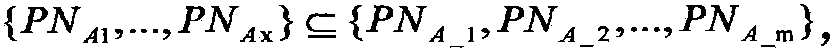A smart phone secure communication system and method
A technology for confidential communication and smart phones, which is applied in the field of information security and can solve problems such as denial, wireless eavesdropping, and limitation of the scope of application of mobile phones.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
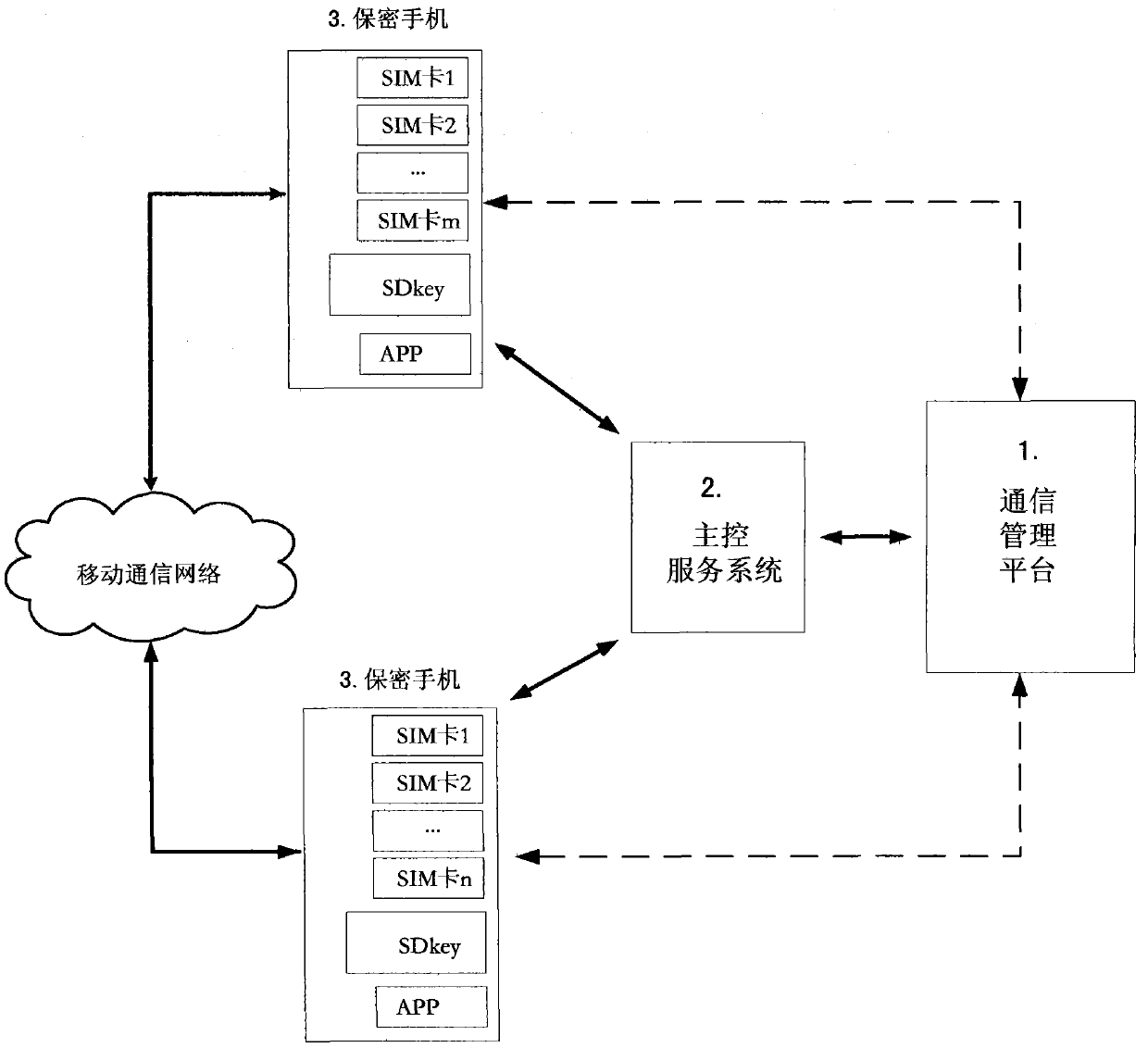
[0089] Embodiment 1: see figure 1 , a smart phone security communication system, comprising: a communication management platform 1, a main control service system 2 and a plurality of security mobile phones 3; the communication management platform 1 is accessed through the Internet by means of a terminal PC browser, and is used for mobile phone users , the life cycle of the confidential mobile phone 3, virtual mobile phone number, SIM card number, and user digital certificate is managed; the terminal PC is connected with the confidential mobile phone 3 through a USB interface, and imports a digital certificate for the confidential mobile phone 3;
[0090] The main control service system 2 and the secure mobile phone 3 perform SSL two-way authentication and establish encrypted long connections through the Internet or 2G / 3G / 4G mobile communication network; control and transmit the entire communication process of the secure mobile phone 3 communication parties key, user digital ce...
Embodiment 2
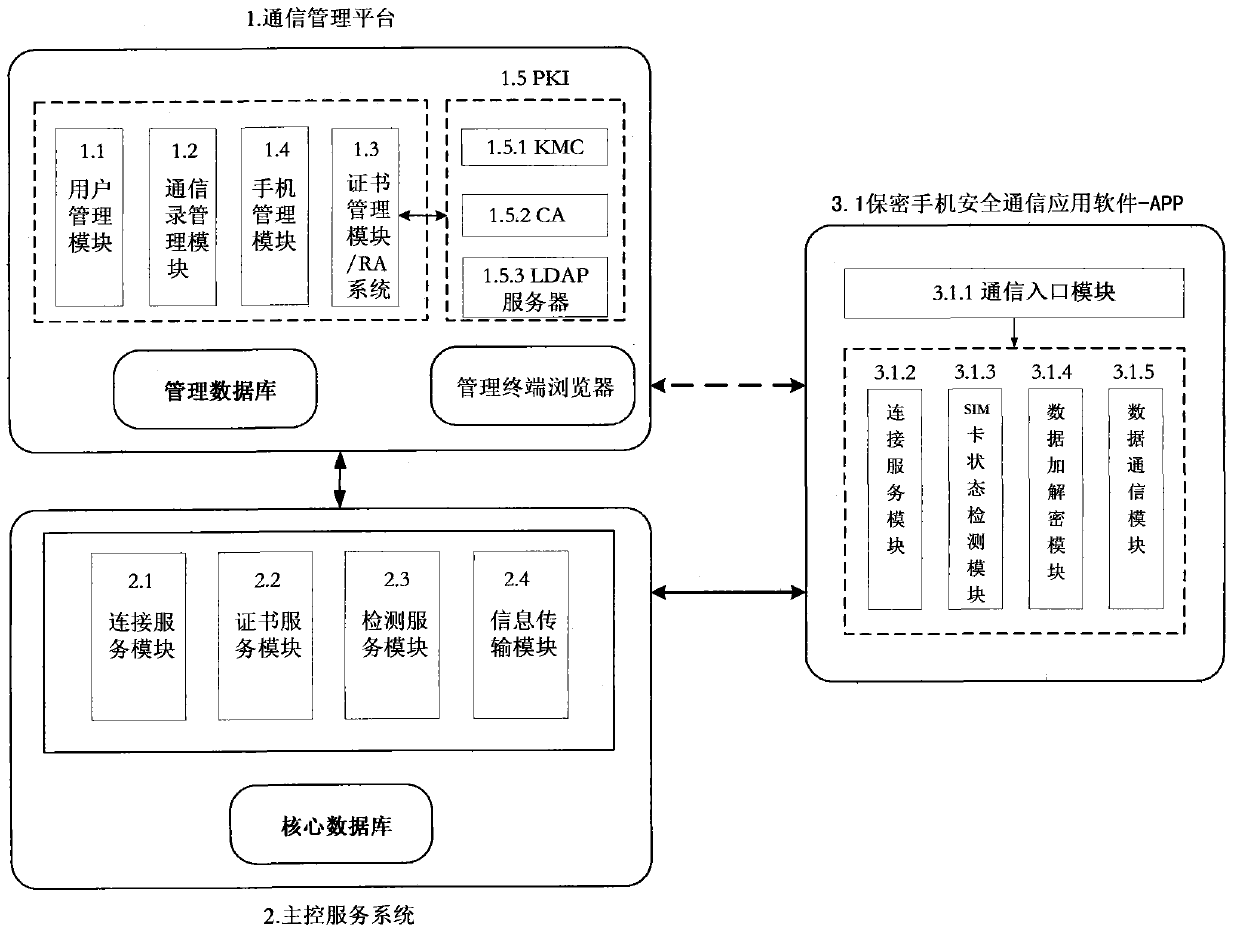
[0092] Example 2: see figure 2 , in a kind of smart phone secure communication system described in embodiment 1, it is characterized in that:
[0093] The communication management platform 1 includes: a user management module 1.1, an address book management module 1.2, a certificate management module 1.3, and a mobile phone management module 1.4; wherein:
[0094] Described user management module 1.1 carries out real-name information registration, information change, user cancellation management for the user, and creates a unique virtual mobile phone number for each user;
[0095] The address book management module 1.2 performs user addition, deletion, change, and cancellation of SIM card number operations, and binds or unbinds the virtual mobile phone number of the user with the SIM card number, so that one virtual mobile phone number Corresponding to t SIM card numbers of the user;
[0096] The certificate management module 1.3 manages the life cycle of the user's encrypt...
Embodiment 3
[0109] Embodiment 3: a kind of intelligent mobile phone secure communication system as described in embodiment 1 or 2, it is characterized in that:
[0110] Described SSL two-way authentication refers to adopting the SSL3.0 agreement that Netscape Company Netscape proposes, realizes the identity verification of client and server both sides by digital signature and digital certificate;
[0111] Described local PIN code authentication refers to verifying the user PIN code of the described custom SDkey built into the secure mobile phone 3;
[0112] The session key includes an encryption algorithm key and a broken algorithm key;
[0113] The encryption is broken, which means that the APP of the sender will obtain the voice data unit or short message of each frame through the microphone of the confidential mobile phone, the analog-to-digital converter and the voice data frame sampling, and first use the encryption algorithm key and the corresponding The encryption algorithm is enc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com