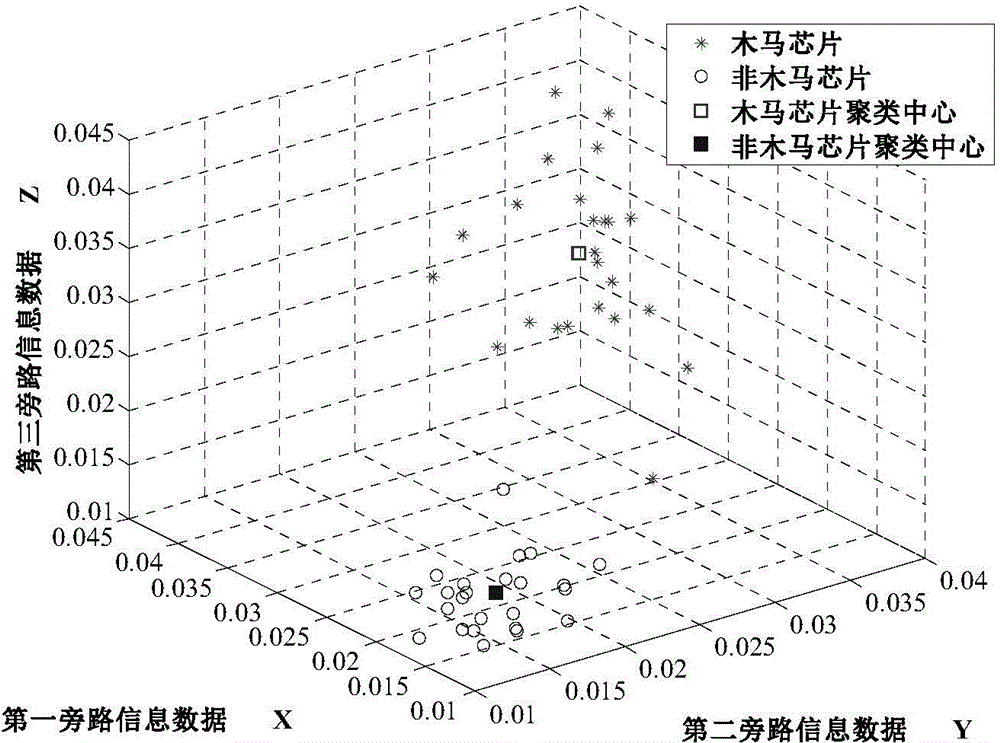
[0027] In the above step s100, the required bypass information can be selectively obtained according to the functions of the chip to be tested and the bypass information corresponding to the area where there may be a hardware Trojan horse, and the above bypass information can be stored in the vector X k , used for subsequent chip clustering and type determination, where X k The subscript k=1,2,......
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com